|
|
Home | Switchboard | Unix Administration | Red Hat | TCP/IP Networks | Neoliberalism | Toxic Managers |
| (slightly skeptical) Educational society promoting "Back to basics" movement against IT overcomplexity and bastardization of classic Unix | |||||||
| News | GCC | Best C books | Recommended Links | Debugging | Make |
| Richard Stallman and War of Software Clones | The Short History of GCC development | Classic Unix tools | History | Humor | Etc |
Edited content from Wikipedia
GDB was first written by Richard Stallman in 1986 as part of his GNU project. It was the third major program after Emacs and GCC created in the project. It was modeled after the DBX debugger from BSD. Like with other major GNU programs Stallman soon lost control of the development and from 1990 to 1993 it was maintained by John Gilmore while he worked for Cygnus Solutions. Now it is maintained by the GDB Steering Committee which is appointed by the Free Software Foundation. (See GDB- The GNU Project Debugger). GDB is still actively developed and available on all major architectures. Among good tutorials:
GDB Cheat Sheet is available from yolinux project. See also O'Reilly Linux Command Directory gdb
GDB offers standard facilities the allow tracing and altering the execution of computer programs. The user can monitor and modify the values of programs' internal variables, and call functions independently of the program's normal behavior. Since version 7.0, support for "reversible debugging" — allowing a debugging session to step backward, much like rewinding a crashed program to see what happened — is available. Version 7.0 new features also include support for Python scripting.
GDB offers a 'remote' mode often used when debugging embedded systems. Remote operation is when GDB runs on one machine and the program being debugged runs on another. GDB can communicate to the remote 'stub' which understands GDB protocol via serial connection or TCP/IP.[9] A stub program can be created by linking to the appropriate stub files provided with GDB, which implement the target side of the communication protocol.[10] Alternatively, gdbserver can be used to remotely debug the program without needing to change it in any way. The same mode is also used by KGDB for debugging a running Linux kernel on the source level with gdb. With KGDB, kernel developers can debug a kernel in much the same way as they debug application programs. It makes it possible to place breakpoints in kernel code, step through the code and observe variables. On architectures where hardware debugging registers are available, watchpoints can be set which trigger breakpoints when specified memory addresses are executed or accessed. KGDB requires an additional machine which is connected to the machine to be debugged using a serial cable or ethernet. On FreeBSD, it is also possible to debug using Firewire direct memory access(DMA).
The debugger does not contain its own graphical user interface, and defaults to a command-line interface. Several front-ends have been built for it, such as Xxgdb, Data Display Debugger (DDD), Nemiver, KDbg, Xcode debugger, GDBtk/Insight and the HP Wildebeest Debugger GUI (WDB GUI). IDEs such as Codelite, Code::Blocks, Dev-C++, GNAT Programming Studio (GPS), KDevelop, Qt Creator, MonoDevelop, Eclipse, NetBeans and VisualStudio (see VS AddIn Gallery) can interface with GDB. GNU Emacs has a "GUD mode" and several tools for VIM exist[citation needed]. These offer facilities similar to debuggers found in IDEs.
Some other debugging tools have been designed to work with GDB, such as memory leak detectors.
Command run -v run the loaded program with the parameters bt backtrace (in case the program crashed) info registers dump all registers disass $pc-32, $pc+32 disassemble
Consider the following source-code written in C:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
size_t
foo_len (const char *s)
{
return strlen (s);
}
int
main (int argc, char *argv[])
{
const char *a = NULL;
printf ("size of a = %d\n", foo_len (a));
exit (0);
}
Using the GCC compiler on GNU/Linux, the code must be compiled using the -g flag in order to include appropriate debug information on the binary generated, thus making it possible to inspect it using GDB. Assuming that the file containing the code above is named example.c, the command for the compilation could be:
gcc example.c -g -o example
And the binary can now be run:
# ./example Segmentation fault
Since the example code, when executed, generates a segmentation fault, GDB can be used to inspect the problem.
# gdb ./example GNU gdb (GDB) Fedora (7.3.50.20110722-13.fc16) Copyright (C) 2011 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "x86_64-redhat-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /path/example...done. (gdb) run Starting program: /path/example Program received signal SIGSEGV, Segmentation fault. 0x0000000000400527 in foo_len (s=0x0) at example.c:8 8 return strlen (s); (gdb) print s $1 = 0x0
Program received signal SIGSEGV, Segmentation fault. 0x0000000000400527 in foo_len (s=0x0) at example.c:8 8 return strlen (s); (gdb) print s $1 = 0x0 The problem is present in line 8, and occurs when calling the function strlen (because its argument, s, is NULL).
Depending on the implementation of strlen (in-line or not), the output can be different.
To fix the problem, the variable a (in the function main) must contain a valid string. Here is a fixed version of the code:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
size_t
foo_len (const char *s)
{
return strlen (s);
}
int
main (int argc, char *argv[])
{
const char *a = "This is a test string";
printf ("size of a = %d\n", foo_len (a));
exit (0);
}
Recompiling and running the executable again inside GDB now gives
a correct result:
GNU gdb (GDB) Fedora (7.3.50.20110722-13.fc16) Copyright (C) 2011 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "x86_64-redhat-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /path/example...done. (gdb) run Starting program: /path/example size of a = 21 [Inferior 1 (process 14290) exited normally]GDB prints the output of printf in the screen, and then informs the user that the program exited normally.
|
|
Switchboard | ||||
| Latest | |||||
| Past week | |||||
| Past month | |||||
|
|
Feb 14, 2012 | sanctum.geek.nz
When unexpected behaviour is noticed in a program, GNU/Linux provides a wide variety of command-line tools for diagnosing problems. The use of
gdb, the GNU debugger, and related tools like the lesser-known Perl debugger, will be familiar to those using IDEs to set breakpoints in their code and to examine program state as it runs. Other tools of interest are available however to observe in more detail how a program is interacting with a system and using its resources.Debugging with
gdbYou can use
gdbin a very similar fashion to the built-in debuggers in modern IDEs like Eclipse and Visual Studio.If you are debugging a program that you've just compiled, it makes sense to compile it with its debugging symbols added to the binary, which you can do with a
gcccall containing the-goption. If you're having problems with some code, it helps to also use-Wallto show any errors you may have otherwise missed:$ gcc -g -Wall example.c -o exampleThe classic way to use
gdbis as the shell for a running program compiled in C or C++, to allow you to inspect the program's state as it proceeds towards its crash.$ gdb example ... Reading symbols from /home/tom/example...done. (gdb)At the
(gdb)prompt, you can typerunto start the program, and it may provide you with more detailed information about the causes of errors such as segmentation faults, including the source file and line number at which the problem occurred. If you're able to compile the code with debugging symbols as above and inspect its running state like this, it makes figuring out the cause of a particular bug a lot easier.(gdb) run Starting program: /home/tom/gdb/example Program received signal SIGSEGV, Segmentation fault. 0x000000000040072e in main () at example.c:43 43 printf("%d\n", *segfault);After an error terminates the program within the
(gdb)shell, you can typebacktraceto see what the calling function was, which can include the specific parameters passed that may have something to do with what caused the crash.(gdb) backtrace #0 0x000000000040072e in main () at example.c:43You can set breakpoints for
gdbusing thebreakto halt the program's run if it reaches a matching line number or function call:(gdb) break 42 Breakpoint 1 at 0x400722: file example.c, line 42. (gdb) break malloc Breakpoint 1 at 0x4004c0 (gdb) run Starting program: /home/tom/gdb/example Breakpoint 1, 0x00007ffff7df2310 in malloc () from /lib64/ld-linux-x86-64.so.2Thereafter it's helpful to step through successive lines of code using
step. You can repeat this, like anygdbcommand, by pressing Enter repeatedly to step through lines one at a time:(gdb) step Single stepping until exit from function _start, which has no line number information. 0x00007ffff7a74db0 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6You can even attach
gdbto a process that is already running, by finding the process ID and passing it togdb:$ pgrep example 1524 $ gdb -p 1524This can be useful for redirecting streams of output for a task that is taking an unexpectedly long time to run.
Debugging withvalgrindThe much newer valgrind can be used as a debugging tool in a similar way. There are many different checks and debugging methods this program can run, but one of the most useful is its Memcheck tool, which can be used to detect common memory errors like buffer overflow:
$ valgrind --leak-check=yes ./example ==29557== Memcheck, a memory error detector ==29557== Copyright (C) 2002-2011, and GNU GPL'd, by Julian Seward et al. ==29557== Using Valgrind-3.7.0 and LibVEX; rerun with -h for copyright info ==29557== Command: ./example ==29557== ==29557== Invalid read of size 1 ==29557== at 0x40072E: main (example.c:43) ==29557== Address 0x0 is not stack'd, malloc'd or (recently) free'd ==29557== ...The
Tracing system and library calls withgdbandvalgrindtools can be used together for a very thorough survey of a program's run. Zed Shaw's Learn C the Hard Way includes a really good introduction for elementary use ofvalgrindwith a deliberately broken program.ltraceThe
straceandltracetools are designed to allow watching system calls and library calls respectively for running programs, and logging them to the screen or, more usefully, to files.You can run
ltraceand have it run the program you want to monitor in this way for you by simply providing it as the sole parameter. It will then give you a listing of all the system and library calls it makes until it exits.$ ltrace ./example __libc_start_main(0x4006ad, 1, 0x7fff9d7e5838, 0x400770, 0x400760 srand(4, 0x7fff9d7e5838, 0x7fff9d7e5848, 0, 0x7ff3aebde320) = 0 malloc(24) = 0x01070010 rand(0, 0x1070020, 0, 0x1070000, 0x7ff3aebdee60) = 0x754e7ddd malloc(24) = 0x01070030 rand(0x7ff3aebdee60, 24, 0, 0x1070020, 0x7ff3aebdeec8) = 0x11265233 malloc(24) = 0x01070050 rand(0x7ff3aebdee60, 24, 0, 0x1070040, 0x7ff3aebdeec8) = 0x18799942 malloc(24) = 0x01070070 rand(0x7ff3aebdee60, 24, 0, 0x1070060, 0x7ff3aebdeec8) = 0x214a541e malloc(24) = 0x01070090 rand(0x7ff3aebdee60, 24, 0, 0x1070080, 0x7ff3aebdeec8) = 0x1b6d90f3 malloc(24) = 0x010700b0 rand(0x7ff3aebdee60, 24, 0, 0x10700a0, 0x7ff3aebdeec8) = 0x2e19c419 malloc(24) = 0x010700d0 rand(0x7ff3aebdee60, 24, 0, 0x10700c0, 0x7ff3aebdeec8) = 0x35bc1a99 malloc(24) = 0x010700f0 rand(0x7ff3aebdee60, 24, 0, 0x10700e0, 0x7ff3aebdeec8) = 0x53b8d61b malloc(24) = 0x01070110 rand(0x7ff3aebdee60, 24, 0, 0x1070100, 0x7ff3aebdeec8) = 0x18e0f924 malloc(24) = 0x01070130 rand(0x7ff3aebdee60, 24, 0, 0x1070120, 0x7ff3aebdeec8) = 0x27a51979 --- SIGSEGV (Segmentation fault) --- +++ killed by SIGSEGV +++You can also attach it to a process that's already running:
$ pgrep example 5138 $ ltrace -p 5138Generally, there's quite a bit more than a couple of screenfuls of text generated by this, so it's helpful to use the
-ooption to specify an output file to which to log the calls:$ ltrace -o example.ltrace ./exampleYou can then view this trace in a text editor like Vim, which includes syntax highlighting for
ltraceoutput: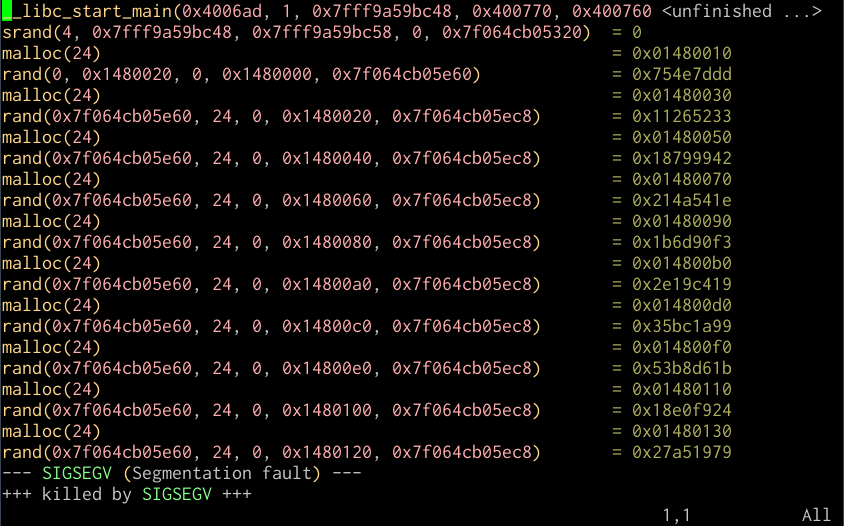
Vim session with ltrace output
I've found
Tracking open files withltracevery useful for debugging problems where I suspect improper linking may be at fault, or the absence of some needed resource in achrootenvironment, since among its output it shows you its search for libraries at dynamic linking time and opening configuration files in/etc, and the use of devices like/dev/randomor/dev/zero.lsofIf you want to view what devices, files, or streams a running process has open, you can do that with
lsof:$ pgrep example 5051 $ lsof -p 5051For example, the first few lines of the
apache2process running on my home server are:# lsof -p 30779 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME apache2 30779 root cwd DIR 8,1 4096 2 / apache2 30779 root rtd DIR 8,1 4096 2 / apache2 30779 root txt REG 8,1 485384 990111 /usr/lib/apache2/mpm-prefork/apache2 apache2 30779 root DEL REG 8,1 1087891 /lib/x86_64-linux-gnu/libgcc_s.so.1 apache2 30779 root mem REG 8,1 35216 1079715 /usr/lib/php5/20090626/pdo_mysql.so ...Interestingly, another way to list the open files for a process is to check the corresponding entry for the process in the dynamic
/procdirectory:# ls -l /proc/30779/fdThis can be very useful in confusing situations with file locks, or identifying whether a process is holding open files that it needn't.
Viewing memory allocation withpmapAs a final debugging tip, you can view the memory allocations for a particular process with
pmap:# pmap 30779 30779: /usr/sbin/apache2 -k start 00007fdb3883e000 84K r-x-- /lib/x86_64-linux-gnu/libgcc_s.so.1 (deleted) 00007fdb38853000 2048K ----- /lib/x86_64-linux-gnu/libgcc_s.so.1 (deleted) 00007fdb38a53000 4K rw--- /lib/x86_64-linux-gnu/libgcc_s.so.1 (deleted) 00007fdb38a54000 4K ----- [ anon ] 00007fdb38a55000 8192K rw--- [ anon ] 00007fdb392e5000 28K r-x-- /usr/lib/php5/20090626/pdo_mysql.so 00007fdb392ec000 2048K ----- /usr/lib/php5/20090626/pdo_mysql.so 00007fdb394ec000 4K r---- /usr/lib/php5/20090626/pdo_mysql.so 00007fdb394ed000 4K rw--- /usr/lib/php5/20090626/pdo_mysql.so ... total 152520KThis will show you what libraries a running process is using, including those in shared memory. The total given at the bottom is a little misleading as for loaded shared libraries, the running process is not necessarily the only one using the memory; determining "actual" memory usage for a given process is a little more in-depth than it might seem with shared libraries added to the picture. Posted in GNU/Linux Tagged backtrace , breakpoint , debugging , file , file handle , gdb , ltrace , memory , process , strace , trace , unix Unix as IDE: Building Posted on February 13, 2012 by Tom Ryder Because compiling projects can be such a complicated and repetitive process, a good IDE provides a means to abstract, simplify, and even automate software builds. Unix and its descendents accomplish this process with a
Makefile, a prescribed recipe in a standard format for generating executable files from source and object files, taking account of changes to only rebuild what's necessary to prevent costly recompilation.One interesting thing to note about
Anatomy of amakeis that while it's generally used for compiled software build automation and has many shortcuts to that effect, it can actually effectively be used for any situation in which it's required to generate one set of files from another. One possible use is to generate web-friendly optimised graphics from source files for deployment for a website; another use is for generating static HTML pages from code, rather than generating pages on the fly. It's on the basis of this more flexible understanding of software "building" that modern takes on the tool like Ruby'srakehave become popular, automating the general tasks for producing and installing code and files of all kinds.MakefileThe general pattern of a
Makefileis a list of variables and a list of targets , and the sources and/or objects used to provide them. Targets may not necessarily be linked binaries; they could also constitute actions to perform using the generated files, such asinstallto instate built files into the system, andcleanto remove built files from the source tree.It's this flexibility of targets that enables
maketo automate any sort of task relevant to assembling a production build of software; not just the typical parsing, preprocessing, compiling proper and linking steps performed by the compiler, but also running tests (make test), compiling documentation source files into one or more appropriate formats, or automating deployment of code into production systems, for example, uploading to a website via agit pushor similar content-tracking method.An example
Makefilefor a simple software project might look something like the below:all: example example: main.o example.o library.o gcc main.o example.o library.o -o example main.o: main.c gcc -c main.c -o main.o example.o: example.c gcc -c example.c -o example.o library.o: library.c gcc -c library.c -o library.o clean: rm *.o example install: example cp example /usr/binThe above isn't the most optimal
Makefilepossible for this project, but it provides a means to build and install a linked binary simply by typingmake. Each target definition contains a list of the dependencies required for the command that follows; this means that the definitions can appear in any order, and the call tomakewill call the relevant commands in the appropriate order.Much of the above is needlessly verbose or repetitive; for example, if an object file is built directly from a single C file of the same name, then we don't need to include the target at all, and
makewill sort things out for us. Similarly, it would make sense to put some of the more repeated calls into variables so that we would not have to change them individually if our choice of compiler or flags changed. A more concise version might look like the following:CC = gcc OBJECTS = main.o example.o library.o BINARY = example all: example example: $(OBJECTS) $(CC) $(OBJECTS) -o $(BINARY) clean: rm -f $(BINARY) $(OBJECTS) install: example cp $(BINARY) /usr/binMore general uses ofmakeIn the interests of automation, however, it's instructive to think of this a bit more generally than just code compilation and linking. An example could be for a simple web project involving deploying PHP to a live webserver. This is not normally a task people associate with the use of
make, but the principles are the same; with the source in place and ready to go, we have certain targets to meet for the build.PHP files don't require compilation, of course, but web assets often do. An example that will be familiar to web developers is the generation of scaled and optimised raster images from vector source files, for deployment to the web. You keep and version your original source file, and when it comes time to deploy, you generate a web-friendly version of it.
Let's assume for this particular project that there's a set of four icons used throughout the site, sized to 64 by 64 pixels. We have the source files to hand in SVG vector format, safely tucked away in version control, and now need to generate the smaller bitmaps for the site, ready for deployment. We could therefore define a target
icons, set the dependencies, and type out the commands to perform. This is where command line tools in Unix really begin to shine in use withMakefilesyntax:icons: create.png read.png update.png delete.png create.png: create.svg convert create.svg create.raw.png && \ pngcrush create.raw.png create.png read.png: read.svg convert read.svg read.raw.png && \ pngcrush read.raw.png read.png update.png: update.svg convert update.svg update.raw.png && \ pngcrush update.raw.png update.png delete.png: delete.svg convert delete.svg delete.raw.png && \ pngcrush delete.raw.png delete.pngWith the above done, typing
make iconswill go through each of the source icons files in a Bash loop, convert them from SVG to PNG using ImageMagick'sconvert, and optimise them withpngcrush, to produce images ready for upload.A similar approach can be used for generating help files in various forms, for example, generating HTML files from Markdown source:
docs: README.html credits.html README.html: README.md markdown README.md > README.html credits.html: credits.md markdown credits.md > credits.htmlAnd perhaps finally deploying a website with
git push web, but only after the icons are rasterized and the documents converted:deploy: icons docs git push webFor a more compact and abstract formula for turning a file of one suffix into another, you can use the
.SUFFIXESpragma to define these using special symbols. The code for converting icons could look like this; in this case,$<refers to the source file,$*to the filename with no extension, and$@to the target.icons: create.png read.png update.png delete.png .SUFFIXES: .svg .png .svg.png: convert $< $*.raw.png && \ pngcrush $*.raw.png $@Tools for building aMakefileA variety of tools exist in the GNU Autotools toolchain for the construction of
configurescripts andmakefiles for larger software projects at a higher level, in particularautoconfandautomake. The use of these tools allows generatingconfigurescripts andmakefiles covering very large source bases, reducing the necessity of building otherwise extensive makefiles manually, and automating steps taken to ensure the source remains compatible and compilable on a variety of operating systems.Covering this complex process would be a series of posts in its own right, and is out of scope of this survey.
Thanks to user samwyse for the
.SUFFIXESsuggestion in the comments. Posted in GNU/Linux Tagged build , clean , dependency , generate , install , make , makefile , target , unix Unix as IDE: Compiling Posted on February 12, 2012 by Tom Ryder There are a lot of tools available for compiling and interpreting code on the Unix platform, and they tend to be used in different ways. However, conceptually many of the steps are the same. Here I'll discuss compiling C code withgccfrom the GNU Compiler Collection, and briefly the use ofperlas an example of an interpreter. GCCGCC is a very mature GPL-licensed collection of compilers, perhaps best-known for working with C and C++ programs. Its free software license and near ubiquity on free Unix-like systems like GNU/Linux and BSD has made it enduringly popular for these purposes, though more modern alternatives are available in compilers using the LLVM infrastructure, such as Clang .
The frontend binaries for GNU Compiler Collection are best thought of less as a set of complete compilers in their own right, and more as drivers for a set of discrete programming tools, performing parsing, compiling, and linking, among other steps. This means that while you can use GCC with a relatively simple command line to compile straight from C sources to a working binary, you can also inspect in more detail the steps it takes along the way and tweak it accordingly.
I won't be discussing the use of
Compiling and assembling object codemakefiles here, though you'll almost certainly be wanting them for any C project of more than one file; that will be discussed in the next article on build automation tools.You can compile object code from a C source file like so:
$ gcc -c example.c -o example.oAssuming it's a valid C program, this will generate an unlinked binary object file called
example.oin the current directory, or tell you the reasons it can't. You can inspect its assembler contents with theobjdumptool:$ objdump -D example.oAlternatively, you can get
gccto output the appropriate assembly code for the object directly with the-Sparameter:$ gcc -c -S example.c -o example.sThis kind of assembly output can be particularly instructive, or at least interesting, when printed inline with the source code itself, which you can do with:
$ gcc -c -g -Wa,-a,-ad example.c > example.lstPreprocessorThe C preprocessor
cppis generally used to include header files and define macros, among other things. It's a normal part ofgcccompilation, but you can view the C code it generates by invokingcppdirectly:$ cpp example.cThis will print out the complete code as it would be compiled, with includes and relevant macros applied.
Linking objectsOne or more objects can be linked into appropriate binaries like so:
$ gcc example.o -o exampleIn this example, GCC is not doing much more than abstracting a call to
Compiling, assembling, and linkingld, the GNU linker. The command produces an executable binary calledexample.All of the above can be done in one step with:
$ gcc example.c -o exampleThis is a little simpler, but compiling objects independently turns out to have some practical performance benefits in not recompiling code unnecessarily, which I'll discuss in the next article.
Including and linkingC files and headers can be explicitly included in a compilation call with the
-Iparameter:$ gcc -I/usr/include/somelib.h example.c -o exampleSimilarly, if the code needs to be dynamically linked against a compiled system library available in common locations like
/libor/usr/lib, such asncurses, that can be included with the-lparameter:$ gcc -lncurses example.c -o exampleIf you have a lot of necessary inclusions and links in your compilation process, it makes sense to put this into environment variables:
$ export CFLAGS=-I/usr/include/somelib.h $ export CLIBS=-lncurses $ gcc $CFLAGS $CLIBS example.c -o exampleThis very common step is another thing that a
Compilation planMakefileis designed to abstract away for you.To inspect in more detail what
gccis doing with any call, you can add the-vswitch to prompt it to print its compilation plan on the standard error stream:$ gcc -v -c example.c -o example.oIf you don't want it to actually generate object files or linked binaries, it's sometimes tidier to use
-###instead:$ gcc -### -c example.c -o example.oThis is mostly instructive to see what steps the
More verbose error checkinggccbinary is abstracting away for you, but in specific cases it can be useful to identify steps the compiler is taking that you may not necessarily want it to.You can add the
-Walland/or-pedanticoptions to thegcccall to prompt it to warn you about things that may not necessarily be errors, but could be:$ gcc -Wall -pedantic -c example.c -o example.oThis is good for including in your
Profiling compilation timeMakefileor in yourmakeprgdefinition in Vim, as it works well with the quickfix window discussed in the previous article and will enable you to write more readable, compatible, and less error-prone code as it warns you more extensively about errors.You can pass the flag
-timetogccto generate output showing how long each step is taking:$ gcc -time -c example.c -o example.oOptimisationYou can pass generic optimisation options to
gccto make it attempt to build more efficient object files and linked binaries, at the expense of compilation time. I find-O2is usually a happy medium for code going into production:
gcc -O1gcc -O2gcc -O3Like any other Bash command, all of this can be called from within Vim by:
:!gcc % -o exampleInterpretersThe approach to interpreted code on Unix-like systems is very different. In these examples I'll use Perl, but most of these principles will be applicable to interpreted Python or Ruby code, for example.
InlineYou can run a string of Perl code directly into the interpreter in any one of the following ways, in this case printing the single line "Hello, world." to the screen, with a linebreak following. The first one is perhaps the tidiest and most standard way to work with Perl; the second uses a heredoc string, and the third a classic Unix shell pipe.
$ perl -e 'print "Hello world.\n";' $ perl <<<'print "Hello world.\n";' $ echo 'print "Hello world.\n";' | perlOf course, it's more typical to keep the code in a file, which can be run directly:
$ perl hello.plIn either case, you can check the syntax of the code without actually running it with the
-cswitch:$ perl -c hello.plBut to use the script as a logical binary , so you can invoke it directly without knowing or caring what the script is, you can add a special first line to the file called the "shebang" that does some magic to specify the interpreter through which the file should be run.
#!/usr/bin/env perl print "Hello, world.\n";The script then needs to be made executable with a
chmodcall. It's also good practice to rename it to remove the extension, since it is now taking the shape of a logic binary:$ mv hello{.pl,} $ chmod +x helloAnd can thereafter be invoked directly, as if it were a compiled binary:
$ ./helloThis works so transparently that many of the common utilities on modern GNU/Linux systems, such as the
adduserfrontend touseradd, are actually Perl or even Python scripts.In the next post, I'll describe the use of
makefor defining and automating building projects in a manner comparable to IDEs, with a nod to newer takes on the same idea with Ruby'srake. Posted in GNU/Linux Tagged assembler , compiler , gcc , interpreter , linker , perl , python , ruby , unix Unix as IDE: Editing Posted on February 11, 2012 by Tom Ryder The text editor is the core tool for any programmer, which is why choice of editor evokes such tongue-in-cheek zealotry in debate among programmers. Unix is the operating system most strongly linked with two enduring favourites, Emacs and Vi, and their modern versions in GNU Emacs and Vim, two editors with very different editing philosophies but comparable power.Being a Vim heretic myself, here I'll discuss the indispensable features of Vim for programming, and in particular the use of shell tools called from within Vim to complement the editor's built-in functionality. Some of the principles discussed here will be applicable to those using Emacs as well, but probably not for underpowered editors like Nano.
This will be a very general survey, as Vim's toolset for programmers is enormous , and it'll still end up being quite long. I'll focus on the essentials and the things I feel are most helpful, and try to provide links to articles with a more comprehensive treatment of the topic. Don't forget that Vim's
Filetype detection:helphas surprised many people new to the editor with its high quality and usefulness.Vim has built-in settings to adjust its behaviour, in particular its syntax highlighting, based on the filetype being loaded, which it happily detects and generally does a good job at doing so. In particular, this allows you to set an indenting style conformant with the way a particular language is usually written. This should be one of the first things in your
.vimrcfile.if has("autocmd") filetype on filetype indent on filetype plugin on endifSyntax highlightingEven if you're just working with a 16-color terminal, just include the following in your
.vimrcif you're not already:syntax onThe colorschemes with a default 16-color terminal are not pretty largely by necessity, but they do the job, and for most languages syntax definition files are available that work very well. There's a tremendous array of colorschemes available, and it's not hard to tweak them to suit or even to write your own. Using a 256-color terminal or gVim will give you more options. Good syntax highlighting files will show you definite syntax errors with a glaring red background.
Line numberingTo turn line numbers on if you use them a lot in your traditional IDE:
set numberYou might like to try this as well, if you have at least Vim 7.3 and are keen to try numbering lines relative to the current line rather than absolutely:
set relativenumberTags filesVim works very well with the output from the
ctagsutility. This allows you to search quickly for all uses of a particular identifier throughout the project, or to navigate straight to the declaration of a variable from one of its uses, regardless of whether it's in the same file. For large C projects in multiple files this can save huge amounts of otherwise wasted time, and is probably Vim's best answer to similar features in mainstream IDEs.You can run
:!ctags -Ron the root directory of projects in many popular languages to generate atagsfile filled with definitions and locations for identifiers throughout your project. Once atagsfile for your project is available, you can search for uses of an appropriate tag throughout the project like so::tag someClassThe commands
Calling external programs:tnand:tpwill allow you to iterate through successive uses of the tag elsewhere in the project. The built-in tags functionality for this already covers most of the bases you'll probably need, but for features such as a tag list window, you could try installing the very popular Taglist plugin . Tim Pope's Unimpaired plugin also contains a couple of useful relevant mappings.Until 2017, there were three major methods of calling external programs during a Vim session:
:!<command>-- Useful for issuing commands from within a Vim context particularly in cases where you intend to record output in a buffer.:shell-- Drop to a shell as a subprocess of Vim. Good for interactive commands.- Ctrl-Z -- Suspend Vim and issue commands from the shell that called it.
Since 2017, Vim 8.x now includes a
Lint programs and syntax checkers:terminalcommand to bring up a terminal emulator buffer in a window. This seems to work better than previous plugin-based attempts at doing this, such as Conque . For the moment I still strongly recommend using one of the older methods, all of which also work in othervi-type editors.Checking syntax or compiling with an external program call (e.g.
perl -c,gcc) is one of the calls that's good to make from within the editor using:!commands. If you were editing a Perl file, you could run this like so::!perl -c % /home/tom/project/test.pl syntax OK Press Enter or type command to continueThe
%symbol is shorthand for the file loaded in the current buffer. Running this prints the output of the command, if any, below the command line. If you wanted to call this check often, you could perhaps map it as a command, or even a key combination in your.vimrcfile. In this case, we define a command:PerlLintwhich can be called from normal mode with\l:command PerlLint !perl -c % nnoremap <leader>l :PerlLint<CR>For a lot of languages there's an even better way to do this, though, which allows us to capitalise on Vim's built-in quickfix window. We can do this by setting an appropriate
makeprgfor the filetype, in this case including a module that provides us with output that Vim can use for its quicklist, and a definition for its two formats::set makeprg=perl\ -c\ -MVi::QuickFix\ % :set errorformat+=%m\ at\ %f\ line\ %l\. :set errorformat+=%m\ at\ %f\ line\ %lYou may need to install this module first via CPAN, or the Debian package
libvi-quickfix-perl. This done, you can type:makeafter saving the file to check its syntax, and if errors are found, you can open the quicklist window with:copento inspect the errors, and:cnand:cpto jump to them within the buffer.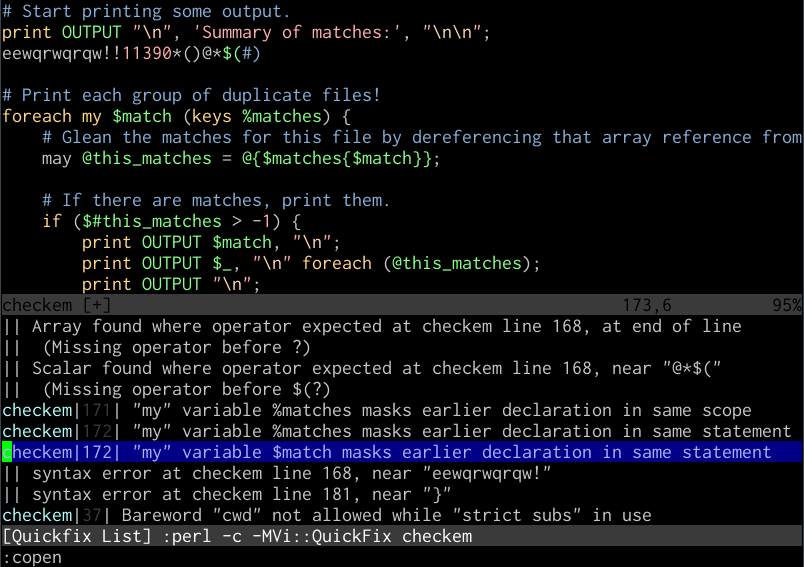
Vim quickfix working on a Perl file
This also works for output from
Reading output from other commandsgcc, and pretty much any other compiler syntax checker that you might want to use that includes filenames, line numbers, and error strings in its error output. It's even possible to do this with web-focused languages like PHP , and for tools like JSLint for JavaScript . There's also an excellent plugin named Syntastic that does something similar.You can use
:r!to call commands and paste their output directly into the buffer with which you're working. For example, to pull a quick directory listing for the current folder into the buffer, you could type::r!lsThis doesn't just work for commands, of course; you can simply read in other files this way with just
:r, like public keys or your own custom boilerplate::r ~/.ssh/id_rsa.pub :r ~/dev/perl/boilerplate/copyright.plFiltering output through other commandsYou can extend this to actually filter text in the buffer through external commands, perhaps selected by a range or visual mode, and replace it with the command's output. While Vim's visual block mode is great for working with columnar data, it's very often helpful to bust out tools like
column,cut,sort, orawk.For example, you could sort the entire file in reverse by the second column by typing:
:%!sort -k2,2rYou could print only the third column of some selected text where the line matches the pattern
/vim/with::'<,'>!awk '/vim/ {print $3}'You could arrange keywords from lines 1 to 10 in nicely formatted columns like:
:1,10!column -tReally any kind of text filter or command can be manipulated like this in Vim, a simple interoperability feature that expands what the editor can do by an order of magnitude. It effectively makes the Vim buffer into a text stream, which is a language that all of these classic tools speak.
There is a lot more detail on this in my "Shell from Vi" post.
Built-in alternativesIt's worth noting that for really common operations like sorting and searching, Vim has built-in methods in
Diffing:sortand:grep, which can be helpful if you're stuck using Vim on Windows, but don't have nearly the adaptability of shell calls.Vim has a diffing mode,
vimdiff, which allows you to not only view the differences between different versions of a file, but also to resolve conflicts via a three-way merge and to replace differences to and fro with commands like:diffputand:diffgetfor ranges of text. You can callvimdifffrom the command line directly with at least two files to compare like so:$ vimdiff file-v1.c file-v2.c
Vim diffing a .vimrc file Version control
You can call version control methods directly from within Vim, which is probably all you need most of the time. It's useful to remember here that
%is always a shortcut for the buffer's current file::!svn status :!svn add % :!git commit -aRecently a clear winner for Git functionality with Vim has come up with Tim Pope's Fugitive , which I highly recommend to anyone doing Git development with Vim. There'll be a more comprehensive treatment of version control's basis and history in Unix in Part 7 of this series.
The differencePart of the reason Vim is thought of as a toy or relic by a lot of programmers used to GUI-based IDEs is its being seen as just a tool for editing files on servers, rather than a very capable editing component for the shell in its own right. Its own built-in features being so composable with external tools on Unix-friendly systems makes it into a text editing powerhouse that sometimes surprises even experienced users.
Oct 03, 2006
GDB, the GNU Project Debugger, has a macro capability that is sophisticated and allows you to personalize and customize GDB to have just the tools you need. The mechanism for providing help documentation on your customized commands makes it an easy tool to share with others as well.The previous article on this topic, "Fun with strace and GDB," covered the basics of using these tools to explore your system and attach to programs that are already running to see what they were doing. This article presses on to customize the debugger to make the experience more personal and efficient.
When GDB, the GNU Project Debugger, starts up, it looks for a file in the current user's home directory called .gdbinit; if the file exists, GDB executes all the commands in the file. Normally, this file is used for simple configuration commands, such as setting the default assembler format desired (Intel® or Motorola) or default radix to display input and output data (decimal or hexadecimal). It can also read a macro-coding language that allows m
GDB was first written by Richard Stallman in 1986 as part of his GNU system, after his GNU Emacs was "reasonably stable".[3] GDB is free software released under the GNU General Public License (GPL). It was modeled after the DBX debugger, which came with Berkeley Unix distributions.[3]
From 1990 to 1993 it was maintained by John Gilmore while he worked for Cygnus Solutions[citation needed]. Now it is maintained by the GDB Steering Committee which is appointed by the Free Software Foundation.[4]
[edit] Release history2012 August 17: GDB 7.5 2012 April 26: GDB 7.4.1 2012 January 24: GDB 7.4 2011 July 26: GDB 7.3[5] 2010 September 2: GDB 7.2 2010 March 18: GDB 7.1 2009 October 6: GDB 7.0 2008 March 27: GDB 6.8 2003 October 3: GDB 6.0 [edit] Technical details[edit] FeaturesGDB offers extensive facilities for tracing and altering the execution of computer programs. The user can monitor and modify the values of programs' internal variables, and even call functions independently of the program's normal behavior.
GDB target processors (as of 2003) include: Alpha, ARM, AVR, H8/300, System/370, System 390, X86 and its 64-bit extension X86-64, IA-64 "Itanium", Motorola 68000, MIPS, PA-RISC, PowerPC, SuperH, SPARC, and VAX. Lesser-known target processors supported in the standard release have included A29K, ARC, ETRAX CRIS, D10V, D30V, FR-30, FR-V, Intel i960, 68HC11, Motorola 88000, MCORE, MN10200, MN10300, NS32K, Stormy16, and Z8000. (Newer releases will likely not support some of these.) GDB has compiled-in simulators for even lesser-known target processors such like M32R or V850.[6]
GDB is still actively developed. As of version 7.0 new features include support for Python scripting.[7] Since version 7.0, support for "reversible debugging" - allowing a debugging session to step backward, much like rewinding a crashed program to see what happened - is available.[8]
[edit] Remote debuggingGDB offers a 'remote' mode often used when debugging embedded systems. Remote operation is when GDB runs on one machine and the program being debugged runs on another. GDB can communicate to the remote 'stub' which understands GDB protocol via Serial or TCP/IP.[9] A stub program can be created by linking to the appropriate stub files provided with GDB, which implement the target side of the communication protocol.[10] Alternatively, gdbserver can be used to remotely debug the program without needing to change it in any way.
The same mode is also used by KGDB for debugging a running Linux kernel on the source level with gdb. With KGDB, kernel developers can debug a kernel in much the same way as they debug application programs. It makes it possible to place breakpoints in kernel code, step through the code and observe variables. On architectures where hardware debugging registers are available, watchpoints can be set which trigger breakpoints when specified memory addresses are executed or accessed. KGDB requires an additional machine which is connected to the machine to be debugged using a serial cable or ethernet. On FreeBSD, it is also possible to debug using Firewire direct memory access (DMA)[citation needed].
[edit] Graphical user interfaceThe debugger does not contain its own graphical user interface, and defaults to a command-line interface. Several front-ends have been built for it, such as Xxgdb, Data Display Debugger (DDD), Nemiver, KDbg, Xcode debugger, GDBtk/Insight and the HP Wildebeest Debugger GUI (WDB GUI). IDEs such as Codelite, Code::Blocks, Dev-C++, GNAT Programming Studio (GPS), KDevelop, Qt Creator, MonoDevelop, Eclipse, NetBeans and VisualStudio (see VS AddIn Gallery) can interface with GDB. GNU Emacs has a "GUD mode" and several tools for VIM exist[citation needed]. These offer facilities similar to debuggers found in IDEs.
Some other debugging tools have been designed to work with GDB, such as memory leak detectors.
[edit] Examples of commandsgdb program debug "program" (from the shell) run -v run the loaded program with the parameters bt backtrace (in case the program crashed) info registers dump all registers disass $pc-32, $pc+32 disassemble
[edit] An example sessionConsider the following source-code written in C:
#include <stdio.h> #include <stdlib.h> #include <string.h>
size_t foo_len (const char *s) { return strlen (s); }
int main (int argc, char *argv[]) { const char *a = NULL;
printf ("size of a = %d\n", foo_len (a));
exit (0); } Using the GCC compiler on GNU/Linux, the code above must be compiled using the -g flag in order to include appropriate debug information on the binary generated, thus making it possible to inspect it using GDB. Assuming that the file containing the code above is named example.c, the command for the compilation could be:
gcc example.c -g -o example And the binary can now be run:
# ./example Segmentation fault Since the example code, when executed, generates a segmentation fault, GDB can be used to inspect the problem.
# gdb ./example GNU gdb (GDB) Fedora (7.3.50.20110722-13.fc16) Copyright (C) 2011 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "x86_64-redhat-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /path/example...done. (gdb) run Starting program: /path/example
Program received signal SIGSEGV, Segmentation fault. 0x0000000000400527 in foo_len (s=0x0) at example.c:8 8 return strlen (s); (gdb) print s $1 = 0x0 The problem is present in line 8, and occurs when calling the function strlen (because its argument, s, is NULL).
Depending on the implementation of strlen (in-line or not), the output can be different, e.g.:
# gdb ./example GNU gdb (GDB) 7.3.1 Copyright (C) 2011 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "i686-pc-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /tmp/gdb/example...done.
(gdb) run Starting program: /tmp/gdb/example
Program received signal SIGSEGV, Segmentation fault. 0xb7ee94f3 in strlen () from /lib/i686/cmov/libc.so.6
(gdb) bt #0 0xb7ee94f3 in strlen () from /lib/i686/cmov/libc.so.6 #1 0x08048435 in foo_len (s=0x0) at example.c:8 #2 0x0804845a in main (argc=<optimized out>, argv=<optimized out>) at example.c:16 To fix the problem, the variable a (in the function main) must contain a valid string. Here is a fixed version of the code:
#include <stdio.h> #include <stdlib.h> #include <string.h>
size_t foo_len (const char *s) { return strlen (s); }
int main (int argc, char *argv[]) { const char *a = "This is a test string";
printf ("size of a = %d\n", foo_len (a));
exit (0); } Recompiling and running the executable again inside GDB now gives a correct result:
GNU gdb (GDB) Fedora (7.3.50.20110722-13.fc16) Copyright (C) 2011 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "x86_64-redhat-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /path/example...done. (gdb) run Starting program: /path/example size of a = 21 [Inferior 1 (process 14290) exited normally] GDB prints the output of printf in the screen, and then informs the user that the program exited normally.
[edit] See also Free software portal Computer programming portal Affinic Debugger GUI Binary File Descriptor library (libbfd) dbx ddd, a GUI for gdb and other debuggers gdbserver [edit] References1.^ "GDB Documentation - Supported Languages". http://sourceware.org/gdb/current/onlinedocs/gdb/Supported-Languages.html#Supported-Languages. Retrieved 2011-11-28. 2.^ "GDB Documentation - Summary". http://sourceware.org/gdb/current/onlinedocs/gdb/Summary.html#Summary. Retrieved 2011-11-28. 3.^ a b "Richard Stallman lecture at the Royal Institute of Technology, Sweden (1986-10-30)". http://www.gnu.org/philosophy/stallman-kth.html. Retrieved 2006-09-21. "Then after GNU Emacs was reasonably stable, which took all in all about a year and a half, I started getting back to other parts of the system. I developed a debugger which I called GDB which is a symbolic debugger for C code, which recently entered distribution. Now this debugger is to a large extent in the spirit of DBX, which is a debugger that comes with Berkeley Unix." 4.^ "GDB Steering Committee". http://www.gnu.org/software/gdb/committee/. Retrieved 2008-05-11. 5.^ http://www.gnu.org/software/gdb/news/ 6.^ "GDB Documentation - Summary - Contributors". http://sourceware.org/gdb/current/onlinedocs/gdb/Contributors.html#Contributors. Retrieved 2011-12-01. 7.^ "GDB 7.0 Release Notes". http://sourceware.org/gdb/wiki/GDB_7.0_Release. Retrieved 2011-11-28. 8.^ "Reverse Debugging with GDB". http://www.sourceware.org/gdb/wiki/ReverseDebug. Retrieved 2012-6-28. 9.^ Howto: GDB Remote Serial Protocol: Writing a RSP Server 10.^ Implementing a remote stub [edit] External linksOfficial website KGDB: Linux Kernel Source Level Debugger MyGDB: GDB Frontend web site which is In Korean language A Visual Studio plugin for debugging with GDB [edit] DocumentationRichard M. Stallman, Roland Pesch, Stan Shebs, et al., Debugging with GDB (Free Software Foundation, 2011) ISBN 978-0-9831592-3-0 GDB Internals [edit] TutorialsPeter Jay Salzman's GDB guide: Using The GNU GDB Debugger (Peter Jay Salzman) RMS's gdb Tutorial (Ryan Schmidt
ore powerful customizations. The language follows this basic format:
define <command> <code> end document <command> <help text> endThe command is known as a user command. All other standard GDB commands can be combined with flow-control instructions and passed parameters to create a language that allows you to customize the behavior of the debugger for the specific application being debugged.
Start simple: Clear the screen
It's always good to start simple and build up from there. Start the xterm, fire up your favorite editor, and let's begin creating a useful .gdbinit file! The output from debuggers can be messy and, as a matter of personal preference, many people like to be able to clear the screen when working with any tool that has the potential for creating cluttering. GDB has no built-in command for clearing the screen, but it can call shell functions; the following code steps outside the debugger to clear the xterm console with the cls command:
define cls shell clear end document cls Clears the screen with a simple command. endThe upper portion of the definition, bounded by the define ... end verbs, frames the code that is executed when the command is invoked.
The lower portion of the definition, bounded by document ... end, is used by the GDB command interpreter to display help text associated with the cls command when you type help cls.
After you type the code into the .gdbinit file, fire up GDB and enter the cls command. Your screen clears, and all you see is the GDB prompt. Your journey into GDB customization has begun!
The importance of documentation
If you enter the help user command, you see a summary of all the user commands you've entered in the .gdbinit file. The designers of the .gdbinit user-defined commands have provided an important feature that you shouldn't ignore when you're writing your own commands: the document ... end clause. Maintaining functional documentation of how commands work becomes critical as the number of these commands increase.
You might have already experienced the problem. Suppose you wrote some code from a few years ago; then, when you revisit it, perhaps to fix a bug or modify it by adding a new feature, you realize that you're having a hard time understanding your own code. Good programmers make it a habit to keep code short, simple, and well-documented so that it's maintainable.
What's true for programming code in general is true for debugger code. Keeping careful notes and well-documented code will serve you well as you work your way through this most rewarding of careers.
Community uses for GDB
Human beings learn new things many ways, including by studying what others have done. Budding automotive engineers start by opening the hood of their first car, pulling out their tools, and removing parts to clean and study. Such an exercise lets them keep a clean machine while learning how the automobile engine works.
Budding computer scientists are no different in that they want to see just how programs work -- how they interact with dynamic libraries and the native operating system. The tool for seeing how these things work is the debugger. Computer programming is a complex activity, and by being able to interact with a community of like-minded people, asking questions and getting answers, new computer scientists can satisfy their need for knowledge.
In the global programming community, there are always a healthy number of people who hunger and thirst for knowledge. They aren't content with just running programs on their computers -- they want to know more. They want to know how those programs run, and they enjoy exploring the functionality of their systems with the best tool available for the purpose: the debugger. By reverse engineering, a way of learning how programs work by running them under a debugger and keeping careful notes of how they do what they do, you can learn a lot from what the authors of the program being studied have done. Many low-level details involved in programming are undocumented; the only way to learn about them is to see them in action.
Reverse engineering has an undeserved reputation as a black art practiced only by hackers and criminals intent on breaking copy-protection systems and writing worms and viruses to inflict harm on the world of computers. Although there are such people, the vast majority of those who study how programs work, using debuggers and reverse engineering, are the present and future software engineers who want and need to know how these things work. They have formed online communities to share their knowledge and discoveries; discouraging this activity is destructive and retards the future progress of computer science.
Many of the user functions defined in this article come from such communities of hungry knowledge seekers. If you want to know more about them, you're encouraged to study the Web sites referenced in the Resources section of this document.
Breakpoint aliases
It's a well-known fact that many of the GDB commands are too verbose. Even though they can be abbreviated, the GDB macro language allows for even greater simplifications. Commands, such as info breakpoints, can be made as simple as bpl. Listing 1 shows a great set of such simple and highly useful breakpoint alias user commands to edit into your growing .gdbinit file.
Listing 1: Breakpoint alias commandsdefine bpl info breakpoints end document bpl List breakpoints end define bp set $SHOW_CONTEXT = 1 break * $arg0 end document bp Set a breakpoint on address Usage: bp addr end define bpc clear $arg0 end document bpc Clear breakpoint at function/address Usage: bpc addr end define bpe enable $arg0 end document bpe Enable breakpoint # Usage: bpe num end define bpd disable $arg0 end document bpd Disable breakpoint # Usage: bpd num end define bpt set $SHOW_CONTEXT = 1 tbreak $arg0 end document bpt Set a temporary breakpoint on address Usage: bpt addr end define bpm set $SHOW_CONTEXT = 1 awatch $arg0 end document bpm Set a read/write breakpoint on address Usage: bpm addr endOnce you get used to using breakpoint alias commands, your debugging sessions become more rewarding; these commands greatly increase the debugger's effectiveness, because you can accomplish more with less effort.
Displaying process information
The GDB user-defined commands can be called by other user-defined commands, leading to greater effectiveness for them all. This is the incremental nature of programming languages -- writing lower-level functions that are called by progressively higher-level functions until the tools conveniently do what you want them to do with minimal effort on your part. The next set of GDB definitions to incorporate into your .gdbinit file display useful process information when they're invoked, as shown in Listing 2 .
Listing 2: Process information commandsdefine argv show args end document argv Print program arguments end define stack info stack end document stack Print call stack end define frame info frame info args info locals end document
Why waste huge amounts of time debugging? Do yourself a favor and learn to debug like a professional. In this Web page Prof. Norman Matloff has some resources which hopefully will be useful to you in that regard.
First, there is Norm Matloff's introduction to the art of debugging and gdb. The first part of that document lays out a general strategy for debugging, and then illustrates the strategy using the gdb debugging tool.
The other resource available here is information by Dr. Matloff on ddd, a graphical front end to gdb. Note that ddd is available on CSIF machines in the directory /altpkg/ddd, and on Linux sites in the directory devel/debuggers/ddd.
Here is documentation on ddd:
- The ddd home page. This includes sample pictures of ddd in action, the ddd source files (and some binaries), a list of reviews of ddd and even a list of comapnies where ddd is used.
- The mini-manual on ddd by Norm Matloff. This is a brief introduction which should be enough to get you going.
- If you want to learn more advanced features, see the ddd man page , which seems to be missing on the CSIF machines.
ltrace is a library call tracer, i.e. a debugging tool which prints out a trace of all the dynamic library calls made by another process/program. It also displays system calls, as well as `strace'. The program to be traced need not be recompiled for this, so you can use it on binaries for which you don't have the source handy.
Version 0.3.6 adds support for Linux/ARM and Linux/m68k machines.
kdbg 0.2.3KDbg is a graphical user interface to gdb, the GNU debugger. It provides an intuitive interface for setting breakpoints, inspecting variables, and stepping through code.
DDD 3.0.91The Data Display Debugger (DDD) is a common graphical user interface for GDB, DBX, and XDB, the popular UNIX debuggers. Besides ``classical'' front-end features such as viewing source texts, DDD provides a graphical data display, where data structures are displayed as graphs. A simple mouse click dereferences pointers or views structure contents, updated each time the program stops. Using DDD, you can reason about your application by viewing its data, not just by viewing it execute lines of source code.
This is the second beta version for 3.1. It fixes all the bugs reported for the first one (3.0.90).
Google matched content |
GDB Tutorial - a shorter, more command explanatory gdb tutorial than the one above !!!NEW!!!
GDB Internals - Table of Contents
GDB The GNU Debugger -- main page from cygnos
GDB FTP directory -- from cygnus -- the lkatest version is there
Debugging with GDB - Table of Contents
Debugging with GDU - Table of Contents
Doug Rohde ``An introduction to using gdb under Emacs''
GNU Emacs Manual - Debugger Operation
Society
Groupthink : Two Party System as Polyarchy : Corruption of Regulators : Bureaucracies : Understanding Micromanagers and Control Freaks : Toxic Managers : Harvard Mafia : Diplomatic Communication : Surviving a Bad Performance Review : Insufficient Retirement Funds as Immanent Problem of Neoliberal Regime : PseudoScience : Who Rules America : Neoliberalism : The Iron Law of Oligarchy : Libertarian Philosophy
Quotes
War and Peace : Skeptical Finance : John Kenneth Galbraith :Talleyrand : Oscar Wilde : Otto Von Bismarck : Keynes : George Carlin : Skeptics : Propaganda : SE quotes : Language Design and Programming Quotes : Random IT-related quotes : Somerset Maugham : Marcus Aurelius : Kurt Vonnegut : Eric Hoffer : Winston Churchill : Napoleon Bonaparte : Ambrose Bierce : Bernard Shaw : Mark Twain Quotes
Bulletin:
Vol 25, No.12 (December, 2013) Rational Fools vs. Efficient Crooks The efficient markets hypothesis : Political Skeptic Bulletin, 2013 : Unemployment Bulletin, 2010 : Vol 23, No.10 (October, 2011) An observation about corporate security departments : Slightly Skeptical Euromaydan Chronicles, June 2014 : Greenspan legacy bulletin, 2008 : Vol 25, No.10 (October, 2013) Cryptolocker Trojan (Win32/Crilock.A) : Vol 25, No.08 (August, 2013) Cloud providers as intelligence collection hubs : Financial Humor Bulletin, 2010 : Inequality Bulletin, 2009 : Financial Humor Bulletin, 2008 : Copyleft Problems Bulletin, 2004 : Financial Humor Bulletin, 2011 : Energy Bulletin, 2010 : Malware Protection Bulletin, 2010 : Vol 26, No.1 (January, 2013) Object-Oriented Cult : Political Skeptic Bulletin, 2011 : Vol 23, No.11 (November, 2011) Softpanorama classification of sysadmin horror stories : Vol 25, No.05 (May, 2013) Corporate bullshit as a communication method : Vol 25, No.06 (June, 2013) A Note on the Relationship of Brooks Law and Conway Law
History:
Fifty glorious years (1950-2000): the triumph of the US computer engineering : Donald Knuth : TAoCP and its Influence of Computer Science : Richard Stallman : Linus Torvalds : Larry Wall : John K. Ousterhout : CTSS : Multix OS Unix History : Unix shell history : VI editor : History of pipes concept : Solaris : MS DOS : Programming Languages History : PL/1 : Simula 67 : C : History of GCC development : Scripting Languages : Perl history : OS History : Mail : DNS : SSH : CPU Instruction Sets : SPARC systems 1987-2006 : Norton Commander : Norton Utilities : Norton Ghost : Frontpage history : Malware Defense History : GNU Screen : OSS early history
Classic books:
The Peter Principle : Parkinson Law : 1984 : The Mythical Man-Month : How to Solve It by George Polya : The Art of Computer Programming : The Elements of Programming Style : The Unix Hater’s Handbook : The Jargon file : The True Believer : Programming Pearls : The Good Soldier Svejk : The Power Elite
Most popular humor pages:
Manifest of the Softpanorama IT Slacker Society : Ten Commandments of the IT Slackers Society : Computer Humor Collection : BSD Logo Story : The Cuckoo's Egg : IT Slang : C++ Humor : ARE YOU A BBS ADDICT? : The Perl Purity Test : Object oriented programmers of all nations : Financial Humor : Financial Humor Bulletin, 2008 : Financial Humor Bulletin, 2010 : The Most Comprehensive Collection of Editor-related Humor : Programming Language Humor : Goldman Sachs related humor : Greenspan humor : C Humor : Scripting Humor : Real Programmers Humor : Web Humor : GPL-related Humor : OFM Humor : Politically Incorrect Humor : IDS Humor : "Linux Sucks" Humor : Russian Musical Humor : Best Russian Programmer Humor : Microsoft plans to buy Catholic Church : Richard Stallman Related Humor : Admin Humor : Perl-related Humor : Linus Torvalds Related humor : PseudoScience Related Humor : Networking Humor : Shell Humor : Financial Humor Bulletin, 2011 : Financial Humor Bulletin, 2012 : Financial Humor Bulletin, 2013 : Java Humor : Software Engineering Humor : Sun Solaris Related Humor : Education Humor : IBM Humor : Assembler-related Humor : VIM Humor : Computer Viruses Humor : Bright tomorrow is rescheduled to a day after tomorrow : Classic Computer Humor
The Last but not Least Technology is dominated by two types of people: those who understand what they do not manage and those who manage what they do not understand ~Archibald Putt. Ph.D
Copyright © 1996-2021 by Softpanorama Society. www.softpanorama.org was initially created as a service to the (now defunct) UN Sustainable Development Networking Programme (SDNP) without any remuneration. This document is an industrial compilation designed and created exclusively for educational use and is distributed under the Softpanorama Content License. Original materials copyright belong to respective owners. Quotes are made for educational purposes only in compliance with the fair use doctrine.
FAIR USE NOTICE This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available to advance understanding of computer science, IT technology, economic, scientific, and social issues. We believe this constitutes a 'fair use' of any such copyrighted material as provided by section 107 of the US Copyright Law according to which such material can be distributed without profit exclusively for research and educational purposes.
This is a Spartan WHYFF (We Help You For Free) site written by people for whom English is not a native language. Grammar and spelling errors should be expected. The site contain some broken links as it develops like a living tree...
|
|
You can use PayPal to to buy a cup of coffee for authors of this site |
Disclaimer:
The statements, views and opinions presented on this web page are those of the author (or referenced source) and are not endorsed by, nor do they necessarily reflect, the opinions of the Softpanorama society. We do not warrant the correctness of the information provided or its fitness for any purpose. The site uses AdSense so you need to be aware of Google privacy policy. You you do not want to be tracked by Google please disable Javascript for this site. This site is perfectly usable without Javascript.
Last modified: June, 13, 2018