Total Surveillance Bulletin, 2016
For the list of top articles see Recommended Links section
- 20161229 : Cell phones can track their location, hoover up their personal info, record their conversations but that doesn't stop most people from owning one anyway. The populace has been convinced that owning the device that constantly spies on them is a necessity ( Dec 29, 2016 , www.nakedcapitalism.com )
- 20161229 : Cell phones can track their location, hoover up their personal info, record their conversations but that doesn't stop most people from owning one anyway. The populace has been convinced that owning the device that constantly spies on them is a necessity ( Dec 29, 2016 , www.nakedcapitalism.com )
- 20161226 : Snowden: 'The Central Problem of the Future' Is Control of User Data ( Dec 26, 2016 , tech.slashdot.org )
- 20161226 : NSA's Best Are 'Leaving In Big Numbers,' Insiders Say ( Dec 26, 2016 , yro.slashdot.org )
- 20161226 : HP Shutting Down Default FTP, Telnet Access To Network Printers ( Dec 26, 2016 , hardware.slashdot.org )
- 20161226 : New Stegano Exploit Kit Hides Malvertising Code In Banner Pixels ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : Backdoor Accounts Found in 80 Sony IP Security Camera Models ( Dec 26, 2016 , yro.slashdot.org )
- 20161226 : Yahoo Fixes Flaw Allowing an Attacker To Read Any User's Emails ( Dec 26, 2016 , tech.slashdot.org )
- 20161226 : Zeus Variant 'Floki Bot' Targets PoS Data ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : 5-Year-Old Critical Linux Vulnerability Patched ( Dec 26, 2016 , linux.slashdot.org )
- 20161226 : Vulnerability Prompts Warning: Stop Using Netgear WiFi Routers ( Dec 26, 2016 , mobile.slashdot.org )
- 20161226 : Malvertising Campaign Infects Your Router Instead of Your Browser ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : Newly Uncovered Site Suggests NSA Exploits For Direct Sale ( Dec 26, 2016 , news.slashdot.org )
- 20161226 : Netgear Releases 'Beta' Patches For Additional Routers Found With Root Vulnerability ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : McAfee Takes Six Months To Patch Remote Code Exploit In Linux VirusScan Enterprise ( Dec 26, 2016 , linux.slashdot.org )
- 20161226 : Massive Mirai Botnet Hides Its Control Servers On Tor ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : LinkedIn Warns 9.5 Million Lynda Users About Database Breach ( Dec 26, 2016 , yro.slashdot.org )
- 20161226 : The FBI Is Arresting People Who Rent DDoS Botnets ( Dec 26, 2016 , yro.slashdot.org )
- 20161226 : Russians Used Malware On Android Devices To Track and Target Ukraine Artillery, Says Report ( Dec 26, 2016 , yro.slashdot.org )
- 20161226 : Security Researchers Can Turn Headphones Into Microphones ( Dec 26, 2016 , news.slashdot.org )
- 20161226 : Personal Data For More Than 130,000 Sailors Hacked: U.S. Navy ( Dec 26, 2016 , news.slashdot.org )
- 20161226 : Muni System Hacker Hit Others By Scanning For Year-Old Java Vulnerability ( Dec 26, 2016 , developers.slashdot.org )
- 20161226 : Russia Says Foreign Spies Plan Cyber Attack On Banking System ( Dec 26, 2016 , it.slashdot.org )
- 20161226 : Sysadmin Gets Two Years In Prison For Sabotaging ISP ( Dec 26, 2016 , news.slashdot.org )
- 20161226 : Crooks Need Just Six Seconds To Guess A Credit Card Number ( Dec 26, 2016 , it.slashdot.org )
- 20161217 : You think Putin personally supervised the Yahoo hacking? This could make many people patriotic in a hurry. ( Dec 17, 2016 , www.nakedcapitalism.com )
- 20161217 : Yahoo's Hack Could Force Paying $145 Million Verizon Break-up Fee - Breitbart ( Dec 17, 2016 , www.breitbart.com )
- 20161215 : Georgia asks Trump to investigate DHS cyberattacks ( Dec 15, 2016 , marknesop.wordpress.com )
- 20161214 : Yahoo discovers hack affecting 1 billion users, breaking its own world record ( www.dailynews.com )
- 20161210 : The head of the worlds largest private surveillance operation, billionaire Eric Schmidt ( Dec 10, 2016 , www.nakedcapitalism.com )
- 20161205 : Peggy Noonan What We Lose if We Give Up Privacy by Peggy Noonan ( Aug 16, 2013 , WSJ )
- 20161205 : The internet is at risk of transforming from an open platform to myriad national networks ( www.ft.com )
- 20161125 : Is Obama presiding over a national security state gone rogue? by Michael Cohen ( Jun 21, 2013 , The Guardian )
- 20161121 : Apples iCloud retains the entire call history of every iPhone for as long as four months, making it an easy target for law enforcement and surveillance ( Nov 17, 2016 , economistsview.typepad.com )
- 20161118 : On Clapper resignation ( Nov 18, 2016 , www.nakedcapitalism.com )
- 20161118 : Physical access is not equal to game over ( www.nakedcapitalism.com )
- 20161111 : In the last few years, the Federal Trade Commission has sued more than dozen debt relief companies. They simply lie to consumers, says the FTCs Alice Hrdy. ( Nov 11, 2016 , www.nbcnews.com )
- 20161107 : Under the Din of the Presidential Race Lies a Once and Future Threat Cyberwarfare ( www.nytimes.com )
- 20161106 : Russia expects Washington to provide an explanation after a report claimed that Pentagon cyber-offensive specialists have hacked into Russias power grids, telecommunications networks, and the Kremlins command systems for a possible sabotage ( Nov 06, 2016 , www.moonofalabama.org )
- 20161103 : And Now For Some Comic Relief by Jonathan V. Last ( Nov 03, 2016 , www.weeklystandard.com )
- 20161030 : Speaking also of Pedesta email it is interesting that it was Podesta who make mistake of assessing phishing email link, probably accidentally ( turcopolier.typepad.com )
- 20161029 : A recent linguistic analysis cited in the New York Times speculates without any real trace of evidence that the hackers language in threats against Sony was written by a native Russian speaker and not a native Korean speaker ( www.nakedcapitalism.com )
- 20161029 : Phishing for Fools, Hipster Edition ( Oct 29, 2016 , www.nakedcapitalism.com )
- 20161028 : Note on propagandists masquerading as security experts ( observer.com )
- 20161028 : I find the whole hysteria over Russian hacking very one-sided. ( www.nakedcapitalism.com )
- 20161022 : Botnets can use internet enabled devices other then PC, tablets and phones ( Oct 22, 2016 , www.nakedcapitalism.com )
- 20161018 : Dear Clinton Team We Noticed You Might Need Some Email Security Tips ( theintercept.com )
- 20161009 : All your ISP's have been carrying NSA gear within their infrastructure for how long now ( Oct 09, 2016 , www.zerohedge.com )
- 20161008 : As the Surveillance Expands, Best Way to Resist is to Bury the NSA in Garbage ( Oct 08, 2016 , www.counterpunch.org )
- 20161008 : Yahoo Email Scanner Was Installed by Government ( Oct 07, 2016 , news.antiwar.com )
- 20160928 : Yahoo email capture FT Alphaville ( Sep 28, 2016 , ftalphaville.ft.com )
- 20160928 : Scan and go as surveillance tool ( Sep 26, 2016 , www.nakedcapitalism.com )
- 20160926 : Probe of leaked U.S. NSA hacking tools examines operatives mistake ( Reuters )
- 20160918 : Long-Secret Stingray Manuals Detail How Police Can Spy on Phones ( Sep 18, 2016 , theintercept.com )
- 20160916 : Edward Snowdens New Revelations Are Truly Chilling ( Oct 08, 2015 , Zero Hedge reprinted from TrueActivist.com )
- 20160916 : More Passwords, Please: 98 Million Leaked From 2012 Breach Of 'Russia's Yahoo' ( Sep 16, 2016 , it.slashdot.org )
- 20160916 : Unredacted User Manuals Of Stingray Device Show How Accessible Surveillance Is ( Sep 16, 2016 , yro.slashdot.org )
- 20160903 : There is interesting and expert commentary to NSO group software in the Hacker News forum ( Sep 03, 2016 , www.nakedcapitalism.com )
- 20160903 : How Spy Tech Firms Let Governments See Everything on a Smartphone ( Sep 03, 2016 , www.nytimes.com )
- 20160829 : Transfere of technology with the help of three letter agencies ( Aug 29, 2016 , economistsview.typepad.com )
- 20160821 : The NSA Leak Is Real, Snowden Documents Confirm by Sam Biddle ( Aug 19, 2016 , theintercept.com )
- 20160807 : Commentary The worlds best cyber army doesn't belong to Russia ( Aug 4, 2016 , Reuters )
- 20160807 : Edward Snowden Tweets Cryptic Code Was it a Dead Man's Switch ( sputniknews.com )
- 20160802 : NSA Architect: Agency Has ALL of Clinton's Deleted Emails ( www.breitbart.com )
- 20160606 : Got privacy If you use Twitter or a smartphone, maybe not so much ( www.pcworld.com )
- 20160602 : Gaius Publius Bernstein – The White House Is Terrified the Clinton Campaign Is in Freefall ( naked capitalism )
- 20160530 : Secret Text in Senate Bill Would Give FBI Warrantless Access to Email Records ( www.nakedcapitalism.com )
- 20160521 : The 10 Most Disturbing Snowden Revelations ( February 11, 2014 , pcmag.com )
- 20160410 : Government Hackers, Inc. ( April 6, 2016 , The American Conservative )
- 20160402 : Google builds a permanent profile on you and stores it at their end. ( www.zerohedge.com )
- 20160312 : Edward Snowden Interview on Apple vs. FBI, Privacy, the NSA, and More ( www.youtube.com )
- 20160312 : Edward Snowden Speaks Out: I will not be able to return form exile ( www.youtube.com )
- 20160310 : Using a decent VPN for everything is rapidly becoming a must. ( www.nakedcapitalism.com )
- 20160213 : US intelligence chief: we might use the internet of things to spy on you ( www.theguardian.com )
- 20160129 : US government finds top secret information in Clinton emails ( www.theguardian.com )
- 20160124 : I Ramped Up My Internet Security, and You Should Too by Julia Angwin ( Jan. 20, 2016 , ProPublica )
- 20160120 : Facebook the new social control paradigm ( Zero Hedge )
- 20160111 : Obama seeks Silicon Valley aid to spy on social media ( www.wsws.org )
- 20160109* Allen Dulles and modern neocons ( www.moonofalabama.org ) [Recommended]
Notable quotes:
"... I'd wager that most people know that cell phones can track their location, hoover up their personal info, record their conversations, etc, etc but that doesn't stop most people from owning one anyway. The populace has been convinced that owning the device that constantly spies on them is a necessity. ..."
"... I've often wondered whether the relatively high difficulty in buying a smartphone with less than two cameras has something to do with the SIGINT Enabling Project. ..."
PQS
,
December 28, 2016 at 11:30 am
I was paranoid about the Roomba and I'm pretty sure it doesn't have
any connectivity, nor does it record anything.
Personal assistant connected to both the 'net and Large Corp? No. Way.
lyman alpha blob
,
December 28, 2016 at 1:01 pm
I'd wager that most people know that cell phones can track their
location, hoover up their personal info, record their conversations, etc,
etc but that doesn't stop most people from owning one anyway. The
populace has been convinced that owning the device that constantly spies
on them is a necessity.
Don't think learning that Echo is doing the same thing would deter
most people from using it. 'Convenience' and all
cocomaan
,
December 28, 2016 at 5:40 pm
Fortunately, I can barely hear the person I'm talking to through my
smartphone, so I am not optimistic that it can actually hear me from
someplace else in the house, especially compared to someone's Echo I
have experience with. But point taken.
hunkerdown
,
December 28, 2016 at 6:20 pm
The microphoneS (often there is an extra mic to cancel ambient
noise) in a phone are exquisitely sensitive. The losses you're
hearing are those from crushing that comparatively high-fidelity
signal into a few thousand bits per second for transmission to/from
the base station.
I've often wondered whether the relatively high difficulty
in buying a smartphone with less than two cameras has something to
do with the SIGINT Enabling Project.
(Not that
I'm
foily )
carycat
,
December 28, 2016 at 3:17 pm
Wonder if Mr. B gave Mr. T and all the other attendees an Echo at Mr.
T's tech summit. ATT and all the other big telcom players all said,
scout's honor, they don't listen in on their customer's phone calls, so
no worries because Fortune 500 companies are such ethical people. That
may even be technically true because the 3 letter agencies and their
minions (human or otherwise) are doing the actual listening. So if you
are too lazy to go to Amazon.com to delete your idle chit chat, I can
sell you a cloth to wipe it with (maybe I'll even list it on Amazon's
marketplace).
Daryl
,
December 28, 2016 at 8:09 pm
It should be fairly simple to determine whether it's sending
everything home by analyzing network traffic.
Of course, just because it doesn't right now, doesn't mean that Amazon
or your local three letter agency cannot alter it to do so in the future
Notable quotes:
"... I'd wager that most people know that cell phones can track their location, hoover up their personal info, record their conversations, etc, etc but that doesn't stop most people from owning one anyway. The populace has been convinced that owning the device that constantly spies on them is a necessity. ..."
"... I've often wondered whether the relatively high difficulty in buying a smartphone with less than two cameras has something to do with the SIGINT Enabling Project. ..."
PQS
,
December 28, 2016 at 11:30 am
I was paranoid about the Roomba and I'm pretty sure it doesn't have
any connectivity, nor does it record anything.
Personal assistant connected to both the 'net and Large Corp? No. Way.
lyman alpha blob
,
December 28, 2016 at 1:01 pm
I'd wager that most people know that cell phones can track their
location, hoover up their personal info, record their conversations, etc,
etc but that doesn't stop most people from owning one anyway. The
populace has been convinced that owning the device that constantly spies
on them is a necessity.
Don't think learning that Echo is doing the same thing would deter
most people from using it. 'Convenience' and all
cocomaan
,
December 28, 2016 at 5:40 pm
Fortunately, I can barely hear the person I'm talking to through my
smartphone, so I am not optimistic that it can actually hear me from
someplace else in the house, especially compared to someone's Echo I
have experience with. But point taken.
hunkerdown
,
December 28, 2016 at 6:20 pm
The microphoneS (often there is an extra mic to cancel ambient
noise) in a phone are exquisitely sensitive. The losses you're
hearing are those from crushing that comparatively high-fidelity
signal into a few thousand bits per second for transmission to/from
the base station.
I've often wondered whether the relatively high difficulty
in buying a smartphone with less than two cameras has something to
do with the SIGINT Enabling Project.
(Not that
I'm
foily )
carycat
,
December 28, 2016 at 3:17 pm
Wonder if Mr. B gave Mr. T and all the other attendees an Echo at Mr.
T's tech summit. ATT and all the other big telcom players all said,
scout's honor, they don't listen in on their customer's phone calls, so
no worries because Fortune 500 companies are such ethical people. That
may even be technically true because the 3 letter agencies and their
minions (human or otherwise) are doing the actual listening. So if you
are too lazy to go to Amazon.com to delete your idle chit chat, I can
sell you a cloth to wipe it with (maybe I'll even list it on Amazon's
marketplace).
Daryl
,
December 28, 2016 at 8:09 pm
It should be fairly simple to determine whether it's sending
everything home by analyzing network traffic.
Of course, just because it doesn't right now, doesn't mean that Amazon
or your local three letter agency cannot alter it to do so in the future
(techcrunch.com)
157
Posted by
BeauHD
on Wednesday December 14, 2016 @05:00AM
from
the
no-place-to-hide
dept.
Twitter CEO Jack Dorsey
interviewed
Edward Snowden via Periscope
about the wide world of technology. The NSA
whistleblower "
discussed
the data that many online companies continue to collect about their users
,
creating a 'quantified world' -- and more opportunities for government
surveillance," reports TechCrunch. Snowden said, "If you are being tracked,
this is something you should agree to, this is something you should understand,
this is something you should be aware of and can change at any time."
TechCrunch reports:
Snowden acknowledged that there's a distinction between
collecting the content of your communication (i.e., what you said during a
phone call) and the metadata (information like who you called and how long it
lasted). For some, surveillance that just collects metadata might seem less
alarming, but in Snowden's view, "That metadata is in many cases much more
dangerous and much more intrusive, because it can be understood at scale." He
added that we currently face unprecedented perils because of all the data
that's now available -- in the past, there was no way for the government to get
a list of all the magazines you'd read, or every book you'd checked out from
the library. "[In the past,] your beliefs, your future, your hopes, your dreams
belonged to you," Snowden said. "Increasingly, these things belong to
companies, and these companies can share them however they want, without a lot
of oversight." He wasn't arguing that companies shouldn't collect user data at
all, but rather that "the people who need to be in control of that are the
users." "This is the central problem of the future, is how do we return control
of our identities to the people themselves?" Snowden said.
(cyberscoop.com)
412
Posted by EditorDavid
on Sunday December 11, 2016 @11:34AM
from the
blaming-Oliver-Stone
dept.
schwit1
quotes CyberScoop:
Low
morale at the National Security Agency is causing some of the agency's most
talented people
to leave in favor of private sector jobs
, former NSA Director Keith
Alexander told a room full of journalism students, professors and cybersecurity
executives Tuesday. The retired general and other insiders say a combination of
economic and social factors including negative press coverage -- have played a
part... "I am honestly surprised that some of these people in cyber companies
make up to seven figures. That's five times what the chairman of the Joint
Chiefs of Staff makes. Right? And these are people that are 32 years old. Do
the math. [The NSA] has great competition," he said.
The rate at which these cyber-tacticians are exiting public service has
increased over the last several years and has gotten considerably worse over
the last 12 months, multiple former NSA officials and D.C. area-based
cybersecurity employers have told CyberScoop in recent weeks... In large part,
Alexander blamed the press for propagating an image of the NSA that causes
people to believe they are being spied on at all times by the U.S. government
regardless of their independent actions.
"What really bothers me is that the people of NSA, these folks who take paltry
government salaries to protect this nation, are made to look like they are
doing something wrong," the former NSA Director added. "They are doing exactly
what our nation has asked them to do to protect us. They are the heroes."
(pcworld.com)
83
Posted by msmash
on Tuesday December 06, 2016 @11:00AM
from the
business-as-usual
dept.
Security experts consider the aging FTP and Telnet protocols unsafe, and HP has
decided to clamp down on access to networked printers through the remote-access
tools
. From a report on PCWorld:
Some of HP's new business printers
will, by default, be closed to remote access via protocols like FTP and Telnet.
However, customers can activate remote printing access through those protocols
if needed. "HP has started the process of closing older, less-maintained
interfaces including ports, protocols and cipher suites" identified by the U.S.
National Institute of Standards and Technology as less than secure, the company
said in a statement. In addition, HP also announced firmware updates to
existing business printers with improved password and encryption settings, so
hackers can't easily break into the devices.
(bleepingcomputer.com)
207
Posted by
BeauHD
on Tuesday December 06, 2016 @08:25PM
from the
hidden-in-plain-sight
dept.
An anonymous reader quotes a report from BleepingComputer:
For the past two
months, a new exploit kit has been
serving malicious code hidden in the pixels of banner ads via a malvertising
campaign
that has been active on several high profile websites.
Discovered by security researchers from ESET
, this new exploit kit is named
Stegano, from the word
steganography
, which is a technique of hiding content inside other files.
In this particular scenario, malvertising campaign operators hid malicious code
inside PNG images used for banner ads. The crooks took a PNG image and altered
the transparency value of several pixels. They then packed the modified image
as an ad, for which they bought ad displays on several high-profile websites.
Since a large number of advertising networks allow advertisers to deliver
JavaScript code with their ads, the crooks also included JS code that would
parse the image, extract the pixel transparency values, and using a
mathematical formula, convert those values into a character. Since images have
millions of pixels, crooks had all the space they needed to pack malicious code
inside a PNG photo. When extracted, this malicious code would redirect the user
to an intermediary ULR, called gate, where the host server would filter users.
This server would only accept connections from Internet Explorer users. The
reason is that the gate would exploit the CVE-2016-0162 vulnerability that
allowed the crooks to determine if the connection came from a real user or a
reverse analysis system employed by security researchers. Additionally, this IE
exploit also allowed the gate server to detect the presence of antivirus
software. In this case, the server would drop the connection just to avoid
exposing its infrastructure and trigger a warning that would alert both the
user and the security firm. If the gate server deemed the target valuable, then
it would redirect the user to the final stage, which was the exploit kit
itself, hosted on another URL. The Stegano exploit kit would use three Adobe
Flash vulnerabilities (CVE-2015-8651, CVE-2016-1019 or CVE-2016-4117) to attack
the user's PC, and forcibly download and launch into execution various strains
of malware.
(pcworld.com)
55
Posted by msmash
on Wednesday December 07, 2016 @12:20PM
from
the
security-woes
dept.
Many network security cameras made by Sony could be taken over by hackers and
infected with botnet malware if their firmware is not updated to the latest
version. Researchers from SEC Consult have
found two backdoor accounts that exist in 80 models of professional Sony
security cameras
, mainly used by companies and government agencies given
their high price, PCWorld reports. From the article:
One set of hard-coded
credentials is in the Web interface and allows a remote attacker to send
requests that would enable the Telnet service on the camera, the SEC Consult
researchers said in an advisory Tuesday. The second hard-coded password is for
the root account that could be used to take full control of the camera over
Telnet. The researchers established that the password is static based on its
cryptographic hash and, while they haven't actually cracked it, they believe
it's only a matter of time until someone does. Sony released a patch to the
affected camera models last week.
(zdnet.com)
30
Posted by msmash
on Thursday December 08, 2016 @11:45AM
from the
security-woes-and-fixes
dept.
Yahoo says it has fixed a severe security vulnerability in its email service
that
allowed an attacker to read a victim's email inbox
. From a report on ZDNet:
The cross-site scripting (XSS) attack only required a victim to view an email
in Yahoo Mail. The internet giant paid out $10,000 to security researcher Jouko
Pynnonen for privately disclosing the flaw through the HackerOne bug bounty, In
a write-up, Pynnonen said that the flaw was similar to last year's Yahoo Mail
bug, which similarly let an attacker compromise a user's account. Yahoo filters
HTML messages to ensure that malicious code won't make it through into the
user's browser, but the researcher found that the filters didn't catch all of
the malicious data attributes.
(onthewire.io)
25
Posted by
BeauHD
on Friday December 09, 2016 @05:00AM
from the
out-of-the-woodwork
dept.
Trailrunner7
quotes a report
from On the Wire:
Malware gangs, like sad wedding bands bands, love to play
the hits. And one of the hits they keep running back over and over is the Zeus
banking Trojan, which has been in use for many years in a number of different
forms. Researchers have
unearthed a new piece of malware called Floki Bot that is based on the
venerable Zeus source code
and is being used to infect point-of-sale
systems, among other targets. Flashpoint
conducted the analysis
of Floki Bot with Cisco's Talos research team, and
the two organizations said that the author behind the bot maintains a presence
on a number of different underground forums, some of which are in Russian or
other non-native languages for him. Kremez said that attackers sometimes will
participate in foreign language forums as a way to expand their knowledge.
Along with its PoS infection capability, Floki Bot also has a feature that
allows it to use the Tor network to communicate.
"During our analysis of
Floki Bot, Talos identified modifications that had been made to the dropper
mechanism present in the leaked Zeus source code in an attempt to make Floki
Bot more difficult to detect. Talos also observed the introduction of new code
that allows Floki Bot to make use of the Tor network. However, this
functionality does not appear to be active for the time being," Cisco's Talos
team
said in its analysis
.
(threatpost.com)
68
Posted by EditorDavid
on Saturday December 10, 2016 @12:34PM
from the
local-Linux-attacks
dept.
msm1267
quotes Kaspersky Lab's
ThreatPost:
A critical,
local code-execution vulnerability in the Linux kernel
was patched more
than a week ago, continuing a run of serious security issues in the operating
system, most of which have been hiding in the code for years. Details on the
vulnerability were
published
Tuesday by researcher Philip Pettersson
, who said the vulnerable code was
introd in August 2011.
A patch was pushed to the mainline Linux kernel December 2, four days after it
was privately disclosed. Pettersson has developed a proof-of-concept exploit
specifically for Ubuntu distributions, but told Threatpost his attack could be
ported to other distros with some changes. The vulnerability is a race
condition that was discovered in the
af_packet
implementation in the
Linux kernel, and Pettersson said that a local attacker could exploit the bug
to gain kernel code execution from unprivileged processes. He said the bug
cannot be exploited remotely.
"Basically it's a bait-and-switch," the researcher told Threatpost. "The bug
allows you to trick the kernel into thinking it is working with one kind of
object, while you actually switched it to another kind of object before it
could react."
(securityledger.com)
147
Posted by EditorDavid
on Sunday December 11, 2016 @01:34PM
from the
nixing-the-network
dept.
"By convincing a user to visit a specially crafted web site, a remote attacker
may execute arbitrary commands with root privileges on affected routers," warns
a new vulnerability notice
from Carnegie Mellon University's CERT. Slashdot reader
chicksdaddy
quotes Security
Ledger's story about certain models of Netgear's routers:
Firmware version
1.0.7.2_1.1.93 (and possibly earlier) for the R7000 and version 1.0.1.6_1.0.4
(and possibly earlier) for the R6400 are
known to contain the arbitrary command injection vulnerability
. CERT cited
"community reports" that indicate the R8000, firmware version 1.0.3.4_1.1.2, is
also vulnerable... The flaw was found in new firmware that runs the Netgear
R7000 and R6400 routers. Other models and firmware versions may also be
affected, including the R8000 router, CMU CERT warned.
With no work around to the flaw, CERT recommended that Netgear customers
disable their wifi router until a software patch from the company that
addressed the hole was available... A search of the public internet using the
Shodan search engine finds around 8,000 R6450 and R7000 devices that can be
reached directly from the Internet and that would be vulnerable to takeover
attacks. The vast majority of those are located in the United States.
Proof-of-concept exploit code was released by a Twitter user who, according to
the article, said "he informed Netgear of the flaw more than four months ago,
but did not hear back from the company since then."
(bleepingcomputer.com)
137
Posted by
BeauHD
on Wednesday December 14, 2016 @07:45PM
from
the
connected-devices
dept.
An anonymous reader quotes a report from BleepingComputer:
Malicious ads are
serving exploit code to infect routers
, instead of browsers, in order to
insert ads in every site users are visiting. Unlike previous malvertising
campaigns that targeted users of old Flash or Internet Explorer versions, this
campaign focused on Chrome users, on both desktop and mobile devices. The
malicious ads included in this malvertising campaign contain exploit code for
166 router models, which allow attackers to take over the device and insert ads
on websites that didn't feature ads, or replace original ads with the
attackers' own. Researchers
haven't yet managed to determine an exact list of affected router models
,
but some of the brands targeted by the attackers include Linksys, Netgear,
D-Link, Comtrend, Pirelli, and Zyxel. Because the attack is carried out via the
user's browser, using strong router passwords or disabling the administration
interface is not enough. The only way users can stay safe is if they update
their router's firmware to the most recent versions, which most likely includes
protection against the vulnerabilities used by this campaign.
The
"campaign" is called DNSChanger EK and works when attackers buy ads on
legitimate websites and insert malicious JavaScript in these ads, "which use a
WebRTC request to a Mozilla STUN server to determine the user's local IP
address," according to BleepingComputer. "Based on this local IP address, the
malicious code can determine if the user is on a local network managed by a
small home router, and continue the attack. If this check fails, the attackers
just show a random legitimate ad and move on. For the victims the crooks deem
valuable, the attack chain continues. These users receive a tainted ad which
redirects them to the DNSChanger EK home, where the actual exploitation begins.
The next step is for the attackers to send an image file to the user's browser,
which contains an AES (encryption algorithm) key embedded inside the photo
using the technique of steganography. The malicious ad uses this AES key to
decrypt further traffic it receives from the DNSChanger exploit kit. Crooks
encrypt their operations to avoid the prying eyes of security researchers."
(vice.com)
33
Posted by
BeauHD
on Wednesday December 14, 2016 @08:25PM
from
the
buy-one-get-one
dept.
An anonymous reader quotes a report from Motherboard:
The Shadow Brokers --
a hacker or group of hackers that stole computer exploits from the National
Security Agency -- has been quiet for some time. After their auction and
crowd-funded approach for selling the exploits met a lukewarm reception, the
group seemingly stopped posting new messages in October. But a newly uncovered
website, which includes a file apparently signed with The Shadow Brokers'
cryptographic key, suggests the group is
trying to sell hacking tools directly to buyers one by one
, and a cache of
files appears to include more information on specific exploits. On Wednesday,
someone calling themselves Boceffus Cleetus
published a Medium post
called "Are the Shadow Brokers selling NSA tools on
ZeroNet?" Cleetus, who has
an American flag with
swastikas
as their profile picture, also tweeted the post from a Twitter
account created this month. The site includes a long list of supposed items for
sale, with names like ENVOYTOMATO, EGGBASKET, and YELLOWSPIRIT. Each is sorted
into a type, such as "implant," "trojan," and "exploit," and comes with a price
tag between 1 and 100 bitcoins ($780 -- $78,000). Customers can purchase the
whole lot for 1000 bitcoins ($780,000). The site also lets visitors download a
selection of screenshots and files related to each item. Along with those is a
file signed with a PGP key with an identical fingerprint to that linked to the
original Shadow Brokers dump of exploits from August. This newly uncovered file
was apparently signed on 1 September; a different date to any of The Shadow
Brokers'
previously signed messages
.
(netgear.com)
26
Posted by EditorDavid
on Saturday December 17, 2016 @10:34AM
from the
but-they-might-not-work
dept.
The Department of Homeland Security's CERT issued a warning last week that
users
should "strongly
consider"
not using some models of NetGear routers, and the list expanded
this week to include 11 different models. Netgear's now updated their web page,
announcing eight "beta" fixes, along with three more "production" fixes.
chicksdaddy
writes:
The
company said the new [beta] firmware has not been fully tested and "
might
not work for all users
." The company offered it as a "temporary solution"
to address the security hole. "Netgear is working on a production firmware
version that fixes this command injection vulnerability and will release it as
quickly as possible," the company said in a post to its online knowledgebase
early Tuesday.
The move follows publication of a warning from experts at Carnegie Mellon on
December 9 detailing a serious "arbitrary command injection" vulnerability in
the latest version of firmware used by a number of Netgear wireless routers.
The security hole could allow a remote attacker to take control of the router
by convincing a user to visit a malicious web site... The vulnerability was
discovered by an individual...who says
he contacted Netgear about the flaw four months ago
, and went public with
information on it after the company failed to address the issue on its own.
Posted by EditorDavid
on Saturday December 17, 2016 @05:34PM
from the
jeopardized-in-June
dept.
mask.of.sanity
writes:
A
researcher has reported
10 vulnerabilities in McAfee's VirusScan Enterprise for Linux
that when
chained together result in root remote code execution. McAfee took six months
to fix the bugs issuing a patch December 9th.
Citing the
security note
,
CSO adds that "one of the issues
affects Virus Scan Enterprise for Windows version 8.7i through at least 8.8
."
The vulnerability was reported by Andrew Fasano at MIT's federally-funded
security lab, who said he targeted McAfee's client because "it runs as root, it
claims to make your machine more secure, it's not particularly popular, and it
looks like it hasn't been updated in a long time."
Posted by EditorDavid
on Saturday December 17, 2016 @06:34PM
from the
catch-me-if-you-can
dept.
"Following a failed takedown attempt, changes made to the Mirai malware variant
responsible for building one of today's biggest botnets of IoT devices will
make it incredibly harder for authorities and security firms to shut it down,"
reports Bleeping Computer. An anonymous reader writes:
Level3 and others"
have been very close to taking down one of the biggest Mirai botnets around,
the same one that attempted to
knock the Internet offline in Liberia
, and also hijacked 900,000 routers
from
German ISP Deutsche Telekom
.The botnet narrowly escaped due to the fact
that its maintainer, a hacker known as BestBuy, had implemented a
domain-generation algorithm to generate random domain names where he hosted his
servers.
Currently, to avoid further takedown attempts from similar security firms,
BestBuy has
started moving the botnet's command and control servers to Tor
. "It's all
good now. We don't need to pay thousands to ISPs and hosting. All we need is
one strong server," the hacker said. "Try to shut down .onion 'domains' over
Tor," he boasted, knowing that nobody can.
(neowin.net)
35
Posted by EditorDavid
on Sunday December 18, 2016 @02:34PM
from the
profile-views
dept.
Less than four weeks after Microsoft formally
acquired LinkedIn for $26 billion
, there's been a database breach. An
anonymous reader writes:
LinkedIn is sending emails to 9.5 million users of
Lynda.com, its online learning subsidiary,
warning the users of a database breach by "an unauthorized third party"
.
The affected database included contact information for at least some of the
users. An email to customers says "while we have no evidence that your specific
account was accessed or that any data has been made publicly available, we
wanted to notify you as a precautionary measure." Ironically, the breach comes
less than a month after Russia
blocked access to LinkedIn over privacy concerns
.
LinkedIn has also reset the passwords for 55,000 Lynda.com accounts (though
apparently many of its users don't have accounts with passwords).
(bleepingcomputer.com)
211
Posted by EditorDavid
on Sunday December 18, 2016 @04:44PM
from the
denial-of-liberty-counterattack
dept.
This week the FBI arrested a 26-year-old southern California man for launching
a DDoS attack against online chat service Chatango at the end of 2014 and in
early 2015 -- part of a new crackdown on the customers of "DDoS-for-hire"
services. An anonymous reader writes:
Sean Krishanmakoto Sharma, a computer
science graduate student at USC, is now
facing up to 10 years in prison
and/or a fine of up to $250,000.
Court documents
describe a service called Xtreme Stresser as "basically a
Linux botnet DDoS tool," and allege that Sharma rented it for an attack on
Chatango, an online chat service. "Sharma is now free on a $100,000 bail,"
reports Bleeping Computer, adding "As part of his bail release agreement,
Sharma is banned from accessing certain sites such as HackForums and tools such
as VPNs..."
"Sharma's arrest is part of
a bigger operation against DDoS-for-Hire services, called Operation Tarpit
,"
the article points out. "Coordinated by Europol, Operation Tarpit took place
between December 5 and December 9, and concluded with the arrest of 34 users of
DDoS-for-hire services across the globe, in countries such as Australia,
Belgium, France, Hungary, Lithuania, the Netherlands, Norway, Portugal,
Romania, Spain, Sweden, the United Kingdom and the United States." It grew out
of an earlier investigation into a U.K.-based DDoS-for-hire service which had
400 customers who ultimately launched 603,499 DDoS attacks on 224,548 targets.
Most of the other suspects arrested were under the age of 20.
(reuters.com)
101
Posted by
BeauHD
on Thursday December 22, 2016 @06:25PM
from the
come-out-come-out-wherever-you-are
dept.
schwit1
quotes a report from
Reuters:
A hacking group linked to the Russian government and high-profile
cyber attacks against Democrats during the U.S. presidential election likely
used a
malware implant on Android devices to track and target Ukrainian artillery
units
from late 2014 through 2016, according to a
new report
released Thursday. The malware was able to retrieve
communications and some locational data from infected devices, intelligence
that would have likely been used to strike against the artillery in support of
pro-Russian separatists fighting in eastern Ukraine, the report from cyber
security firm CrowdStrike found. The hacking group, known commonly as Fancy
Bear or APT 28, is believed by U.S. intelligence officials to work primarily on
behalf of the GRU, Russia's military intelligence agency. The implant leveraged
a legitimate Android application developed by a Ukrainian artillery officer to
process targeting data more quickly, CrowdStrike said. Its deployment "extends
Russian cyber capabilities to the front lines of the battlefield," the report
said, and "could have facilitated anticipatory awareness of Ukrainian artillery
force troop movement, thus providing Russian forces with useful strategic
planning information."
(techcrunch.com)
122
Posted by
BeauHD
on Thursday November 24, 2016 @08:00AM
from the
proof-of-concept
dept.
As if we don't already have enough devices that can listen in on our
conversations, security researchers at Israel's Ben Gurion University have
created malware that will turn your headphones into microphones
that can
slyly record your conversations. TechCrunch reports:
The proof-of-concept,
called "
Speake(a)r
," first
turned headphones connected to a PC into microphones and then tested the
quality of sound recorded by a microphone vs. headphones on a target PC. In
short, the headphones were nearly as good as an unpowered microphone at picking
up audio in a room. It essentially "retasks" the RealTek audio codec chip
output found in many desktop computers into an input channel. This means you
can plug your headphones into a seemingly output-only jack and hackers can
still listen in. This isn't a driver fix, either. The embedded chip does not
allow users to properly prevent this hack which means your earbuds or nice cans
could start picking up conversations instantly. In fact, even if you disable
your microphone, a computer with a RealTek chip could still be hacked and
exploited without your knowledge. The sound quality, as shown by this chart, is
pretty much the same for a dedicated microphone and headphones.
The
researchers have
published a video
on YouTube demonstrating how this malware works.
(reuters.com)
57
Posted by msmash
on Thursday November 24, 2016 @10:04AM
from the
security-woes
dept.
Hackers gained access to sensitive information, including Social Security
numbers,
for
134,386 current and former U.S. sailors, the U.S. Navy has said
. According
to Reuters:
It said a laptop used by a Hewlett Packard Enterprise Services
employee working on a U.S. Navy contract was hacked. Hewlett Packard informed
the Navy of the breach on Oct. 27 and the affected sailors will be notified in
the coming weeks, the Navy said. "The Navy takes this incident extremely
seriously - this is a matter of trust for our sailors," Chief of Naval
Personnel Vice Admiral Robert Burke said in a statement.
(arstechnica.com)
30
Posted by
BeauHD
on Tuesday November 29, 2016 @09:05PM
from the
thank-God-for-backups
dept.
An anonymous reader quotes a report from Ars Technica:
The attacker who
infected servers and desktop computers
at the San Francisco Metropolitan
Transit Agency (SFMTA) with ransomware on November 25 apparently
gained access to the agency's network by way of a known vulnerability in an
Oracle WebLogic server
. That vulnerability is similar to the one used to
hack a Maryland hospital network's systems in April and infect multiple
hospitals with crypto-ransomware. And evidence suggests that SFMTA wasn't
specifically targeted by the attackers; the agency just came up as a target of
opportunity through a vulnerability scan. In an e-mail to Ars, SFMTA
spokesperson Paul Rose said that on November 25, "we became aware of a
potential security issue with our computer systems, including e-mail." The
ransomware "encrypted some systems mainly affecting computer workstations," he
said, "as well as access to various systems. However, the SFMTA network was not
breached from the outside, nor did hackers gain entry through our firewalls.
Muni operations and safety were not affected. Our customer payment systems were
not hacked. Also, despite media reports, no data was accessed from any of our
servers." That description of the ransomware attack is not consistent with some
of the evidence of previous ransomware attacks by those behind the SFMTA
incident -- which Rose said primarily affected about 900 desktop computers
throughout the agency. Based on communications uncovered from the ransomware
operator behind the Muni attack published by
security reporter Brian Krebs
, an SFMTA Web-facing server was likely
compromised by what is referred to as a "deserialization" attack after it was
identified by a vulnerability scan. A security researcher told Krebs that he
had been able to gain access to the mailbox used in the malware attack on the
Russian e-mail and search provider Yandex by guessing its owner's security
question, and he provided details from the mailbox and another linked mailbox
on Yandex. Based on details found in e-mails for the accounts, the attacker ran
a server loaded with open source vulnerability scanning tools to identify and
compromise servers to use in spreading the ransomware,
known as HDDCryptor and Mamba
, within multiple organizations' networks.
(reuters.com)
88
Posted by msmash
on Friday December 02, 2016 @12:20PM
from the
hmmm
dept.
Russia said on Friday it had uncovered a plot by foreign spy agencies to sow
chaos in Russia's banking system via a
coordinated wave of cyber attacks and fake social media reports about banks
going bust
. From a report on Reuters:
Russia's domestic intelligence
agency, the Federal Security Service (FSB), said that the servers to be used in
the alleged cyber attack were located in the Netherlands and registered to a
Ukrainian web hosting company called BlazingFast. The attack, which was to
target major national and provincial banks in several Russian cities, was meant
to start on Dec. 5, the FSB said in a statement. "It was planned that the cyber
attack would be accompanied by a mass send-out of SMS messages and publications
in social media of a provocative nature regarding a crisis in the Russian
banking system, bankruptcies and license withdrawals," it said. "The FSB is
carrying out the necessary measures to neutralize threats to Russia's economic
and information security."
Posted by EditorDavid
on Sunday December 04, 2016 @02:39PM
from the
BOFH
dept.
After being let go over a series of "personal issues" with his employer, things
got worse for 26-year-old network administrator Dariusz J. Prugar, who will now
have to spend two years in prison for hacking the ISP where he'd worked. An
anonymous reader writes:
Prugar had
used his old credentials to log into the ISP's network and "take back" some of
the scripts
and software he wrote... "Seeking to hide his tracks, Prugar
used an automated script that deleted various logs," reports Bleeping Computer.
"As a side effect of removing some of these files, the ISP's systems crashed,
affecting over 500 businesses and over 5,000 residential customers."
When the former ISP couldn't fix the issue, they asked Prugar to help. "During
negotiations, instead of requesting money as payment, Prugar insisted that he'd
be paid using the rights to the software and scripts he wrote while at the
company, software which was now malfunctioning, a week after he left." This
tipped off the company, who detected foul play, contacted the FBI and rebuilt
its entire network.
Six years later, Prugar was found guilty after a
one-week jury trial, and was ordered by the judge to
pay $26,000 in restitution to the ISP
(which went out of business in
October of 2015).
Prugar's two-year prison sentence begins December 27.
(independent.co.uk)
110
Posted by EditorDavid
on Sunday December 04, 2016 @07:39AM
from the
one-Mississippi-two-Mississippi
dept.
schwit1
quotes The Independent:
Criminals can work out the card number, expiration date, and security code for
a Visa debit or credit card
in as little as six seconds using guesswork
, researchers have found...
Fraudsters use a so-called Distributed Guessing Attack to get around security
features put in place to stop online fraud, and this may have been the method
used in
the recent Tesco Bank hack
...
According to a study published in the academic journal IEEE Security & Privacy,
fraudsters could use computers to systematically
fire different
variations of security data at hundreds of websites simultaneously
. Within
seconds, by a process of elimination, the criminals could verify the correct
card number, expiration date and the three-digit security number on the back of
the card.
One of the researchers explained this attack combines two weaknesses into one
powerful attack. "Firstly, current online payment systems do not detect
multiple invalid payment requests from different websites... Secondly,
different websites ask for different variations in the card data fields to
validate an online purchase. This means it's quite easy to build up the
information and piece it together like a jigsaw puzzle."
Notable quotes:
"... this will probably be in tomorrow's washington post. "how putin sabotaged the election by hacking yahoo mail". and "proton" and "putin" are 2 syllable words beginning with "p", which is dispositive according to experts who don't want to be indentified. ..."
"... [Neo]Liberals have gone truly insane, I made the mistake of trying to slog through the comments the main "putin did it" piece on huffpo out of curiosity. Big mistake, liberals come across as right wing nutters in the comments, I never knew they were so very patriotic, they never really expressed it before. ..."
"... Be sure and delete everything from your Yahoo account BEFORE you push the big red button. They intentionally wait 90 days to delete the account in order that ECPA protections expire and content can just be handed over to the fuzz. ..."
"... It's a good thing for Obama that torturing logic and evasive droning are not criminal acts. ..."
"... "Relations with Russia have declined over the past several years" I reflexively did a Google search. Yep, Victoria Nuland is still employed. ..."
"... With all the concern expressed about Russian meddling in our election process why are we forgetting the direct quid pro quo foreign meddling evidenced in the Hillary emails related to the seldom mentioned Clinton Foundation or the more likely meddling by local election officials? Why have the claims of Russian hacking received such widespread coverage in the Press? ..."
"... I watched it too and agree with your take on it. For all the build up about this press conference and how I thought we were going to engage in direct combat with Russia for these hacks (or so they say it is Russia, I still wonder about that), he did not add any fuel to this fire. ..."
"... The whole thing was silly – the buildup to this press conference and then how Obama handled the hacking. A waste of time really. I don't sense something is going on behind the scenes but it is weird that the news has been all about this Russian hacking. He did not get into the questions about the Electoral College either and he made it seem like Trump indeed is the next President. I mean it seems like the MSM was making too much about this issue but then nothing happened. ..."
pretzelattack ,
December 16, 2016 at 3:46 pm
this will probably be in tomorrow's washington post. "how putin sabotaged the election
by hacking yahoo mail". and "proton" and "putin" are 2 syllable words beginning with "p",
which is dispositive according to experts who don't want to be indentified.
HBE ,
December 16, 2016 at 4:13 pm
[Neo]Liberals have gone truly insane, I made the mistake of trying to slog through the
comments the main "putin did it" piece on huffpo out of curiosity. Big mistake, liberals come
across as right wing nutters in the comments, I never knew they were so very patriotic, they never
really expressed it before.
B1whois ,
December 16, 2016 at 6:45 pm
The great sucking pit of need that keeps on giving. when will it abate?
different clue ,
December 16, 2016 at 6:49 pm
They are only hurt at the loss of their beloved Clintron, and are seizing on the Puttin Diddit
excuse.
polecat ,
December 16, 2016 at 7:45 pm
Did they happen to offer you some Guyana Kool-Aid with that order of vitriol ?
Brad ,
December 16, 2016 at 10:26 pm
Unfortunately the whole "grief cycle" will get a reboot after next Monday's "Election II".
The rest of us are to be pissed off that the CIA and Clinton clique have continued to agiprop
this.
Knot Galt ,
December 16, 2016 at 10:48 pm
Since the ex-Correct The Record key jockeys are out of a job they have to practice their craft
somewhere.
hunkerdown ,
December 16, 2016 at 5:23 pm
Be sure and delete everything from your Yahoo account BEFORE you push the big red button. They
intentionally wait 90 days to delete the account in order that ECPA protections expire and content
can just be handed over to the fuzz.
auntienene ,
December 16, 2016 at 8:07 pm
I don't think I've looked at my yahoo account in 8-10 years and I didn't use their email; just
had an address. I don't remember my user name or password. I did get an email from them (to my
not-yahoo address) advising of the breach.
Do I need to do anything at all?
hunkerdown ,
December 16, 2016 at 8:22 pm
auntienene, probably not, but as a general principle it's better to close accounts down properly
than to abandon them.
Tvc15 ,
December 16, 2016 at 10:50 pm
I was amazed as I watched a local am news show in Pittsburgh recommend adding your cell phone
number in addition to changing your password. Yeah, that's a great idea, maybe my ss# would provide
even more security.
Jeremy Grimm ,
December 16, 2016 at 4:30 pm
I use yahoo email. Why should I move? As I understood the breach it was primarily a breach
of the personal information used to establish the account. I've already changed my password -
did it a couple of days after the breach was reported. I had a security clearance with DoD which
requires disclosure of a lot more personal information than yahoo had. The DoD data has been breached
twice from two separate servers.
As far as reading my emails - they may prove useful for phishing but that's about all. I'm
not sure what might be needed for phishing beyond a name and email address - easily obtained from
many sources I have no control over.
So - what am I vulnerable to by remaining at yahoo that I'm not already exposed to on a more
secure server?
polecat ,
December 16, 2016 at 7:53 pm
You are vulnerable to the knowledge that Marissa Mayer is STILL employed as a high-level corporate
twit --
Lee ,
December 16, 2016 at 3:05 pm
It's a good thing for Obama that torturing logic and evasive droning are not criminal acts.
Ranger Rick ,
December 16, 2016 at 3:12 pm
"Relations with Russia have declined over the past several years" I reflexively did a Google
search. Yep, Victoria Nuland is still employed.
Pat ,
December 16, 2016 at 3:32 pm
Yeah, it isn't like Mr. 'We go high' is going to admit our relationship has declined because
we have underhandedly tried to isolate and knee cap them for pretty much his entire administration.
Jeremy Grimm ,
December 16, 2016 at 4:44 pm
Are you referring to Obama's press conference? If so, I am glad he didn't make a big deal out
of the Russian hacking allegations - as in it didn't sound like he planned a retaliation for the
fictional event and its fictional consequences. He rose slightly in stature in my eyes - he's
almost as tall as a short flea.
With all the concern expressed about Russian meddling in our election process why are we forgetting
the direct quid pro quo foreign meddling evidenced in the Hillary emails related to the seldom
mentioned Clinton Foundation or the more likely meddling by local election officials? Why have
the claims of Russian hacking received such widespread coverage in the Press?
Why is a lameduck
messing with the Chinese in the South China sea? What is the point of all the "fake" news hogwash?
Is it related to Obama's expression of concern about the safety of the Internet? I can't shake
the feeling that something is going on below the surface of these murky waters.
Susan C ,
December 16, 2016 at 5:44 pm
I watched it too and agree with your take on it. For all the build up about this press conference
and how I thought we were going to engage in direct combat with Russia for these hacks (or so
they say it is Russia, I still wonder about that), he did not add any fuel to this fire.
He did
respond at one point to a reporter that the hacks from Russia were to the DNC and Podesta but
funny how he didn't say HRC emails. Be it as it may, I think what was behind it was HRC really
trying to impress all her contributors that Russia really did do her in, see Obama said so, since
she must be in hot water over all the money she has collected from foreign governments for pay
to play and her donors.
The whole thing was silly – the buildup to this press conference and then
how Obama handled the hacking. A waste of time really. I don't sense something is going on behind
the scenes but it is weird that the news has been all about this Russian hacking. He did not get
into the questions about the Electoral College either and he made it seem like Trump indeed is
the next President. I mean it seems like the MSM was making too much about this issue but then
nothing happened.
Pat ,
December 16, 2016 at 7:02 pm
Unfortunately the nightly news is focusing on Obama says Russia hacked the DNC and had it in
for Clinton!!! He warned them to stay out of the vote! There will be consequences! Russia demands
the evidence and then a story about the evidence. (This one might have a few smarter people going
"huh, that's it?!?!")
I do like the some private some public on that consequences and retaliation thing. You either
have to laugh or throw up about the faux I've got this and the real self-righteousness. Especially
since it is supposedly to remind people we can do it to you. Is there anyone left outside of America
who doesn't think they already do do it to anyone Uncle Sam doesn't want in office and even some
they do? Mind you I'm not sure how many harried people watching the news are actually going to
laugh at that one because they don't know how how much we meddle.
Knot Galt ,
December 16, 2016 at 10:55 pm
Obamameter. ty L. Scofield ;-)
Notable quotes:
"... potential material adverse event ..."
"... exploring a price cut or possible exit ..."
"... Net Neutrality . ..."
"... These enforceable, bright-line rules will ban paid prioritization, and the blocking and throttling of lawful content and services ..."
"... communicated with a total of 51 parties to evaluate their interest in a potential transaction ..."
"... 32 parties signed confidentiality agreements with Yahoo ..."
"... Payment card data and bank account information are not stored in the system the company believes was affected ..."
Given that the Donald Trump victory already made Yahoo less attractive for
Verizon, the latest billion-account-hack at Yahoo could let Verizon dump their
buy-out and still collect a
$145 million break-up fee .
Yahoo's stock plunged
over 6 percent after the company
admitted its customer data had been hacked again, with at least 1 billion
accounts exposed in 2014. The horribly bad news for Yahoo followed an equally bad
news report in September that
500 million e-mail account were hacked in 2013. Yahoo unfortunately now has
the distinction of suffering both of the history's largest client hacks.
SIGN UP FOR OUR NEWSLETTER
Verizon's top lawyer told reporters after the first Yahoo hack that the
disclosure constituted a "
potential material adverse event
" that would
allow for the mobile powerhouse to pull out of the $4.83 billion deal they
announced on July 25, 2016.
Less than 24 hours after Yahoo
disclosed the
even larger hack of client accounts by a "state-sponsored actor," Bloomberg
reported
that Verizon is "
exploring a price cut or possible exit
" from its
proposed Yahoo acquisition.
Breitbart
reported that Google and other Silicon Valley companies were huge corporate
winners when Chairman Tom Wheeler and the other two Democrat political appointees
on the FCC voted on a party-line vote in mid-February 2015 for a new regulatory
structure called '
Net
Neutrality .
' Although Wheeler claimed, "
These enforceable,
bright-line rules will ban paid prioritization, and the blocking and throttling of
lawful content and services
," they were a huge economic disaster for
Verizon's high-speed broadband business model.
Verizon responded last year by paying
$4.4 billion to buy AOL in order to pick up popular news sites, large
advertising business, and more than 2 million Internet dial-up subscribers. Buying
Yahoo was expected to give the former telephone company to achieve "scale" by
controlling a second web content pioneer.
After President and CEO Marissa Mayer began organizing an auction in March,
Yahoo stock doubled from $26 a share to $51 by September. But she announced on
Wednesday the new hack, Yahoo's stock has been plunging to $38.40 in after-market
trading.
The buyer normally has to pay a break-up fee if an acquisition fails. But Yahoo
chose to run its own
auction that "
communicated with a total of 51 parties to evaluate their
interest in a potential transaction
." Then between February and April 2016, a
"short list" of "
32 parties signed confidentiality agreements with Yahoo
,"
including 10 strategic parties and 22 financial sponsors.
Yahoo's
13D proxy statement filed with the SEC was mostly boilerplate disclosure, but
it seemed that something must have been a potential problem at Yahoo for the
company to offer a $145 million termination fee to Verizon if the deal did not
close.
Yahoo on Wednesday issued a statement saying personal information from more
than a billion user accounts was stolen in 2014. The news followed the company's
announcement in September that hackers had stolen personal data from at least half
a billion accounts in 2013. Yahoo said it believes the two thefts were by
different parties.
Yahoo admitted that both hacks were so extensive that they included users'
names, email addresses, phone numbers, dates of birth, scrambled passwords and
security questions and answers. But Yahoo stated, "
Payment card data and bank
account information are not stored in the system the company believes was affected
."
Yahoo said they have invalidated unencrypted security questions and answers in
user accounts. They are in the process of notifying potentially affected users and
is requiring them to change their passwords.
Yahoo was already facing nearly two dozen class-action lawsuits over the first
breach and the company's failure to report it on a timely basis. A federal 3 judge
panel last week consolidated 5 of the suits into a mass tort in the San Jose U.S.
District Court.
Undoubtedly, there will be a huge number of user lawsuits filed against Yahoo
in the next few weeks.
Pavlo Svolochenko ,
December 14, 2016 at 2:43 pm
Georgia asks Trump to investigate DHS 'cyberattacks'
If you want to know what Washington is doing at any given time, just look at what they're accusing
the competition of.
yalensis ,
December 14, 2016 at 5:05 pm
As the Worm Turns!
For all those Amurican rubes out there who beleived that Homeland Security was protecting them
against foreign terrorists – ha hahahahahaha!
Yahoo has discovered a 3-year-old security breach that enabled a hacker to compromise more than 1
billion user accounts, breaking the company's own humiliating record for the biggest security breach
in history.
The digital heist disclosed Wednesday occurred in August 2013, more than a year before a separate
hack that Yahoo announced nearly three months ago . That breach affected at least 500 million users,
which had been the most far-reaching hack until the latest revelation.
Yahoo has more than a billion monthly active users, although some have multiple accounts and others
have none at all. An unknown number of accounts were affected by both hacks.
In both attacks, the stolen information included names, email addresses, phone numbers, birthdates
and security questions and answers. The company says it believes bank-account information and payment-card
data were not affected.
Notable quotes:
"... the world's largest private surveillance operation ..."
"... Ha! I wish I'd thought of that line! I just laughed out loud on the train and my fellow commuter drones are shuffling and wondering to themselves if I'm on day release from an institution. ..."
"... Of course, the joke's on us, because that's exactly what they (Google) are with all the right friends in high places to boot ..."
"... Something that has been occurring lately with Chrome makes me think that Google is truly watching. A lot of sites (RT et al) are having the https// crossed out in red implying that the connection is no longer secure. ..."
Clive
December 9, 2016 at 2:42 am
" the head of the world's largest private surveillance operation , billionaire
Eric Schmidt "
Ha! I wish I'd thought of that line! I just laughed out loud on the train and my fellow
commuter drones are shuffling and wondering to themselves if I'm on day release from an institution.
Of course, the joke's on us, because that's exactly what they (Google)
are with all the right friends in high places to boot .
heresy101
December 9, 2016 at 1:33 pm
Something that has been occurring lately with Chrome makes me think that Google is truly
watching. A lot of sites (RT et al) are having the https// crossed out in red implying that the
connection is no longer secure.
For instance, the "true" link in the article above has the https// in red when using Chrome,
but Firefox does not make it unsecure (at least it isn't showing it).
https://www.opendemocracy.net/od-russia/maxim-eristavi/terror-against-ukraine-s-journalists-is-fueled-by-political-elites
Does this have something to do with certificates or is something more sinister going on?
Chrome puts each tab in a new process versus Firefox creating one big file that becomes unstable
if you open too many tabs.
There was a comment on ZH recently that referenced a secure browser but now I can't find the
link. Does anyone have a suggestion?
Clive
December 9, 2016 at 2:09 pm
Probably TOR but I would caution
this is far from foolproof and may even incur The Panopticon's more intrusive surveillance attention.
I value my privacy as much as anyone but I don't use TOR or similar simply because if they
are not a guaranteed solution, what's the point? And besides, why should I have to? It's just
another tax on my time and resources.
Dopey Panda
December 9, 2016 at 7:08 pm
The opendemocracy link you gave shows up as having issues in firefox also. It looks like they
have some insecure images on the page, which is probably what chrome is complaining about.
Notable quotes:
"... A loss of the expectation of privacy in communications is a loss of something personal and intimate, and it will have broader implications. ..."
"... Mr. Hentoff sees the surveillance state as a threat to free speech, too ..."
"... An entrenched surveillance state will change and distort the balance that allows free government to function successfully. ..."
"... "When you have this amount of privacy invasion put into these huge data banks, who knows what will come out?" ..."
"... Asked about those attempts, he mentions the Alien and Sedition Acts of 1798, the Red Scare of the 1920s and the McCarthy era. Those times and incidents, he says, were more than specific scandals or news stories, they were attempts to change our nature as a people. ..."
"... What of those who say they don't care what the federal government does as long as it keeps us safe? The threat of terrorism is real, Mr. Hentoff acknowledges. Al Qaeda is still here, its networks are growing. But you have to be careful about who's running U.S. intelligence and U.S. security, and they have to be fully versed in and obey constitutional guarantees. ..."
"... Mr. Hentoff notes that J. Edgar Hoover didn't have all this technology. "He would be so envious of what NSA can do." ..."
Aug 16, 2013 | WSJ
...Among the pertinent definitions of privacy from the Oxford English Dictionary: "freedom from
disturbance or intrusion," "intended only for the use of a particular person or persons," belonging
to "the property of a particular person." Also: "confidential, not to be disclosed to others." Among
others, the OED quotes the playwright Arthur Miller, describing the McCarthy era: "Conscience was
no longer a private matter but one of state administration."
Privacy is connected to personhood. It has to do with intimate things-the innards of your head
and heart, the workings of your mind-and the boundary between those things and the world outside.
A loss of the expectation of privacy in communications is a loss of something personal and
intimate, and it will have broader implications. That is the view of Nat Hentoff, the great
journalist and civil libertarian. He is 88 now and on fire on the issue of privacy. "The media has
awakened," he told me. "Congress has awakened, to some extent." Both are beginning to realize "that
there are particular constitutional liberty rights that [Americans] have that distinguish them from
all other people, and one of them is privacy."
Mr. Hentoff sees excessive government surveillance as violative of the Fourth Amendment, which
protects "the right of the people to be secure in their persons, houses, papers, and effects, against
unreasonable searches and seizures" and requires that warrants be issued only "upon probable cause
. . . particularly describing the place to be searched, and the persons or things to be seized."
But Mr. Hentoff sees the surveillance state as a threat to free speech, too. About a
year ago he went up to Harvard to speak to a class. He asked, he recalled: "How many of you realize
the connection between what's happening with the Fourth Amendment with the First Amendment?" He told
the students that if citizens don't have basic privacies-firm protections against the search and
seizure of your private communications, for instance-they will be left feeling "threatened." This
will make citizens increasingly concerned "about what they say, and they do, and they think." It
will have the effect of constricting freedom of expression. Americans will become careful about what
they say that can be misunderstood or misinterpreted, and then too careful about what they say that
can be understood. The inevitable end of surveillance is self-censorship.
All of a sudden, the room became quiet. "These were bright kids, interested, concerned, but they
hadn't made an obvious connection about who we are as a people." We are "free citizens in a self-governing
republic."
Mr. Hentoff once asked Justice William Brennan "a schoolboy's question": What is the most important
amendment to the Constitution? "Brennan said the First Amendment, because all the other ones come
from that. If you don't have free speech you have to be afraid, you lack a vital part of what it
is to be a human being who is free to be who you want to be." Your own growth as a person will in
time be constricted, because we come to know ourselves by our thoughts.
He wonders if Americans know who they are compared to what the Constitution says they are.
Mr. Hentoff's second point: An entrenched surveillance state will change and distort the balance
that allows free government to function successfully. Broad and intrusive surveillance will,
definitively, put government in charge. But a republic only works, Mr. Hentoff notes, if public officials
know that they-and the government itself-answer to the citizens. It doesn't work, and is distorted,
if the citizens must answer to the government. And that will happen more and more if the government
knows-and you know-that the government has something, or some things, on you. "The bad thing is you
no longer have the one thing we're supposed to have as Americans living in a self-governing republic,"
Mr. Hentoff said. "The people we elect are not your bosses, they are responsible to us." They must
answer to us. But if they increasingly control our privacy, "suddenly they're in charge if they know
what you're thinking."
This is a shift in the democratic dynamic. "If we don't have free speech then what can we do if
the people who govern us have no respect for us, may indeed make life difficult for us, and in fact
belittle us?"
If massive surveillance continues and grows, could it change the national character? "Yes, because
it will change free speech."
What of those who say, "I have nothing to fear, I don't do anything wrong"? Mr. Hentoff suggests
that's a false sense of security.
"When you have this amount of privacy invasion put into these huge data banks, who knows
what will come out?"
Or can be made to come out through misunderstanding the data, or finagling, or mischief of one
sort or another.
"People say, 'Well I've done nothing wrong so why should I worry?' But that's too easy a way
to get out of what is in our history-constant attempts to try to change who we are as Americans."
Asked about those attempts, he mentions the Alien and Sedition Acts of 1798, the Red Scare
of the 1920s and the McCarthy era. Those times and incidents, he says, were more than specific scandals
or news stories, they were attempts to change our nature as a people.
What of those who say they don't care what the federal government does as long as it keeps
us safe? The threat of terrorism is real, Mr. Hentoff acknowledges. Al Qaeda is still here, its networks
are growing. But you have to be careful about who's running U.S. intelligence and U.S. security,
and they have to be fully versed in and obey constitutional guarantees.
"There has to be somebody supervising them who knows what's right. . . . Terrorism is not going
to go away. But we need someone in charge of the whole apparatus who has read the Constitution."
Advances in technology constantly up the ability of what government can do. Its technological
expertise will only become deeper and broader.
"They think they're getting to how you think. The technology is such that with the masses of
databases, then privacy will get even weaker."
Mr. Hentoff notes that J. Edgar Hoover didn't have all this technology. "He would be so envious
of what NSA can do."
Notable quotes:
"... Far from being seen as the guardian of a free and open online medium, the US has been painted as an oppressor, cynically using its privileged position to spy on foreign nationals. The result, warn analysts, could well be an acceleration of a process that has been under way for some time as other countries ringfence their networks to protect their citizens' data and limit the flow of information. ..."
"... At the most obvious level, the secret data-collection efforts being conducted by the US National Security Agency threaten to give would-be censors of the internet in authoritarian countries rhetorical cover as they put their own stamp on their local networks. ..."
"... But the distrust of the US that the disclosures are generating in the democratic world, including in Europe , are also likely to have an impact. From the operation of a nation's telecoms infrastructure to the regulation of the emerging cloud computing industry, changes in the architecture of networks as countries seek more control look set to cause a sea change in the broader internet. ..."
Revelations about
US
surveillance of the global internet – and the part played by some of the biggest American internet
companies in facilitating it – have stirred angst around the world.
Far from being seen as the guardian of a free and open online medium, the US has been painted as
an oppressor, cynically using its privileged position to spy on foreign nationals. The result, warn
analysts, could well be an acceleration of a process that has been under way for some time as other
countries ringfence their networks to protect their citizens' data and limit the flow of information.
"It is difficult to imagine the internet not becoming more compartmentalised and Balkanised," says
Rebecca MacKinnon, an expert on online censorship. "Ten years from now, we will look back on the
free and open internet" with nostalgia, she adds.
At the most obvious level, the secret data-collection efforts being conducted by the US National
Security Agency threaten to give would-be censors of the
internet in authoritarian countries rhetorical cover as they put their own stamp on their local
networks.
But the distrust of the US that the disclosures are generating in the democratic world,
including
in Europe, are also likely to have an impact. From the operation of a nation's telecoms infrastructure
to the regulation of the emerging cloud computing industry, changes in the architecture of networks
as countries seek more control look set to cause a sea change in the broader internet.
National security state gone rogue is fascism. Frankly, I don't see evidence of huge abuse
of US liberties. But I do see our foreign policy distorted by a counter-terror obsession
Notable quotes:
"... the government's interpretation of that law ..."
"... "One reports a crime; and one commits a crime." ..."
"... but does not include differences of opinion concerning public policy matters ..."
Jump to comments (118)
Two weeks ago, the Guardian began publishing a series of eye-opening revelations about the National
Security Agency and its surveillance
efforts both in the United States
and overseas. These stories raised long-moribund and often-ignored questions about the pervasiveness
of government surveillance and the extent to which privacy rights are being violated by this secret
and seemingly unaccountable security apparatus.
However, over the past two weeks, we've begun to get a clearer understanding of the story and
the implications of what has been published – informed in part by a new-found (if forced upon them)
transparency from the intelligence community. So here's one columnist's effort to sort the wheat
from the chaff and offer a few answers to the big questions that have been raised.
These revelations are a big deal, right?
To fully answer this question, it's important to clarify the revelations that have sparked such
controversy. The Guardian (along with the Washington Post) has broken a number of stories, each of
which tells us very different things about what is happening inside the US government around matters
of surveillance and cyber operations. Some are relatively mundane, others more controversial.
The story that has shaped press coverage and received the most attention was the first one – namely,
the publication of a judicial order from the
Fisa court to Verizon that
indicated the US is "hoovering" up millions of phone records (so-called "metadata") into a giant
NSA database. When it broke, the
story was quickly portrayed as a frightening tale of government overreach and violation of privacy
rights. After all, such metadata – though it contains no actual content – can be used rather easily
as a stepping-stone to more intrusive forms of surveillance.
But what is the true extent of the story here: is this picture of government Big Brotherism correct
or is this massive government surveillance actually quite benign?
First of all, such a collection of data is not, in and of itself, illegal. The
Obama administration
was clearly acting within the constraints of federal law and received judicial approval for this
broad request for data. That doesn't necessarily mean that the law is good or that the
government's interpretation of that law is not too broad, but unlike the Bush "warrantless wiretapping"
stories of several years ago, the US government is here acting within the law.
The real question that should concern us is one raised by the
TV writer David Simon in a widely cited blogpost looking at the issues raised by the Guardian's
reporting, namely:
"Is government accessing the data for the legitimate public safety needs of the society, or
are they accessing it in ways that abuse individual liberties and violate personal privacy – and
in a manner that is unsupervised."
We know, for example, that the NSA is required to abide by laws that prevent the international
targeting of American citizens (you can
read more about that
here). So, while metadata about phone calls made can be used to discover information about the
individuals making the calls, there are "minimization" rules, procedures and laws that guide the
use of such data and prevent possible abuse and misuse of protected data.
The minimization procedures used by the NSA are controlled by secret Fisa courts. In fact,
last year, the Fisa
court ruled that these procedures didn't pass constitutional muster and had to be rewritten.
Sure, the potential for abuse exists – but so, too, does the potential for the lawful use of metadata
in a way that protects the privacy of individual Americans – and also assists the US government in
pursuit of potential terrorist suspects. Of course, without information on the specific procedures
used by the NSA to minimize the collection of protected data, it is impossible to know that no laws
are being broken or no abuse is occurring.
In that sense, we have to take the government's word for it. And that is especially problematic
when you consider the Fisa court decisions authorizing this snooping are secret and the congressional
intelligence committees tasked with conducting oversight tend to be toothless.
But assumptions of bad faith and violations of privacy by the US government are just that assumptions.
When President Obama says that the NSA is not violating privacy rights because it would be against
the law, we can't simply disregard such statements as self-serving. Moreover, when one considers
the privacy violations that Americans willingly submit to at airports, what personal data they give
to the government in their tax returns, and what is regularly posted voluntarily on Facebook, sent
via email and searched for online, highly-regulated data-mining by the NSA seems relatively tame.
Edward Snowden:
is he a hero or a traitor?
One of the key questions that have emerged over this story is the motivation of the leaker in
question, Edward Snowden. In
his initial public interview, with Glenn Greenwald on 9 June, Snowden explained his actions,
in part, thus:
"I'm willing to sacrifice because I can't in good conscience allow the US government to destroy
privacy, internet freedom and basic liberties for people around the world with this massive surveillance
machine they're secretly building."
Now, while one can argue that Snowden's actions do not involve personal sacrifice, whether they
are heroic is a much higher bar to cross. First of all, it's far from clear that the US government
is destroying privacy, internet freedom and basic liberties for people around the world.
Snowden may sincere about being "valiant for truth", but he wouldn't be the first person to believe
himself such and yet be wrong.
Second, one can make the case that there is a public interest in knowing that the US is collecting
reams of phone records, but where is the public interest – and indeed, to Snowden's own justification,
the violation of privacy – in leaking a presidential directive on cyber operations or leaking that
the US is spying on the Russian president?
The latter is both not a crime it's actually what the NSA was established to do! In his
recent online chat hosted by the Guardian, Snowden suggested that the US should not be spying
on any country with whom it's not formally at war. That is, at best, a dubious assertion, and one
that is at odds with years of spycraft.
On the presidential directive on cyber operations, the damning evidence that Snowden revealed
was that President Obama has asked his advisers to create a list of potential targets for cyber operations
– but such planning efforts are rather routine contingency operations. For example, if the
US military drew up war
plans in case conflict ever occurred between the US and North Korea – and that included offensive
operations – would that be considered untoward or perhaps illegitimate military planning?
This does not mean, however, that Snowden is a traitor. Leaking classified data is a serious offense,
but treason is something else altogether.
The problem for Snowden is that he has now also
leaked classified information about ongoing US intelligence-gathering efforts to foreign governments,
including China and Russia. That may be crossing a line, which means that the jury is still out on
what label we should use to describe Snowden.
Shouldn't Snowden be protected as a whistleblower?
This question of leakers v whistleblowers has frequently been conflated in the public reporting
about the NSA leak (and many others). But this is a crucial error. As Tara Lee, a lawyer at the law
firm DLA Piper, with expertise in defense industry and national security litigation said to me there
is an important distinction between leakers and whistleblowers, "One reports a crime; and one
commits a crime."
Traditionally (and often technically), whistleblowing refers to specific actions that are taken
to bring to attention illegal behavior, fraud, waste, abuse etc. Moreover, the US government provides
federal employees and contractors with the protection to blow the whistle on wrongdoing. In the case
of Snowden, he could have gone to the inspector general at the Department of Justice or relevant
congressional committees.
From all accounts, it appears that he did not go down this path. Of course, since the material
he was releasing was approved by the Fisa court and had the sign-off of the intelligence committee,
he had good reason to believe that he would have not received the most receptive hearing for his
complaints.
Nevertheless, that does not give him carte blanche to leak to the press – and certainly doesn't
give him carte blanche to leak information on activities that he personally finds objectionable but
are clearly legal. Indeed, according to the
Intelligence Community
Whistleblower Protection Act (ICWPA), whistleblowers can make complaints over matter of what
the law calls "urgent concern", which includes "a serious or flagrant problem, abuse, violation of
law or executive order, or deficiency relating to the funding, administration, or operations of an
intelligence activity involving classified information, but does not include differences of opinion
concerning public policy matters [my italics]."
In other words, simply believing that a law or government action is wrong does not give one the
right to leak information; and in the eyes of the law, it is not considered whistleblowing. Even
if one accepts the view that the leaked Verizon order fell within the bounds of being in the "public
interest", it's a harder case to make for the presidential directive on cyber operations or the eavesdropping
on foreign leaders.
The same problem is evident in the incorrect description of
Bradley Manning as
a whistleblower. When you leak hundreds of thousands of documents – not all of which you reviewed
and most of which contain the mundane and not illegal diplomatic behavior of the US government –
you're leaking. Both Manning and now Snowden have taken it upon themselves to decide what
should be in the public domain; quite simply, they don't have the right to do that. If every government
employee decided actions that offended their sense of morality should be leaked, the government would
never be able to keep any secrets at all and, frankly, would be unable to operate effectively.
So, like Manning, Snowden is almost certainly not a whistleblower, but rather a leaker. And that
would mean that he, like Manning, is liable to prosecution for leaking classified material.
Are Democrats hypocrites
over the NSA's activities?
A couple of days ago, my Guardian colleague, Glenn Greenwald made the following assertion:
"The most vehement defenders of NSA surveillance
have been, by far, Democratic (especially Obama-loyal) pundits. One of the most significant
aspects of the Obama legacy has been the transformation of Democrats from pretend-opponents of
the Bush "war on terror" and national security state into their biggest proponents."
This is regular line of argument from Glenn, but it's one that, for a variety of reasons, I believe
is not fair. (I don't say this because I'm an Obama partisan – though I may be called one for writing
this.)
First, the lion's share of criticism of these recent revelations has come, overwhelmingly, from
Democrats and, indeed, from many of the same people, including Greenwald, who were up in arms when
the so-called warrantless wiretapping program was revealed in 2006. The reality is that outside a
minority of activists, it's not clear that many Americans – Democrats or
Republicans –
get all that excited about these types of stories. (Not that this is necessarily a good thing.)
Second, opposition to the Bush program was two-fold: first, it was illegal and was conducted with
no judicial or congressional oversight; second, Bush's surveillance policies did not occur in a vacuum
– they were part of a pattern of law-breaking, disastrous policy decisions and Manichean rhetoric
over the "war on terror". So, if you opposed the manner in which Bush waged war on the "axis of evil",
it's not surprising that you would oppose its specific elements. In the same way, if you now support
how President Obama conducts counter-terrorism efforts, it's not surprising that you'd be more inclined
to view specific anti-terror policies as more benign.
Critics will, of course, argue – and rightly so – that we are a country of laws first. In which
case it shouldn't matter who is the president, but rather what the laws are that govern his or her
conduct. Back in the world of political reality, though, that's not how most Americans think of their
government. Their perceptions are defined in large measure by how the current president conducts
himself, so there is nothing at all surprising about Republicans having greater confidence in a Republican
president and Democrats having greater confidence in a Democratic one, when asked about specific
government programs.
Beyond that, simply having greater confidence in President Obama than President Bush to wield
the awesome powers granted the commander-in-chief to conduct foreign policy is not partisanship.
It's common sense.
George Bush was, undoubtedly,
one of the two or three worst foreign policy presidents in American history (and arguably, our worst
president, period). He and Dick Cheney habitually broke the law, including but not limited to the
abuse of NSA surveillance. President Obama is far from perfect: he made the terrible decision to
surge in Afghanistan, and
he's fought two wars of dubious legality in Libya and Pakistan, but he's very far from the sheer
awfulness of the Bush/Cheney years.
Unless you believe the US should have no NSA, and conduct no intelligence-gathering in the fight
against terrorism, you have to choose a president to manage that agency. And there is nothing hypocritical
or partisan about believing that one president is better than another to handle those responsibilities.
Has NSA surveillance prevented terrorist attacks, as claimed?
In congressional testimony this week, officials from the Department of Justice and the
NSA argued that surveillance efforts stopped "potential terrorist events over 50 times since
9/11". Having spent far too many years listening to public officials describe terrifying terror plots
that fell apart under greater scrutiny, this assertion sets off for me a set of red flags (even though
it may be true).
I have no doubt that NSA surveillance has contributed to national security investigations, but
whether it's as extensive or as vital as the claims of government officials is more doubtful. To
be honest, I'm not sure it matters. Part of the reason the US government conducts NSA surveillance
in the first place is not necessarily to stop every potential attack (though that would be nice),
but to deter potential terrorists from acting in the first place.
Critics of the program like to argue that "of course, terrorists know their phones are being tapped
and emails are being read", but that's kind of the point. If they know this, it forces them to choose
more inefficient means of communicating, and perhaps to put aside potential attacks for fear of being
uncovered.
We also know that not every terrorist has the skills of a Jason Bourne. In fact, many appear to
be not terribly bright, which means that even if they know about the NSA's enormous dragnet, it doesn't
mean they won't occasionally screw up and get caught.
Yet, this gets to a larger issue that is raised by the NSA revelations.
When is enough counter-terrorism enough?
Over the past 12 years, the US has developed what can best be described as a dysfunctional relationship
with terrorism. We've become obsessed with it and with a zero-tolerance approach to stopping it.
While the former is obviously an important goal, it has led the US to take steps that not only undermine
our values (such as torture), but also make us weaker (the invasion of
Iraq, the surge in Afghanistan,
etc).
To be sure, this is not true of every anti-terror program of the past dozen years. For example,
the US does a better job of sharing intelligence among government agencies, and of screening those
who are entering the country. And military efforts in the early days of the "war on terror" clearly
did enormous damage to al-Qaida's capabilities.
In general, though, when one considers the relatively low risk of terrorist attacks – and the
formidable defenses of the United States – the US response to terrorism has been one of hysterical
over-reaction. Indeed, the balance we so often hear about when it comes to protecting privacy while
also ensuring security is only one part of the equation. The other is how do we balance the need
to stop terrorists (who certainly aspire to attack the United States) and the need to prevent anti-terrorism
from driving our foreign policy to a disproportionate degree. While the NSA revelations might not
be proof that we've gone too far in one direction, there's not doubt that, for much of the past 12
years, terrorism has distorted and marred our foreign policy.
Last month, President Obama gave a seminal speech at the National Defense University, in which
he essentially declared the "war on terror" over. With troops coming home from Afghanistan, and drone
strikes on the decline, that certainly seems to be the case. But as the national freakout over the
Boston Marathon bombing – and the extraordinary over-reaction of a city-wide lockdown for one wounded
terrorist on the loose – remind us, we still have a ways to go.
Moreover, since no politician wants to find him- or herself in a situation after a terrorist attack
when the criticism "why didn't you do more?" can be aired, that political imperative of zero tolerance
will drive our counterterrorism policies. At some point, that needs to end.
In fact, nine years ago, our current secretary of state, John Kerry, made this exact point; it's
worth reviewing his words:
"We have to get back to the place we were, where terrorists are not the focus of our lives,
but they're a nuisance I know we're never going to end prostitution. We're never going to end
illegal gambling. But we're going to reduce it, organized crime, to a level where it isn't on
the rise. It isn't threatening people's lives every day, and fundamentally, it's something that
you continue to fight, but it's not threatening the fabric of your life.''
What the NSA revelations should spark is not just a debate on surveillance, but on the way we
think about terrorism and the steps that we should be willing to take both to stop it and ensure
that it does not control us. We're not there yet.
007Prometheus
No GCHQ - MI5 - MI6 - NSA - CIA - FBI etc........... ad nausem!
How many Billions / Trillions are spent on these services? If 11/9 and 7/7 were homegrown attacks,
then i think, they will take us all down with them.
NOTaREALmerican
@007Prometheus
Re: How many Billions / Trillions are spent on these services?
The wonderful thing about living in a "Keynesian" perpetually increasing debt paradise is you
NEVER have to say you can't afford anything. (Well, unless you want to say it, but if you do it's
just political bullshit).
So, to answer your question... A "Keynesian" never asks how much, just how much do you want.
bloopie2
"Frankly, I don't see evidence of huge abuse of US liberties"
Just wait until they come for you.
bloopie2
"When one considers the privacy violations that Americans willingly submit to at airports,
what personal data they give to the government in their tax returns, and what is regularly posted
voluntarily on Facebook, sent via email and searched for online, highly-regulated data-mining
by the NSA seems relatively tame."
Dear Sir: Please post your email addresses, bank accounts, and passwords. We'd like to look
at everything.
Got a problem with that?
Tonieja
"When one considers the privacy violations that Americans willingly submit to at airports,
what personal data they give to the government in their tax returns, and what is regularly
posted voluntarily on Facebook, sent via email and searched for online [...]"
Wow! I don't really care about my personal email. I do care about all political activists,
journalists, lawyers etc. That a journalist would support Stasi style surveillance state is astonishing.
gisbournelove
I wish I had the time to go through this article and demolish it sentence by sentence as it
so richly deserves, but at the moment I don't. Instead, might I suggest to the author that he
go to the guardian archive, read every single story about this in chronological order and then
read every damn link posted in the comment threads on the three most recent stories.
Most especially the links in the comment threads. If after that, he cannot see why we "civil
libertarian freaks" are not just outraged, but frightened, he frankly lacks both historical knowledge
and any ability to analyze the facts that are staring him in the face. I can't believe I am going
to have to say this again but here goes: YOU do not get to give away my contitutional rights,
Mr. Cohen.
I don't give a shit how much you trust Obama compared to dubya. The Bill of Rights states in
clear, unambiguous language what the Federal government may NOT do do its citizens no matter WHO
is president.
goodkurtz
Michael Cohen
Frankly, I don't see evidence of huge abuse of US liberties.
Well of course you wont see them.
But the abuses are very probably already happening on a one to one basis in the same shadows in
which the intelligence was first gathered.
Rusty tell us of Android hacking by the Chinese and today we learn the iphone has issues too
http://bgr.com/2016/11/17/iphone-security-secret-call-history-icloud/
"Russian security firm says iPhone secretly logs all your phone calls"
By Mike Wehner...Nov 17, 2016...10:36 AM
"A Russian security firm is casting doubt on just how big of an ally Apple is when it comes to
consumer privacy. In a new report, the company alleges that Apple's iCloud retains the entire call
history of every iPhone for as long as four months, making it an easy target for law enforcement
and surveillance.
The firm, Elcomsoft, discovered that as long as a user has iCloud enabled, their call history
is synced and stored. The log includes phone numbers, dates and durations of the calls, and even
missed calls, but the log doesn't stop there; FaceTime call logs, as well as calls from apps that
utilize the "Call History" feature, such as Facebook and WhatsApp, are also stored.
There is also apparently no way to actually disable the feature without disabling iCloud entirely,
as there is no toggle for call syncing.
"We offer call history syncing as a convenience to our customers so that they can return calls
from any of their devices," an Apple spokesperson told The Intercept via email."Device data is encrypted
with a user's passcode, and access to iCloud data including backups requires the user's Apple ID
and password. Apple recommends all customers select strong passwords and use two-factor authentication."
But security from unauthorized eyes isn't what users should be worrying about, according to former
FBI agent and computer forensics expert Robert Osgood. "Absolutely this is an advantage [for law
enforcement]," Osgood told The Intercept. ""Four months is a long time [to retain call logs]. It's
generally 30 or 60 days for telecom providers, because they don't want to keep more [records] than
they absolutely have to."
If the name Elcomsoft sounds familiar, it's because the company's phone-cracking software was
used by many of the hackers involved in 2014's massive celebrity nudes leak. Elcomsoft's "Phone Breaker"
software claims the ability to crack iCloud backups, as well as backup files from Microsoft OneDrive
and BlackBerry."
Notable quotes:
"... "Top US intelligence official: I submitted my resignation" As of January 20th or so. When he was going to be gone anyway. Just had to get his name in the news one more time. ..."
"... Clapper has been like a difficult to eradicate sexually transmitted disease in the intelligence community. Unfortunately, I suspect he may have already infected others who will remain and pass it around. ..."
paulmeli
November 17, 2016 at 3:00 pm
"Top US intelligence official: I submitted my resignation" As of January 20th or so. When he was going to be gone anyway. Just had to get his name in the news one more time.
Peter Pan
November 17, 2016 at 6:37 pm
Clapper has been like a difficult to eradicate sexually transmitted disease in the intelligence
community. Unfortunately, I suspect he may have already infected others who will remain and pass
it around.
fresno dan
November 17, 2016 at 6:54 pm
paulmeli
November 17, 2016 at 3:00 pm
So, is Obama gonna pardon him?
Silly me, I keep forgetting that indisputable violations of the law are not prosecuted when done
by those at the top
Notable quotes:
"... What if the disk is passworded? What about that not all systems are exclusively for business/corporate use (see also BYOD) and therefore may be tuned to varying security postures owing to other factors? ..."
"... Physical access ≠ game over. Physical access + unguarded time + experience + tooling = game over. One used to could safely leave someone alone with their computer while one went to the kitchen for a glass of water. Now this tooling has made the time and experience components a bit less relevant to successful, quick pwnage with few or no tracks. Neato! ..."
LarryB
November 17, 2016 at 2:59 pm
The "Poison Tap" is not really that big of deal. It's usually trivially easy
to break into any computer that you can physically access. You can boot from a
CD or USB drive, for instance, or even just steal the hard drive. Security on USB
needs to be improved, but this is not even close to being the end of the world.
Knifecatcher
November 17, 2016 at 4:07 pm
+1. If someone has direct physical access to your device – PC or smartphone
– you're pretty much hosed.
Daryl
November 17, 2016 at 6:30 pm
Yep. Physical access is root access.
River
November 17, 2016 at 7:35 pm
If you have the time with the physical machine anyway.
I could see kids having fun with this though. Going into a box store that has computers on display,
getting access (even better if they have a web cam on it). Upload porn or shocking material and showing
the customers and watching/recording the reactions and putting it on youtube.
Or more nefarious, the same thing but for casing a store (limited vantage from the web cam .but
may better than nothing).
Etc. lots you could do and more importantly not a lot of skill required. Lower bar for entry for
hacking mischief and a low cost.
hunkerdown
November 17, 2016 at 7:51 pm
LarryB, and how long will that take you? And will you have the computer back
together by the time they see you? And will logs suggest anything funny happened
around that time? What if the disk is passworded? What about that not all systems
are exclusively for business/corporate use (see also BYOD) and therefore may
be tuned to varying security postures owing to other factors?
Physical access ≠ game over. Physical access + unguarded time + experience + tooling = game over.
One used to could safely leave someone alone with their computer while one went to the kitchen for
a glass of water. Now this tooling has made the time and experience components a bit less relevant
to successful, quick pwnage with few or no tracks. Neato!
A widespread problem
In the last few years, the Federal Trade Commission has sued more than dozen debt relief companies.
"They simply lie to consumers," says the FTC's Alice Hrdy.
FTC ad IRS investigators have also found some counseling services that claim to be non-profit
when they are actually a for-profit company. The non-profit pitch can make a potential client feel
confident about signing up for the service. "They're preying on the consumer's trust," Hrdy says.
Some of the bad apples in this industry mislead people about their charges. "They either say there
are no fees involved or just a small fee," Hrdy explains. Sometimes, they don't mention fees at all.
Bruce, who lives near Seattle, signed up with a company that promised to lower his interest rates.
He was told to send them a check for $265.
"It was my clear understanding that money was going to pay off my credit card bills," Bruce told
me. It turned out to be a "referral fee" to find him a company that would supposedly help him.
"It was a nasty experience," Bruce says. "They basically stole my money."
Warning: Debt settlement programs
Some companies now claim they can negotiate a one-time settlement with all of your creditors that
will reduce your principal by as much as 50 to 70 percent. By doing this, they say, your monthly
payments will drop dramatically.
"That is virtually impossible under any circumstances," says Travis Plunkett, Legislative Director
of the Consumer Federation of America. That's why CFA warns consumers not to use debt settlement
programs. "They are promising something they can't deliver," Plunkett says.
Credit counselors - a better option
Charles Helms, president of Consumer Counseling Northwest, sees a lot of people who have been burned
by these phony debt relief programs. "It's horrible," he says. Because most of them have a large
up-front fee, they'll take anyone who can pay.
"Their goal is to get you to sign up, not to successfully complete the program," Helms says. "So
here's someone who is financially damaged to begin with and then these companies just go out and
take the last of their resources and kill any hope they have of getting out of that situation."
With a legitimate credit counselor, there is no right answer for everyone. They sit down with
you and give you a free and objective assessment of your financial situation. At Credit Counseling
Northwest, they saw 6,000 people last year and found that debt management was the right option for
only 19 percent of them. The rest were given a plan to work things out on their own.
With a customized consolidated payment plan you should be able to pay off your credit card debt
in 3 to 5 years. You write the counseling agency one check each month and they pay all your creditors.
Do your homework
Facing mounting bills can be frightening, but getting debt relief is not a decision that should be
based on hearing a radio commercial or getting a sales call. You want to find an organization that
will design a debt relief plan specifically for you.
Shop around. Compare a couple of services and get a feel for how they operate. The credit counselor
should spend at least 20 to 30 minutes with you in order to get a complete picture of your finances.
If they don't do that, you're not really getting any counseling.
Ask a lot of questions and get those answers in writing. Find out about the fees. The Consumer
Federation of America says you shouldn't pay more than $50 for the set-up fee and no more than a
$25 monthly maintenance fee. If the agency is vague or reluctant to talk about fees, go someplace
else.
Don't rely on names or the claim of a non-profit status. Check them out with the Better Business
Bureau or your local consumer protection office.
By doing your homework you should be able to find a service that doesn't over-charge or over-promise.
Here's a good place to start:
The National
Foundation for Credit Counseling . They'll help you find a certified counselor near you.
More Information:
This neocon propagandists (or more correctly neocon provocateur) got all major facts wrong. And
who unleashed Flame and
Stuxnet I would like to ask him.
Was it Russians? And who invented the concept of "color revolution" in which influencing of election
was the major part of strategy ? And which nation instituted the program of covert access to email boxes
of all major webmail providers? He should study the history of malware and the USA covert operations
before writing this propagandist/provocateur opus to look a little bit more credible...
Notable quotes:
"... Email, a main conduit of communication for two decades, now appears so vulnerable that the nation seems to be wondering whether its bursting inboxes can ever be safe. ..."
The 2016 presidential race will be remembered for many ugly moments, but the most lasting historical
marker may be one that neither voters nor American intelligence agencies saw coming: It is the first
time that a foreign power has unleashed cyberweapons to disrupt, or perhaps influence, a United States
election.
And there is a foreboding sense that, in elections to come, there is no turning back.
The steady drumbeat of allegations of Russian troublemaking - leaks from stolen emails and probes
of election-system defenses - has continued through the campaign's last days. These intrusions, current
and former administration officials agree, will embolden other American adversaries, which have been
given a vivid demonstration that, when used with some subtlety, their growing digital arsenals can
be particularly damaging in the frenzy of a democratic election.
"Most of the biggest stories of this election cycle have had a cybercomponent to them - or the
use of information warfare techniques that the Russians, in particular, honed over decades," said
David Rothkopf, the chief executive and editor of Foreign Policy, who has written two histories of
the National Security Council. "From stolen emails, to WikiLeaks, to the hacking of the N.S.A.'s
tools, and even the debate about how much of this the Russians are responsible for, it's dominated
in a way that we haven't seen in any prior election."
The magnitude of this shift has gone largely unrecognized in the cacophony of a campaign dominated
by charges of groping and pay-for-play access. Yet the lessons have ranged from the intensely personal
to the geostrategic.
Email, a main conduit of communication for two decades, now appears so vulnerable that the
nation seems to be wondering whether its bursting inboxes can ever be safe. Election systems,
the underpinning of democracy, seem to be at such risk that it is unimaginable that the United States
will go into another national election without treating them as "critical infrastructure."
But President Obama has been oddly quiet on these issues. He delivered a private warning to President
Vladimir V. Putin of Russia during their final face-to-face encounter two months ago, aides say.
Still, Mr. Obama has barely spoken publicly about the implications of foreign meddling in the election.
His instincts, those who have worked with him on cyberissues say, are to deal with the problem by
developing new norms of international behavior or authorizing covert action rather than direct confrontation.
After a series of debates in the Situation Room, Mr. Obama and his aides concluded that any public
retaliation should be postponed until after the election - to avoid the appearance that politics
influenced his decision and to avoid provoking Russian counterstrikes while voting is underway. It
remains unclear whether Mr. Obama will act after Tuesday, as his aides hint, or leave the decision
about a "proportional response" to his successor.
Cybersleuths, historians and strategists will debate for years whether Russia's actions reflected
a grand campaign of interference or mere opportunism on the part of Mr. Putin. While the administration
has warned for years about the possibility of catastrophic attacks, what has happened in the past
six months has been far more subtle.
Russia has used the techniques - what they call "hybrid war," mixing new technologies with old-fashioned
propaganda, misinformation and disruption - for years in former Soviet states and elsewhere in Europe.
The only surprise was that Mr. Putin, as he intensified confrontations with Washington as part of
a nationalist campaign to solidify his own power amid a deteriorating economy, was willing to take
them to American shores.
The most common theory is that while the Russian leader would prefer the election of Donald J.
Trump - in part because Mr. Trump has suggested that NATO is irrelevant and that the United States
should pull its troops back to American shores - his primary motive is to undercut what he views
as a smug American sense of superiority about its democratic processes.
Madeleine K. Albright, a former secretary of state who is vigorously supporting Hillary Clinton,
wrote recently that Mr. Putin's goal was "to create doubt about the validity of the U.S. election
results, and to make us seem hypocritical when we question the conduct of elections in other countries."
If so, this is a very different use of power than what the Obama administration has long prepared
the nation for.
Four years ago, Leon E. Panetta, the defense secretary at the time, warned of an impending "cyber
Pearl Harbor" in which enemies could "contaminate the water supply in major cities or shut down the
power grid across large parts of the country," perhaps in conjunction with a conventional attack.
Molin | Nov 5, 2016 7:21:49 AM |
52
Obama hack Russia openly,
"Russia expects Washington to provide an explanation after a report claimed that Pentagon cyber-offensive
specialists have hacked into Russia's power grids, telecommunications networks, and the Kremlin's
command systems for a possible sabotage."
https://www.rt.com/news/365423-russia-us-hacker-grid/
Presenting...the Clinton IT Department! This has not been an especially ennobling election.
Or a rewarding one. Or even entertaining. Pretty much everything about 2016 has been boorish and
grotesque. But finally it is time to laugh.
This has not been an especially ennobling election. Or a rewarding one. Or even entertaining.
Pretty much everything about 2016 has been boorish and grotesque. But finally it is time to laugh.
Ladies and gentlemen, I present the Clinton IT department.
Over the weekend we finally found out how Clinton campaign honcho John Podesta's emails were hacked.
But first a couple disclaimers:
1) Yes, it's unpleasant to munch on the fruit of the poisoned tree. But this isn't a court of
law and you can't just ignore information that's dragged into the public domain.
2) We're all vulnerable to hackers. Even if you're a security nut who uses VPNs and special email
encryption protocols, you can be hacked. The only real security is the anonymity of the herd. Once
a hacker targets you, specifically, you're toast.
I'm a pretty tech-savvy guy and if the Chinese decided to hack my emails tonight, you'd have everything
I've ever written posted to Wikileaks before the sun was up tomorrow.
But that is … not John Podesta's situation.
What happened was this: On March 19, Podesta got what looked--kind of, sort of--like an email
from Google's Gmail team. The email claimed that someone from the Ukraine had tried to hack into
Podesta's Gmail account and that he needed to change his password immediately.
This is what's called a "phishing" scam, where hackers send legitimate-looking emails that, when
you click on the links inside them, actually take you someplace dangerous. In Podesta's case, there
was a link that the email told him to click in order to change his password.
This was not an especially good bit of phishing.
Go have a look yourself. The email calls Podesta by his first name. It uses bit.ly as a link
shortener. Heck, the subject line is the preposterous "*someone has your password*". Why would Google
say "someone has your password?" They wouldn't. They'd say that there had been log-in attempts that
failed two-step authentication, maybe. Or that the account had been compromised, perhaps. If you've
spent any time using email over the last decade, you know exactly how these account security emails
are worded.
And what's more, you know that you never click on the link in the email. If you get a notice from
your email provider or your bank or anyone who holds sensitive information of yours saying that your
account has been compromised, you leave the email, open your web browser, type in the URL of the
website, and then manually open your account information. Again, let me emphasize: You never click
on the link in the email!
But what makes this story so priceless isn't that John Podesta got fooled by an fourth-rate phishing
scam. After all, he's just the guy who's going to be running Hillary Clinton's administration. What
does he know about tech? And Podesta, to his credit, knew what he didn't know: He emailed the Clinton
IT help desk and said, Hey, is this email legit?
And the Clinton tech team's response was: Hell yes!
No, really. Here's what they said: One member of the team responded to Podesta by saying "The
gmail one is REAL." Another answered by saying "This is a legitimate email. John needs to change
his password immediately."
It's like the Clinton IT department is run by 90-year-old grandmothers. I half-expect the next
Wikileaks dump to have an email from one Clinton techie to another asking for help setting their
VCR clock.
As the other guy likes to say, "only the best people."
mistah charley, ph.d. said...
30 October 2016 at 09:13 AM
Speaking also of Podesta's email, not Huma's, the following is interesting:
http://www.cnn.com/2016/10/28/politics/phishing-email-hack-john-podesta-hillary-clinton-wikileaks/index.html
Briefly, it seems Podesta received an email "You need to change your password", asked for professional advice from his
staff if it was legit, was told "Yes, you DO need to change your password", but then clicked on the link in the original email,
which was sent him with malicious intent, as he suspected at first and then was inappropriately reassured about - rather than
on the link sent him by the IT staffer.
Result - the "phishing" email got his password info, and the world now gets to see all his emails.
Personally, my hope is that Huma and HRC will be pardoned for all their crimes, by Obama, before he leaves office.
Then I hope that Huma's divorce will go through, and that once Hillary is sworn in she will at last be courageous enough to
divorce Bill (who actually performed the Huma-Anthony Weiner nuptials - you don't have to make these things up).
Then it could happen that the first same-sex marriage will be performed in the White House, probably by the minister of DC's
Foundry United Methodist Church, which has a policy of LBGQT equality. Or maybe Hillary, cautious and middle-of-the-road as usual,
will go to Foundry UMC sanctuary for the ceremony, recognizing that some Americans' sensibilities would be offended by having
the rite in the White House.
As Nobel Laureate Bob Dylan wrote, "Love is all there is, it makes the world go round, love and only love, it can't be denied.
No matter what you think about it, you just can't live without it, take a tip from one who's tried."
Notable quotes:
"... An important thing about that Time article regarding the Sony Hack is that it is almost two years old. Important because I'm still having to tell people that despite what the President and the government said North Korea didn't hack Sony because of a really bad movie, but that insiders did it for reasons that were never part of the media blitz about it. And believe me, considering that Clinton is lying through her teeth beyond even the government about this, I point this out a lot. ..."
"... Something that jumped out at me in December 2014 was a blog post by David E Martin. His blog post more or less laid out the whole game plan–and in so doing, I suspect he thwarted the planned story line. It was amazing to read that the whole plot had actually been presented to Congress years before. ..."
"... I'm inferring his intention in writing the post was to spill enough beans to prevent a catastrophic false flag event, as that is why he wrote his book "Coup d'Twelve" . (He spoke about this on numerous radio interviews at the time, and as also discussed it in person.) ..."
"... Never let an opportunity for a bit of Russian bashing go to waste it seems. Is there anything at all in the history of the entire world that the Russians aren't responsible for? ..."
Pat
October 26, 2016 at 2:21 pm
An important thing about that Time article regarding the Sony Hack is that it is almost two
years old. Important because I'm still having to tell people that despite what the President and
the government said North Korea didn't hack Sony because of a really bad movie, but that insiders
did it for reasons that were never part of the media blitz about it. And believe me, considering
that Clinton is lying through her teeth beyond even the government about this, I point this out
a lot.
TheCatSaid
October 26, 2016 at 8:32 pm
Something that jumped out at me in December 2014 was a blog post by David E Martin. His
blog post more or less laid out the whole game plan–and in so doing, I suspect he thwarted
the planned story line. It was amazing to read that the whole plot had actually been presented
to Congress years before.
I'm inferring his intention in writing the post was to spill enough beans to prevent a catastrophic
false flag event, as that is why he wrote his book
"Coup d'Twelve" . (He spoke about this on numerous radio interviews at the time, and as also
discussed it in person.)
Foy
October 26, 2016 at 9:09 pm
I had to laugh when I read this in the article though:
"A recent linguistic analysis cited in the New York Times found that the hackers' language
in threats against Sony was written by a native Russian speaker and not a native Korean speaker."
Never let an opportunity for a bit of Russian bashing go to waste it seems. Is there anything
at all in the history of the entire world that the Russians aren't responsible for?
allan
October 28, 2016 at 10:19 pm
Phishing for Fools, Hipster Edition:
Emails show how Clinton campaign chairman apparently hacked [AP]
New evidence appears to show how hackers earlier this year stole more than 50,000 emails
of Hillary Clinton's campaign chairman, an audacious electronic attack blamed on Russia's government
and one that has resulted in embarrassing political disclosures about Democrats in the final
weeks before the U.S. presidential election.
The hackers sent John Podesta an official-looking email on Saturday, March 19, that appeared
to come from Google. It warned that someone in Ukraine had obtained Podesta's personal Gmail
password and tried unsuccessfully to log in, and it directed him to a website where he should
"change your password immediately."
Podesta's chief of staff, Sara Latham, forwarded the email to the operations help desk of
Clinton's campaign, where staffer Charles Delavan in Brooklyn, New York, wrote back 25 minutes
later, "This is a legitimate email. John needs to change his password immediately."
But the email was not authentic. …
Lambert
Strether Post author
October 29, 2016 at 12:49 am
And if the ploy was that low-grade, that means that the Russki superbrains in the KGB didn't
have to be behind it. Dear Lord.
This really is a hubris followed by nemesis thing, isn't it? And how sad it is, how tragic,
that it was Brooklyn that brought Podesta down. Somehow I think Delavan is going to have
a hard time getting a job in politics again, but he did the country a great service.
TheCatSaid
October 29, 2016 at 1:17 pm
Social engineering wins again. This was something I learned about long ago when Black Box Voting.org
started (approx. 2004). It was one of the many vulnerabilities in various points of election systems,
both with paper and paperless. Very easy to get officials to reveal passwords that allowed access–that's
in addition to the corruption situations. (Or rather, the social engineering angle would be just
one of the tools used by insiders.)
All their arguments does not stand even entry level programmer scrutiny. Especially silly are "Russian
keyboard and timestamps" argument. As if, say Israelis or, say, Estonians, or any other country with
sizable Russian speaking population can't use those to direct investigation at the wrong track ;-).
If I were a Russian hacker trying to penetrate into DNC servers I would use only NSA toolkit and
libraries that I can find on black market. First on all they are reasonably good. the second that help
to direct people to in a wrong direction. and if knew Spanish or English or French reasonably well I
would use them exclusively. If not I would pay for translation of set of variables into those languages
and "forget" to delete symbol table in one of the module giving raw meat to idiots like those.
Actually you can find a lot of such people even in London, Paris, Madrid and NYC, and some of them
really do not like the US neoliberal administration with its unending wars of expansion of neoliberal
empire :-) But still they are considered to be "security expert". When you hear now the word "security
expert", please substitute it for "security charlatan" for better comprehensions -- that's almost always
the case about people posing as security experts for MSM. The only reliable exception are whistleblowers
-- those people sacrifices their lucrative carriers for telling the truth, so they can usually be trusted.
They might exaggerate things on the negative side, though. I personally highly respect William Binney.
The "regular" security expects especially from tiny, struggling security companies in reality they
are low paid propagandists amplifying the set of prepared talking point. The arguments are usually pretty
childish. BTW, after the USA/Israeli operation against Iran using Stixnet and Flame in Middle East,
complex Trojans are just commonplace and are actually available to more or less qualified hacker, or
even a unqualified person with some money and desire to take risks.
I especially like the phrase "beyond a reasonable doubt that the hack was in fact an operation of
the Russian state." Is not this a slander, or what ? Only two cagagiry of peopel: impetcils and paid
presstitutes has think about complex hacking operation origin "beyond reasonable doubt")
Oct 28, 2016 |
observer.com
Original title:
7 Reasons
Security Firms Believe the Russian State Hacked the DNC
Originally from: Bloomberg
• 10/26/16 1:02pm
How do we really know that the
breaches of the Democratic National Committee were conducted by organizations working on behalf
of the Russian state? With the CIA considering a major counterstrike against the superpower,
as NBC has reported , it's worthwhile for the public to measure how confident we can be that
Putin's government actually deserves retribution.
"When you're investigating a cybersecurity breach, no one knows whether you're a Russian hacker
or a Chinese hacker pretending to be a Russian hacker or even a U.S. hacker pretending to be a Chinese
hacker pretending to be a Russian hacker," reporter Jordan Robertson says during the third episode
of
a solid new podcast from Bloomberg, called "Decrypted." In the new episode, he and fellow reporter
Aki Ito
break down the facts that put security experts beyond a reasonable doubt that the hack was
in fact an operation of the Russian state.
Here are the key points:
- Familiar techniques. Crowdstrike
came in first, once DNC IT teams suspected breaches and recognized the techniques of the two
groups it calls Cozy Bear and Fancy Bear. Others refer to them as APT 28 and 29, where APT stands
for " Advanced
Persistent Threat ." Crowdstrike's co-founder Dmitri Alperovitch broke down his reasoning
on its blog , writing, "We've had lots of experience with both of these actors attempting
to target our customers in the past and know them well. In fact, our team considers them some
of the best adversaries out of all the numerous nation-state, criminal and hacktivist/terrorist
groups we encounter on a daily basis."
- Redundancy is Russian. The Crowdstrike post explains that the fact that two organizations
were inside and apparently not working together is consistent with Russian operations. " While
you would virtually never see Western intelligence agencies going after the same target without
de-confliction for fear of compromising each other's operations, in Russia this is not an uncommon
scenario," Alperovitch writes.
- Such nice code. Bloomberg turns to an ex-cop at one of the companies that Crowdstrike recruited
to check its work, Mike Buratowski at
Fidelis . His company put the code
discovered on DNC servers into a virtual environment to test it. "You look at the complexity of
what the malware was able to do. The fact that it had the ability to, basically, terminate itself
and wipe its tracks, hide its tracks. You know, that's not stuff you see in commoditized malware,
really," Buratowski said. In other words, this wasn't the kind of malware a cybercriminal could
buy on the black market. It was bespoke stuff made by teams of pros. Buratowski later calls the
code "elegant." Motherboard gives examples of
phishing
emails used , which showed careful attention to detail. Too good, he contends, for one person
or a small team to build.
- Russian keyboards and timestamps. Investigators found evidence in the code that it had been
written on a Russian style keyboard and
found timestamps across multiple pieces of code consistent with the Russian workday.
- Motive. This was an extremely complex hack that took a lot of time and effort. Again, the
Crowdstrike post helps here. It discusses evidence that the spies returned to the scene of the
crime repeatedly to change out code to avoid detection. Buratowski refers to it as an entity with
more operational discipline than an individual or a loose group could sustain. Which begs the
question: who but a nation-state would have sufficient motive to work that hard? Further, the
same groups were linked both to the hacks on
John Podesta and
Colin Powell , which suggests a multi-front initiative. That goes beyond what a hacker collective
might do for bragging rights or lulz.
- Information war. The DNC emails dropped the day before the party's national convention. "Releasing
the emails the evening before the convention started? Now you're looking at it like: that really
smacks of an information operation," Buratowski says.
-
Official attribution from the US government . Washington sees evidence of breaches all the
time. It seldom points the finger at specific states, the Decrypted team argues. The fact that
it has is powerful. "There are ways the government can really know what's going on," Robertson
said, "in a way that no private cybersecurity could ever match."
From there, the podcast asks: what does this hack mean for the U.S. election. They come to basically
the same conclusions that
the Observer did in September : voting systems are very safe-voter rolls are less so, but nation-states
probably want to discredit our system more than they want to change outcomes.
How sure can we be? Buratowski says, "Barring seeing someone at a keyboard or a confession, you're
relying on that circumstantial evidence." So, we can never really know for sure. In fact, even Crowdstrike's
attribution is based on prior experience, which assumes that they have attributed other hacks correctly
in the past. Former congressional staffer Richard Diamond
in USA Today argues that the hacks can be explained by bad passwords, but he also neglects
to counter Crowdstrike's descriptions of the sophisticated code placed inside the servers. From Bloomberg's
version of events, how the hackers got in was really the least interesting part of their investigation.
So what does it all mean? It's natural for political junkies to wonder if there might be further
disclosures coming before Election Day, but - if this is an information operation-it might be even
more disruptive to hold documents until after the election in order to throw doubt on our final choice.
Either way, further disclosures will probably come.
Notable quotes:
"... I find the whole hysteria over Russian hacking very one-sided. If the US takes it upon itself, out of sincere concern, to help out "moderates" in overthrowing a repressive, evil government in Syria, Libya and Iraq, maybe the same thing happening to the US itself is not that weird? Here is a tyrannical government with little regard for its demotivated and demoralized citizens who can not on their own displace it. This government threatens nuclear war and kills an unjustified number of its own citizens. Its public infrastructure is in ruins and oligarchy is everywhere. In the past the US has set the example for dealing with such troubled states; its time the doctor took his own medicine. ..."
"... Ahhhh, but that exactly where the "exceptional" clause kicks in. You see, America is justified in intervening in other countries' business because we see further, with a clearer gaze and a purer heart, than any other country in the world. Mired as they are in ignorance or inertia, no other country is qualified to judge us, and any mistakes that we make only occur because of the depths of our love for others and our passion for freedom. ..."
"... America has entered one of its periods of historical madness, but this the worst I can remember: worse than McCarthyism, worse that the Bay of Pigs and in the long term potentially more disastrous than the Vietnam War. ~John le Carre ..."
"... It is terrifying to watch Clinton rave about adopting a more "muscular, aggressive" approach to foreign affairs - with little or no push back from the national media, either party or even many citizens. Hell, they are applause lines at her rallies. ..."
"... If 15 years of endless wars, trillions of dollars of wasted money, hundreds of thousands of casualties on all sides and metastasizing terrorist threat with no end in sight doesn't give one a little pause before advocating more of the same, then we might have a problem. ..."
"... Hillary said twice during the debates that "America is great because America is good." Translation: We can do whatever we damn well please because we can. Lord, help us all. I'm so sick of hearing this and our endless criminal wars. ..."
Bjornasson
October 26, 2016 at 3:20 pm
I find the whole hysteria over Russian hacking very one-sided. If the US takes it upon itself,
out of sincere concern, to help out "moderates" in overthrowing a repressive, evil government
in Syria, Libya and Iraq, maybe the same thing happening to the US itself is not that weird?
Here is a tyrannical government with little regard for its demotivated and demoralized citizens
who can not on their own displace it. This government threatens nuclear war and kills an unjustified
number of its own citizens. Its public infrastructure is in ruins and oligarchy is everywhere.
In the past the US has set the example for dealing with such troubled states; its time the
doctor took his own medicine.
reslez
October 26, 2016 at 5:07 pm
The "evidence" for Russian hacking is so suspect that anyone who repeats the story instantly
stamps themselves as either a con or a mark. It's depressing to see media corruption so blatantly
displayed. Now I know what 2003 must have felt like (I was too young to have much of an opinion
back then).
Gareth
October 26, 2016 at 6:21 pm
The "17 intelligence agencies" claim is complete Clinton bullshit. I'm kind of amazed that
journalists are now stating this as fact. I could say I'm shocked but nothing the presstitutes
do surprises me anymore. They are busy preening for their future White House access. It kind
of makes me want to get drunk and vote for the orange haired guy.
Kokuanani
October 26, 2016 at 6:57 pm
Just finished trying to "re-educate" my husband after he listened to [and apparently believed]
a report in the CBS Evening News on the "Russian hacking of Clinton's e-mails." They reported
it as complete "fact," without even a perfunctory "alleged."
Too difficult to do this correction one person at a time, while the networks have such massive
reach.
Kurt Sperry
October 26, 2016 at 9:42 pm
It *is* highly asymmetric warfare. And as is normal when working the insurgent side, the
trick isn't to try to win by a large number of winning individual engagements, but rather of
delegitimatizing the side with the resource advantage in a broader, cultural way. Delegitimize
the mainstream media actively. If you win the culture war, you win the political war too just
as a bonus. Tell the truth, unapologetically. That's as bad-ass as it gets.
WJ
October 26, 2016 at 10:30 pm
This is sound advice. Problem is, how to delegitimate media generally? Actual insurgents
avoid direct confrontations with superior occupying power and opt for a variety of other strategies
of attack, including: IED's, flash attacks, suicide bombings, disruption of civilian life,
etc. What are some equivalent, concrete (and legal) strategies for disrupting the order of
imposed media? The use of social media seems to be one option, and maybe the most successful.
Yet this tends to reach only certain segments of population who are unlikely to watch CNN or
read the Post in any case. How can one harm the media powers where it hurts them most, by reaching
and disrupting their actual consumers, who tend to be older, establishment-minded, white, etc…?
Kurt Sperry
October 26, 2016 at 11:36 pm
How to delegitimize the media? They are doing that themselves. In spades. Listen to the
people around you, they are getting wise to it. Just point it out to anyone who'll listen.
It isn't the bombs and attacks that win an insurgency, none of that stuff works if the cause
isn't widely understood and shared. The victory is won–to recycle a cliché–in the hearts and
minds of the ordinary people. Naked Capitalism is a big ammo depot and we are the grunts and
the munitions are ideas. And as I alluded to above, the power of truth. Truth will kick ass
and take names if you let it.
Ulysses
October 27, 2016 at 10:30 am
"Truth will kick ass and take names if you let it."
Thanks for the spirit-raising exhortation Kurt!! Many Americans are walking around with
heads like over-inflated cognitive dissonance balloons. If you listen closely, you can hear
these balloons popping off all the time, resulting in yet another person able to confront reality.
Massinissa
October 26, 2016 at 7:26 pm
What other intelligence agencies are there than the CIA and NSA? Does anyone know the other
15, and why are these intelligence agencies never spoken of in the media except when its useful
for Clinton?
xformbykr
October 26, 2016 at 7:33 pm
see
http://www.businessinsider.com/17-agencies-of-the-us-intelligence-community-2013-5#
JTMcPhee
October 27, 2016 at 3:14 pm
Why is it called a "community?" Cabal? Coven? Hey, isn't the proper collective noun for
lawyers (Clintons, Yoo, Meese, Obama, etc.) a "conspiracy?"
Bjornasson
October 26, 2016 at 6:09 pm
The idea is essentially that even if the evidence did exist, it should be welcomed with
the same enthusiasm that US interventions have in Syria and Libya.
dennison p nyberg
October 27, 2016 at 11:24 am
truth
Tom
October 26, 2016 at 5:23 pm
Ahhhh, but that exactly where the "exceptional" clause kicks in. You see, America is justified
in intervening in other countries' business because we see further, with a clearer gaze and
a purer heart, than any other country in the world. Mired as they are in ignorance or inertia,
no other country is qualified to judge us, and any mistakes that we make only occur because
of the depths of our love for others and our passion for freedom.
abynormal
October 26, 2016 at 6:26 pm
America has entered one of its periods of historical madness, but this the worst I can remember:
worse than McCarthyism, worse that the Bay of Pigs and in the long term potentially more disastrous
than the Vietnam War. ~John le Carre
KILLING MACHINES AND THE MADNESS OF MILITARISM
http://www.artsandopinion.com/2014_v13_n5/giroux-6.htm
by Henry Giroux
Tom
October 26, 2016 at 6:48 pm
historical madness/hysterical madness … take your pick.
It is terrifying to watch Clinton rave about adopting a more "muscular, aggressive" approach
to foreign affairs - with little or no push back from the national media, either party or even
many citizens. Hell, they are applause lines at her rallies.
If 15 years of endless wars, trillions of dollars of wasted money, hundreds of thousands
of casualties on all sides and metastasizing terrorist threat with no end in sight doesn't
give one a little pause before advocating more of the same, then we might have a problem.
abynormal
October 26, 2016 at 7:12 pm
she's a scorned woman beginning with her father. she's passive-aggressive with women…projects
her never ending insecurities. SO she has something to prove…vengeance is mine.
First, she'll drone Mercy Street(s)…
Elizabeth
October 26, 2016 at 7:58 pm
Hillary said twice during the debates that "America is great because America is good." Translation:
We can do whatever we damn well please because we can. Lord, help us all. I'm so sick of hearing
this and our endless criminal wars.
Not mentioned in the News of the Wired snips: the Dyn DDOS was the latest using a megascale IOT
botnet. Coming soon to a Smart Toaster|Thermostat|Fridge|WasherDryer|EggTimer|PencilSharpener|Dishwasher|GarbageCompacter|BabyMonitor
near you!
hunkerdown
October 21, 2016 at 7:36 pm
I suspect various enforcement agencies are using those cameras for something else, like mass
video surveillance, and having just lost a lot of TLS vulnerabilities, are motivated to keep their
sources' name out of the news (as befits TS/SI NOFORN projects), though steering the industry's
and the commercial market economy's Confidence Fairy out of an imminent uncontrolled landing would
suffice to explain the quiet.
OpenThePodBayDoorsHAL
October 21, 2016 at 7:38 pm
For people who understand what that means it is mind-blowing, the processors in your parking
garage gate or your nursery's NannyCam being used in a giant global concerto of digital disruption.
Smells like the NSA in a desperate attempt to disrupt the flows from Wiki, they already gave the
Clinton camp their best spyware (FoxAcid) and this would be par for the course given the level
of lawbreaking and dirty tricks.
cm
October 22, 2016 at 1:13 am
Will be illuminating to see if Congress demands IOT accountabilty. IMO the IOT manufacturers
should be held to the same level of accountability as car manufacturers,
Notable quotes:
"... Well-crafted spear-phishing emails can be incredibly hard to spot, but if you ever end up on a website asking you for a password, you should be skeptical. Check the URL and make sure you're at a legitimate login page before typing in your password, or navigate to the login page directly. ..."
Here are some easy ways the Clinton team could have avoided getting hacked and might
prevent it in the future.
There is probably no one more acutely aware of the importance of good cybersecurity right now
than Hillary Clinton's campaign chairman John Podesta, whose emails have been laid bare by
WikiLeaks, are being mined for news by journalists (including at The Intercept), and are
available for anyone with internet access to read.
So as a public service to Podesta and everyone else on Clinton's staff, here are some email
security tips that could have saved you from getting hacked, and might help you in the future.
Use a strong password
There's a method for coming up with passwords that are mathematically unfeasible for anyone
to ever guess by brute force, but that are still possible for you to memorize. I've written
about it before, in detail, including an explanation of the math behind it.
But in short: You start with a long list of words and then randomly select one (by rolling
dice), then another, and so on, until you end up with something like: "slinging gusty bunny
chill gift." Using this method, called Diceware, there is a one in 28 quintillion (that is, 28
with 18 zeros at the end) chance of guessing this exact password.
For online services that prevent attackers from making very many guesses - including Gmail - a
five-word Diceware password is much stronger than you'll ever need. To make it super easy, use
this wordlist from the Electronic Frontier Foundation.
.... ... ...
Use a unique password for each application
The same day that WikiLeaks published Podesta's email, his Twitter account got hacked as
well. How do you think that happened? I have a guess: He reused a password that was exposed in
his email, and someone tried it on his Twitter account.
... ... ...
Turn on two-factor authentication
Last year, when I asked National Security Agency whistleblower Edward Snowden what ordinary
people could do to improve their computer security, one of the first pieces of advice he gave
was to use two-factor authentication. If Podesta had enabled it on his Gmail account, you
probably wouldn't be reading his email today.
Google calls it "2-Step Verification" and has an excellent website explaining why you need it,
how it works, and how it protects you. In short: When you log in to your account, after you
type in your password you'll need one more piece of information before Google will allow you
to proceed. Depending on how you set it up you might receive this uniquely generated
information in a text message, a voice call, or a mobile app, or you could plug in a special
security key into your USB port.
Once you start using it, hackers who manage to trick you into giving up your password still
won't be able to log in to your account - at least not without successfully executing a
separate attack against your phone or physically stealing your security key.
Watch out for phishers
... ... ...
Well-crafted spear-phishing emails can be incredibly hard to spot, but if you ever end
up on a website asking you for a password, you should be skeptical. Check the URL and make
sure you're at a legitimate login page before typing in your password, or navigate to the
login page directly.
Encrypt your email
.... ... ...
To get started, check out the Electronic Frontier Foundation's Surveillance Self-Defense guide
for using email encryption for Windows, Mac OS X, and Linux. If enough people in your
organization use encrypted email, consider using our newly released tool GPG Sync to make it
somewhat simpler.
Don't listen to the wrong people
... ... ...
poeg -> junction:
Oct 8, 2016 2:30 PM
You cats haven't had end to end encryption for more than 5 years and while not at all
difficult to accomplish, the resistance to using such code has amazed all in the ITSEC
community not feeding at the .gov trough. All your ISP's have been carrying NSA gear within
their infrastructure for how long now? Juniper's back door in their gear wasn't to push
firmware updates. The whole system has been left open for a number of reasons, none of which
would be capitalism, free markets or satisfied consumers.
Kirk2NCC1701 -> junction
•Oct 8, 2016 2:59 PM
Well, if you use Yahoo, Outlook or Google mail, then you're the Village Idiot, if you use
those free services for anything other than harmless, boring stuff. You know, Yoga and Cooking
recipes -- like Hillary.
IF you're serious about email privacy, use an email service that is OUTSIDE the US.
As you know, I use Hushmail.me for my Kirk2NCC1701 handle and ZH friends. Hushmail is in
Canada and after speaking with them in person, I am confident that they take their customer's
Privacy seriously, especially for their paying customers. Now, I may have used a Yahoo
alt-persona account, but only for "Trumping". I also may have used Google and Outlook for
"vanilla" stuff, and I may have used other offshore emails for "secure" purposes where lawful
business and personal privacy matters were involved (but No illegal activities, as I'm not an
"illegal" type. Devious, curious, inquiring, opinionated? Hell yes. Illegal? No.)
"Trunping" (copyright 2016, Kirk2NCC1701) -- behaving Trump-like: bombastic, pleasure-seeking,
pussy-seeking, pussy-pleasuring
Dugald -> Kirk2NCC1701
•Oct 8, 2016 5:35 PM
Been using Pidgeon and Forked stick for years for private stuff.....
as for my Gmail account, I don't give a shit.....
Parrotile -> Kirk2NCC1701
•Oct 8, 2016 8:46 PM
I very rarely need to send anything particularly confidential. My employers expect me to
use the systems they provide for all "Medical in Confidence" stuff, and so since that
requirement is part of my Contract, they are entirely liable for any failures, not me.
EMail - Outlook. It works and again nothing of "interest" is ever sent. If I DO need to
send information that's "Sensitive", I have one of these: -
http://thumbs.picclick.com/00/s/OTAwWDExMTk=/z/GWMAAOSw3YNXbDD6/$/Canon-typestar-10-ii-portable-electronic-typewriter-_57.jpg
- Which works very well, and the cartridges are easily available. Person-to-Person, or
Recorded Delivery mail. Works just fine and of course NO "electronic paper trail" . . . .
Notable quotes:
"... Waihopai, INFOSEC, Information Security, Information Warfare, IW, IS, Priavacy, Information Terrorism, Terrorism Defensive Information, Defense Information Warfare, Offensive Information, Offensive Information Warfare, National Information Infrastructure, InfoSec, Reno, Compsec, Computer Terrorism, Firewalls, Secure Internet Connections, ISS, Passwords, DefCon V, Hackers, Encryption, Espionage, USDOJ, NSA, CIA, S/Key, SSL, FBI, Secert Service, USSS, Defcon, Military, White House, Undercover, NCCS, Mayfly, PGP, PEM, RSA, Perl-RSA, MSNBC, bet, AOL, AOL TOS, CIS, CBOT, AIMSX, STARLAN, 3B2, BITNET, COSMOS, DATTA, E911, FCIC, HTCIA, IACIS, UT/RUS, JANET, JICC, ReMOB, LEETAC, UTU, VNET, BRLO, BZ, CANSLO, CBNRC, CIDA, JAVA, Active X, Compsec 97, LLC, DERA, Mavricks, Meta-hackers, ^?, Steve Case, Tools, Telex, Military Intelligence, Scully, Flame, Infowar, Bubba, Freeh, Archives, Sundevil, jack, Investigation, ISACA, NCSA, spook words, Verisign, Secure, ASIO, Lebed, ICE, NRO, Lexis-Nexis, NSCT, SCIF, FLiR, Lacrosse, Flashbangs, HRT, DIA, USCOI, CID, BOP, FINCEN, FLETC, NIJ, ACC, AFSPC, BMDO, NAVWAN, NRL, RL, NAVWCWPNS, NSWC, USAFA, AHPCRC, ARPA, LABLINK, USACIL, USCG, NRC, ~, CDC, DOE, FMS, HPCC, NTIS, SEL, USCODE, CISE, SIRC, CIM, ISN, DJC, SGC, UNCPCJ, CFC, DREO, CDA, DRA, SHAPE, SACLANT, BECCA, DCJFTF, HALO, HAHO, FKS, 868, GCHQ, DITSA, SORT, AMEMB, NSG, HIC, EDI, SAS, SBS, UDT, GOE, DOE, GEO, Masuda, Forte, AT, GIGN, Exon Shell, CQB, CONUS, CTU, RCMP, GRU, SASR, GSG-9, 22nd SAS, GEOS, EADA, BBE, STEP, Echelon, Dictionary, MD2, MD4, MDA, MYK, 747,777, 767, MI5, 737, MI6, 757, Kh-11, Shayet-13, SADMS, Spetznaz, Recce, 707, CIO, NOCS, Halcon, Duress, RAID, Psyops, grom, D-11, SERT, VIP, ARC, S.E.T. Team, MP5k, DREC, DEVGRP, DF, DSD, FDM, GRU, LRTS, SIGDEV, NACSI, PSAC, PTT, RFI, SIGDASYS, TDM. SUKLO, SUSLO, TELINT, TEXTA. ELF, LF, MF, VHF, UHF, SHF, SASP, WANK, Colonel, domestic disruption, smuggle, 15kg, nitrate, Pretoria, M-14, enigma, Bletchley Park, Clandestine, nkvd, argus, afsatcom, CQB, NVD, Counter Terrorism Security, Rapid Reaction, Corporate Security, Police, sniper, PPS, ASIS, ASLET, TSCM, Security Consulting, High Security, Security Evaluation, Electronic Surveillance, MI-17, Counterterrorism, spies, eavesdropping, debugging, interception, COCOT, rhost, rhosts, SETA, Amherst, Broadside, Capricorn, Gamma, Gorizont, Guppy, Ionosphere, Mole, Keyhole, Kilderkin, Artichoke, Badger, Cornflower, Daisy, Egret, Iris, Hollyhock, Jasmine, Juile, Vinnell, B.D.M.,Sphinx, Stephanie, Reflection, Spoke, Talent, Trump, FX, FXR, IMF, POCSAG, Covert Video, Intiso, r00t, lock picking, Beyond Hope, csystems, passwd, 2600 Magazine, Competitor, EO, Chan, Alouette,executive, Event Security, Mace, Cap-Stun, stakeout, ninja, ASIS, ISA, EOD, Oscor, Merlin, NTT, SL-1, Rolm, TIE, Tie-fighter, PBX, SLI, NTT, MSCJ, MIT, 69, RIT, Time, MSEE, Cable & Wireless, CSE, Embassy, ETA, Porno, Fax, finks, Fax encryption, white noise, pink noise, CRA, M.P.R.I., top secret, Mossberg, 50BMG, Macintosh Security, Macintosh Internet Security, Macintosh Firewalls, Unix Security, VIP Protection, SIG, sweep, Medco, TRD, TDR, sweeping, TELINT, Audiotel, Harvard, 1080H, SWS, Asset, Satellite imagery, force, Cypherpunks, Coderpunks, TRW, remailers, replay, redheads, RX-7, explicit, FLAME, Pornstars, AVN, Playboy, Anonymous, Sex, chaining, codes, Nuclear, 20, subversives, SLIP, toad, fish, data havens, unix, c, a, b, d, the, Elvis, quiche, DES, 1*, NATIA, NATOA, sneakers, counterintelligence, industrial espionage, PI, TSCI, industrial intelligence, H.N.P., Juiliett Class Submarine, Locks, loch, Ingram Mac-10, sigvoice, ssa, E.O.D., SEMTEX, penrep, racal, OTP, OSS, Blowpipe, CCS, GSA, Kilo Class, squib, primacord, RSP, Becker, Nerd, fangs, Austin, Comirex, GPMG, Speakeasy, humint, GEODSS, SORO, M5, ANC, zone, SBI, DSS, S.A.I.C., Minox, Keyhole, SAR, Rand Corporation, Wackenhutt, EO, Wackendude, mol, Hillal, GGL, CTU, botux, Virii, CCC, Blacklisted 411, Internet Underground, XS4ALL, Retinal Fetish, Fetish, Yobie, CTP, CATO, Phon-e, Chicago Posse, l0ck, spook keywords, PLA, TDYC, W3, CUD, CdC, Weekly World News, Zen, World Domination, Dead, GRU, M72750, Salsa, 7, Blowfish, Gorelick, Glock, Ft. Meade, press-release, Indigo, wire transfer, e-cash, Bubba the Love Sponge, Digicash, zip, SWAT, Ortega, PPP, crypto-anarchy, AT&T, SGI, SUN, MCI, Blacknet, Middleman, KLM, Blackbird, plutonium, Texas, jihad, SDI, Uzi, Fort Meade, supercomputer, bullion, 3, Blackmednet, Propaganda, ABC, Satellite phones, Planet-1, cryptanalysis, nuclear, FBI, Panama, fissionable, Sears Tower, NORAD, Delta Force, SEAL, virtual, Dolch, secure shell, screws, Black-Ops, Area51, SABC, basement, data-haven, black-bag, TEMPSET, Goodwin, rebels, ID, MD5, IDEA, garbage, market, beef, Stego, unclassified, utopia, orthodox, Alica, SHA, Global, gorilla, Bob, Pseudonyms, MITM, Gray Data, VLSI, mega, Leitrim, Yakima, Sugar Grove, Cowboy, Gist, 8182, Gatt, Platform, 1911, Geraldton, UKUSA, veggie, 3848, Morwenstow, Consul, Oratory, Pine Gap, Menwith, Mantis, DSD, BVD, 1984, Flintlock, cybercash, government, hate, speedbump, illuminati, president, freedom, cocaine, $, Roswell, ESN, COS, E.T., credit card, b9, fraud, assasinate, virus, anarchy, rogue, mailbomb, 888, Chelsea, 1997, Whitewater, MOD, York, plutonium, William Gates, clone, BATF, SGDN, Nike, Atlas, Delta, TWA, Kiwi, PGP 2.6.2., PGP 5.0i, PGP 5.1, siliconpimp, Lynch, 414, Face, Pixar, IRIDF, eternity server, Skytel, Yukon, Templeton, LUK, Cohiba, Soros, Standford, niche, 51, H&K, USP, ^, sardine, bank, EUB, USP, PCS, NRO, Red Cell, Glock 26, snuffle, Patel, package, ISI, INR, INS, IRS, GRU, RUOP, GSS, NSP, SRI, Ronco, Armani, BOSS, Chobetsu, FBIS, BND, SISDE, FSB, BfV, IB, froglegs, JITEM, SADF, advise, TUSA, HoHoCon, SISMI, FIS, MSW, Spyderco, UOP, SSCI, NIMA, MOIS, SVR, SIN, advisors, SAP, OAU, PFS, Aladdin, chameleon man, Hutsul, CESID, Bess, rail gun, Peering, 17, 312, NB, CBM, CTP, Sardine, SBIRS, SGDN, ADIU, DEADBEEF, IDP, IDF, Halibut, SONANGOL, Flu, &, Loin, PGP 5.53, EG&G, AIEWS, AMW, WORM, MP5K-SD, 1071, WINGS, cdi, DynCorp, UXO, Ti, THAAD, package, chosen, PRIME, SURVIAC ..."
by Dave Lindorff
Word that Yahoo! last year, at the urging of the National Security Agency, secretly developed
a program that monitored the mail of all 280 million of its customers and turned over to the NSA
all mail from those who used any of the agency's thousands of keywords, shows that the US has become
a total police state in terms of trying to monitor every person in the country (and outside too).
With the courts, especially at the appellate and Supreme Court level, rolling over and supporting
this massive evisceration of basic freedoms, including the First Amendment guarantee of freedom of
speech and the Fourth Amendment protection against illegal search and seizure and invasion of privacy,
perhaps the best way for us to fight back is to overload the spy system. How to do this? Just copy
and paste random fragments of the following list (a bit dated, but useable), provided courtesy of
the publication Business Insider, and include them in every communication - email, social media,
etc. - that you send out.
The secret Yahoo! assault (reported on here by Alfredo Lopez in
yesterday's article ),
works by searching users' emails for keywords on an NSA list of suspected words that might be used
by alleged terrorists or anti-government activists, and then those suspect communications are forwarded
to the NSA, where humans eventually have to separate the wheat from the chaff. Too much chaff (and
they surely have too much chaff anyhow!) and they will be buried with work and unable to read anything.
In fact, critics of the government's metastasizing universal surveillance program, including former
FBI agents and other experts, have long criticized the effort to turn the US into a replica of East
Germany with its Stazi secret police, cannot work and is actually counter-productive, because with
spy agencies' limited manpower looking at all the false leads provided by keyword monitoring, they
are bound to miss the real dangerous messages. In fact, this was also the argument used against the
FBI's program of monitoring mosques and suspecting every Muslim American who expressed criticism
of the US. Most are just people saying what a lot of us say: that the US wars in the Middle East
are wrong or even criminal, but they are just citizens or immigrants exercising their free speech
when they do this, not terrorists, and spying on them is and has been a huge waste or time and resources.
... ... ...
a sample of the NSA's keyword list:
Waihopai, INFOSEC, Information Security, Information Warfare, IW, IS, Priavacy, Information
Terrorism, Terrorism Defensive Information, Defense Information Warfare, Offensive Information, Offensive
Information Warfare, National Information Infrastructure, InfoSec, Reno, Compsec, Computer Terrorism,
Firewalls, Secure Internet Connections, ISS, Passwords, DefCon V, Hackers, Encryption, Espionage,
USDOJ, NSA, CIA, S/Key, SSL, FBI, Secert Service, USSS, Defcon, Military, White House, Undercover,
NCCS, Mayfly, PGP, PEM, RSA, Perl-RSA, MSNBC, bet, AOL, AOL TOS, CIS, CBOT, AIMSX, STARLAN, 3B2,
BITNET, COSMOS, DATTA, E911, FCIC, HTCIA, IACIS, UT/RUS, JANET, JICC, ReMOB, LEETAC, UTU, VNET, BRLO,
BZ, CANSLO, CBNRC, CIDA, JAVA, Active X, Compsec 97, LLC, DERA, Mavricks, Meta-hackers, ^?, Steve
Case, Tools, Telex, Military Intelligence, Scully, Flame, Infowar, Bubba, Freeh, Archives, Sundevil,
jack, Investigation, ISACA, NCSA, spook words, Verisign, Secure, ASIO, Lebed, ICE, NRO, Lexis-Nexis,
NSCT, SCIF, FLiR, Lacrosse, Flashbangs, HRT, DIA, USCOI, CID, BOP, FINCEN, FLETC, NIJ, ACC, AFSPC,
BMDO, NAVWAN, NRL, RL, NAVWCWPNS, NSWC, USAFA, AHPCRC, ARPA, LABLINK, USACIL, USCG, NRC, ~, CDC,
DOE, FMS, HPCC, NTIS, SEL, USCODE, CISE, SIRC, CIM, ISN, DJC, SGC, UNCPCJ, CFC, DREO, CDA, DRA, SHAPE,
SACLANT, BECCA, DCJFTF, HALO, HAHO, FKS, 868, GCHQ, DITSA, SORT, AMEMB, NSG, HIC, EDI, SAS, SBS,
UDT, GOE, DOE, GEO, Masuda, Forte, AT, GIGN, Exon Shell, CQB, CONUS, CTU, RCMP, GRU, SASR, GSG-9,
22nd SAS, GEOS, EADA, BBE, STEP, Echelon, Dictionary, MD2, MD4, MDA, MYK, 747,777, 767, MI5, 737,
MI6, 757, Kh-11, Shayet-13, SADMS, Spetznaz, Recce, 707, CIO, NOCS, Halcon, Duress, RAID, Psyops,
grom, D-11, SERT, VIP, ARC, S.E.T. Team, MP5k, DREC, DEVGRP, DF, DSD, FDM, GRU, LRTS, SIGDEV, NACSI,
PSAC, PTT, RFI, SIGDASYS, TDM. SUKLO, SUSLO, TELINT, TEXTA. ELF, LF, MF, VHF, UHF, SHF, SASP, WANK,
Colonel, domestic disruption, smuggle, 15kg, nitrate, Pretoria, M-14, enigma, Bletchley Park, Clandestine,
nkvd, argus, afsatcom, CQB, NVD, Counter Terrorism Security, Rapid Reaction, Corporate Security,
Police, sniper, PPS, ASIS, ASLET, TSCM, Security Consulting, High Security, Security Evaluation,
Electronic Surveillance, MI-17, Counterterrorism, spies, eavesdropping, debugging, interception,
COCOT, rhost, rhosts, SETA, Amherst, Broadside, Capricorn, Gamma, Gorizont, Guppy, Ionosphere, Mole,
Keyhole, Kilderkin, Artichoke, Badger, Cornflower, Daisy, Egret, Iris, Hollyhock, Jasmine, Juile,
Vinnell, B.D.M.,Sphinx, Stephanie, Reflection, Spoke, Talent, Trump, FX, FXR, IMF, POCSAG, Covert
Video, Intiso, r00t, lock picking, Beyond Hope, csystems, passwd, 2600 Magazine, Competitor, EO,
Chan, Alouette,executive, Event Security, Mace, Cap-Stun, stakeout, ninja, ASIS, ISA, EOD, Oscor,
Merlin, NTT, SL-1, Rolm, TIE, Tie-fighter, PBX, SLI, NTT, MSCJ, MIT, 69, RIT, Time, MSEE, Cable &
Wireless, CSE, Embassy, ETA, Porno, Fax, finks, Fax encryption, white noise, pink noise, CRA, M.P.R.I.,
top secret, Mossberg, 50BMG, Macintosh Security, Macintosh Internet Security, Macintosh Firewalls,
Unix Security, VIP Protection, SIG, sweep, Medco, TRD, TDR, sweeping, TELINT, Audiotel, Harvard,
1080H, SWS, Asset, Satellite imagery, force, Cypherpunks, Coderpunks, TRW, remailers, replay, redheads,
RX-7, explicit, FLAME, Pornstars, AVN, Playboy, Anonymous, Sex, chaining, codes, Nuclear, 20, subversives,
SLIP, toad, fish, data havens, unix, c, a, b, d, the, Elvis, quiche, DES, 1*, NATIA, NATOA, sneakers,
counterintelligence, industrial espionage, PI, TSCI, industrial intelligence, H.N.P., Juiliett Class
Submarine, Locks, loch, Ingram Mac-10, sigvoice, ssa, E.O.D., SEMTEX, penrep, racal, OTP, OSS, Blowpipe,
CCS, GSA, Kilo Class, squib, primacord, RSP, Becker, Nerd, fangs, Austin, Comirex, GPMG, Speakeasy,
humint, GEODSS, SORO, M5, ANC, zone, SBI, DSS, S.A.I.C., Minox, Keyhole, SAR, Rand Corporation, Wackenhutt,
EO, Wackendude, mol, Hillal, GGL, CTU, botux, Virii, CCC, Blacklisted 411, Internet Underground,
XS4ALL, Retinal Fetish, Fetish, Yobie, CTP, CATO, Phon-e, Chicago Posse, l0ck, spook keywords, PLA,
TDYC, W3, CUD, CdC, Weekly World News, Zen, World Domination, Dead, GRU, M72750, Salsa, 7, Blowfish,
Gorelick, Glock, Ft. Meade, press-release, Indigo, wire transfer, e-cash, Bubba the Love Sponge,
Digicash, zip, SWAT, Ortega, PPP, crypto-anarchy, AT&T, SGI, SUN, MCI, Blacknet, Middleman, KLM,
Blackbird, plutonium, Texas, jihad, SDI, Uzi, Fort Meade, supercomputer, bullion, 3, Blackmednet,
Propaganda, ABC, Satellite phones, Planet-1, cryptanalysis, nuclear, FBI, Panama, fissionable, Sears
Tower, NORAD, Delta Force, SEAL, virtual, Dolch, secure shell, screws, Black-Ops, Area51, SABC, basement,
data-haven, black-bag, TEMPSET, Goodwin, rebels, ID, MD5, IDEA, garbage, market, beef, Stego, unclassified,
utopia, orthodox, Alica, SHA, Global, gorilla, Bob, Pseudonyms, MITM, Gray Data, VLSI, mega, Leitrim,
Yakima, Sugar Grove, Cowboy, Gist, 8182, Gatt, Platform, 1911, Geraldton, UKUSA, veggie, 3848, Morwenstow,
Consul, Oratory, Pine Gap, Menwith, Mantis, DSD, BVD, 1984, Flintlock, cybercash, government, hate,
speedbump, illuminati, president, freedom, cocaine, $, Roswell, ESN, COS, E.T., credit card, b9,
fraud, assasinate, virus, anarchy, rogue, mailbomb, 888, Chelsea, 1997, Whitewater, MOD, York, plutonium,
William Gates, clone, BATF, SGDN, Nike, Atlas, Delta, TWA, Kiwi, PGP 2.6.2., PGP 5.0i, PGP 5.1, siliconpimp,
Lynch, 414, Face, Pixar, IRIDF, eternity server, Skytel, Yukon, Templeton, LUK, Cohiba, Soros, Standford,
niche, 51, H&K, USP, ^, sardine, bank, EUB, USP, PCS, NRO, Red Cell, Glock 26, snuffle, Patel, package,
ISI, INR, INS, IRS, GRU, RUOP, GSS, NSP, SRI, Ronco, Armani, BOSS, Chobetsu, FBIS, BND, SISDE, FSB,
BfV, IB, froglegs, JITEM, SADF, advise, TUSA, HoHoCon, SISMI, FIS, MSW, Spyderco, UOP, SSCI, NIMA,
MOIS, SVR, SIN, advisors, SAP, OAU, PFS, Aladdin, chameleon man, Hutsul, CESID, Bess, rail gun, Peering,
17, 312, NB, CBM, CTP, Sardine, SBIRS, SGDN, ADIU, DEADBEEF, IDP, IDF, Halibut, SONANGOL, Flu, &,
Loin, PGP 5.53, EG&G, AIEWS, AMW, WORM, MP5K-SD, 1071, WINGS, cdi, DynCorp, UXO, Ti, THAAD, package,
chosen, PRIME, SURVIAC
Software Could've Given NSA Much More Access Than Just Emails
Former employees of Yahoo have corroborated this week's stories about the company scanning all
emails coming into their servers on behalf of the NSA, saying that the "email scanner" software was
not Yahoo-built,
but
actually made and installed by the US government .
The employees, including at least one on Yahoo's own internal security team, reported finding
the software on the
email
server and believing they were begin hacked, before executives informed them the government had done
it. They described the software as a broader "rootkit" that could give the NSA access to much more
than just emails.
To make matters worse, the employees
say the government's software was "buggy" and poorly-designed , meaning it could've given other
hackers who discovered it the same access to the Yahoo server, adding to the danger it posed to customers'
privacy.
Yahoo itself has been mostly mum on the matter, issuing a statement claiming the initial reports
were "misleading" but not elaborating at all. The NSA denied the claim outright, though they have
been repeatedly caught lying about similar programs in the past.
Izabella Kaminska joined FT Alphaville in October
2008. Before that she worked as a producer at CNBC, a natural gas reporter at Platts and an associate
editor of BP's internal magazine.
If your email provider suffered a security breach would you:
a) prefer to be informed about it as soon as possible so as to take evasive action?
or
b) prefer not to be informed until years later, by which time any evasive actions may have
become pointless?
On the basis you chose the first option and a security breach happened, would you:
a) appreciate the warning and the password reset nudge, dismiss the incident to a Smeg happens
scenario and continue using the service provider because at least they're vigilant about security?
or
b) Recoil in disgust at the very idea your email provider's security systems were lax enough
to allow this to happen and immediately defect to a rival provider?
On the basis you would have chosen the first option and then the first option again (and then
a security breach happened), how would you then react if your email provider determined that a) it
was better to keep you in the dark about it and b) this was because they anticipated you would defect?
To wit, here's a nice insight from Nicole Perlroth and Vindu Goel
at the New York Times for the legacy loyal yahoo email users still out there (h/t @melaniehannah):
Mr. Stamos, who departed Yahoo for Facebook last year, declined to comment. But during his
tenure, Ms. Mayer also rejected the most basic security measure of all: an automatic reset of
all user passwords, a step security experts consider standard after a breach. Employees say the
move was rejected by Ms. Mayer's team for fear that even something as simple as a password change
would drive Yahoo's shrinking email users to other services.
Two points on the back of that.
As a yahoo email user, I can testify to the fact that being continuously told by friends and family
that: "Hey there, I think your email may have been hacked" is incentive enough to defect to an alternative
provider.
Second, when I tried to download our complete email history so as to shutter the account formally,
we found that this was in fact impossible unless we had the time and temperament to forward up to
20 years worth of email individually to a new account.
To date I am yet to get a reply from the Yahoo service team with respect to how I might get my
hands on my own data in a more practical manner.
Speaking of frictions, here's another relevant snippet from the article:
The "Paranoids," the internal name for Yahoo's security team, often clashed with other parts
of the business over security costs. And their requests were often overridden because
of concerns that the inconvenience of added protection would make people stop using the company's
products.
All of which suggests the crux of Mayer's Yahoo strategy was focused on maximising the security/access
paradox to her own benefit. Namely, maximising access to the detriment of user security if it helped
to bolster Yahoo's user numbers, but minimising user access to their own data if it helped to maximise
the security of yahoo's own stock valuation.
Nice. This entry was posted by
Izabella Kaminska
on Wednesday September 28th, 2016 17:02 . Tagged with
cyber security ,
yahoo .
The choice between security and ease of access is a difficult one, and shouldn't be trivialized.
Password policies are a good example - overly loose, and hackers will be able to guess users'
passwords; overly strict (e.g., requiring a password change every month), and users will resort
to passwords on sticky notes stuck to their monitors. If you make things too difficult for users,
they will find ways to ease the burden, and some of those ways will actually make security significantly
worse.
That's not to say that Yahoo made the right decision, but it is to say that it isn't as easy as
assuming that more security is always better.
I have managed to use the web for 20 years without ever visiting yahoo.com - by intention.
I got the impression that they try to imprison their users rather than empower them.
I assume their e-mail service was 'free'. If so their users got exactly what they paid for.
In an ideal world each e-mail would cost the sender a cent. This would solve the problem of spam,
and generate funds to develop and promote better web security.
Oooh, you had a Yahoo email account? You've just lost a big chunk of credibility.
I mean I have a Yahoo account (as well as a Netscape account and a Hotmail, sorry, whatever they
call it) plus one or two others. Every time a new email provider has popped up I check their tech
credentials and migrate to the provider that seems to hire the best techies. They get the sensitive
mail. I keep the old accounts and use them for spam-associated registrations and whatnot.
Presently Google and Proton are my principal providers. Anyone who carried on with Yahoo for sensitive
mail has nobody to blame other than him/herself.
Settle down. Changing email accounts is a hassle, particularly for one's contacts.
OBA 5pts Featured 9 hours ago
@izabellakaminska - setup up your yahoo account
and your new email account on an email client like mac mail or microsoft outlook- make sure they
are both setup as an IMAP account. Wait for all the yahoo email to download and then simply select
all messages and drag them across to your new account.
@ OBA
Better yet, just leave the digital past...proud achievements and baggage alike...and step
into the future with a clean slate.
@ OBA
Thank you, this is a great suggestion. I've been trying to figure out how to backup my
Yahoo! account - I only use it for signing up for things where I might get spam, but still wanted
an easy way to back it up. I already used an e-mail client to get e-mails for one of my other accounts,
I don't know why it never occurred to me to do the same for Yahoo!.
Notable quotes:
"... Another goal of course is to track even further every single purchase - what, and where, and when. And then sell the consumption data to the insurers perhaps… a packet of cigs per day? Or too many bottles of booze? ..."
temporal
September 25, 2016 at 9:08 am
Scan and go.
Swapping standing in line at the check-out for the line at the exit. And when there is an issue
then the greeter calls in the check-out police thereby pissing off the customer. Brilliant.
While Apple fanboys are willing to work for their iPhone's company for free by doing their
own check-out I doubt that is likely for people going to Sam's Club. As well many customers, even
if they have a smartphone, will not enjoy using up their data plan as they try to check and process
the details online.
All these smartphone apps have one major goal, besides collecting credit fees. Reduce store
overhead by getting customers to do more of the work while eliminating employees. The winners
are not the customers or people looking for a way to make ends meet.
Pavel
September 25, 2016 at 2:27 pm
Another goal of course is to track even further every single purchase - what, and where,
and when. And then sell the consumption data to the insurers perhaps… a packet of cigs per day?
Or too many bottles of booze?
Of course they are already doing that with the store "fidelity cards", but the mobile apps
will be more precise and less optional.
Notable quotes:
"... A U.S. investigation into a leak of hacking tools used by the National Security Agency is focusing on a theory that one of its operatives carelessly left them available on a remote computer ..."
"... The tools, which enable hackers to exploit software flaws in computer and communications systems from vendors such as Cisco Systems and Fortinet Inc, were dumped onto public websites last month by a group calling itself Shadow Brokers. ..."
"... But officials heading the FBI-led investigation now discount both of those scenarios, the people said in separate interviews. NSA officials have told investigators that an employee or contractor made the mistake about three years ago during an operation that used the tools, the people said. ..."
"... That person acknowledged the error shortly afterward, they said. But the NSA did not inform the companies of the danger when it first discovered the exposure of the tools, the sources said. Since the public release of the tools, the companies involved have issued patches in the systems to protect them. ..."
"... Because the sensors did not detect foreign spies or criminals using the tools on U.S. or allied targets, the NSA did not feel obligated to immediately warn the U.S. manufacturers, an official and one other person familiar with the matter said. ..."
A U.S. investigation into a leak of hacking tools used by the National Security Agency is focusing
on a theory that one of its operatives carelessly left them available on a remote computer and
Russian hackers found them, four people with direct knowledge of the probe told Reuters.The
tools, which enable hackers to exploit software flaws in computer and communications systems from
vendors such as Cisco Systems and Fortinet Inc, were dumped onto public websites last month by a
group calling itself Shadow Brokers.
The public release of the tools coincided with U.S. officials saying they had concluded that Russia
or its proxies were responsible for hacking political party organizations in the run-up to the Nov.
8 presidential election. On Thursday, lawmakers accused Russia of being responsible
... ... ...
But officials heading the FBI-led investigation now discount both of those scenarios, the
people said in separate interviews. NSA officials have told investigators that an employee or contractor
made the mistake about three years ago during an operation that used the tools, the people said.
That person acknowledged the error shortly afterward, they said. But the NSA did not inform the
companies of the danger when it first discovered the exposure of the tools, the sources said. Since
the public release of the tools, the companies involved have issued patches in the systems to protect
them.
Investigators have not ruled out the possibility that the former NSA person, who has since departed
the agency for other reasons, left the tools exposed deliberately. Another possibility, two of the
sources said, is that more than one person at the headquarters or a remote location made similar
mistakes or compounded each other's missteps.
Representatives of the NSA, the Federal Bureau of Investigation and the office of the Director of
National Intelligence all declined to comment.
After the discovery, the NSA tuned its sensors to detect use of any of the tools by other parties,
especially foreign adversaries with strong cyber espionage operations, such as China and Russia.
That could have helped identify rival powers' hacking targets, potentially leading them to be defended
better. It might also have allowed U.S officials to see deeper into rival hacking operations while
enabling the NSA itself to continue using the tools for its own operations.
Because the sensors did not detect foreign spies or criminals using the tools on U.S. or allied
targets, the NSA did not feel obligated to immediately warn the U.S. manufacturers, an official and
one other person familiar with the matter said.
In this case, as in more commonplace discoveries of security flaws, U.S. officials weigh what intelligence
they could gather by keeping the flaws secret against the risk to U.S. companies and individuals
if adversaries find the same flaws.
Richard Tynan, a technologist with Privacy International, told The Intercept
that the " manuals released today offer the most up-to-date view on the
operation of" Stingrays and similar cellular surveillance devices, with
powerful capabilities that threaten civil liberties, communications infrastructure,
and potentially national security. He noted that the documents show the
"Stingray II" device can impersonate four cellular communications towers
at once, monitoring up to four cellular provider networks simultaneously,
and with an add-on can operate on so-called 2G, 3G, and 4G networks simultaneously.
Notable quotes:
"... Submitted by Sophie McAdam via TrueActivist.com, ..."
"... He disclosed that government spies can legally hack into any citizen's phone to listen in to what's happening in the room, view files, messages and photos, pinpoint exactly where a person is (to a much more sophisticated level than a normal GPS system), and monitor a person's every move and every conversation, even when the phone is turned off. ..."
"... "Nosey Smurf": lets spies turn the microphone on and listen in on users, even if the phone itself is turned off ..."
"... Snowden says: "They want to own your phone instead of you." It sounds very much like he means we are being purposefully encouraged to buy our own tracking devices. That kinda saved the government some money, didn't it? ..."
"... It's one more reason to conclude that smartphones suck. And as much as we convince ourselves how cool they are, it's hard to deny their invention has resulted in a tendency for humans to behave like zombies , encouraged child labor, made us more lonely than ever, turned some of us into narcissistic selfie – addicts , and prevented us from communicating with those who really matter (the ones in the same room at the same time). Now, Snowden has given us yet another reason to believe that smartphones might be the dumbest thing we could have ever inflicted on ourselves. ..."
Submitted by Sophie McAdam via TrueActivist.com,
In an interview with the BBC's 'Panorama' which aired in Britain last week,
Edward Snowden spoke in detail about the spying capabilities of the UK intelligence
agency GCHQ. He disclosed that government spies can legally hack
into any citizen's phone to listen in to what's happening in the room, view
files, messages and photos, pinpoint exactly where a person is (to a much more
sophisticated level than a normal GPS system), and monitor a person's every
move and every conversation, even when the phone is turned off.
These technologies are named after Smurfs, those little
blue cartoon characters who had a recent Hollywood makeover. But despite the
cute name, these technologies are very disturbing; each one is built to spy
on you in a different way:
- "Dreamy Smurf": lets the phone be powered on and off
- "Nosey Smurf": lets spies turn the microphone on and listen in on
users, even if the phone itself is turned off
- "Tracker Smurf":a geo-location tool which allows [GCHQ]
to follow you with a greater precision than you would get from the typical
triangulation of cellphone towers.
- "Paranoid Smurf": hides the fact that it has taken
control of the phone. The tool will stop people from recognizing that the
phone has been tampered with if it is taken in for a service, for instance.
Snowden says: "They want to own your phone instead of you." It sounds
very much like he means we are being purposefully encouraged to buy our own
tracking devices. That kinda saved the government some money, didn't it?
His revelations should worry anyone who cares about human rights, especially
in an era where the threat of terrorism is used to justify all sorts of governmental
crimes against civil liberties. We have willingly given up our freedoms in the
name of security; as a result we have
neither. We seem to have forgotten that to live as a free person is a basic
human right: we are essentially free beings. We are born naked and without certification;
we do not belong to any government nor monarchy nor individual, we don't even
belong to any nation or culture or religion- these are all social constructs.
We belong only to the universe that created us, or whatever your equivalent
belief. It is therefore a natural human right not to be not be under secret
surveillance by your own government, those corruptible liars who are supposedly
elected by and therefore accountable to the people.
The danger for law-abiding citizens who say they have nothing to fear because
they are not terrorists, beware: many peaceful British protesters have been
arrested under the Prevention Of Terrorism Act since its introduction in
2005. Edward
Snowden's disclosure confirms just how far the attack on civil liberties
has gone since
9/11 and the London bombings. Both events have allowed governments the legal
right to essentially wage war on their own people, through the Patriot Act in
the USA and the Prevention Of Terrorism
Act in the UK. In Britain, as in the USA,
terrorism and
activism seem to have morphed into one entity, while nobody really knows
who the real
terrorists are any more. A sad but absolutely realistic fact of life in
2015: if you went to a peaceful protest at weekend and got detained, you're
probably getting
hacked right now.
It's one more reason to conclude that smartphones suck. And as much as
we convince ourselves how cool they are, it's hard to deny their invention has
resulted in a tendency for humans to behave like
zombies, encouraged child labor, made us more
lonely than ever, turned some of us into
narcissistic
selfie–addicts,
and prevented us from
communicating with those who really
matter (the ones in the same room at the same time). Now, Snowden has given
us yet another reason to believe that
smartphones might be the dumbest thing we could have ever inflicted on ourselves.
(arstechnica.com)
23
Posted
by manishs
on Tuesday September 06, 2016 @02:00PM
from the
security-woes
dept.
Sean Gallagher, writing for ArsTechnica:
Another
major site breach from four years ago has
resurfaced. Today, LeakedSource revealed that it had
received a copy of a February 2012 dump of the user
database of Rambler.ru
, a Russian search, news,
and e-mail portal site that closely mirrors the
functionality of Yahoo. The dump included usernames,
passwords, and ICQ instant messaging accounts for
over 98 million users. And while previous breaches
uncovered by LeakedSource this year had at least
some encryption of passwords, the Rambler.ru
database stored user passwords in plain text --
meaning that whoever breached the database instantly
had access to the e-mail accounts of all of
Rambler.ru's users. The breach is the latest in a
series of "mega-breaches" that LeakedSource says it
is processing for release. Rambler isn't the only
Russian site that has been caught storing
unencrpyted passwords by hackers. In June, a hacker
offered for sale the entire user database of the
Russian-language social networking site VK.com
(formerly VKontakte) from a breach that took place
in late 2012 or early 2013; that database also
included unencrypted user passwords, as ZDNet's Zach
Whittaker reported.
(theintercept.com)
94
Posted
by manishs
on Monday September 12, 2016 @04:00PM
from the
truth-is-out-there
dept.
The Intercept has today published
200-page documents revealing details about Harris
Corp's Stingray surveillance device
, which has
been one of the closely guarded secrets in law
enforcement for more than 15 years. The firm, in
collaboration with police clients across the U.S.
have "fought" to keep information about the mobile
phone-monitoring boxes from the public against which
they are used. The publication reports that the
surveillance equipment carries a price tag in the
"low six figures." From the report:
The San
Bernardino Sheriff's Department alone has snooped
via Stingray, sans warrant, over 300 times. Richard
Tynan, a technologist with Privacy International,
told The Intercept that the "manuals released today
offer the
most up-to-date view on the operation of
"
Stingrays and similar cellular surveillance devices,
with powerful capabilities that threaten civil
liberties, communications infrastructure, and
potentially national security. He noted that the
documents show the "Stingray II" device can
impersonate four cellular communications towers at
once, monitoring up to four cellular provider
networks simultaneously, and with an add-on can
operate on so-called 2G, 3G, and 4G networks
simultaneously.
Pavel ,
September 3, 2016 at 8:11 am
I just found this via Hacker News… perhaps it was in yesterday's links and I missed it. Truly
scary in the Orwellian sense and yet another reason not to use a smartphone. Chilling read.
SAN FRANCISCO - Want to invisibly spy on 10 iPhone owners without their knowledge? Gather their
every keystroke, sound, message and location? That will cost you $650,000, plus a $500,000 setup
fee with an Israeli outfit called the NSO Group. You can spy on more people if you would like
- just check out the company's price list.
The NSO Group is one of a number of companies that sell surveillance tools that can capture
all the activity on a smartphone, like a user's location and personal contacts. These tools can
even turn the phone into a secret recording device.
Since its founding six years ago, the NSO Group has kept a low profile. But last month, security
researchers caught its spyware trying to gain access to the iPhone of a human rights activist
in the United Arab Emirates. They also discovered a second target, a Mexican journalist who wrote
about corruption in the Mexican government.
Now, internal NSO Group emails, contracts and commercial proposals obtained by The New York
Times offer insight into how companies in this secretive digital surveillance industry operate.
The emails and documents were provided by two people who have had dealings with the NSO Group
but would not be named for fear of reprisals.
–NY Times: How Spy Tech Firms Let Governments See Everything on a Smartphone
There is interesting and expert commentary in the Hacker News forum:
https://news.ycombinator.com/item?id=12417938.
Pat ,
September 3, 2016 at 12:01 pm
I could be wrong, but the promos for Sixty Minutes on the local news make it seem they might
be about this subject. Either way it is another scare you about what your cell phone can do story,
possibly justified this time.
Jeotsu ,
September 3, 2016 at 2:15 pm
An anecdote which I cannot support with links or other evidence:
A friend of mine used to work for a (non USA) security intelligence service. I was bouncing
ideas off him for a book I'm working on, specifically ideas about how monitoring/electronics/spying
can be used to measure and manipulate societies. He was useful for telling if my ideas (for a
Science Fiction novel) were plausible without ever getting into details. Always very careful to
keep his replies in the "white" world of what any computer security person would know, without
delving into anything classified.
One day we were way out in the back blocks, and I laid out one scenario for him to see if it
would be plausible. All he did was small cryptically, and point at a cell phone lying on a table
10 meters away. He wouldn't say a word on the subject.
It wasn't his cellphone, and we were in a relatively remote region with no cell phone coverage.
It told me that my book idea was far too plausible. It also told me that every cellphone is
likely recording everything all the time, for later upload when back in signal range. (Or at least
there was the inescapable possibility that the cell phones were doing so, and that he had to assume
foreign (or domestic?) agencies could be following him through monitoring of cell phones of friends
and neighbors.)
It was a clarifying moment for me.
Every cellphone has a monumental amount of storage space (especially for audio files). Almost
every cellphone only has a software "switch" for turning it off, not a hardware interlock where
you can be sure off is off. So how can you ever really be sure it is "off"? Answer- you can't
Sobering thought. Especially when you consider the Bluffdale facility in the USA.
The New York Times
There are dozens of digital spying companies that can
track everything a target does on a smartphone.
Credit
Spencer Platt/Getty Images
SAN FRANCISCO - Want to invisibly spy on 10
iPhone
owners without their knowledge? Gather their every keystroke, sound,
message and location? That will cost you $650,000, plus a $500,000 setup fee with an
Israeli outfit called the NSO Group. You can spy on more people if you would like -
just check out the company's price list.
The NSO Group is one of a number of companies that
sell surveillance tools
that can capture all the activity on a smartphone, like a
user's location and personal contacts. These tools can even turn the phone into a
secret recording device.
Since its founding six years ago, the NSO Group has kept a low profile. But last
month, security researchers
caught its spyware trying to gain access
to the iPhone of a human rights activist
in the United Arab Emirates. They also discovered a second target, a Mexican
journalist who wrote about corruption in the Mexican government.
Now, internal NSO Group emails, contracts and commercial proposals obtained by The
New York Times offer insight into how companies in this secretive digital
surveillance industry operate. The emails and documents were provided by two people
who have had dealings with the NSO Group but would not be named for fear of
reprisals.
The company is one of dozens of digital spying outfits that track everything a target
does on a smartphone. They aggressively market their services to governments and law
enforcement agencies around the world. The industry argues that this spying is
necessary to track terrorists, kidnappers and drug lords. The NSO Group's corporate
mission statement is "Make the world a safe place."
Ten people familiar with the company's sales, who refused to be identified, said that
the NSO Group has a strict internal vetting process to determine who it will sell to.
An ethics committee made up of employees and external counsel vets potential
customers based on human rights rankings set by the World Bank and other global
bodies. And to date, these people all said, NSO has yet to be denied an export
license.
But critics note that the company's spyware has also been used to track journalists
and human rights activists.
"There's no check on this," said Bill Marczak, a senior fellow at the Citizen Lab at
the University of Toronto's Munk School of Global Affairs. "Once NSO's systems are
sold, governments can essentially use them however they want. NSO can say they're
trying to make the world a safer place, but they are also making the world a more
surveilled place."
The NSO Group's capabilities are in higher demand now that companies like Apple,
Facebook and Google are using stronger encryption to protect data in their systems,
in the process making it harder for government agencies to track suspects.
The NSO Group's spyware finds ways around encryption by baiting targets to click
unwittingly on texts containing malicious links or by exploiting previously
undiscovered software flaws. It was taking advantage of
three such flaws in Apple software
- since fixed - when it was discovered by
researchers last month.
The cyberarms industry typified by the NSO Group operates in a legal gray area, and
it is often left to the companies to decide how far they are willing to dig into a
target's personal life and what governments they will do business with. Israel has
strict export controls for digital weaponry, but the country has never barred the
sale of NSO Group technology.
Since it is privately held, not much is known about the NSO Group's finances, but its
business is clearly growing. Two years ago, the NSO Group sold a controlling stake in
its business to Francisco Partners, a
private equity
firm based in San Francisco, for $120 million. Nearly a year
later, Francisco Partners was exploring a sale of the company for 10 times that
amount, according to two people approached by the firm but forbidden to speak about
the discussions.
The company's internal documents detail pitches to countries throughout Europe and
multimillion-dollar contracts with Mexico, which paid the NSO Group more than $15
million for three projects over three years, according to internal NSO Group emails
dated in 2013.
"Our intelligence systems are subject to Mexico's relevant legislation and have legal
authorization," Ricardo Alday, a spokesman for the Mexican embassy in Washington,
said in an emailed statement. "They are not used against journalists or activists.
All contracts with the federal government are done in accordance with the law."
Zamir Dahbash, an NSO Group spokesman, said that the sale of its spyware was
restricted to authorized governments and that it was used solely for criminal and
terrorist investigations. He declined to comment on whether the company would cease
selling to the U.A.E. and Mexico after last week's disclosures.
For the last six years, the NSO Group's main product, a tracking system called
Pegasus, has been used by a growing number of government agencies to target a range
of smartphones - including iPhones, Androids, and BlackBerry and Symbian systems -
without leaving a trace.
Among the Pegasus system's capabilities, NSO Group contracts assert, are the
abilities to extract text messages, contact lists, calendar records, emails, instant
messages and GPS locations. One capability that the NSO Group calls "room tap" can
gather sounds in and around the room, using the phone's own microphone.
Pegasus can use the camera to take snapshots or screen grabs. It can deny the phone
access to certain websites and applications, and it can grab search histories or
anything viewed with the phone's web browser. And all of the data can be sent back to
the agency's server in real time.
In its commercial proposals, the NSO Group asserts that its tracking software and
hardware can install itself in any number of ways, including "over the air stealth
installation," tailored text messages and emails, through public Wi-Fi hot spots
rigged to secretly install NSO Group software, or the old-fashioned way, by spies in
person.
Much like a traditional software company, the NSO Group prices its surveillance tools
by the number of targets, starting with a flat $500,000 installation fee. To spy on
10 iPhone users, NSO charges government agencies $650,000; $650,000 for 10 Android
users; $500,000 for five BlackBerry users; or $300,000 for five Symbian users - on
top of the setup fee, according to one commercial proposal.
You can pay for more targets. One hundred additional targets will cost $800,000, 50
extra targets cost $500,000, 20 extra will cost $250,000 and 10 extra costs $150,000,
according to an NSO Group commercial proposal. There is an annual system maintenance
fee of 17 percent of the total price every year thereafter.
What that gets you, NSO Group documents say, is "unlimited access to a target's
mobile devices." In short, the company says: You can "remotely and covertly collect
information about your target's relationships, location, phone calls, plans and
activities - whenever and wherever they are."
And, its proposal adds, "It leaves no traces whatsoever."
Notable quotes:
"... Some "American" companies and public research institutions are surely victims of espionage, but for the most part private industry has brought this on itself by building offshore offices and *actively* directing their workers to transfer the knowledge and "train their replacements", so that they can do the work instead of US workers who are let go (or not again hired) because their skills are now "irrelevant". ..."
"... In "defense" or "national interest" related work, for the most part citizens of or even people originating from countries that are considered military or geopolitical adversaries are excluded from participation. This makes it much harder to infiltrate people in the US, as long as it is not offshored. But then the US govt and its contractors will pay higher rates for the product/service than US consumers who will have to do "more with less" (money). ..."
"... Oh, China (public and private entities) surely engages in those things it is accused of, but this is by far outweighed by US business captains shoving the "free" know-how and innovation down their throats to enable the short term "cost savings" (which will in short order be compensated for by declining aggregate demand when the formerly well paid local staff can only buy the cheapest stuff, and retail adjusts and mostly orders the cheapest). ..."
"... Likewise most "everybody else" also. I have a good number of colleagues from China and other Asian countries. Many of them take pride in coming up with their own solutions instead of copying stuff, like people everywhere. ..."
"... A German language article where this and other cases are mentioned: http://www.zeit.de/1998/28/199828.spionage.neu_.xml Nobody is squeaky clean in this game. ..."
"... At the time I was working in a tech company there, and new security protocols were instituted, like not sending certain confidential information by email or fax. There was even an anecdote (unverified) of how a foreign service (not US in that case) was allegedly intercepting business documents/negotiations that were conducted by fax, and making the information available to "their" own companies bidding for the same project. Whether true or not, that's what the management was concerned about. ..."
EMichael :
August 28, 2016 at 11:14 AM
"Transfer" has more than one meaning.
" If spying is the world's second oldest profession, the government of China has given it a
new, modern-day twist, enlisting an army of spies not to steal military secrets but the trade
secrets and intellectual property of American companies. It's being called "the great brain robbery
of America."
The Justice Department says that the scale of China's corporate espionage is so vast it constitutes
a national security emergency, with China targeting virtually every sector of the U.S. economy,
and costing American companies hundreds of billions of dollars in losses -- and more than two
million jobs.
John Carlin: They're targeting our private companies. And it's not a fair fight. A private
company can't compete against the resources of the second largest economy in the world."
John Carlin: This is a serious threat to our national security. I mean, our economy depends on
the ability to innovate. And if there's a dedicated nation state who's using its intelligence
apparatus to steal day in and day out what we're trying to develop, that poses a serious threat
to our country.
Lesley Stahl: What is their ultimate goal, the Chinese government's ultimate goal?
John Carlin: They want to develop certain segments of industry and instead of trying to out-innovate,
out-research, out-develop, they're choosing to do it through theft.
All you have to do, he says, is look at the economic plans published periodically by the Chinese
Politburo. They are, according to this recent report by the technology research firm INVNT/IP,
in effect, blueprints of what industries and what companies will be targeted for theft."
http://www.cbsnews.com/news/60-minutes-great-brain-robbery-china-cyber-espionage/
cm -> EMichael,
August
28, 2016 at 12:38 PM
Some "American" companies and public research institutions are surely victims of espionage,
but for the most part private industry has brought this on itself by building offshore offices
and *actively* directing their workers to transfer the knowledge and "train their replacements",
so that they can do the work instead of US workers who are let go (or not again hired) because
their skills are now "irrelevant".
Likewise if a manufacturer outsources to an offshore supplier, they have to divulge some of
their secret sauce and technical skill to their "partner" if they want the product to meet specs
and quality metrics.
In "defense" or "national interest" related work, for the most part citizens of or even
people originating from countries that are considered military or geopolitical adversaries are
excluded from participation. This makes it much harder to infiltrate people in the US, as long
as it is not offshored. But then the US govt and its contractors will pay higher rates for the
product/service than US consumers who will have to do "more with less" (money).
Paine -> cm... ,
Sunday, August 28, 2016 at 02:02 PM
Important
We have a serious industry in dis info about china
cm -> Paine... ,
Sunday, August 28, 2016 at 03:47 PM
Oh, China (public and private entities) surely engages in those things it is accused of, but
this is by far outweighed by US business captains shoving the "free" know-how and innovation down
their throats to enable the short term "cost savings" (which will in short order be compensated
for by declining aggregate demand when the formerly well paid local staff can only buy the cheapest
stuff, and retail adjusts and mostly orders the cheapest).
cm -> Paine... ,
Sunday, August 28, 2016 at 03:54 PM
Likewise most "everybody else" also. I have a good number of colleagues from China and other
Asian countries. Many of them take pride in coming up with their own solutions instead of copying
stuff, like people everywhere.
"Stealing" of ideas is practiced everywhere. I know an anecdote from a "Western" company where
a high level engineering manager suggested inviting another academic/research group on the pretext
of exploring a collaboration, only to get enough of an idea of their approach, and then dump them.
Several of the present staff balked at this and it didn't go anywhere. But it was instructive.
Paine -> cm... ,
Sunday, August 28, 2016 at 05:05 PM
I'd suggest stolen " recipes " to use Paul Romers term
Only encourage the parallel Han project
You can't really build something significantly novel
Simply out of specs
Paine -> Paine... ,
Sunday, August 28, 2016 at 05:05 PM
Classic case
The soviet a bomb project
cm -> Paine... ,
Sunday, August 28, 2016 at 05:43 PM
There are two aspects of "stealing ideas":
(1) How is it done (because we don't know)
(2) Which approach has been proven to work (out of many that we would have to try)
The focus in discussing the topic is often on (1), and it is certainly an important aspect,
perhaps the most important one if the adversary is in bootstrapping mode.
However once you are at a certain level, (2) becomes more important - the solution space is
simply too large, and knowing what has already worked elsewhere can cut through a lot of failed
experiments (including finding a better solution of course).
(2) also relates somewhat to "best practices" - don't try to innovate and create yet another
proprietary thing that only the people who created it understand, do what everybody else is doing,
then you can hire more people who "already know it", or if "others" improve or build on the existing
solution, that immediately applies to your version as well.
The downside is that your solution is not "differentiated". But if it is cheaper it doesn't
have to.
ilsm -> Paine... ,
Sunday, August 28, 2016 at 04:20 PM
To sell F-35 the US gives everything needed to manufacture parts of the aircraft to the buying
country...
To do that or any other kind of manufacturing the processes with all drawings and accurate
parts lists are in the plant.........
If you can keep that stuff 'under wraps' you spend a lot, fill the plant with US personnel
, endure inefficiencies, create bottlenecks....
cm -> EMichael... ,
Sunday, August 28, 2016 at 01:05 PM
Then there was a story about this:
https://en.wikipedia.org/wiki/Enercon#Patent_dispute
where US electronic surveillance was allegedly involved in a business dispute. In this case
there is no explicit claim about technology theft, but two companies were accusing each other
of patent violations, and espionage techniques were used to "obtain evidence".
cm -> cm... ,
Sunday, August 28, 2016 at 01:07 PM
A German language article where this and other cases are mentioned:
http://www.zeit.de/1998/28/199828.spionage.neu_.xml
Nobody is squeaky clean in this game.
cm -> cm... ,
Sunday, August 28, 2016 at 04:12 PM
BTW note the date - this kind of stuff was going on in the 90's. It is not a recent invention.
BTW this here was mentioned, you may have heard of it, in any case it was a big deal in Germany
where the US had several operational bases:
https://en.wikipedia.org/wiki/ECHELON
At the time I was working in a tech company there, and new security protocols were instituted,
like not sending certain confidential information by email or fax. There was even an anecdote
(unverified) of how a foreign service (not US in that case) was allegedly intercepting business
documents/negotiations that were conducted by fax, and making the information available to "their"
own companies bidding for the same project. Whether true or not, that's what the management was
concerned about.
Paine -> EMichael... ,
Sunday, August 28, 2016 at 02:00 PM
Pure propaganda
You have a embark able tolerance for manipulation
Paine -> EMichael... ,
Sunday, August 28, 2016 at 02:04 PM
Trump talk modulated by the manhattan elites
The same pokes that play the other end of the stick
That de industrialized the rust belt
Notable quotes:
"... The evidence that ties the ShadowBrokers dump to the NSA comes in an agency manual for implanting
malware, classified top secret, provided by Snowden, and not previously available to the public. The
draft manual instructs NSA operators to track their use of one malware program using a specific 16-character
string, "ace02468bdf13579." That exact same string appears throughout the ShadowBrokers leak in code
associated with the same program, SECONDDATE. ..."
On Monday, a hacking group calling itself the "ShadowBrokers" announced an auction for what it claimed
were "cyber weapons" made by the NSA. Based on never-before-published documents provided by the whistleblower
Edward Snowden, The Intercept can confirm that the arsenal contains authentic NSA software,
part of a powerful constellation of tools used to covertly infect computers worldwide.The provenance
of the code has been a matter of heated debate this week among cybersecurity experts, and while it
remains unclear how the software leaked, one thing is now beyond speculation: The malware is covered
with the NSA's virtual fingerprints and clearly originates from the agency.
The evidence that ties the ShadowBrokers dump to the NSA comes in an agency manual for implanting
malware, classified top secret, provided by Snowden, and not previously available to the public.
The draft manual instructs NSA operators to track their use of one malware program using a specific
16-character string, "ace02468bdf13579." That exact same string appears throughout the ShadowBrokers
leak in code associated with the same program, SECONDDATE.
SECONDDATE plays a specialized role inside a complex global system built by the U.S. government
to infect and monitor what one document
estimated to be millions of computers around the world. Its release by ShadowBrokers, alongside
dozens of other malicious tools, marks the first time any full copies of the NSA's offensive software
have been available to the public, providing a glimpse at how an elaborate system outlined in the
Snowden documents looks when deployed in the real world, as well as concrete evidence that NSA hackers
don't always have the last word when it comes to computer exploitation.
But malicious software of this sophistication doesn't just pose a threat to foreign governments,
Johns Hopkins University cryptographer Matthew Green told The Intercept:
The danger of these exploits is that they can be used to target anyone who is using a vulnerable
router. This is the equivalent of leaving lockpicking tools lying around a high school cafeteria.
It's worse, in fact, because many of these exploits are not available through any other means,
so they're just now coming to the attention of the firewall and router manufacturers that need
to fix them, as well as the customers that are vulnerable.
So the risk is twofold: first, that the person or persons who stole this information might
have used them against us. If this is indeed Russia, then one assumes that they probably have
their own exploits, but there's no need to give them any more. And now that the exploits have
been released, we run the risk that ordinary criminals will use them against corporate targets.
The NSA did not respond to questions concerning ShadowBrokers, the Snowden documents, or its malware.
A Memorable SECONDDATE
The offensive tools released by ShadowBrokers are organized under a litany of code names such
as POLARSNEEZE and ELIGIBLE BOMBSHELL, and their exact purpose is still being assessed. But we do
know more about one of the weapons: SECONDDATE.
SECONDDATE is a tool designed to intercept web requests and redirect browsers on target computers
to an NSA web server. That server, in turn, is designed to infect them with malware. SECONDDATE's
existence was
first reported by The Intercept in 2014, as part of a look at a global computer exploitation
effort code-named TURBINE. The malware server, known as FOXACID, has also been
described in previously released Snowden documents.
Other documents released by The Intercept today not only tie SECONDDATE to the ShadowBrokers
leak but also provide new detail on how it fits into the NSA's broader surveillance and infection
network. They also show how SECONDDATE has been used, including to spy on Pakistan and a computer
system in Lebanon.
The top-secret manual that authenticates the SECONDDATE found in the wild as the same one used
within the NSA is a 31-page document titled "FOXACID
SOP for Operational Management" and marked as a draft. It dates to no earlier than 2010. A section
within the manual describes administrative tools for tracking how victims are funneled into FOXACID,
including a set of tags used to catalogue servers. When such a tag is created in relation to a SECONDDATE-related
infection, the document says, a certain distinctive identifier must be used:

The same SECONDDATE MSGID string appears in 14 different files throughout the ShadowBrokers leak,
including in a file titled SecondDate-3021.exe. Viewed through a code-editing program (screenshot
below), the NSA's secret number can be found hiding in plain sight:

All told, throughout many of the folders contained in the ShadowBrokers' package (screenshot below),
there are 47 files with SECONDDATE-related names, including different versions of the raw code required
to execute a SECONDDATE attack, instructions for how to use it, and other related files.
.

After viewing the code, Green told The Intercept the MSGID string's occurrence in both
an NSA training document and this week's leak is "unlikely to be a coincidence." Computer security
researcher Matt Suiche, founder of UAE-based cybersecurity startup Comae Technologies, who has been
particularly vocal in his analysis of the ShadowBrokers this week, told The Intercept "there
is no way" the MSGID string's appearance in both places is a coincidence.
Where SECONDDATE Fits In
This overview jibes with previously unpublished classified files provided by Snowden that illustrate
how SECONDDATE is a component of BADDECISION, a broader NSA infiltration tool. SECONDDATE helps the
NSA pull off a "man in the middle" attack against users on a wireless network, tricking them into
thinking they're talking to a safe website when in reality they've been sent a malicious payload
from an NSA server.
According to one December 2010 PowerPoint presentation titled "Introduction
to BADDECISION," that tool is also designed to send users of a wireless network, sometimes referred
to as an 802.11 network, to FOXACID malware servers. Or, as the presentation puts it, BADDECISION
is an "802.11 CNE [computer network exploitation] tool that uses a true man-in-the-middle attack
and a frame injection technique to redirect a target client to a FOXACID server." As another
top-secret slide puts it, the attack homes in on "the greatest vulnerability to your computer:
your web browser."

One slide points out that the attack works on users with an encrypted wireless connection to the
internet.
That trick, it seems, often involves BADDECISION and SECONDDATE, with the latter described as
a "component" for the former. A series of diagrams in the "Introduction to BADDECISION" presentation
show how an NSA operator "uses SECONDDATE to inject a redirection payload at [a] Target Client,"
invisibly hijacking a user's web browser as the user attempts to visit a benign website (in the example
given, it's CNN.com). Executed correctly, the file explains, a "Target Client continues normal webpage
browsing, completely unaware," lands on a malware-filled NSA server, and becomes infected with as
much of that malware as possible - or as the presentation puts it, the user will be left "WHACKED!"
In the other top-secret presentations, it's put plainly: "How
do we redirect the target to the FOXACID server without being noticed"? Simple: "Use NIGHTSTAND
or BADDECISION."
The sheer number of interlocking tools available to crack a computer is dizzying. In the
FOXACID manual, government hackers are told an NSA hacker ought to be familiar with using SECONDDATE
along with similar man-in-the-middle wi-fi attacks code-named MAGIC SQUIRREL and MAGICBEAN. A top-secret
presentation on FOXACID lists further ways to redirect targets to the malware server system.

To position themselves within range of a vulnerable wireless network, NSA operators can use a
mobile antenna system running software code-named BLINDDATE, depicted in the field in what appears
to be Kabul. The software can even be attached to a drone. BLINDDATE in turn can run BADDECISION,
which allows for a SECONDDATE attack:

Elsewhere in these files, there are at least two documented cases of SECONDDATE being used to
successfully infect computers overseas: An April 2013
presentation boasts of successful attacks against computer systems in both Pakistan and Lebanon.
In the first, NSA hackers used SECONDDATE to breach "targets in Pakistan's National Telecommunications
Corporation's (NTC) VIP Division," which contained documents pertaining to "the backbone of Pakistan's
Green Line communications network" used by "civilian and military leadership."
In the latter, the NSA used SECONDDATE to pull off a man-in-the-middle attack in Lebanon "for
the first time ever," infecting a Lebanese ISP to extract "100+ MB of Hizballah Unit 1800 data,"
a special subset of the terrorist group dedicated to aiding Palestinian militants.
SECONDDATE is just one method that the NSA uses to get its target's browser pointed at a FOXACID
server. Other methods include sending spam that attempts to exploit bugs in popular web-based email
providers or entices targets to click on malicious links that lead to a FOXACID server. One
document, a newsletter for the NSA's Special Source Operations division, describes how NSA software
other than SECONDDATE was used to repeatedly direct targets in Pakistan to FOXACID malware web servers,
eventually infecting the targets' computers.
A Potentially Mundane Hack
Snowden, who worked for NSA contractors Dell and Booz Allen Hamilton, has offered some context
and a relatively mundane possible explanation for the leak: that the NSA headquarters was not hacked,
but rather one of the computers the agency uses to plan and execute attacks was compromised. In a
series of tweets,
he pointed out that the NSA often lurks on systems that are supposed to be controlled by others,
and it's possible someone at the agency took control of a server and failed to clean up after themselves.
A regime, hacker group, or intelligence agency could have seized the files and the opportunity to
embarrass the agency.
Documents
Documents published with this story:
Notable quotes:
"... The NSA identified Peña's cellphone and those of his associates using advanced software that can filter out specific phones from the swarm around the candidate. These lines were then targeted. The technology, one NSA analyst noted, "might find a needle in a haystack." The analyst described it as "a repeatable and efficient" process. ..."
"... Another NSA operation, begun in May 2010 and codenamed FLATLIQUID, targeted Pena's predecessor, President Felipe Calderon. The NSA, the documents revealed, was able "to gain first-ever access to President Felipe Calderon's public email account." ..."
"... At the same time, members of a highly secret joint NSA/CIA organization, called the Special Collection Service, are based in the U.S. embassy in Mexico City and other U.S. embassies around the world. It targets local government communications, as well as foreign embassies nearby. For Mexico, additional eavesdropping, and much of the analysis, is conducted by NSA Texas, a large listening post in San Antonio that focuses on the Caribbean, Central America and South America. ..."
"... Unlike the Defense Department's Pentagon, the headquarters of the cyberspies fills an entire secret city. Located in Fort Meade, Maryland, halfway between Washington and Baltimore, Maryland, NSA's headquarters consists of scores of heavily guarded buildings. The site even boasts its own police force and post office. ..."
"... One top-secret operation, code-named TreasureMap, is designed to have a "capability for building a near real-time interactive map of the global Internet. … Any device, anywhere, all the time." Another operation, codenamed Turbine, involves secretly placing "millions of implants" - malware - in computer systems worldwide for either spying or cyberattacks. ..."
"... Yet there can never be a useful discussion on the topic if the Obama administration continues to point fingers at other countries without admitting that Washington is engaged heavily in cyberspying and cyberwarfare. ..."
"... The Shadow Factory: The Ultra-Secret NSA From 9/11 to the Eavesdropping on America ..."
National attention is focused on Russian eavesdroppers' possible targeting of U.S. presidential candidates
and the Democratic Congressional Campaign Committee. Yet, leaked top-secret National Security Agency
documents show that the Obama administration has long been involved in major bugging operations against
the election campaigns -- and the presidents -- of even its closest allies.The United States is,
by far, the world's
most aggressive
nation when it comes to cyberspying and cyberwarfare. The National Security Agency has been eavesdropping
on foreign cities, politicians, elections and entire countries since it first turned on its receivers
in 1952. Just as other countries, including Russia, attempt to do to the United States. What is new
is a country leaking the intercepts back to the public of the target nation through a middleperson.
There is a strange irony in this. Russia, if it is actually involved in the hacking of the computers
of the Democratic National Committee, could be attempting to influence a U.S. election by leaking
to the American public the falsehoods of its leaders. This is a tactic Washington used against the
Soviet Union and other countries during the Cold War.
In the 1950s, for example, President Harry S Truman created the Campaign of Truth to reveal to
the Russian people the "Big Lies" of their government. Washington had often discovered these lies
through eavesdropping and other espionage.
Today, the United States has morphed from a Cold War, and in some cases a hot war, into a cyberwar,
with computer coding replacing bullets and bombs. Yet the American public manages to be "shocked,
shocked" that a foreign country would attempt to conduct cyberespionage on the United States.
NSA operations have, for example, recently delved into elections in Mexico, targeting its
last presidential campaign. According to a top-secret PowerPoint presentation leaked by former NSA
contract employee Edward Snowden, the operation involved a "surge effort against one of Mexico's
leading presidential candidates, Enrique Peña Nieto, and nine of his close associates." Peña won
that election and is now Mexico's president.
The NSA identified Peña's cellphone and those of his associates using advanced software that can
filter out specific phones from the swarm around the candidate. These lines were then targeted. The
technology, one NSA analyst noted, "might find a needle in a haystack." The analyst described it
as "a repeatable and efficient" process.
The eavesdroppers also succeeded in intercepting 85,489 text messages, a
Der Spiegel article noted.
Another NSA operation, begun in May 2010 and codenamed FLATLIQUID, targeted Pena's predecessor,
President Felipe Calderon. The NSA, the documents revealed, was able "to gain first-ever access to
President Felipe Calderon's public email account."
At the same time, members of a highly secret joint NSA/CIA organization, called the Special Collection
Service, are based in the U.S. embassy in Mexico City and other U.S. embassies around the world.
It targets local government communications, as well as foreign embassies nearby. For Mexico, additional
eavesdropping, and much of the analysis, is conducted by NSA Texas, a large listening post in San
Antonio that focuses on the Caribbean, Central America and South America.
Unlike the Defense Department's Pentagon, the headquarters of the cyberspies fills an entire secret
city. Located in Fort Meade, Maryland, halfway between Washington and Baltimore, Maryland, NSA's
headquarters consists of scores of heavily guarded buildings. The site even boasts its own police
force and post office.
And it is about to grow considerably bigger, now that the NSA cyberspies have merged with the
cyberwarriors of U.S. Cyber Command, which controls its own Cyber Army, Cyber Navy, Cyber Air Force
and Cyber Marine Corps, all armed with state-of-the-art cyberweapons. In charge of it all is a four-star
admiral, Michael S. Rogers.
Now under construction inside NSA's secret city, Cyber Command's new $3.2- billion headquarters
is to include 14 buildings, 11 parking garages and an enormous cyberbrain - a 600,000-square-foot,
$896.5-million supercomputer facility that will eat up an enormous amount of power, about 60 megawatts.
This is enough electricity to power a city of more than 40,000 homes.
In 2014, for a cover story in Wired and a PBS documentary, I spent three days in Moscow
with Snowden, whose last NSA job was as a contract cyberwarrior. I was also granted rare access to
his archive of documents. "Cyber Command itself has always been branded in a sort of misleading way
from its very inception," Snowden told me. "It's an attack agency. … It's all about computer-network
attack and computer-network exploitation at Cyber Command."
The idea is to turn the Internet from a worldwide web of information into a global battlefield
for war. "The next major conflict will start in cyberspace," says one of the secret NSA documents.
One key phrase within Cyber Command documents is "Information Dominance."
The Cyber Navy, for example, calls itself the Information Dominance Corps. The Cyber Army is providing
frontline troops with the option of requesting "cyberfire support" from Cyber Command, in much the
same way it requests air and artillery support. And the Cyber Air Force is pledged to "dominate cyberspace"
just as "today we dominate air and space."
Among the tools at their disposal is one called Passionatepolka, designed to "remotely brick network
cards." "Bricking" a computer means destroying it – turning it into a brick.
One such situation took place in war-torn Syria in 2012, according to Snowden, when the NSA attempted
to remotely and secretly install an "exploit," or bug, into the computer system of a major Internet
provider. This was expected to provide access to email and other Internet traffic across much of
Syria. But something went wrong. Instead, the computers were bricked. It
took down the Internet across the country for a period of time.
While Cyber Command executes attacks, the National Security Agency seems more interested in tracking
virtually everyone connected to the Internet, according to the documents.
One top-secret operation, code-named TreasureMap, is designed to have a "capability for building
a near real-time interactive map of the global Internet. … Any device, anywhere, all the time." Another
operation, codenamed Turbine, involves secretly placing "millions of implants" - malware - in computer
systems worldwide for either spying or cyberattacks.
Yet, even as the U.S. government continues building robust eavesdropping and attack systems, it
looks like there has been far less focus on security at home. One benefit of the cyber-theft of the
Democratic National Committee emails might be that it helps open a public dialogue about the dangerous
potential of cyberwarfare. This is long overdue. The
possible security problems for the U.S. presidential election in November are already being discussed.
Yet there can never be a useful discussion on the topic if the Obama administration continues
to point fingers at other countries without admitting that Washington is engaged heavily in cyberspying
and cyberwarfare.
In fact, the United States is the only country ever to launch an actual cyberwar -- when the Obama
administration used a cyberattack to destroy thousands of centrifuges, used for nuclear enrichment,
in Iran. This was an illegal act of war, according to the Defense Department's own definition.
Given the news reports that many more DNC emails are waiting to be leaked as the presidential
election draws closer, there will likely be many more reminders of the need for a public dialogue
on cybersecurity and cyberwarfare before November.
(James Bamford is the author of The Shadow Factory: The Ultra-Secret NSA From 9/11 to the
Eavesdropping on America. He is a columnist for Foreign Policy magazine.)
© Photo: Screenshot: Council of Europe
News
21:57 06.08.2016
(updated
04:45 07.08.2016)
Get short URL
31
62487
109
20
After posting a 64 character hex code
that is believed to be an encryption key, the internet worries that the famed
whistleblower may have been killed or captured resulting in the triggering of a dead
man's switch and potentially the release of many more US national secrets.
 © AP Photo/ Christopher Lane
Edward Snowden Not Dead: 'He's Fine' Says Glenn Greenwald After Mysterious
Tweet
On Friday night, famed NSA whistleblower Edward Snowden tweeted out a 64 character
code before quickly deleting the message along with a mysterious warning earlier this
week that "It's Time" which had called on colleagues of the former contractor
to contact him leaving the internet to speculate that the characters could be an
encryption key for a major document leak, it may be a "dead man's switch" set to go
in effect if the whistleblower were killed or captured, or potentially both.
© AP Photo/ Christopher Lane
Edward Snowden Not Dead: 'He's Fine' Says Glenn Greenwald After Mysterious
Tweet
On Friday night, famed NSA whistleblower Edward Snowden tweeted out a 64 character
code before quickly deleting the message along with a mysterious warning earlier this
week that "It's Time" which had called on colleagues of the former contractor
to contact him leaving the internet to speculate that the characters could be an
encryption key for a major document leak, it may be a "dead man's switch" set to go
in effect if the whistleblower were killed or captured, or potentially both.
A dead man's switch is a message set up to be automatically sent if the holder
of an account does not perform a regular check-in. The whistleblower has acknowledged
that he has distributed encrypted files to journalists and associates that have not
yet been released so in Snowden's case, the dead man's switch could be an encryption
key for those files.
As of this time, Edward Snowden's Twitter account has gone silent for over 24
hours which is far from unprecedented for the whistleblower but is curious at a time
when public concern has been raised over his well-being. The 64 hex characters in the
code do appear to rule out the initial theory that Edward Snowden, like so many
of us, simply butt dialed his phone, but instead is a clearly a secure hash algorithm
that can serve as a signature for a data file or as a password.
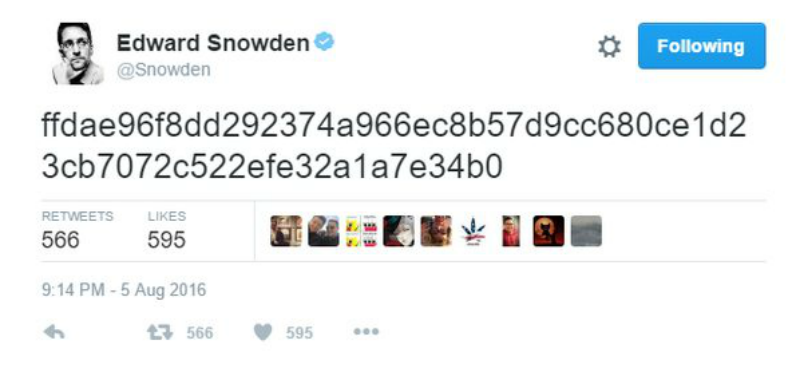
The timing shortly after the "It's Time" tweet also have caused concern for some
Reddit theorists
such as a user named stordoff who believes that the nascent
Twitter post "was intended to set something in motion." The user postulates that it
is an encrypted message, a signal, or a password.
Snowden's initial data release in 2013 exposed what many had feared about the NSA
for years, that the agency had gone rogue and undertaken a massive scheme of domestic
surveillance. However, it is also known that the information released was only part
of the document cache he had acquired from government servers.
 © REUTERS/ Svein Ove Ekornesvaag/NTB Scanpix
'It's Time': Whistleblower Edward Snowden Tweets Mysterious Warning
© REUTERS/ Svein Ove Ekornesvaag/NTB Scanpix
'It's Time': Whistleblower Edward Snowden Tweets Mysterious Warning
It has been reported that additional government data was distributed in encrypted
files to trusted journalists who were told to not release the information unless they
received a signal urging them to – information that the whistleblower determined was
too sensitive for release at the time.
The possibility also exists that Snowden has decided that after three years
in hiding that additional information needed to be released to the public independent
of some physical harm to himself, but the whistleblower's fans and privacy advocates
across the world will continue to sit on the edge of their seats in worry until and
unless he tweets to confirm that he is safe.
A very important, informative interview. Outlines complexity of challenges of modern society and
the real power of "alphabet agencies" in the modern societies (not only in the USA) pretty
vividly. You need to listen to it several times to understand better the current environment.
Very sloppy security was the immanent feature both of Hillary "bathroom" server and DNC emails hacks.
So there probably were multiple parties that has access to those data not a single one (anti Russian
hysteria presumes that the only party are Russian and that's silly; what about China, Iran and
Israel?).
Russian government would not use a "known attack" as they would immediately be traced back.
Anything, any communications that goes over the network are totally. 100% exposed to NSA data
collection infrastructure. Clinton email messages are not exception. NSA does have
information on them, including all envelopes (the body of the message might be encrypted and that's
slightly complicate the matter, but there is no signs that Clinton of DNC used encryption of them)
NSA has the technical capabilities to trace the data back and they most probably have most if not
all of deleted mail. The "total surveillance", the total data mailing used by NSA definitely includes
the mail envelopes which makes possible to enumerate all the missing mails.
Notable quotes:
"... The National Security Agency (NSA) has "all" of Hillary Clinton's deleted emails and the FBI could gain access to them if they so desired, William Binney, a former highly placed NSA official, declared in a radio interview broadcast on Sunday. ..."
"... Binney referenced testimony before the Senate Judiciary Committee in March 2011 by then-FBI Director Robert S. Mueller in which Meuller spoke of the FBI's ability to access various secretive databases "to track down known and suspected terrorists." ..."
"... "Now what he (Mueller) is talking about is going into the NSA database, which is shown of course in the (Edward) Snowden material released, which shows a direct access into the NSA database by the FBI and the CIA Which there is no oversight of by the way. So that means that NSA and a number of agencies in the U.S. government also have those emails." ..."
"... Listen to the full interview here: ... ..."
"... And the other point is that Hillary, according to an article published by the Observer ..."
The National Security Agency (NSA) has "all" of Hillary Clinton's deleted emails and the FBI
could gain access to them if they so desired, William Binney, a former highly placed NSA official,
declared in a radio interview broadcast on Sunday.
Speaking as an analyst, Binney raised the possibility that the hack of the Democratic National
Committee's server was done not by Russia but by a disgruntled U.S. intelligence worker concerned
about Clinton's compromise of national security secrets via her personal email use.
Binney was an architect of the NSA's surveillance program. He became a famed whistleblower when
he resigned on October 31, 2001, after spending more than 30 years with the agency.
He was speaking on this reporter's Sunday radio program, "Aaron
Klein Investigative Radio," broadcast on New York's AM 970 The Answer and Philadelphia's NewsTalk
990 AM.
Binney referenced
testimony before the Senate Judiciary Committee in March 2011 by then-FBI Director Robert S.
Mueller in which Meuller spoke of the FBI's ability to access various secretive databases "to track
down known and suspected terrorists."
Stated Binney:
"Now what he (Mueller) is talking about is going into the NSA database, which is shown
of course in the (Edward) Snowden material released, which shows a direct access into the NSA
database by the FBI and the CIA Which there is no oversight of by the way. So that means that
NSA and a number of agencies in the U.S. government also have those emails."
"So if the FBI really wanted them they can go into that database and get them right now," he stated
of Clinton's emails as well as DNC emails.
Asked point blank if he believed the NSA has copies of "all" of Clinton's emails, including the
deleted correspondence, Binney replied in the affirmative.
"Yes," he responded. "That would be my point. They have them all and the FBI can get them right
there."
Listen to the full interview here: ...
Binney surmised that the hack of the DNC could have been coordinated by someone inside the U.S.
intelligence community angry over Clinton's compromise of national security data with her email use.
And the other point is that Hillary, according to an
article published
by the Observer in March of this year, has a problem with NSA because she compromised Gamma
material. Now that is the most sensitive material at NSA. And so there were a number of NSA
officials complaining to the press or to the people who wrote the article that she did that. She
lifted the material that was in her emails directly out of Gamma reporting. That is a direct compromise
of the most sensitive material at the NSA. So she's got a real problem there. So there are many
people who have problems with what she has done in the past. So I don't necessarily look at the Russians
as the only one(s) who got into those emails.
The Observer defined the GAMMA classification:
GAMMA compartment, which is an NSA handling caveat that is applied to extraordinarily sensitive
information (for instance, decrypted conversations between top foreign leadership, as this was).
Aaron Klein is Breitbart's Jerusalem bureau chief and senior investigative reporter. He
is a New York Times bestselling author and hosts the popular weekend talk radio program, "Aaron
Klein Investigative Radio." Follow him on
Twitter @AaronKleinShow. Follow
him on Facebook.
May 18, 2016
PCWorld
You're probably giving away more than you think
The location stamps on just a handful of Twitter posts can help even low-tech stalkers find you,
researchers found.
The notion of online privacy has been greatly diminished in recent years, and just this week two
new studies confirm what to many minds is already a dismal picture.
First, a study
reported on Monday by Stanford University found that smartphone metadata-information about calls
and text messages, such as time and length-can reveal a surprising amount of personal detail.
To investigate their topic, the researchers built an Android app and used it to retrieve the metadata
about previous calls and text messages-the numbers, times, and lengths of communications-from more
than 800 volunteers' smartphone logs. In total, participants provided records of more than 250,000
calls and 1.2 million texts.
The researchers then used a combination of automated and manual processes to understand just what's
being revealed. What they found was that it's possible to infer a lot more than you might think.
A person who places multiple calls to a cardiologist, a local drug store, and a cardiac arrhythmia
monitoring device hotline likely suffers from cardiac arrhythmia, for example. Based on frequent
calls to a local firearms dealer that prominently advertises AR semiautomatic rifles and to the customer
support hotline of a major manufacturer that produces them, it's logical to conclude that another
likely owns such a weapon.
The researchers set out to fill what they consider knowledge gaps within the National Security
Agency's current phone metadata program. Currently, U.S. law gives more privacy protections to call
content and makes it easier for government agencies to obtain metadata, in part because policymakers
assume that it shouldn't be possible to infer specific sensitive details about people based on metadata
alone.
This study, reported in the Proceedings
of the National Academy of Sciences, suggests otherwise. Preliminary versions of the work have already
played a role in federal surveillance policy debates and have been cited in litigation filings and
letters to legislators in both the U.S. and abroad.
It takes as few as eight tweets to locate someone
Researchers at MIT and Oxford University, meanwhile, have
shown that the
location stamps on just a handful of Twitter posts can be enough to let even a low-tech snooper find
out where you live and work.
Though Twitter's location-reporting service is off by default, many Twitter users choose
to activate it. Now, it looks like even as few as eight tweets over the course of a single
day can give stalkers what they need to track you down.
The researchers used real tweets from Twitter users in the Boston area; users consented to the
use of their data and also confirmed their home and work addresses, their commuting routes, and the
locations of various leisure destinations from which they had tweeted.
The time and location data associated with the tweets were then presented to a group of 45 study
participants, who were asked to try to deduce whether the tweets had originated at the Twitter users'
homes, workplaces, leisure destinations or commute locations.
Bottom line: They had little trouble figuring it out. Equipped with map-based representations,
participants correctly identified Twitter users' homes roughly 65 percent of the time and their workplaces
at closer to 70 percent.
Part of a more general project at MIT's Internet Policy Research Initiative, the
paper was presented last
week at the Association for Computing Machinery's Conference on Human Factors in Computing Systems.
"Many people have this idea that only machine-learning techniques can discover interesting patterns
in location data, and they feel secure that not everyone has the technical knowledge to do that,"
said Ilaria Liccardi, a research scientist at MIT's Internet Policy Research Initiative and first
author on the paper. "What we wanted to show is that when you send location data as a secondary piece
of information, it is extremely simple for people with very little technical knowledge to find out
where you work or live."
Twitter said it does not comment on third-party research, but directed users to
online information about its optional location
feature.
Notable quotes:
"... But the panic is also a clear indication, and perhaps as important, another message, not just to Clinton but to Team Dem, that the Administration can't, or won't but is making it seem like can't, do what it takes to save Hillary's bacon. ..."
"... The fact that there is an independent effort, completely outside the Administration's control, pursuing the server mess, also makes it riskier for the DoJ to do nothing if Judicial Watch exposes damning documents. ..."
"... The Democrats don't have any dirt on Trump the Republicans didn't have. Trump is a referendum on the establishment. The establishment can't attack him, and any attacks too similar to the very publicized establishment attacks will be dismissed. ..."
"... Maybe not Mittens and Bill Kristol at this point, the GOP elites will show loyalty because anything less will risk their own position. The base will remove GOP elites over certain sins. The Teabaggers cleaned the GOP caucus of TARP voters. ..."
"... "Trump is a referendum on the establishment." ..."
"... That's the best one-sentence explanation for his success that I've seen. ..."
"... That is certainly the narrative Trump wants. What I find the height of black, despairing comedy is that anyone believes it. In addition to being completely untrustworthy and self-centered, Trump has little to gain by overthrowing the status quo, and has given many signs that he will continue business as usual, only with a slightly different crew of low-rent elites in charge at the top. ..."
"... No matter what he says, Trump is not leading some sort of revolution to abolish the Empire and replace it with something else, much less something better. He just wants a shortcut to being Emperor. ..."
"... I'm under the impression that if not for the Benghazi investigation, the home server would not have been discovered. However, maybe someone else can confirm that I'm correct. Which, if you think about it, does not actually make sense. The NSA should have known all along. Why on earth she supposed that she could get around the NSA is simply… words fail me. ..."
"... My tin foil hat has always told me Clintonistas may not have worked overly hard for Kerry in 2004, even offering bad advice. Every Winner and Loser column from after the election listed on clear winner, the front runner for the 2008 Democratic nomination, Hillary Clinton. Clinton Inc was operating out of crummy digs in Harlem because they couldn't raise money, but the money poured in after the Kerry loss. ..."
"... My only fear re: how Clinton could win in November would be if she and Bill had the juice to help throw 2000 and 2004 to keep the path clear for her. Unless she can steal in the General, she isn't going to be President. That would also explain Obama's focus on caucuses in 2008 - he went after her soft, less stealable underbelly. (I realize there are also less CT explanations for this.) ..."
"... "Maintaining a homebrew server could be written off as a policy violation, rather than a criminal matter. " ..."
"... Given the last 15 years of brutal, if selective, prosecutions for mishandling materials less sensitive than some of the material on Clinton's servers, I don't think many people will buy that. ..."
"... The elephant in the room is not the private server per se, but the use of it to circumvent any exposure to FOIA requests. The pay-for-play activities of the Secretary with regard to the Foundation can certainly be inferred, and if proven are grounds for an indictment leading to prosecution for treason, and the incarceration (if not the death penalty) for the entire Clinton family. The tons of circumstantial evidence regarding the timing of payments and the goodies granted, would be sufficient for a Grand Jury indictment; the "smell' test is overwhelming. ..."
"... People seem to forget that Clinton served on the Committee on Armed Services from 2003 to 2009 and on the Subcommittee on Emerging Threats and Capabilities … you know, the Subcommittee that has jurisdiction over Department of Defense policies and programs to counter emerging threats, information warfare and special operations programs. ..."
"... I too would want to keep my PRIVATE and PERSONAL emails and other communications private … if she'd been above board and simply had a private email for non-official communications and kept the official State Dept stuff on the official account, there would be nothing here. ..."
"... Sanders will lose his clout and things go back to normal. ..."
"... private server ..."
"... a personal email account was allowed ..."
"... It seems that Mills claimed that HRC's use of the private email was not kept secret and lots of Admin officials knew about it. (Note that people had to make a special request to be able to use her email.) But Obama claimed he only learned of it "like the rest of you, in the news reports". So Obama and Hillary never emailed each other while she was SoS? ..."
"... They never were chummy esp. after all the heat of the campaign: "You're likeable enough, Hillary". ..."
"... It was reported last January that there were eighteen emails between Clinton and Obama that State was not going to release for security reasons. So yes, they did email each other. It would be interesting to know what security instructions Obama received regarding using his email. Did anyone ever caution him to check the sender's email address as a caution against phishing? Her email address was clintonemail dot com. Even a technical neophyte has to know that means either she or some other entity was hosting the site; and, if a separate entity, did that entity have security clearance for handling those emails? Obama knew darn well that she was using an unsecure system. He is equally guilty of enabling her risk-taking. ..."
"... Now that Elizabeth Warren is being a good girl and playing footsie with Schumer, I can see them thinking putting her in as VP would work well enough. I don't think so (in my neck of the progressive woods, there seems to be a general understanding that she sold out), but more importantly, I can't imagine Hillary stepping away only to see Liz moved in. ..."
"... Their smartest real play would be to let Bernie have the nom and bide their time, hoping they can work in the background with Republicans to taint and undermine him. But I suspect that they're exactly smart enough to know that probably wouldn't work. ..."
"... my rich friends (lifetime republicans included) will vote for hillary, my poor friends won't. ..."
"... Clinton voters are the small amount type. She has only "won," even in the states she did did "win," by massively suppressing the vote. She hasn't even held onto her own voters from 2008, even in conservative states. Her "big wins" in the South were with much smaller numbers of votes cast. There are people who genuinely want to vote for her. They were not enough to win the Democratic primary without massive suppression AND theft. ..."
"... The problem for Hillary is there is no indication the email scandal narrative will ever improve to the point of improving her untrustworthy numbers. The best she can hope for is the FBI stating it will not recommend an indictment which will merely confirm the public's correct perception that the power elite are treated better than the rank and file. Hillary cannot unring the Inspector General's conclusion she circumvented FOIA and federal record keeping laws. She cannot undue the fact she maintained thousands of classified records, along with 22 top secret documents on the private server. She cannot change the fact she hid her use of the private server from the public and only disclosed it when caught by the Senate Committee investigating Benghazi. Everyone who pays attention to the facts is disgusted by her misconduct in this matter. ..."
"... I think her problem is that, in routing official traffic through a private mail server, she's tried to avoid records of her work (as a public official!) ever becoming available to the public. It looks, at the very least, like she's trying to hide something and it's a demonstration of breathtaking contempt for the very people whose votes she's now asking for. ..."
"... If he shagged under the legal age limit girls, traveled on a jet which was used in slave trade of underage girls, etc; then it isn't just his business, it's a criminal matter. If Mrs. Clinton enabled, and/or aided and abetted, then she could be facing criminal charges. ..."
"... The interesting thing is Jeffery Epstein has hidden cameras on both his plane and all over the US Virgin Island private pedophile reserve he ran for politicians and high level government officials. The overseas press is reporting he blackmailed his way out of Federal Charges. Was Bill part of that blackmail? ..."
"... Bill is a sexual predator. His affair with Jennifer Flower was consensual. But starting from when he was Governor, there is a long list of credible allegations of him engaging in sexual harassment (extremely aggressive come-ons with women he had just met, often women who were state employees or Dem consultatnts), including a rape allegation by Juanita Brodderick. We've even had a reader in comments say that when Bill Clinton visited a friend, he asked their college aged daughter when he was alone with her if she wanted to ride in his car and give him a blow job. DC contacts confirm the city is rife with stories like that. ..."
"... If there were an equal ..."
"... As strange a thing as this is to say, I find myself wishing that more journalists had experience in IT security. I do have such experience, and from what I can see most people really don't appreciate just how totally, ludicrously irresponsible it is for that server to exist. Talk of it having been "secured" by some lone IT contractor is ridiculous on its face. I wouldn't run a homebrew email server, and I am basically not worth hacking – very much unlike the US Secretary of State. ..."
"... Seriously, think about it. The Secretary of State had a private email server which seems to have been widely known about within the State Department and other people in government who had dealings with Hillary Clinton. There's really no question as to if that thing was hacked – you can absolutely bet your ass ..."
"... That's what's really galling to me – even by Hillary's own stated standards, what she did with her email is orders of magnitude worse than what Snowden did. But it's Hillary Clinton, so it gets handwaved by the Democrats' long practice at assuming a Clinton scandal is overblown nonsense. ..."
"... That's why people like Chelsea Manning, Edward Snowden, Thomas Drake, Jeffrey Sterling, John Kiriakou, Joe Wilson, and so forth are persecuted by the government while people like Clinton (and Petraeus, Novack, Libby, Bush, Cheney, Obama, Biden, etc.) are protected. It has nothing whatsoever to do with the merits of events. Just as one example, here's the 'ole Gray Lady serving as dutiful stenographer for Nancy Pelosi herself, the Democratic Speaker from San Francisco, supposedly one of the most liberal parts of the entire country, explaining that the law doesn't apply to people in power. ..."
"... I've worked in IT and software development for years and agree that her provision of that server doesn't meet the most basic requirements for security. Also, I work for a rather large company with a sizable federal contract and, if you haven't contracted with the government, you can only imagine the levels of security they impose upon their vendors. Two-factor authentication, encryption at rest, kernel hardening and on and on. Not only do you HAVE to do these things if you want to do business with the government, they bring in teams of their IT people to audit you. And it is not perfunctory in any way. They take InfoSec very, very seriously. ..."
"... Yesterday in the WSJ was this op-ed which made many of the same points that were made here, as well as discusses the fallout if Clinton loses the California primary. I also think that the Dems are not only just worried about the nomination now. The IG's report clears a path for hearings by the Republicans against Clinton after the election. ..."
"... I agree. Sanders has nothing to gain and a lot to lose by "making nice" with the Dem establishment. Why make nice with them? They are the problem, not the solution. That's a mainstay of Sanders' campaign. ..."
"... The Clinton fanaticism isn't about Sanders. They believe they need Clinton. An active DoJ might be a threat. A few have backwards ideas about politics. Some simply did the believe Sanders when he said Hillary was weak, but with a Gabbard in play, many Democrats can kiss their ambitions good bye if Sanders wins. ..."
"... I've said it elsewhere: Sanders is unacceptable to the DNC because a Sanders win would render the DNC networks, influence and fundraising abilities irrelevant overnight. The DNC would no longer be gatekeepers. You can win without them. Thus, Team D does not fear a Sanders defeat, and they can live with President Trump. In fact, that would represent an unprecedented fundraising opportunity. But from the Team D perspective, a Sanders victory must be prevented at all costs. ..."
"... How the hell could Sanders "make friends" with members of the Democratic Party elite? He is blowing up their revolving-door-greasing funding model. Running as effectively as he has with almost no lobbyist money? No major corporate donors to speak of? What can he offer them, except unpleasant changes that negatively impact their careers? ..."
"... "The implications of all of this are that Hillary Clinton did not want her emails subjected to the Freedom of Information Act or subpoenas from Congress. And that's why she set up a home-brew server" ..."
"... But this is definitely putting a lot of spin on the ball, because the other half of the story is the reason WHY she wanted to avoid FOIA and Congressional scrutiny. The answer is: so that between her and Bill she could sell her office to the highest bidders, which the FBI is quite prepared to prove, or if denied that chance, to "leak like crazy" ..."
"... Caution: this course of action carries a high risk of nominating Bernie ..."
"... And that bring up another point for all you "feminist" Clintonistas. Wasn't the whole point of the "first woman in the White House" thing to show that women can do it alone? That they don't need men carrying them around all the time to be successful? Well what's up with your candidate? I have never (in my 65 years) ever seen anyone (woman or man) need more help from other people (mostly men) to gain the success they seek. At every single turn in this campaign we have Ms. Clinton needing someone else, someone MORE, falling on their sword for her. Because left on her own, against a freaking socialist, for Christ's sakes, all she has been able to do is F@ck up. A FIFTY POINT LEAD, gone. Wasted. Nothing to show. And this is what you want as feminism's representative in the White House? Shame on you. ..."
"... Most of the DLC establishment could find it easy enough to "live" with a Trump Presidency. Just like Lil Marco Rubio, they'll easily bend their knees to kiss Trump's heiney and make deals with him. What's it to them, after all? ..."
"... In that scenario Hillary wins the nomination and loses the election, Obama pardons her to head off (in his telling) partisan persecution and looks noble (to the credulous) standing up for her, clearing the way to elbow in on the Clinton network for the-haven't you heard?-Obama Foundation. And the grift goes on. ..."
"... stopped ..."
"... Because the email thing, and the speeches thing, and the neo-liberalism thing, whatever. Bernstein's "leaking" makes clear that as far back as February Obama's guys in the trenches said – hey, we just saw the Bear funds blow up, and this thing is going to end badly one way or the other. We don't know exactly how bad, but bad. Which is bad for us… ..."
"... Yves – Time hss proved you wise. Japanafication is exactly what has been unfolding. And according to Forbes and the Fed, 48% of the population having less than a grand in savings means the US is near third world. One can buy Pop Tarts in third world countries also. ..."
"... The real danger is geopolitics. And this bitch that thinks she is queen has no issues literally seeing 1/3 of the global population dying to escape her crimes. Think of what a rapist does to a rape victim many times. Strangle that woman so she doesnt indict you. Yeah, it is that bad. But there are some form of tech that will end any world war quickly. Stuff of science fiction. America's competitors should think twice, or such may dissapear. Literally. ..."
"... However – and this must have been Clinton's worst nightmare x 10 - unbeknownest to CESC and Platte River, the backup server accidentally synced with another off-site server belonging to Datto for two years before anyone realized it. ..."
"... wasn't ..."
"... to the cloud was taking place ..."
"... So one Democratically connected organization signed onto this separate justice system for the politically connected. Possibly the concern Obama has for his unfunded $1Billion Presidential Library will force him to burnish his legacy by NOT rescuing HRC with some dubious legal maneuver. It is somewhat ironic that Nixon was brought down by a private electronic system (his tape recording system) while Clinton may be brought down by her own private electronic email system. ..."
"... Regardless my experience with talking to Hillary supporters is that no amount of scandal of outright criminal lawbreaking affects their views about Hillary. They revert to "she's been scrutinized and tested for decades by her enemies and she's survived." They are people on the margins who will be affected. How many are the Dem establishment? It's going to take a whopper to get them to tank Hillary IMO. ..."
"... There is a detail that is being universally missed both in the MSM and alternative press: it is a virtual certainty that the NSA has a copy of every email sent or received by that server. ..."
"... Don't forget the mayhem when the FSB (who else) posted Nuland's little chat with Pyatt over an insecure line. Let no one forget that HRC is strongly connected to the neocon project to undermine Russia's return to strength. ..."
"... Just ask yourself: What would Vladimir Putin do? ..."
"... $1 Billion Library ..."
"... I too think bernie will pull it out, the other choices are terrible. I'm looking for aspirational latinos to flock to bernie in california and it'll be a rout that can't be ignored. I hope that's what happens. ..."
"... Clintonsomething – "The Campaign Years" ..."
"... I'm not sure the media's current focus on Hillary's email server is warranted. There are definitely indications that she violated email policies, but there don't seem to be specifics about what these actions were trying to hide. I think her very questionable family ties to corporate money are a more meaningful topic in determining her suitability for the U.S. presidency ..."
"... The Clinton Machine (in other words the political operation of the Bill and Hillary, and potentially Chelsea) has always operated on the basis the money and connections will fix everything. It has, after all, gotten them this far. However, as a core operational mode, it also accumulates cynicism and tends to value loyalty over performance, leading to degradation over time. ..."
"... Seems to me that except in a relatively few corners and local settings, and now very frankly via our mostly collective embrace of the Neo geist, "America" has always and only been about "screwing the other guy." ..."
"... I don't believe "foaming one more runway" (read: having your DOJ, FBI appear helpless) wouldn't bother this administration. A Loyalist are those unengaged (or too engaged) whom choose willingly to believe the disastrous economic and political experiment, that attempted to organize human behavior around the dictates of the global marketplace, has been a splendid success…or worse, blindly, my tribal leader is in accordance with all that is good. ..."
"... Haiti. Look at film of the Clintons in Haiti to see how they work. & Haiti is one place where also the elites own the deeds. Haiti Is America, only sooner. ..."
"... For what it's worth, Jonathan Turley suggests Hillary still has friends in high places in his discussion of former Clinton IT advisor, Bryan Pagliano, who is taking the fifth amendment in deposition on email scandal, ..."
"... Those e-mails don't alarm me anywhere near as much as the $200,000 plus speaking fees from Wall St. NO speech by anyone is worth anywhere near such an amount. These were clearly bribes, there's simply no other way of looking at it. I have no interest in seeing the transcripts of those speeches because the money counts far more than the content, and speaks for itself. No way would I vote for someone so clearly in the pocket of the oligarchy. ..."
But the panic is also a clear indication, and perhaps as important, another message, not just
to Clinton but to Team Dem, that the Administration can't, or won't but is making it seem like can't,
do what it takes to save Hillary's bacon.
And I suspect it really is "can't". The FBI has enough autonomy that if they find real dirt on
the Clintons, they will leak like crazy if the DoJ does not pursue the case in a serious way. That
would make the Administration complicit, and Obama does not want his final months in office tainted
by his Administration touching the Clinton tar baby any more than it has to. In addition, the Judicial
Watch cases are proceeding, and the judge, having had the Clinton side deal with him repeatedly in
bad faith, is not going to cut it any slack. The fact that there is an independent effort, completely
outside the Administration's control, pursuing the server mess, also makes it riskier for the DoJ
to do nothing if Judicial Watch exposes damning documents.
By Gaius Publius
, a professional writer living on the West Coast of the United States and frequent contributor
to DownWithTyranny, digby, Truthout, and Naked Capitalism. Follow him on Twitter
@Gaius_Publius ,
Tumblr and
Facebook . Originally published
at
at Down With Tyranny . GP article here.
The last time I featured former Watergate reporter Carl Bernstein on these pages, it was to showcase
his
delivery of messages he received from the White House , to the effect that the "White House"
thought Clinton was blowing it with her Wall Street speeches stance, and because of that, the "White
House" was freaking out (to put it colloquially) - at least as Bernstein tells it.
Here's part of what Bernstein - a Clinton supporter - said last February (my transcript and emphasis;
video at the link):
Bernstein: There is a huge story going on. I've spent part of this weekend talking
to people in the White House. They are horrified at how Hillary Clinton is blowing up her own
campaign .
And they're worried that the Democrats could blow - they are horrified that the whole business
of the transcripts, accepting the money - that she could blow the Democrats' chance for White
House. They want her to win. Obama wants her to win.
But Sanders has shown how vulnerable she is. These ethical lapses have tied the White House
up in knots. They don't know what to do. They're beside themselves. And now, you've got a situation
with these transcripts a little like Richard Nixon and his tapes that he stonewalled on and didn't
release.
... ... ...
In that context , listen to the current "White House" message about the Clinton campaign
via Bernstein and video at the top (my
italics):
Bernstein: The implications of all of this [the email server issue] are that Hillary
Clinton did not want her emails subjected to the Freedom of Information Act or subpoenas from
Congress. And that's why she set up a home-brew server.
I think we all know that. People around her will tell you that in private if you really get
them behind a closed door.
I was in Washington this week, I spoke to a number of top Democratic officials and they're
terrified, including people at the White House, that her campaign is in free fall because of this
distrust factor. Indeed, Trump has a similar problem, but she's the one whose numbers are going
south.
And the great hope in the White House, as well as the Democratic leadership and people who
support her, is that she can just get to this convention, get the nomination - which they're
no longer 100% sure of - and get President Obama out there to help her, he's got a lot of
credibility, it's an election that's partly about his legacy .
But she needs all the help she can get because right now her campaign is in huge trouble…
... ... ...
Two takeaways - one is that top Democrats know how precarious Clinton's position is . They're
not fooled any more than you are. That's worth noticing. And second, the White House and Bernstein
are not blaming Sanders . Whoever crafted this message for us is blaming the Clinton campaign
only, and by extension, Clinton herself.
fajensen ,
June 1, 2016 at 8:35 am
Hmm. Does make one wonder.
If "they" are so worried about Hillary flubbing her "inevitable" nomination as presidential candidate,
and "they" are apparently not so worried about Hillary loosing to Trump in the run for president
later, one does wonder about the possibility of "they" having some good quality dirt on Trump
(or a backdoor to the voting machines).
Really Good Quality Dirt!
It is a *big* issue to mishandle classified information – normal people will be prosecuted
and may go to jail even by coincidence; like a selfie in front of equipment they didn't know was
classified and which was not labelled as such. Then on top of that comes the sleaze-factor with
avoiding the FOIA requirements, destruction of evidence (which means that certainly Hillary was
up to *something* crooked, because why else bother with all the work? it's very *easy* to hand
over a verified duplicate of a hard disk compared to everything Hillary tried to not do this!)
and of course the blatant incompetence + arrogance shown by Hillary by running a private business,
a crooked one at that, from work?!
A street level dope dealer can manage to compartmentalize their real business from the one
they report to the IRS. But not Hillary.
NotTimothyGeithner ,
June 1, 2016 at 10:47 am
The Democrats don't have any dirt on Trump the Republicans didn't have. Trump is a referendum
on the establishment. The establishment can't attack him, and any attacks too similar to the very
publicized establishment attacks will be dismissed.
The simple problem is Republican voters selected him over the GOP establishment. All the Republicans
will line up because Trump is now their rightful leader. Maybe not Mittens and Bill Kristol
at this point, the GOP elites will show loyalty because anything less will risk their own position.
The base will remove GOP elites over certain sins. The Teabaggers cleaned the GOP caucus of TARP
voters.
The secret weapon is to be a generic tax and spend Democrat, uninterested in colonialism.
marcus ,
June 2, 2016 at 10:43 am
Yes, the intelligence establishment has dirt the two leading candidates (Trump and Clinton).
This can be used in what ever way is expedient, but most of all to maintain the status quo. Like
the mafia, you have committed a crime so you have to promote our crimes or you will be exposed/deposed.
Which is why the race to the bottom of the hogs wallow is being actively promoted. Likely, no
dirt on Sanders, which is why the MSM and even some parts of social media are enlisted to create
the appearance of dirt because blackmail/graymail of Sanders will be difficult or impossible.
Crespo ,
June 1, 2016 at 11:49 am
"Trump is a referendum on the establishment."
That's the best one-sentence explanation for his success that I've seen.
Jason ,
June 1, 2016 at 12:51 pm
That is certainly the narrative Trump wants. What I find the height of black, despairing
comedy is that anyone believes it. In addition to being completely untrustworthy and self-centered,
Trump has little to gain by overthrowing the status quo, and has given many signs that he will
continue business as usual, only with a slightly different crew of low-rent elites in charge at
the top.
No matter what he says, Trump is not leading some sort of revolution to
abolish the Empire and replace it with something else, much less something better. He just wants
a shortcut to being Emperor.
That he may end up being so bad at the job the entire edifice burns down is not, IMHO, any
sort of positive. I don't like where we are or where we are headed, but neither do I want my family
trying to survive in some sort of post-apocalyptic wasteland.
I'll repeat the tin-foil hat level thought that keeps crossing my mind with Trump: his job
is to discredit any sort of opposition to the establishment from the right for a generation
or more.
Detroit Dan ,
June 1, 2016 at 2:18 pm
I think you're underestimating Trump. As you note, he does want to maintain current establishment,
and he could be successful at this for awhile (e.g. ramping up spending and not worrying about
deficits).
The establishment (Clinton types not aggressively calling out Republicans and proposing credible
alternatives) has brought us to this point.
Martin Finnucane ,
June 1, 2016 at 11:35 am
Then on top of that comes the sleaze-factor with avoiding the FOIA requirements …
That's it, right there. She purposefully conducted the business of the State in such a manner
to avoid scrutiny by the citizenry. That is a breach of the public trust that cannot be countenanced,
cannot go unpunished. She's gotta go, and if "everybody's doing it," then they all gotta go too.
readerOfTeaLeaves ,
June 1, 2016 at 11:29 am
I'm under the impression that if not for the Benghazi investigation, the home server would
not have been discovered. However, maybe someone else can confirm that I'm correct. Which, if
you think about it, does not actually make sense. The NSA should have known all along. Why on
earth she supposed that she could get around the NSA is simply… words fail me.
Morning Joe is saying that Trump is polling as 'more trustworthy' than Clinton.
If the White House isn't in a panic at this point, they're somnambulant.
NotTimothyGeithner ,
June 1, 2016 at 11:45 am
The Washington elite still labor under the delusion the sycophants are the general population
and everything will return to normal any time now.
Antifa ,
June 1, 2016 at 12:03 pm
I thought it was strictly due to Benghazi-related FOIA requests from Congress that brought
her server to light, but
this article indicates it was discovered as a matter of routine housekeeping when John Kerry
became SoS, and they finally filled the position of Inspector General at State.
Something Clinton didn't get around to doing . . .
NotTimothyGeithner ,
June 1, 2016 at 12:58 pm
My tin foil hat has always told me Clintonistas may not have worked overly hard for Kerry
in 2004, even offering bad advice. Every Winner and Loser column from after the election listed
on clear winner, the front runner for the 2008 Democratic nomination, Hillary Clinton. Clinton
Inc was operating out of crummy digs in Harlem because they couldn't raise money, but the money
poured in after the Kerry loss.
If this election was about whether the country wanted a fourth term of the Kerry Edwards Cantwell?
(She makes the most sense for a Vice President to Edwards 2012 running mate) teams, where would
Clinton Inc be?
aab ,
June 1, 2016 at 6:49 pm
My only fear re: how Clinton could win in November would be if she and Bill had the juice
to help throw 2000 and 2004 to keep the path clear for her. Unless she can steal in the General,
she isn't going to be President. That would also explain Obama's focus on caucuses in 2008 - he
went after her soft, less stealable underbelly. (I realize there are also less CT explanations
for this.)
But watching the primary play out suggests to me that there are limits to election theft capability.
I don't think there's anyway she wanted to drag this out this long. The theft in Kentucky was
pretty obvious and clumsy, too. That plus the Republican Party doing its thing rallying around
its nominee gives me hope that at least we won't get President Clinton.
It feels a bit like clinging to a ice floe in the North Atlantic, though.
Ray Phenicie ,
June 1, 2016 at 7:02 pm
But there's another point here too which is out in the open and yet no one is talking about
it much except to note that her emails were not part of the National Archives. She had a private
server for that very Orwellian reason-she planned to control the historical record by having a
whole parcel of it hidden and not available until she decided to release it, if ever. I see the
reference to Orwell as particularly apt . Remember in 1984 our besotted hero, (depressed
with the horror of what he was doing), spent the livelong day erasing or changing the archival
records related to key events that Big Brother needed changing. His needs, like Hilary's, kept
changing from day to day so the censorship was endless.
Clinton has always been in charge of a Ministry of Truth-yesterday she stood for practice 'A'
but now today opposes practice 'A'. The private server is just another facet of MiniTrue.
HotFlash ,
June 2, 2016 at 8:32 am
The domain name was clintonemail.com, so the email addresses would be
[email protected] etc. etc. Anyone receiving
these emails *could* see that if they looked, but if the sender is in your address book it may
just come in as that person's name or nickname as you have it in own your machine.
While it may be that most recipients wouldn't bother to drill down to the actual originating
address, there are offices and agencies that would definitely be tuned to this sort of thing.
For instance, State's in-house IT security people seem to have twigged, not that it helped.
What I wonder is, aren't there 16 some-odd agencies who scan and analyze email traffic? In
this case, the metadata alone would have told much (as it so often does).
tinheart ,
June 1, 2016 at 5:00 pm
Illuminating. She was jealous of Obama who only had one Blackberry.
http://www.cnet.com/uk/news/hillary-clinton-blackberry-security-envy-nsa-no-go/
pretzelattack ,
June 1, 2016 at 6:39 am
suddenly, i'm feeling optimistic again. obama might be many things, but he is a very good politician,
and he protects his legacy like an enraged bear protects cubs. throwing clinton under the bus
to do that? no problem, if doing so results in less damage to his image, and i trust him to be
able to judge that well.
Bullwinkle ,
June 1, 2016 at 10:28 am
He's not a very good politician. Too much of a phoney.
nowhere ,
June 1, 2016 at 11:16 am
Politician, not Statesmen.
Steve ,
June 1, 2016 at 11:53 am
"Too much of a phoney" sounds to me like the kernel of the prototypical modern politician.
aab ,
June 1, 2016 at 6:53 pm
I don't think he gives even one f**k about his image or legacy. He cares about being wealthy
and having high status. He's only cutting Clinton loose if his owners that previously told him
he had to help her now tell him to toss her over.
voteforno6 ,
June 1, 2016 at 6:40 am
I still have my doubts that any indictments are forthcoming. Maintaining a homebrew server
could be written off as a policy violation, rather than a criminal matter. The punishments for
that are administrative (loss of job, loss of security clearance), which don't really touch her.
Having classified information in those emails, unless it's really egregious, probably won't result
in any criminal charges, either. I wouldn't be surprised if that is rather common among senior
government officials. If they go after Clinton for that, a lot of other people could be put under
greater scrutiny. My guess is that there is institutional pressure in the government to not charge
one of their own for that.
If any charges are filed, it will probably be for something else that they've stumbled upon,
possibly related to the Clinton Foundation. That's why I find it interesting that the news about
Terry McAuliffe broke when it did. If they are pursuing something, there will be pressure to resolve
it before the election. At the same time, they won't want to rush it, because they're only going
to get one shot at this – you don't want to take a swing at the Clintons, and miss.
allan ,
June 1, 2016 at 6:55 am
"Maintaining a homebrew server could be written off as a policy violation, rather than a criminal
matter. "
Given the last 15 years of brutal, if selective, prosecutions for mishandling materials less
sensitive than some of the material on Clinton's servers, I don't think many people will buy that.
voteforno6 ,
June 1, 2016 at 7:46 am
They may not buy it, but that feeds directly into my other point – senior government officials
are rarely held accountable for those types of actions, unless they're really egregious. People
much lower on the food chain are held to a higher standard. Because of that, I think that there
will be resistance to prosecution from other senior officials, simply because they don't want
to be put in jeopardy as well.
apber ,
June 1, 2016 at 8:38 am
The elephant in the room is not the private server per se, but the use of it to circumvent
any exposure to FOIA requests. The pay-for-play activities of the Secretary with regard to the
Foundation can certainly be inferred, and if proven are grounds for an indictment leading to prosecution
for treason, and the incarceration (if not the death penalty) for the entire Clinton family. The
tons of circumstantial evidence regarding the timing of payments and the goodies granted, would
be sufficient for a Grand Jury indictment; the "smell' test is overwhelming.
Norb ,
June 1, 2016 at 8:52 am
All well and true, but when do citizens say enough is enough. Creating and maintaining a two
tiered justice system is not the foundation on which democracy is built. How egregious does lawbreaking
have to become before support is withdrawn from these people?
readerOfTeaLeaves ,
June 1, 2016 at 11:48 am
IMVHO, that is exactly what we are seeing play out.
And trying to equate what Hillary did with Colin Powell's early use of email is simply beyond
the pale: I've seen no credible evidence that Powell ever set out to evade the NSA or the FBI.
For Hillary to conflate the two is flagrantly dishonest, and it pisses me off.
We may be at a 'tipping point' of the public finally fed up with a two tier system. Add in
income inequality, and things tip even more.
NotTimothyGeithner ,
June 1, 2016 at 12:45 pm
Equating Hillary to a war criminal makes perfect sense.
MyLessThanPrimeBeef ,
June 1, 2016 at 12:54 pm
That's for the FBI to show – hard evidence of intention evasion…a memo or a witness, while
Clinton, on the other side, will argue computer/internet illiteracy.
Tom ,
June 1, 2016 at 1:31 pm
Clinton has already been planting seeds of computer illiteracy, through her subordinates, who
claim Clinton "didn't even know how to access email on a desktop!" My lands, what's a pretty little
thing to do? Why, a lady such as Hillary must rely on the kindness of strangers, or gentleman
such as Bryan "Nowhere Man" Magliano, her IT Manager, to convey her electronic missives to others
in a timely manner.
People seem to forget that Clinton served on the Committee on Armed Services from 2003 to 2009
and on the Subcommittee on Emerging Threats and Capabilities … you know, the Subcommittee that
has jurisdiction over Department of Defense policies and programs to counter emerging threats,
information warfare and special operations programs.
If it were possible, I'd go back through the Sub committees minutes or transcripts to see how
involved ole' Hillary got when the subject was attempts by foreign governments or agents to hack
into U.S. government employees' emails.
oh ,
June 1, 2016 at 3:00 pm
It's possible that some of the information was only accessible by computer. She couldn't have
had any aides helping her 'cause they probably were not cleared to read such
info.
MyLessThanPrimeBeef ,
June 1, 2016 at 3:59 pm
From Jim Haywood on today's cooler:
But if you've ever watched one of these hearings, you know that perhaps 20 percent of the
committee members have even a layperson's knowledge of monetary policy. The rest waste their
5-minute question time delivering set-piece partisan rants.
Probably more display of illiteracy. Or, no unlike some college teachers – no practice experience, thought they sound impressive
in theory.
Lambert
Strether ,
June 1, 2016 at 2:58 pm
Intent is not a bar to a charge of gross negligence. "No intent" is a Clinton talking point.
MyLessThanPrimeBeef ,
June 1, 2016 at 3:57 pm
Perhaps her intent is to negotiate gross negligence to just negligence. From there, it's 'everyone does.'
Malcolm MacLeod, MD ,
June 1, 2016 at 9:03 pm
LS: Little rides on the fact that Mrs Clinton may be guilty of
stupidity, ignorance, or evil intent. The primary fact is that
Mrs Clinton is, was, and probably has been guilty of duplicitous
conduct for the majority of her life. She's no beginner or social
climber, but a real mountaineer.
polecat ,
June 1, 2016 at 12:01 pm
well…support IS being withdrawn , from them, in real time !!! That's why people, increasingly,
will vote scorched earth …. for Trump, if Sanders gets cheated out of the nom. They've had it
with the two-tired JUST US system, and the corrupt pols and corporate slugs who've benefited by
it !!
Brooklin Bridge ,
June 2, 2016 at 7:56 am
Agree. It's hard to know how many, but a significant number of people certainly are sensing
the depth of this morass, even if the particulars remain vague, and are reacting as best they
can given the choices. Since reasonable choices have been crushed to an amazing degree, as Matthews
– under orders no doubt – made clear, and this is part of what people sense is wrong, scorched
earth is what remains.
JacobiteInTraining ,
June 1, 2016 at 1:03 pm
In my case, it has already been withdrawn.
Hell, if Bonnie Prince Snowden were to land on the US equivalent of Eriskay…I would like as
not put on fatigues and go to join him, along with whatever other ragtag band of 'jacobites' rallied
to the cause.
Yes, it would likely end as miserably as 'The Forty Five' did, but I am long past believing
that ANYONE in a position of power in the Federal Government – any branch – really 'gets it' that
We, The People, are sick and damned tired of the crap they are up to, and the lengths they are
willing to go to pander and enrich their fellow power mongers.
The 'Just Us' system, indeed.
Maybe a little whiff of grapeshot might wake them up.
I know its either that, or someday the guillotines will be set up by a starving rabble with
far less of a sense of humor about these things then I.
jsn ,
June 1, 2016 at 10:44 am
What is interesting to me is the quality of what happens next as an exemplar: either Obama
doubles down on the Patraus treatment for the elite and everyone who's ever had a security clearance
is formally notified that the rules only apply to little people, or D O Justice acts on this in
the same spirit they have acted on Assange, Manning, Snowden, Stirling etc.
For those implicated at the heart of the security establishment, either decision will have
crystal clear implications. If it is the latter, the National Security State lumbers on in its
more or less current form which isn't exactly great and embroils our "presumptive" nominee
in a criminal investigation. If the former, things could get very interesting as those feeling
betrayed will be uniquely positioned to do something about it, particularly in the prospect of
spooks foreign or domestic having dirt with which to blackmail a sitting President.
Another great example of a status quo that, however you support it, sucks.
jawbone ,
June 1, 2016 at 9:31 am
"Maintaining a homebrew server could be written off as a policy violation, rather than a criminal
matter. The punishments for that are administrative (loss of job, loss of security clearance),
which don't really touch her."
Could she be denied top security clearance were she to be elected president? Or, is it given
no matter what to whomever is elected?
Also, it seems from the article that there are many people now privy to just how badly she
managed her email situation (others things as well? And are there actual hard copies? More tapes?)
and that could make her independence as president, well, simply no there there. Sounds like the
PTBs and/or their minions have her by the short hairs. And if she had any tendencies whatsoever
to not serve the Corporatists fully, that is no longer an issue: She would be totally controlled.
So, Hillary would now more than ever be the Corporatists very best bet to consolidate their
control, in the US and globally. Trump, second but could possibly be "uncooperative." Bernie?
Never allowed to be voted on as the Dem nominee.
fajensen ,
June 2, 2016 at 6:14 am
Oooh … Dear! Good Point: Hillary being so terribly bad that she's absolutely perfect for everyone
who needs to buy influence.
The excitement is seeing the market value of "The House of Clinton's Services" dropping from
hard currency to small favors and protection and now this once-in-a-century opportunity to get
in at the bottom may go away!
tegnost ,
June 1, 2016 at 11:08 am
Have you read this? from march and linked on 5/29 in the cooler. they've stumbled on a few
things…
https://informedvote2016.wordpress.com/2016/03/18/do-i-really-need-to-worry-about-hillarys-emails-yes-she-will-be-indicted-full-form/
and as pointed out here the administration can't bury judicial watch in the same way they let
the banksters off by telling DOJ to let 'em go. And fajensen points out above, classification
violations get little people in big trouble, and letting clinton off, which they can't seem to
do, will upset a lot of gov employees…but maybe it's just more eleventy dimensional chess
Gaianne ,
June 1, 2016 at 12:21 pm
Lurking in the background is the likelihood that the Russians scooped up everything on Hillary's
server, and the certainty that the NSA knows what they know.
This will not sit well with a lot of people.
Hillary will soon be down to her paid hangers-on and diehard loyalists. Even the bankers will
have to start recalculating.
–Gaianne
reslez ,
June 1, 2016 at 1:17 pm
It seems clear that being hacked by the Russians rated pretty low on the Clinton totem pole
of priorities. What concerned her more was the optics of whatever emails she was sending and how
the American public would react to seeing them. All her actions point to that. The Secretary of
State would rather have Russians read her emails than comply with the FOIA and other laws and
risk American citizens see the business she conducted on our behalf and at our expense.
I mean, for all I know senior gov't officials just blanket assume other countries have full
access to everything done on a computer, what do they care what the Russians know, the Russians
are corrupt too. But when it comes to a bad headline? Panic button time.
Praedor ,
June 1, 2016 at 6:54 am
I don't blame just Hillary. I blame the Clintons in their entirety. Bill was just as squirmy
with the truth (what's YOUR definition of the word "is"? Then there's his whole, "I did not have
asexual relations with that woman"). Their slimy slipperyness is genetic. They can't help but
lie, obfuscate, prevaricate. Bill is Hillary, Hillary is Bill.
As to wanting to avoid FOIA and subpoenas on her emails, I am sympathetic in broad strokes.
I too would want to keep my PRIVATE and PERSONAL emails and other communications private. I believe
strongly in the right to privacy and that is why I vehemently oppose NSA spying and corporate
spying via metadata. Our private lives BELONG TO US ALONE. The difference between Hillary and
I is in the nature of private communications. Unlike the Clintons, I am not a money grubbing greedy
bastard who will lie, cheat, steal my way to wealthy. I have NO sympathy for anyone seeking to
keep that crap secret and private. That said, if she'd been above board and simply had a private
email for non-official communications and kept the official State Dept stuff on the official account,
there would be nothing here. I served 20 years in the military. We kept official and confidential
communication strictly on the official network and via the official email accounts. Personal use
of the official email was discouraged and limited. You NEVER used your personal civilian email
for official communications. Never never never. I can't give her a pass on that because we in
the military wouldn't get a pass. We'd get an investigation and likely lose our security clearance
(career ending that is).
Alex morfesis ,
June 1, 2016 at 8:36 am
I did not have security violations with that server…
when $hillary was out of town…
$he liked to watch…
because all is well in the garden…
so you go tell rafael that I aint takin' no jive….
fajensen ,
June 1, 2016 at 9:31 am
I too would want to keep my PRIVATE and PERSONAL emails and other communications private
…
if she'd been above board and simply had a private email for non-official communications and kept
the official State Dept stuff on the official account, there would be nothing here.
Exactly. How hard can it be?
The work mail belongs to the workplace, we can basically expect that the PHB or the PFY in
tech support will read through it and it will be stored forever. Same with web-traffic. "Work"
may read, store and analyze it – so we visit naughty pages at home, strictly on our own time.
That is some of the reasons why we peons always use a private domain for private mail and the
work email for work email. Another one is to limit the ownership of work and ideas to those that
"work" actually does pay for.
Jonathan Holland Becnel ,
June 1, 2016 at 11:37 am
Same here, Praedor!
I commented a day or two ago that when we were downrange, you risked your career putting so
much as an USB into the computer.
Clinton chatted it up on her black berry straight from the offices of Special Ops Command!
LootersParadise ,
June 1, 2016 at 3:06 pm
I'm sympathetic to most of your argument, including your characterization of the Clinton's
obsession with personal gain. The Clinton Foundation is a money-making machine fueled by graft,
pure and simple.
But it's ironic that you criticize Bill for lying about personal affairs in one paragraph,
which only happened because Ken Starr actively sought to violate his personal privacy, and state
later that "our private lives belong to us alone." The only reason I have a shred of sympathy
for Bill is because Starr and his ilk trampled on his right to privacy. That judgment is shared
by most Americans, as reflected in public polls.
And as for "we in the military wouldn't get a pass" consider the by-the-book punishment of
David Petraeus – which never happened. The military doesn't have any special claim to legal fidelity
or consequences. As always, the enforcement of laws in this country varies according to the power
of the accused. That's why Hillary isn't and never will be in prison.
Kurghen ,
June 2, 2016 at 7:37 am
While generally sympathetic to LootersParadise's argument, I would point out that when Bill
Clinton was Commander-in-Chief, young military drill sergeants were being court martialed and
sentenced to lengthy prison terms for consensual sex with female trainees. The legal premise was
that the disparity in their rank and authority made any sexual relations "tantamount to rape".
Clinton's behavior with a young intern was worse than bad judgement, it was predatory, and no
military commander or drill sergeant would have been excused from such conduct with the argument
it was merely a "personal affair".
Yves Smith
Post author ,
June 1, 2016 at 4:22 pm
You keep your private business private by using separate equipment. 2 smartphones. 2 laptops.
Tons of people in DC do this, starting with Congressional staffers and assistants to people in
Federal agencies. This isn't rocket science. She just wasn't willing to bother.
aab ,
June 1, 2016 at 7:13 pm
Isn't it also possible, though, that since her State business really was private business,
in that she and Bill were working together to sell influence at State to enrich the "Foundation,"
this wasn't merely entitled laziness? Maybe they made the decision that the best way to limit
the paper trail was to just send all State Department correspondence through the server and thus
directly to Bill, making it harder to track and prove when they were explicitly collaborating.
I can totally see them thinking this was quite clever.
Entitled also works, of course. I do think a big reason for the Blackberry is that she refused
to allow the guy who "ought to be carrying her bags" to have a goody she didn't have.
HotFlash ,
June 2, 2016 at 8:36 am
Apparently that one doesn't fly either, f
rom the horse's mouth via Slate.
Money quote: "I'm like two steps short of a hoarder. So I have an iPad, a mini iPad, an iPhone
and a Blackberry."
Pat ,
June 1, 2016 at 7:06 am
The case can be made that the known hacking was of someone she had a correspondence with (troubling
as that was) not of her server. While I don't believe her server was secure, and I'm pretty damn
sure the IG and the FBI don't think it either, the public can still be spun on this. That is not
the problem.
No, what has become crystal clear is that she didn't have permission to set up her email this
way, that the NSA and State did not sign off on it, that she was told that and because she didn't
want any public oversight of her actions she blew off federal regulations regarding FOIA and the
collection of records for the State Department both in setting up the server itself AND in not
supplying any documents not in government possession upon leaving office (not two years later).
Because she did handle classified material on that email server, she did put herself in jeopardy
legally – regardless of her intent and whether the material was hacked or not. And people who
do have to follow Security guidelines or face dismissal, fines or worse are pissed as hell about
it and are not going to let it go. So it can't just be played off as a right wing conspiracy –
no matter how much they try. These guys aren't Judicial Watch, and their credentials are better
than Podesta's.
On the public level, except for the Clinton sycophants and tribal Dems who desperately want
to believe this really is a nothing burger, what this means is that Clinton had no intention of
allowing public oversight into her actions if she can avoid it by any means whatsoever, regulations
and the law be damned. And that she does not consider herself a public employee even if she is
one and being a public employee is where her power lies. Now those of us who distrust her and
her husband and child just outright assume that this is because her real business is selling access
to government and its monies or services to those with the funds to afford the Clintons. But most
people are reacting to the sheer arrogance of the "law doesn't apply to me" attitude and the lies
about it so far. But the longer this stays around the more it will become 'what DID she have to
hide'.
So this tells me something different. It isn't really about how big a threat Clinton is to
the 'Obama legacy' and how terrified they are she is blowing this. Or rather has blown this since
it stems from actions from seven years ago, although later choices have compounded it. No, this
is about how much bigger a threat Sanders is to that legacy and how close her blowing this gets
HIM to the nomination. Otherwise why is this about her getting the nomination. Her getting the
nomination and then Obama getting out on the road and saving her butt only works if the threats
from the investigation disappear BEFORE she gets the nomination officially. It really blows up
while he is campaigning for her and his legacy is also blown.
Of course, this presupposes that he WILL get out there and campaign for her beyond a few cursory
appearances. If the President is suddenly too busy to campaign, I will admit to being wrong and
it is all about Clinton's threat to him, even if I think a better strategic choice would be to
find a way to torpedo her outright if that is the concern.
pretzelattack ,
June 1, 2016 at 7:14 am
this may be one of the initial signs of the torpedo. "captain, it looks like something is moving
toward us underwater". he wasn't required to broadcast his concerns like this. you make some excellent
points. meanwhile, i'm successfully controlling my impulse to attempt to do a cartwheel. so far.
Pavel ,
June 1, 2016 at 7:51 am
Pat - excellent analysis, thank you.
And Yves, great post. As you point out, the use of Bernstein as White House messenger - if true
- makes that a pretty explosive little interview.
I note the lawyer twisting himself into knots trying to say that Hillary didn't "lie" about
the server.
Steve H. ,
June 1, 2016 at 7:54 am
– And that she does not consider herself a public employee even if she is one and being a public
employee is where her power lies.
That may be the right twist that puts the optics in focus. Arrogance and petulance are tolerated
in politics ('he's got a Blackberry, I want one!') But the Clintons are cunning enough to not
risk the appearance without reason. They need to be smarter than their customers, and just one
bad email from a dunderhead could prove a quid pro quo link from the Clinton Foundation to the
State Department.
Obama knows better than anyone her tendency to collapse. His campaign was 'Change,' and that
she does not do.
Samuel Conner ,
June 1, 2016 at 7:58 am
"Getting her to the nomination" allows the D establishment, after she is forced to step down,
to replace her with Biden/Warren or some other "anyone but Sanders" ticket with less trouble (party
disunity, bad optics, turnout suppression) than if she implodes before the convention and the
HRC delegates + superdelegates outright steal the nomination from Sanders.
Bryan ,
June 1, 2016 at 8:04 am
IMO, it's utterly impossible in this climate for anyone other than Sanders (or whoever Sanders
signs off on, like Warren) to become nominee if HRC implodes.
Roger Smith ,
June 1, 2016 at 9:19 am
I agree. The optics would be off the charts terrible for the party. They are in a rock and
a hard place. I think their best non-Sanders bet (if they continue their double downs and selfish
folly) is to stay with Clinton. If she implodes, so be it, have her impeached (if she wins) and
be done with it. Pass as much of the responsibility off on her and what she did wrong. "The party
did not know! We are victims!"
vlade ,
June 1, 2016 at 10:56 am
actually, the back-door candidate could be Warren. She endorsed neither, has clearly anti-WS
policies, but is not as "radical" as Sanders. She would likely be acceptable to a number of Sanders
people (incomparably much more so than HC), she's woman (so still a first woman president message)
etc.
She's better debater than Sanders I believe (and incomparably better than HC), and could (assuming
there are no bombs in her backyard) deal with Trump pretty well.
So, if the plan in Dem circles is to get past primaries and then shoot HC and fend off Sanders,
I'd say Warren is about their only reasonable choice.
NotTimothyGeithner ,
June 1, 2016 at 2:06 pm
Warren is a threat to the courtesan class as much as Sanders. Saturday design and Warren threaten
every Democrat who has ever said "the dopes would vote for for If they just understood how smart
we were and had better messaging," just by existing.
vlade ,
June 1, 2016 at 6:20 pm
Warren is a very specific threat to WS. She's a less of a generic threat than Sanders is –
say look at her education proposals. If it looks to Dems like a choice between HC enabling Trump,
Sanders changing the party entirely, or Warren as a compromise, they only reasonably safe bet
is Warren. HC getting nomination and then losing to Trump kills the Dem party (as we know it)
as well as Sanders would if he won. The difference is that one (Sanders) is a certainty, while
the other (HC losing to Trump) is still just a probability. But one raising every day so far.
Coming up with somoene like Warren, even HC can look statesmanlike in pulling it off (say blaming
it on bad health, but giving a chance to another woman), in exchange for a deal that Warren focuses
on WS. Chances of Warren winning against Trump are very high, possibly higher that Sanders.
That said, I doubt this would happen.
Code Name D ,
June 1, 2016 at 1:10 pm
But the question of the day is – are they smart enough to know this? All the chatter I hear
from the beltway is that they don't. That once the nomination is "decided", Sanders will lose
his clout and things go back to normal.
Bryan ,
June 1, 2016 at 2:09 pm
Whole thing hinges on Sanders' concern for his reputation among the elite, and how much he
buys the "Trump-means-the-end-of-civilization" garbage. His only leverage is his base, and frankly
if he tries to make nice with the Dem establishment after she is nominated, he loses a lot of
his cred with that base.
He's going to get very little from them – at most, Warren as VP, which isn't much. No way she
gets to be Treasury Secretary, for instance. And why would they give Sanders anything? At bottom,
the DNC types believe the left will have nowhere to go come November. Thus Sanders has one job:
GIVE HIS BASE SOMEWHERE TO GO. Doesn't matter if he only wins 8%, either as a Green or (far less
likely) an independent. He's got the invitation from Jill Stein sitting out there. Earn matching
funds, raise tens of millions a year, and run candidates across the country in two years. In four
years, mount strong outsider candidates for major offices including president.
But I don't think Sanders has it in him. Too "constructive," as Chuck Schumer called him.
MyLessThanPrimeBeef ,
June 1, 2016 at 2:32 pm
Does Sanders try to make nice with the Dem establishment, or, as Bubba_Gump at 8:58am below
writes, he's too inflexible to make the right friends?
I still don't know what he's doing with the D establishment like Schumer.
Voters will vote him no matter where he goes.
Gaius Publius ,
June 1, 2016 at 2:56 pm
Sanders will lose his clout and things go back to normal.
He won't lose his list, and he now has more followers than any politician in America. He can
run his project sitting in the Senate, using that list and his follower base to influence policy.
IMO. This is far from over.
GP
nat scientist ,
June 1, 2016 at 5:38 pm
The Internet will save Bernie just like it was envisioned by DARPA in the dawn of the Nixonan
Age, built to survive thermo-nuclear annihilation like the ClinTrumpocalypse.
Tony S ,
June 1, 2016 at 4:18 pm
I don't think she'll win (the presidency) even if she DOESN'T implode. She has no message.
She's banking on identity politics. That won't work in a change election.
It's just a question of degree. If she does get indicted, the Dems lose BIG under every possible
scenario except Sanders. If she doesn't, she still probably loses, but at least it won't be a
wipeout downballot.
Big River Bandido ,
June 1, 2016 at 6:00 pm
Downballot the Democrats have already been wiped out, for 22 years running.
Republicans hold 31 governorships to the Democrats' 18. Republicans hold 56% of all statehouse
seats (Democrats 43%), and they control the lower house of 33 state legislatures (compared to
16 for the Democrats). It's difficult to even view the Democrats as a party, but if they are,
they certainly have no depth of talent.
Add a highly disliked business-as-usual politician to the top of the ticket in a "change" election?
Democrats won't have a prayer in the fall.
Fiver ,
June 2, 2016 at 4:34 am
As one who believes Clinton ought to withdraw before inflicting or sustaining any more damage
in the certain knowledge that her candidacy has been hopelessly compromised, I would argue that
Sanders is the one candidate now able to pull other contests along with is own. Sanders could
swing it from a Republican Congress literally impaled by a lethal lack of talent to a Dem Congress
with new faces and new marching orders for long-entrenched types. He really could go all the way
in my opinion.
Brooklin Bridge ,
June 2, 2016 at 8:16 am
The voice of reason, which is why the choice you suggest will be the very last one ever taken
– we won't see it. This isn't merry 'ol England, ok UK, where they still goof by letting votes
get counted sometimes (Jeremy Corbyn).
hunkerdown ,
June 1, 2016 at 4:36 pm
The Democratic Party's working priority list apparently putting control over the Party above
winning elections, I imagine they are very interested in doing the "impossible", if the benefits
to the collaborative nexus of interest (i.e. the Party) of blocking Sanders - neoliberal "purity
pledges" with other countries, State selling more Americans' labor abroad like cheap cord wood,
inducing despair among the left (a favorite of the Israeli wing of the Party, who sees leftists
like unto Hamas) - to the Party outweigh the loss of one election or even the ballot line. With
a post-Citizens United machine and its "non-coordinated" universe of nomenklatura, ready to pick
right back up where it left off with a New (Improved) Democrat Party (Same Great Taste!) or somesuch,
constituted specifically to exclude popular participation, it's relatively cheap.
sleepy ,
June 1, 2016 at 10:35 am
And obviously the reason for the all out push by the media and the Clinton campaign to have
Sanders throw in the towel before the convention which, of course, reached fever pitch the same
week the IG's report came out.
JohnnyGL ,
June 1, 2016 at 11:02 am
This string of comments looks on target. I think this is the unstated reason why the primaries
are STILL important.
If Bernie were to get swept on 6/7, he might fold. Every time he looks like he's losing steam,
he gets a string of rallies with 10s of thousands of people and realizes that he CANNOT stop.
There's too many people counting on him to save us from a Clinton/Trump nightmare.
If Bernie sweeps her on 6/7, the writing is on the wall at that point and she'll look like
she's toast. FBI will get the green light and Dem elite will have to bite their tongues and deal
with him.
My guess is that he wins 4/6 primaries on 6/7 and NM and NJ are losses, but somewhat closer
than anticipated. Clinton will continue to act like it's over and the FBI will continue to dither
and the convention floor ends up being a fight (prob won by Clinton).
A key question is, "When do the rank and file FBI agents lose patience and start leaking bad
details to the media?"
Or do FBI agents start resigning in protest at the dithering of their superiors.
Obama/Clinton may have the top brass at FBI and DOJ on board, but if the rank and file decide
to mutiny, then they can't save this sinking ship that is the SS Clinton!
sleepy ,
June 1, 2016 at 1:48 pm
You have to have tremendous admiration for Sanders to stick it out with what is obviously a
physically and mentally grueling ordeal at the age of 74. I'm 65.
Of course both Trump and Hillary aren't much behind him in age, but Sanders is doing it imho
out of principle and ideals, as well as respect for the public that has backed him. He must think
back to himself as a young man in the 60s, and realize that this is a chance he could only have
dreamt of 50 yrs. ago, and just can't turn his back on that.
Brooklin Bridge ,
June 2, 2016 at 8:21 am
Good observations. This has to be brutal, even for a veteran politician – particularly one
who has kept scruples alive all these years.
Tony S ,
June 1, 2016 at 4:09 pm
"Getting her to the nomination" allows the D establishment, after she is forced to step
down, to replace her with Biden/Warren or some other "anyone but Sanders" ticket with less
trouble (party disunity, bad optics, turnout suppression) than if she implodes before the convention
and the HRC delegates + superdelegates outright steal the nomination from Sanders.
If they do this, the Dems will lose in November. And badly. They won't get more than a handful
of Sanders voters after this kind of a backstab, and the party will be (rightfully) perceived
as a bunch of clueless clowns who thought a potential criminal would make a suitable nominee.
Independents will strongly swing to Trump.
The question is, do the Democrats care? I can easily see the Dem establishment taking one for
the bipartisan consensus beltway team in order to keep Sanders out of the White House. They never
did much to support Gore and Kerry in the wake of their questionable defeats - and both of them
were much more harmless to the establishment than Sanders.
jawbone ,
June 1, 2016 at 9:37 am
NSA did not give Hillary permission to use her own server? That is a known fact or surmised?
Did she even run it by the NSA, other pertinent agencies?
Bcz, if I were in charge of the NSA I'd damn well make sure the agency knew exactly what she
was doing with that server….
Minnie Mouse ,
June 1, 2016 at 11:30 am
What would the e-mail address of a private server look like? Would it be apparent to anybody
who encountered it to be something – say – non standard? But keep your mouth shut.
reslez ,
June 1, 2016 at 1:28 pm
Well, her official email address as SecState would have ended in @state.gov. The address she
actually used was @clintonemail.com. It was obvious to everyone what she was doing. If you work
in the State Dept, do you question your boss over something like that? Maybe not, you might assume
it was cleared somehow. It looks like IT and Security people were appalled.
Jake ,
June 1, 2016 at 1:32 pm
[email protected]
reslez ,
June 1, 2016 at 1:25 pm
The IG report found no evidence she had permission from anyone to use her own email server
nor any record of her even asking for permission. Which contradicts statements she made elsewhere.
3.14e-9 ,
June 1, 2016 at 10:26 pm
Has Clinton ever actually said that the State Department allowed her to have a private
server at home and that everyone knew about it? What I've heard her say, and what I took
away from the little bit of the Mills deposition that I've read so far, is that the State Department
knew she had her own email account ; that use of a personal email account was allowed
, and that others before her also did it, most notably Colin Powell.
Anyone can buy a domain using their last name plus "email.com," or whatever variation thereof
is available. However, most people (presumably) use a hosting service. It seems obvious to me
that there's a huge difference between having a personal email account and storing said email
on a server in your basement, but Clinton appears to have succeeded in conflating the two in the
public's mind. Her supporters certainly seem satisfied, particularly since she has apologized
and openly admitted to a lapse in judgment. I'm not a techie, so maybe I'm meowing up the wrong
telephone pole. Tech people here, what's your take?
If I'm right about the distinction and what they've actually said, Clinton and Mills could
well be telling the truth that many people at DOS knew she was using private email, and that it
was allowed, even for official government business. It's unlikely that her clintonemail.com address
raised many eyebrows, even among those who noticed – and many might not have, because once her
address was in their contact list, the extension probably wasn't displayed. The big exception
was at the very beginning, when her clintonemail address was getting stuck in DOS spam filters
and had to be put on a safe sender list, or something to that effect.
Of those who noticed she wasn't using a .gov address, how many would have thought about the
server she was using, and how many of those would have imagined that her office hadn't gone through
proper security procedures? It's quite plausible that the only people knowledgeable enough to
be concerned were the IT security people, and when a couple of them eventually did raise questions,
they were told to keep quiet about it.
fresno dan ,
June 1, 2016 at 12:12 pm
Pat
June 1, 2016 at 7:06 am
Nicely said!
'what DID she have to hide'.
At some point, some of the substance of what was hidden will be revealed – it is terribly hard
to believe that it will be that she donated a kidney to a Syrian refugee….(Oh look, she looks
sickly because she is SOOOOO Noble!!!)
Lambert
Strether ,
June 1, 2016 at 3:02 pm
The problem is that the "Clinton sycophants and tribal Dems" are a large part of the Democrat
base and an even larger part of the Democrat establishment.
I don't see how they get talked off the ledge (absent Clinton "discovering" new medical problems
(or even Bill, maybe)).
Samuel Conner ,
June 1, 2016 at 7:51 am
Not mentioned in this item, but relevant to Obama's legacy, is that he left the State Dept
IG post unfilled by a permanent appointment throughout HRC's tenure as Secy State. The acting
IG was a career State Dept official, and did not rock HRC's boat. Obama is implicated in HRC's
misdeeds in the sense that he left the barn door open for her. There's a sense in which the HRC
email scandal may become part of Obama's legacy, whatever he does now. As Yves sometimes puts
it, this has been an unnecessary "own goal".
nycTerrierist ,
June 1, 2016 at 9:47 am
Interesting! good catch.
tegnost ,
June 1, 2016 at 11:19 am
Are you sure it wasn't hillary who, as head of state dept., was tasked with appointing an IG?
MyLessThanPrimeBeef ,
June 1, 2016 at 3:01 pm
I think you're right.
That raises another question – conflict of interest for her (any future secretary) to make
that appointment.
A third question is if there is a time limit to have the office filled. Otherwise, the way
to get around it is to delay and run the clock out.
LizinOregon ,
June 1, 2016 at 7:25 pm
No. The IG's of major agencies are nominated by the President and confirmed by the Senate.
Here is an interesting article which hints that using acting-IG's makes them less independent
and is being done intentionally by the Obama Administration. They have the longest vacancies of
any recent President.
http://www.govexec.com/oversight/2015/06/senators-obama-fill-inspector-general-vacancies/114412/
tegnost ,
June 1, 2016 at 8:27 pm
thanks for that, here's a tidbit, I notice the ex-im bank and international development are
(not likely there's any double dealing going on there, no, nothing to see here as long as you
don't look) unmanned, among others
"Currently, said Michael Horowitz, the Justice Department IG who chairs the Council of the
Inspectors General on Integrity and Efficiency, IG slots are vacant at seven major agencies: Interior,
the U.S. Agency for International Development, the Federal Deposit Insurance Corp., the Veterans
Affairs Department, the General Services Administration, the Export-Import Bank and the CIA All
but the CIA's have been empty a year or more, he said, and the Obama administration has submitted
nominations for only three."
and also this
"{"When IG positions remain unfilled, their offices are run by acting IGs who, no matter how qualified
or well-intentioned, are not granted the same protections afforded to Senate-confirmed IGs," said
Chairman Ron Johnson, R-Wis. "They are not truly independent, as they can be removed by the agency
at any time; they are only temporary and do not drive office policy; and they are at greater risk
of compromising their work to appease the agency or the president."}"
Tom in AZ ,
June 2, 2016 at 1:12 am
Are you sure that he didn't nominate anyone, or did the Senate just refuse to give them a hearing,
as in the SC situation now?
Pavel ,
June 1, 2016 at 7:55 am
I browsed through the Cheryl Mills deposition yesterday (which was mainly the lawyers arguing
about the scope of the discussion it seemed) and some of the coverage today. It seems that Mills
claimed that HRC's use of the private email was not kept secret and lots of Admin officials knew
about it. (Note that people had to make a special request to be able to use her email.) But Obama
claimed he only learned of it "like the rest of you, in the news reports". So Obama and Hillary
never emailed each other while she was SoS?
human ,
June 1, 2016 at 8:39 am
I don't find it surprising that they did not communicate directly. Plausible deniability. What
we have is a career civil servant intent on influence peddling and a figurehead interested only
in legacy burnishing. They are a perfect fit … as long as they stay out of each others way.
Qrys ,
June 1, 2016 at 8:52 am
To your last comment: I suspect not. They never were chummy esp. after all the heat of the
campaign: "You're likeable enough, Hillary". Obama has plenty of staff to wrangle correspondence
for that, and his aides being middle-persons (and likely being of a generation that put a lot
more trust in technology at the time) likely didn't think that hard about it…
oh ,
June 1, 2016 at 3:20 pm
They never were chummy esp. after all the heat of the campaign: "You're likeable enough,
Hillary". Is there any confirmation of that besides rumors?
grayslady ,
June 1, 2016 at 9:22 am
It was reported last January that there were eighteen emails between Clinton and Obama that
State was not going to release for security reasons. So yes, they did email each other. It would
be interesting to know what security instructions Obama received regarding using his email. Did
anyone ever caution him to check the sender's email address as a caution against phishing? Her
email address was clintonemail dot com. Even a technical neophyte has to know that means either
she or some other entity was hosting the site; and, if a separate entity, did that entity have
security clearance for handling those emails? Obama knew darn well that she was using an unsecure
system. He is equally guilty of enabling her risk-taking.
MyLessThanPrimeBeef ,
June 1, 2016 at 12:27 pm
Maybe the FBI can investigate just how many people have mishandled classified information.
10,000 government workers?
100,000?
If one can be in trouble for taking a selfie before a classified equipment, that one wasn't
aware so (as fajensen wrote above), can one be in trouble for opening a letter, a disk or a laptop
(mistakenly delivered or left behind) containing classified information?
fajensen ,
June 2, 2016 at 7:07 am
Within the perimeter of a secure environment, you bet you can!
Any paper, CD, computer, phone, …. left alone in the open is already a violation. At the place
I consulted at, there are prominent red+white background with the 3-digit number to call for security
in *all* cases. Everything has to be locked away, even if one is going for coffee or toilet, one
must leave all electronics at the gate. "No mistakes are possible, only conspiracies" the thinking
goes.
If one picks any abandoned device / media up, well, it's kind of the same situation as when
you find a gun on a park bench: Pick it up "for safety", but now your finger-prints are all over
it. And now the police shows up because someone reported the gun …
The very minimum price is a really tedious debriefing by security and punitive training from
HR in the handling of classified material. Maybe some Gender Diversity or Cultural Awareness on
top because you cursed at the debriefing.
Maximum … about 30 years.
Outside the classified zone, it's easier.
If you find an unsecured laptop or briefcase that – per long-standing British security tradition
– was left on the London Tube, you are probably not in trouble, you can even hand it over to The
Daily Mail or whatever for a "reward" since the HMG doesn't pay any. Don't sell it on eBay though.
China and Russia may buy and then … it's espionage.
Kurt Sperry ,
June 1, 2016 at 10:03 am
I had the exact same thought. How do the POTUS and SOS not have any record of electronic communication
between them, zero?
craazyboy ,
June 1, 2016 at 1:50 pm
For important stuff, they use "The Cone of Silence".
https://www.youtube.com/watch?v=g1eUIK9CihA
thoughtful person ,
June 1, 2016 at 8:06 am
"because her real business is selling access to government and its monies or services to those
with the funds to afford the Clintons. But most people are reacting to the sheer arrogance of
the "law doesn't apply to me" attitude and the lies about it so far. But the longer this stays
around the more it will become 'what DID she have to hide'."
Good point. Proceedeing to conduct the public's business in private is the smoke. Many suspect
the donations to the Clinton foundation by various entities with business beefier the state dept,
could be the fire…
dk ,
June 1, 2016 at 8:54 am
That's it. A point being skirted by just about everyone in the MSM. Smoke here, smoke there,
and a black hole in the middle.
redleg ,
June 1, 2016 at 9:16 am
They (DOJ) don't have to charge/indict her with anything to Hindenburg her campaign. RICO the
Foundation and it's over.
I'll bet that's why the FBI is taking so long- the email investigation has spread to the Foundation.
The media isn't going there and the FBI had already leaked that they are looking into it.
jawbone ,
June 1, 2016 at 9:43 am
The "real business" of the Corporatist Dems is –ta dah!– creating more wealth for the Big Whatevers
and making sure they donate enough of their wealth to get the right Corporatist Dems elected.
And, of course, making sure that those who serve the Big Corporations and Big Whatevers well are
granted true wealth once out of office.
And with more wealth comes even more power
it is stunning how very wealthy (as far as we know) the Clintons have become in such a short
time. But it somewhat stunning how very wealthy Corporatist Dems in general become….
Bryan ,
June 1, 2016 at 11:52 am
Here is a liberal publication clearly suggesting this same point last year:
http://www.motherjones.com/politics/2015/05/hillary-clinton-foundation-state-arms-deals
NYPaul ,
June 1, 2016 at 1:34 pm
The public doesn't do nuance; it requires in-your-face visuals: "little girl + the daisy, Willie
Horton, blue dress."
I wonder what the reaction would be to a montage, with the caption, "I would never
let campaign contributions influence my decisions."
First, Hillary collecting $675,000+ for a couple of Goldman speeches…….."They offered it"………cackle.
Then, Bill, with a photo of the "Lolita Express" flying overhead (poetic license:)
Repeatedly requesting permission from State to travel to Africa to meet with Joseph Kabila,
the murderous Dictator of the poorest country on earth, the Republic of Congo. The butcher had
offered Clinton $650,000 to give a short talk, and have his picture taken with the Ex-President.
The request was so outrageous it was, of course, summarily turned down. Not to be deterred so
easily, the Big Dog persisted, telling an aide to try again, this time making sure the decision
maker at State knew it was B.C. personally making the request. Turned down again, Willie shifted
gears, "what if the fee was paid to the Foundation (or, GCI, not sure,) and not directly to me?"
We should be thankful intermediaries had the good sense to , diplomatically, tell Bill to,
basically, get-the-F- outta here with this request. But, naturally, it's the optic of this Ex-President
even requesting such an inappropriate meeting that, so perfectly, illustrates how far down the
sleaze ladder the Clintons have descended.
Oh, you can toss in that, "we came, we saw, he died"……….. extended cackle video for good measure.
https://www.youtube.com/watch?v=Fgcd1ghag5Y
dk ,
June 1, 2016 at 8:09 am
Considering that Obama sees Clinton as part of his legacy, I think there will be some limit
to how far he (his people) will go to protect her. A thoroughly tainted Hillary doesn't serve
his interest. I read the Bernstein statements as first step away from HRC, and not a tiny one
either. "… no longer 100% sure of …" implies "we don't guarantee it".
And the Obama and Clinton teams never warmed to each other, even during her tenure at SoS.
(Team) Obama is certainly upset about the prospect of a Clinton failure, but they're not shedding
any tears.
Skip Intro ,
June 2, 2016 at 12:26 pm
The first step may have been his 'jokes' at the WH correspondents' dinner.
PlutoniumKun ,
June 1, 2016 at 8:10 am
What I don't really get is the motivation for allowing stories like this to leak out, if its
not to undermine Clinton?
The way I see it, if Obama was truly, deeply invested in Clinton winning (and I'd be surprised
at that, given that we know he doesn't really like her), he would be working hard behind the scenes
to shore her up. Get her over the finishing line of the convention, and then deal with things
after that as they arise. This sort of leak can only weaken her significantly and maybe even encourage
a few superdelegates to start thinking Sanders is a safer option.
The only motivation I can think is to lay the groundwork for a coup against her (and, by definition,
Sanders). I'm no expert on internal Dem rules and what is possible legally, but it always seemed
to me that the logical and route for Obama to preserve his legacy and ensure a Dem win is to make
private calls to senior Dems and say 'trust me, I've seen the legal documents, Clinton is finished,
I know she can't get out of this', and then parlay a face saving climbdown (glass of whiskey,
gun, private room, medical cert) for Clinton in order to put forward a 'safe' ticket at the convention
(Kerry/Biden?). Is it possible for her to transfer her elected delegates to AN Other?
pretzelattack ,
June 1, 2016 at 8:19 am
well, that would likely tear the party apart. i think they would rather trump win than sanders,
but imposing biden/kerry or some such is a risky strategy in the present environment. i think
the natural impulse of these people is to be risk averse, and in their bubble they might not be
able to gauge the risk.
dk ,
June 1, 2016 at 8:52 am
I don't think it would tear the party apart, it would just upset the Dem consultants and vendors.
Sanders reliance on small donations completely upsets their economic model, which is based on
a revenue stream from big donors. Big donors aren't interested in supporting populist goals, ergo
populist goals are not money-makers.
On the other hand, a Sanders general candidacy would expose all the Hillary supporters currently
making the "party loyalty" and "not another Nader" arguments to be completely specious if they
didn't pitch in. Some might have the stomach for that, but most are herd followers to begin with.
And the threat of Trump is completely real, regardless (unless the Reps manage to pull a fast
one at their convention… which would completely sever that last leg Clinton is standing on).
sid_finster ,
June 1, 2016 at 10:36 am
Not to mention a Sanders win would render the DNC, their networks, their influence, and yes,
their ability to fundraise, irrelevant.
They would no longer be gatekeepers. They would not be necessary for a candidate to win.
Someone else put it best. The DNC does not fear that Sanders will lose. They fear Sanders winning.
Bryan ,
June 1, 2016 at 12:04 pm
Exactly this. Like vampires, the DNC must find a way to cannibalize the energy of Sanders'
supporters in order to re-invogorate a moribund Party, while not losing influence over it.
But the two fundraising models cannot live comfortably in one party for long, certainly not
if the corp/elite funding continues to determine the Party's direction.
Sanders is risking a historic misstep in staying within the Party too long. He's right to stay
so long as Clinton is capable of imploding, but the moment he's pressured to go full sheepdog
in support of Clinton, he has to step away and use the funding structure to build a truly left/populist
party.
I doubt he will. He wants her to win instead of Trump, and the DNC types will outmaneuver him
because of this. I fear all of the concessions he wins in exchange for his cherished email list
will be for nothing once the real game begins.
human ,
June 1, 2016 at 3:33 pm
Ah yes. The ultimate snatch of defeat from the jaws of victory. The Dems have always been performance
artists extraordinaire.
Harold ,
June 1, 2016 at 7:04 pm
Not to forget. "The Blob" doesn't like Sanders.
PlutoniumKun ,
June 1, 2016 at 9:15 am
Is it really a risk of tearing the party apart? If managed right, it could be sold as a 'unifying'
move to heal the wounds of the nomination process, etc., etc. Especially if a genuine left winger
was added as vice prez. The leadership is risk averse, but they can also be ruthless, and they
may see the risk of a catastrophic Clinton meltdown as a greater risk.
JohnnyGL ,
June 1, 2016 at 11:21 am
DNC is desperately hoping for a knockout blow on 6/7. Wins in states like CA for Sanders would
only rile up his supporters even more.
If they dare to push a Biden/Kerry ticket, it's going to been seen as a "coup". Tensions are
already visibly raised after the NV debacle. DNC tried playing hardball and smearing him and his
supporters and he didn't fold. It seems like the Dem elite might be backing off on these tactics.
A Biden/Kerry ticket would really escalate things and probably make Sanders bolt to the Green
Party for the general election. Under those circumstances, he'd bring a TON of voters with him.
He'd even bring Clinton sympathizers that don't like the DNC's bait-and-switch tactics.
They need Sanders to fade away and fall in line. Every state he wins, every rally with 10s
of thousands showing up make it harder and harder to make that happen.
Pavel ,
June 1, 2016 at 12:31 pm
Given that the mood of the electorate both left and rightwing is "anti-establishment", I don't
see why on earth the Dems would choose Biden/Kerry… how much more establishment could one get?
At least offer Warren (and get the "first female president" too boot) and throw Sanders a bone
- he's too old for VP but could have a cabinet post. Or Senate Majority Leader? (That is probably
too critical a post for the Schumer/Feinstein axis though.)
aab ,
June 1, 2016 at 7:29 pm
There is no genuine left winger to put on as VP. Or rather, they would NEVER put a real left
winger in, given Clinton's possible impeachment or death.
Now that Elizabeth Warren is being a good girl and playing footsie with Schumer, I can see
them thinking putting her in as VP would work well enough. I don't think so (in my neck of the
progressive woods, there seems to be a general understanding that she sold out), but more importantly,
I can't imagine Hillary stepping away only to see Liz moved in.
Their smartest real play would be to let Bernie have the nom and bide their time, hoping they
can work in the background with Republicans to taint and undermine him. But I suspect that they're
exactly smart enough to know that probably wouldn't work.
EoinW ,
June 1, 2016 at 10:32 am
Exactly right! In their bubble, in their world where they manufacture their own reality, can
they gauge risk? I highly doubt it. The establishment needs an establishment candidate. That's
why Sanders will never get the nomination. Given the freak out on the republican side just over
speculating stealing the nomination from Trump, I think it comical anyone could believe the democrats
could airlift Biden in and get away with it. Such an act would simply be establishment desperation
– the only Plan B they could come up with.
Given the vote rigging Sanders supporters believe has been going on, I doubt any will vote
for Clinton. How many would vote Trump and how many would sit out is open for speculation. However
give the nomination to Biden and i think you're guaranteeing a landslide of Sanders supporters
pinching their noses and voting Trump. They'd be just angry enough.
Clinton or Biden? it doesn't matter as Trump wins in a rout. Sanders would be a close call
but he'll never get the nomination. The establishment must have skin in the game until they finally
get what they deserve in November.
I'll also add that i'm not holding my breath that Trump is the instant panacea to save America.
In fact I wouldn't be surprised to see him cutting deals like crazy with the establishment behind
the scenes or after elected. He won't need the unwashed masses after November. Doesn't mean he
does that and even if he cuts some deals he'll still do more good than any establishment candidate.
More and more American voters see him as the only non-establishment option. It's never really
been about Trump. It's about American voters lashing out at the elites. Trump was simply clever
enough to present himself as the great non-professional politician for people to turn to.
James Levy ,
June 1, 2016 at 12:08 pm
People keep saying this about Sanders voters but I know five (three in my family) who will
without fail vote for Clinton over Trump because they hate Trump, see him as a bigot and a fool,
and expect Clinton to be Obama's third term, which they can live with.
I don't agree with them, but this endlessly repeated meme that Sanders voters will NEVER vote
for Clinton is, I think, wishful thinking.
EoinW ,
June 1, 2016 at 12:27 pm
Guilty as charged! Wishful thinking indeed. Guess I can't condemn those for thinking an Obama
like 3rd term would be a better result. I suppose any kind of thinking falls flat when confronted
with the people who live in a highly materialistic and superficial society. Trump optics are very
unPresidential and that counts for a great deal in a society(not just the US) that has been conditioned
to rever the president of the USA.
Won't even touch on the Left and the Culture War because I've made that point previously.
tegnost ,
June 1, 2016 at 1:24 pm
my rich friends (lifetime republicans included) will vote for hillary, my poor friends won't.
The PTB have created more poor people tha they have wealthy so the numbers won't work for hillary
unless a lot of republicans vote for her, which is not a stretch because she is a republican.
But since we talk about nader costing gore (really it was dinos for bush) by taking 500 odd votes
the sanders deserters (including me, i will not vote for hillary under any circumstances, and
not because I think trump is good in any way, hillary is worse IMO) will exact their revenge even
as their more comfortable peers who have and continue to benefit from the rigged game go for hillary.
We really have no idea how this will pan out. So yes, some sanders supporters will be badgered
into clinton, but I think that's a small percentage, people inclined to support hillary already
support her, most of sanders voters are the castaways. Sorry, can't go along with the endless
drone strikes of the 5th term of GWB. Hillary is not the peace candidate.
MyLessThanPrimeBeef ,
June 1, 2016 at 2:17 pm
Clinton voters – those not in the establishment, that is – seem to be the silent type.
You don't see them here or hear them on radio often (just yesterday, on the local public radio,
almost all the callers were for Sanders – it made me wonder if Hillary would lose 0 to 100 in
the upcoming California primary).
aab ,
June 1, 2016 at 7:34 pm
Clinton voters are the small amount type. She has only "won," even in the states she did did "win," by massively suppressing the vote.
She hasn't even held onto her own voters from 2008, even in conservative states. Her "big wins"
in the South were with much smaller numbers of votes cast. There are people who genuinely want to vote for her. They were not enough to win the Democratic
primary without massive suppression AND theft.
Lambert
Strether ,
June 1, 2016 at 3:07 pm
Some will, some won't. How many is to be decided. If Sanders gives his list to the Democrats, I will certainly vote for Trump. I would rather
have Götterdämmerung immediately, then have it play out.
ScottW ,
June 1, 2016 at 8:13 am
The problem for Hillary is there is no indication the email scandal narrative will ever
improve to the point of improving her untrustworthy numbers. The best she can hope for is the
FBI stating it will not recommend an indictment which will merely confirm the public's correct
perception that the power elite are treated better than the rank and file. Hillary cannot unring
the Inspector General's conclusion she circumvented FOIA and federal record keeping laws. She
cannot undue the fact she maintained thousands of classified records, along with 22 top secret
documents on the private server. She cannot change the fact she hid her use of the private server
from the public and only disclosed it when caught by the Senate Committee investigating Benghazi.
Everyone who pays attention to the facts is disgusted by her misconduct in this matter.
Loyal Hillary supporters are the only ones willing to buy into the unbelievable rationales
floated the past year. For the rest of us, everything we learn merely confirms what we previously
thought. That Hillary cannot be trusted, wants to avoid public scrutiny and believes she is above
the law. Everything we learn about the email scandal is much worse than initially portrayed by
Hillary.
As the article states–this is all on Hillary who for over 1,200 days intentionally used a private
email basement server despite being told not to do so. She had numerous opportunities to right
her wrongs, but insisted on doing what she wanted to do because that is always how the Clintons
operate. There is no way Hillary, Bill and her team of misfits should be allowed within a hundred
miles of the oval office. Sadly, Donald will win if Hillary remains the Democrats candidate of
choice.
the blame/e ,
June 1, 2016 at 8:19 am
I believe we can plainly chart the "decay path" (lovely phrase BTW), of Hillary Clinton's failed
attempts to secure the highest office of the land just by looking at pictures of Monica Lewinsky
from 1998 until today.
The true decay path would have been the trajectory Bill Clinton's baggage would have taken,
from the White House to the South Lawn, had Hillary Clinton thrown the bum out in 1998.
I have always been confused by which woman Bill Clinton was lying straight faced about when
the then President of the United States declared before the whole world: "I did not have sex with
that woman."
At the time of the scandal, Hillary Clinton was First Lady of the United States of America,
the most powerful women in the free world. Imagine what her standing-up for women everywhere would
have had, let alone upon the current states of "family values" (so-called)? Imagine the affect
her standing up for herself would have had upon the women of the world?
Instead she used her power to play the "little woman," when she could have assured herself
two (2) terms as President of the United States, even guaranteed herself the title of being the
first Empress of the United States of America if she had wanted.
As it stands, Bill Clinton's legacy is not how he ruined one woman, but two (2).
twisted ,
June 1, 2016 at 9:38 am
I'm sorry, mate. I have to disagree.
Who Mr Clinton shags is his business and his wife's*. Hillary came out smelling like roses.
She got sympathy as devoted wife whose hubby screwed around and, in my view, damn near universal
understanding for her decision to honour her marriage by staying with her hubby.
I think her problem is that, in routing official traffic through a private mail server,
she's tried to avoid records of her work (as a public official!) ever becoming available to the
public. It looks, at the very least, like she's trying to hide something and it's a demonstration
of breathtaking contempt for the very people whose votes she's now asking for.
That the Democrat brains trust knew all this and still decided to try and coronate her
leads me to suspect that they've become completely divorced from reality. Any halfway credible
candidate would trample over whoever the R's pick.
* How classy, not to mention politically astute, would it have been if the R's could have kept
their frothing to themselves and made a single public statement along those lines and got on with
the business of serving their constituents.
Cry Shop ,
June 1, 2016 at 11:36 am
If he shagged under the legal age limit girls, traveled on a jet which was used in slave
trade of underage girls, etc; then it isn't just his business, it's a criminal matter. If Mrs.
Clinton enabled, and/or aided and abetted, then she could be facing criminal charges.
The interesting thing
is Jeffery Epstein has hidden cameras on both his plane and all over the US Virgin Island private
pedophile reserve he ran for politicians and high level government officials. The overseas
press is reporting he blackmailed his way out of Federal Charges. Was Bill part of that blackmail?
the blame/e ,
June 1, 2016 at 1:08 pm
Only if his private business remains private.
Yves Smith
Post author ,
June 1, 2016 at 4:36 pm
In a word, no.
Bill is a sexual predator. His affair with Jennifer Flower was consensual. But starting
from when he was Governor, there is a long list of credible allegations of him engaging in sexual
harassment (extremely aggressive come-ons with women he had just met, often women who were state
employees or Dem consultatnts), including a rape allegation by Juanita Brodderick. We've even
had a reader in comments say that when Bill Clinton visited a friend, he asked their college aged
daughter when he was alone with her if she wanted to ride in his car and give him a blow job.
DC contacts confirm the city is rife with stories like that.
reslez ,
June 1, 2016 at 1:43 pm
> Hillary Clinton was First Lady of the United States of America, the most powerful women in
the free world
Most powerful woman in the world? Somebody's wife? Lord I hope not. Surely there was a female
head of state or a Supreme Court Justice or something with better claim.
Skippy ,
June 1, 2016 at 8:25 am
Clinton's… poster children for Flexians… Disheveled Marsupial… at least the loon pond and wing
nutters are open about their insanity… something about the inelasticity of beliefs…
Northeaster ,
June 1, 2016 at 8:25 am
If there were an equal rule of law in this country, we would not even be discussing
this issue as Clinton would have already been indicted by now. The recent Wikileaks release shows
exactly how complicit Clinton is, was, and will always be, a truly evil human being.
Chibboleth ,
June 1, 2016 at 8:50 am
As strange a thing as this is to say, I find myself wishing that more journalists had experience
in IT security. I do have such experience, and from what I can see most people really don't appreciate
just how totally, ludicrously irresponsible it is for that server to exist. Talk of it having
been "secured" by some lone IT contractor is ridiculous on its face. I wouldn't run a homebrew
email server, and I am basically not worth hacking – very much unlike the US Secretary of State.
Seriously, think about it. The Secretary of State had a private email server which seems
to have been widely known about within the State Department and other people in government who
had dealings with Hillary Clinton. There's really no question as to if that thing was hacked –
you can absolutely bet your ass that multiple foreign intelligence services have been
in and out of that thing.
That's what's really galling to me – even by Hillary's own stated standards, what she did
with her email is orders of magnitude worse than what Snowden did. But it's Hillary Clinton, so
it gets handwaved by the Democrats' long practice at assuming a Clinton scandal is overblown nonsense.
voteforno6 ,
June 1, 2016 at 9:46 am
To be fair, a large number of Clinton scandals have been overblown nonsense…I think Democrats
have gotten so used to fighting off those attacks, that they just assume the same when something
real pops up.
As for the irresponsibility of maintaining that homebrew server, I've tried to explain on other
forums how it was actually worse than getting it through a commercial provider, or even what Powell
did. The responses were usually along the lines of "it wasn't hacked." Sigh.
washunate ,
June 1, 2016 at 10:20 am
Agreed. But that's the thing. These events aren't about the substantive IT issues. They're
just part of concentration of wealth and power; the authoritarians in both major parties are control
freaks who work together in bipartisan cooperation. Laws are for the little people. The ruling
class is above the law. The role of the media is to enforce this system, not challenge it.
That's why people like Chelsea Manning, Edward Snowden, Thomas Drake, Jeffrey Sterling,
John Kiriakou, Joe Wilson, and so forth are persecuted by the government while people like Clinton
(and Petraeus, Novack, Libby, Bush, Cheney, Obama, Biden, etc.) are protected. It has nothing
whatsoever to do with the merits of events.
Just as one example, here's the 'ole Gray Lady serving as
dutiful stenographer
for Nancy Pelosi herself, the Democratic Speaker from San Francisco, supposedly one of the
most liberal parts of the entire country, explaining that the law doesn't apply to people in power.
Peter Bernhardt ,
June 1, 2016 at 10:21 am
Agreed. I've worked in IT and software development for years and agree that her provision
of that server doesn't meet the most basic requirements for security. Also, I work for a rather
large company with a sizable federal contract and, if you haven't contracted with the government,
you can only imagine the levels of security they impose upon their vendors. Two-factor authentication,
encryption at rest, kernel hardening and on and on. Not only do you HAVE to do these things if
you want to do business with the government, they bring in teams of their IT people to audit you.
And it is not perfunctory in any way. They take InfoSec very, very seriously.
Rule no 1 of security: a system is only as secure as its weakest link. Imagine how anyone who
abides by the strict security requirements necessary to work in or for government feels when learning
about Clinton's cavalier disregard for the law? Her arrogant refusal to play by the same rules
as the people she is supposed to lead? In fact, her behavior put the entire system and people's
lives at risk.
She fails the most basic test of genuine leadership. Yet another important example of why she
is unfit to be president.
voteforno6 ,
June 1, 2016 at 10:51 am
The Clintons certainly do have a habit of pushing into that gray area between what is legal
and what is acceptable.
Bryan ,
June 1, 2016 at 2:19 pm
It's not the lack of IT security experience that's keeping journalists from writing about it
more critically.
Lambert
Strether ,
June 1, 2016 at 3:11 pm
Chuck Todd, of all people, gets this right (paraphrasing): "When I think of convenience, I
don't think of running an email server in my house."
Even a WiFi router is too much…
Jack Heape ,
June 1, 2016 at 8:55 am
Good article. The IG's report was the crack in the dam and I believe soon the whole sordid
mess that Clinton has created for herself will come flooding through. I think Bernstein's messaging
was to the Democratic party as a whole that its time to pursue other avenues. And there are other
rumblings as well. Yesterday in the
WSJ was this op-ed which made many of the same points that were made here, as well as discusses
the fallout if Clinton loses the California primary. I also think that the Dems are not only just
worried about the nomination now. The IG's report clears a path for hearings by the Republicans
against Clinton after the election.
Bubba_Gump ,
June 1, 2016 at 8:58 am
What pisses me off to no end is the fact that the party and media are unwilling to pivot to
Sanders. He could win the general, perhaps more easily that HRC. But Sanders is also to blame
on this for being so completely inflexible that he can't make the right friends.
Roger Smith ,
June 1, 2016 at 9:31 am
That is a positive for him generally though. These people don't want "friends" they want others
who are willing to play ball. Sanders says GTFO, enough is enough.
The truth was never going to sit well with these selfish fools and their sycophants.
RUKidding ,
June 1, 2016 at 11:48 am
I agree. Sanders has nothing to gain and a lot to lose by "making nice" with the Dem establishment.
Why make nice with them? They are the problem, not the solution. That's a mainstay of Sanders'
campaign.
NotTimothyGeithner ,
June 1, 2016 at 12:33 pm
Sanders is the ranking member on the budget committee and has been the chair of the veterans
affairs committee. Those are plum jobs which demonstrates the Democratic Party is not a political
party by any normal standard because you don't give the best jobs to people outside the party
unless you need to.
The Clinton fanaticism isn't about Sanders. They believe they need Clinton. An active DoJ
might be a threat. A few have backwards ideas about politics. Some simply did the believe Sanders
when he said Hillary was weak, but with a Gabbard in play, many Democrats can kiss their ambitions
good bye if Sanders wins.
sid_finster ,
June 1, 2016 at 12:48 pm
I've said it elsewhere: Sanders is unacceptable to the DNC because a Sanders win would render
the DNC networks, influence and fundraising abilities irrelevant overnight. The DNC would no longer
be gatekeepers. You can win without them. Thus, Team D does not fear a Sanders defeat, and they can live with President Trump. In fact,
that would represent an unprecedented fundraising opportunity. But from the Team D perspective, a Sanders victory must be prevented at all costs.
FluffytheObeseCat ,
June 1, 2016 at 1:16 pm
How the hell could Sanders "make friends" with members of the Democratic Party elite? He is
blowing up their revolving-door-greasing funding model. Running as effectively as he has with
almost no lobbyist money? No major corporate donors to speak of? What can he offer them, except
unpleasant changes that negatively impact their careers?
Jen ,
June 1, 2016 at 5:01 pm
Depends on whom one includes in the elite, and what one means by negatively. Are the super
delegates who aspire to be on the ticket in November running for their own amusement? If so, I
suppose they don't care whether they ride on Sanders coat tails or sail off the cliff on whomever
the elite deem the nominee should be. Would you rather be the Senate minority leader, or the Senate
majority leader. House minority leader, or speaker of the house? I have no idea where the power
lies here, but I admit that am curious about Pelosi's non stance, and Reid's pivot, with almost
unseemly hast, from saying Sanders needed to get in line, to that he would be more powerful when
he returned to the senate, to saying: "hands off." And sandwiched in between saying no way in
hell would he tolerate a senate vp coming from a state with a Republican governor. Assuming he
has any actual say in the matter, that would torpedo the preferred sop to the Sandernistas: Warren.
Reid is of course gone either way, but Schumer is next in line is he not? What do I know, but
it's entertaining to speculate.
Antifa ,
June 1, 2016 at 9:01 am
When Carl Bernstein opens with, "The implications of all of this are that Hillary Clinton
did not want her emails subjected to the Freedom of Information Act or subpoenas from Congress.
And that's why she set up a home-brew server" he is only telling half the truth, and is framing
the conversation around her supposedly innocent desire for a little privacy. Pretty good lying,
Carl.
But this is definitely putting a lot of spin on the ball, because the other half of the
story is the reason WHY she wanted to avoid FOIA and Congressional scrutiny. The answer is: so
that between her and Bill she could sell her office to the highest bidders, which the FBI is quite
prepared to prove, or if denied that chance, to "leak like crazy" to the media. Good
Lord, the FBI is even considering treating the Clinton Foundation as a Racketeering Influenced
Criminal Organization. There's no chance this is going to just go away.
Given this likelihood of the full story going public in any case, given the completely independent
Judicial Watch investigation, and given that the Russian media actually printed Clinton emails
in their newspapers back in 2013 - and claim to have 20,000 of her emails in hand that they can
release at any time - there's no practical path for the White House or DNC to stonewall or to
clamp a lid on this affair, and roll Hillary across the finish line to the nomination on a hospital
gurney if that's what it takes.
The same problem exists with pardoning her prior to prosecution - it won't silence FBI leaks,
or the Russians, or Judicial Watch, or whomever else wishes to leak the full truth to the morning
papers. The public will be fed a steady discovery of exactly what Obama's unconditional pardon
actually covered. It will be a magical expanding pardon - starting out as a balloon but growing
within months to the size of the Hindenburg before burning to the ground along with Obama's legacy.
As to what the White House knows that they aren't leaking - that would be the devastating damage
Hillary's loss of state secrets has done, none of which can ever be shared with the public. If
covert CIA operations have been ruined, if agents have been exposed, arrested or killed, if someone's
name has gone up on that wall of heroes in the CIA lobby because of Hillary Clinton, the CIA will
not forgive, ever. Nor will they tolerate letting her gain the Oval Office, where she can hire,
fire and otherwise direct them. The NSA is known to be well aware of her public corruption of
the SoS office, and of the wholesale money-laundering of the Clinton Foundation, which Charles
Ortel is now meticulously publishing in the form of PDF files covering every separate arena of
corruption ongoing over there. They don't want her as their boss, either. Steps can be taken to
prevent that from happening, with no risk of exposure.
Hillary's got no way out of her legal troubles other than suddenly checking into a hospital
and being declared terminal. Everyone will hold off, at that point. Until she fails to pass away
by the weekend, at which point her legal nightmare resumes its course. So no, she's got no way
out of what's coming, and no actual path to the White House.
All of which leaves the Democratic Party with only two options:
a) get her nominated at the Convention even if it's by just one vote, but hand pick her VP
for her so that person can be the real candidate when she drops out well before November. Problem:
Hillary has spent several years scorching the earth for other Dem candidates. Nobody has any organization
or resume to suddenly step into her shoes and expect anyone to vote for them in November. If Kerry
is their only choice, please don't bother.
b) induce Hillary to drop out before the Convention, and let the Convention be brokered. Don't
elect Bernie Sanders on the first round, and after that you're home free - keep voting, round
after round, until delegates finally accept your Hillary replacement which isn't Bernie Sanders.
Oh, it will be a raucous, riotous event, but it's all above board, and by the rules. Caution:
this course of action carries a high risk of nominating Bernie Sanders.
shinola ,
June 1, 2016 at 11:24 am
Just speculation, but by keeping quiet the NSA/CIA/FBI could be "investing" in blackmail futures.
The ghost of J. Edgar may still be lurking somewhere in D.C.
Antifa ,
June 1, 2016 at 11:50 am
If it is, it's wearing a dress . . . he was fond of floral prints over tight girdles.
Ping ,
June 1, 2016 at 1:02 pm
The Clinton Foundation, which controls billions in an opaque labrynth structure and funded
by war profiteers, crass political operatives and those with corrupt cynical motives, functions
like the treasury for a supra national shadow regime.
When this story finally unravels, and it will, it will make WaterGate, IranGate look like a
kiddy party.
Code Name D ,
June 1, 2016 at 1:20 pm
I am inclined to agree. Even the mere mention of RICO might mean the FBI is stalking bigger
game – the Clinton Foundation? The Democratic Party itself?
Ping ,
June 1, 2016 at 2:22 pm
The Libya correspondence between Blumenthal, a Clinton Foundation employee who also representes
a security firm evidently poised to be contracted there and HC is an example.
Given all these wheeling and dealing interscections between SOS Hillary and the Clinton Foundation's
unwholesome donors
and the extraordinary lenghts to privatize correspondence (and not fully turn over Blumenthal's
hacked emails to her) there is no other way to reasonably explain the stunning depths.
Especially given HC's interventions have resulted in lawless no man's lands…… hugely profitable
for donor defense contractors or those poised to acquire resources, weaponry (Lybia).
James Levy ,
June 1, 2016 at 4:37 pm
Cheney et al. got away with the no-bid ultra-corrupt Haliburton contracts in Iraq, so there
is a precedent for this kind of naked thieving going unpunished.
Ping ,
June 1, 2016 at 10:37 pm
The many examples of gross corrupt war profiteering facilitated by high office holders going
unpunished or rewarded must be emboldening.
But in my view, setting up a foundation with opaque accounting and trotting around the world
soliciting huge donations while SOS with a private server outside government channels and FOIA
is a new level of organized criminal archetecture.
Ping ,
June 1, 2016 at 10:54 pm
Rewarded or unpunished war profiteering facilitated by high office holders must be emboldening.
But in my view, setting up a foundation with opaque accounting then soliciting huge donations
from donors specializing in political upheaval and military conflict while globe trotting as SOS
using a private server outside of government channels to circumvent FOIA is a new level of criminal
and is essentially a Clinton Foundation serving as treasury at the helm, with presumed HC POTUS
subversively enforcing a shadow supra national archetecture.
Quantum Future ,
June 1, 2016 at 5:32 pm
To Code Name D – One can watch a program on Netflix about Hayden and the CIA realizing it has
gone too far. What may you ask? Well well has the country done since JFK? Selling out to
the bankers affects intelligence too. It just takes awhile for our species to wake up.
And despite the self admitted overeach directed by corrupt politicians I do not find wasting
(literally as in the slang term of the word) funny. This is an issue I have with bombadier Kissinger.
Energy policies and struggles matter. But Clinton always would say "well that policy is ten years
away" regarding energy policy. So when the Russians play a hot card (but overplayed its hand)
because the West in its corruption didnt move faster, lets blame Russia.
These are the kinds of things that kill and cause increased casualties in intelligence. Think
nobody woud notice?
As always, increase competitors in energy, alternative and others. Then Russia can fuck off
as it tries to raise prices. But that requires the rule of law and not selling the country down
the river. Just getting down to some brass tacks here. I get real pissed beause not only can this
get my countrymen killed, along with me but the other reason is some of us have had to do the
job that government is paid do to. I wont expand.
Code Name D ,
June 1, 2016 at 9:55 pm
Ah, I am starting to see the "RICO mention" starting to go mainstream on you-tube. I am starting
to think this was a preemptive leak to try and discredit the real charges should they come out
later. We have yet to see any evidence that would support this and it doesn't fit with the current
noise.
Anne ,
June 1, 2016 at 9:03 am
One has to wonder just how many red flags have to be waved in their faces for it to dawn on
them that, hey, maybe Hillary Clinton isn't – and never was – the right person to pass the baton
to.
Seems to me that if there was some kind of bargain struck in 2008 (you concede and enthusiastically
endorse me, and I'll reward you with a plum job from which you can launch a presidential campaign,
and I'll throw in the full support of the DNC and the superdelegates), there were multiple points
along the way where it was clear Clinton was putting all of that in jeopardy. She made some terrible
decisions, and instead of pulling back, she doubled down.
Are we to believe that no one from "the White House" ever took her aside or suggested that
while she may be living a life of entitlement, there was that little thing known as an election
that was going to depend on public perception of her actions and decisions, and she might want
to consider that, promises notwithstanding, she was playing a fool's game if she bought into her
own invincibility and inevitability?
But maybe "the White House" bought into it, too. How else to explain why, in spite of every
kind of assistance it's possible to get, some of it of questionable legality, the anointed candidate
has done nothing but drop in the polls. A little-known, 74-year old Democratic Socialist from
a teeny-tiny state enters the race polling within the margin of error, and a year and hundreds
of millions of small-dollar donations later, is in a position to deny Clinton a pledged-delegate
nomination.
How large does the writing on the wall have to be over there at "the White House?" How myopic
are these people, anyway? Did their eyes all of a sudden just pop open and they can only just
now see what has been obvious for some time?
I'd like to feel bad for them, but the phrase that comes to mind instead is "hoist on their
own petard."
This whole thing is such a massive exercise in selfish indulgence the only emotion these people
deserve is our anger, which we should put to use by denying them the offices and power they seek.
Benedict@Large ,
June 1, 2016 at 9:17 am
What I don't get here is, if the White House knows she's such a terrible candidate, why do
they want to put her in a real cat fight with Trump? Are they so sure (as Bernstein suggests)
that Obama will be able to carry her across the finish line in November?
And that bring up another point for all you "feminist" Clintonistas. Wasn't the whole point
of the "first woman in the White House" thing to show that women can do it alone? That they don't
need men carrying them around all the time to be successful? Well what's up with your candidate?
I have never (in my 65 years) ever seen anyone (woman or man) need more help from other people
(mostly men) to gain the success they seek. At every single turn in this campaign we have Ms.
Clinton needing someone else, someone MORE, falling on their sword for her. Because left on her
own, against a freaking socialist, for Christ's sakes, all she has been able to do is F@ck up.
A FIFTY POINT LEAD, gone. Wasted. Nothing to show. And this is what you want as feminism's representative
in the White House? Shame on you.
Kurt Sperry ,
June 1, 2016 at 11:19 am
As others have pointed out, all that is required of Hillary at this point is to secure the
nomination. Nothing else really matters. Once Sanders is removed from the picture, her job is
done. A President Trump would be a minor setback from a partisan perspective and a Democratic
Party in opposition to a bogeyman like Trump would experience an amped up version of the unifying
effect it enjoyed in opposition to GWB. It really could serve to paper over the seismic ideological
rifts widening within the current party. Four years in opposition would be a very small price
to pay for averting what would be the existential threat to the party's core that a President
Sanders would represent.
I would think the prospect of a President Trump wouldn't bother the party's insiders much if
at all. The prospect of a President Sanders on the other hand would or could be a crushing and
final defeat for nearly everything the current Democratic Party stands for: a giant and hugely
lucrative influence peddling racket making everyone near its center into extremely wealthy individuals
with patronage jobs waiting for them and their families within the concerns of the people who
are bribing them. President Trump by comparison would be a godsend.
RUKidding ,
June 1, 2016 at 11:51 am
Bingo! Nailed it.
Most of the DLC establishment could find it easy enough to "live" with a Trump Presidency.
Just like Lil Marco Rubio, they'll easily bend their knees to kiss Trump's heiney and make deals
with him. What's it to them, after all?
Sanders? That's a horse of a different feather. Sanders isn't interested in them bending their
knees and kissing his heiney. And THAT's a huge problem for the 1%.
Dig it.
polecat ,
June 1, 2016 at 12:20 pm
….."fool me twice…I…I won't get fooled again !"…..
the 2016 voter's motto…..
the DLC is toast……Burnt toast !!
sid_finster ,
June 1, 2016 at 1:24 pm
Money shot.
TheCatSaid ,
June 1, 2016 at 1:53 pm
I agree with your assessment. Trump would play the game differently, but he could be counted
on to place the game.
Sanders shows that he knows and respects some of the rules of the game, but more of the rulebook
would be up for grabs and the outcomes perhaps less predictable for TPTB.
There are also wildcards–impeachments, assassinations, health issues, pardons, etc.
dingusansich ,
June 1, 2016 at 1:56 pm
In that scenario Hillary wins the nomination and loses the election, Obama pardons her
to head off (in his telling) partisan persecution and looks noble (to the credulous) standing
up for her, clearing the way to elbow in on the Clinton network for the-haven't you heard?-Obama
Foundation. And the grift goes on.
Could be. We'll never know, because we're not at those tables. But could be.
Lambert
Strether ,
June 1, 2016 at 3:14 pm
Yep. Sanders is the real enemy, not Trump.
Angry Panda ,
June 1, 2016 at 9:39 am
1. Somewhat tangentially. I don't know how the 2007-2008 crisis looked to people on the "outside",
but to many of the guys in the trenches the world "blew up" on or about July 18, 2007, when the
two Bear-affiliated subprime funds hit a wall and the credit bubble literally stopped
the next day. Within a month, the SIVs got obliterated and it was downhill from
there.
Yes, it took a while to get to Lehman/AIG. There was the Bear thing, the commodities super-spike
in the summer of 2008, a few other notable items. But again, by the time Lehman came around the
view in the trenches was that the world had already been blowing up for over a year, and now "main
street" finally took notice. Really the one surprise was that the Fed let Lehman go (presumably
as a live experiment, or perhaps simply out of stupidity), and then the CDS markets went haywire
for awhile (hence AIG).
Not 20%-30% probability of "something bad happening". Rather, 100% probability of "something
bad" having already happened and now we're just watching the explosion in slo-mo.
2. Incidentally, this is pretty much what we're seeing with the Clinton campaign. You've already
seen the campaign "blow up", in a way, because Sanders didn't go away in February, or March, or
April, etc. Part of that was Sanders, part of that was general discontent – but part of that is
also Hillary not being able to put away an opponent that is so way out of the Democratic party
mainstream. Because the email thing, and the speeches thing, and the neo-liberalism thing,
whatever. Bernstein's "leaking" makes clear that as far back as February Obama's guys in the trenches
said – hey, we just saw the Bear funds blow up, and this thing is going to end badly one way or
the other. We don't know exactly how bad, but bad. Which is bad for us…
3. I actually think that this signalling is not about a specific thing. It's a more of a general
– you're not doing what you're supposed to do, and your messing up makes us look bad type of thing.
Today it's the emails, tomorrow it's whatever else – there are so many issues with the campaign
(and the candidate) that you could have Bernstein deliver a new speech weekly if not daily. The
overall message seems to be, "you're blowing up, do something, right now", and I would bet they've
been hitting that theme for months in private (the current leak to Bernstein being a sort of a
– you don't want to listen to us in private, here's something in public, now pay attention).
4. Honestly, I would be shocked – shocked! – if the FBI or the DoJ did anything to Hillary
Clinton on this email front. For one, let's dispense with any talk of "autonomy". Whom does the
FBI director report to? Have there been any instances in the past when the White House "influenced"
the direction of the FBI investigation? And what has this administration specifically demonstrated
time and again vis-a-vis leakers (from the standpoint of intimidation)? Or compartmentalizing
information to prevent such? I'm not saying they'll necessarily get away with it, but certainly
they can think that to themselves, at least through November.
The basic idea is that Obama and his people have put their chips on Clinton. For whatever reason
– political, personal, does not matter. They probably did so with a heavy heart (or some such),
but they did it. Now they're freaking out, justifiably, because they literally cannot, cannot
afford to have the Clinton campaign blow up right at this point (after November, sure, why not).
You think these people won't shut the FBI down if they feel they have to? Of course they
will. It will look dirty, of course, but it's – in their minds – probably better than the alternatives,
unless they want to go out with a real bang blowing up both Clinton and the DNC and ending up
as semi-pariahs among a good portion of the DNC donor base for the rest of their lives…which I
doubt.
Eh. The train wreck continues to unfold in slow motion, except that I think this time she actually
has a more than slim chance of making it to November and making it in November (after
which point, let the scandals lottery commence, to the endless delight of Fox News and the like).
Brindle ,
June 1, 2016 at 10:25 am
Tend to agree. Clinton will likely win in November. Trump's potential voter base is less in
number than Clinton's. She has a built-in demographic that, unless she botches the debates totally,
should ensure Trump's defeat. BTW I despise the Clinton's and everything they stand for.
Dikaios Logos ,
June 1, 2016 at 11:03 am
The 2008 Financial Crisis narrative I tend to follow is that Bear and Lehman had the most enemies
and so were the most convenient scapegoats/sacrifices to hand to an angry public. The reality
of these big crises is that the banking system fails absent absent government intervention and
so the saving of the others was a CHOICE.
Likewise, at some point the professional Democrats and the affiliated parts of the organism,
including its funders, might at some point view cutting the umbilical cord to the Clintons as
necessary for their own survival. I'd keep an eye out for that!
washunate ,
June 1, 2016 at 11:23 am
Well said.
FWIW, on the outside, it seemed like things were very bad, so bad that it felt like
the political system was going out of its way to try to cover things up and tell people not to
worry their pretty little heads and other almost comically defensive approaches. And not just
in finance specifically, but all over our system, secrecy and ignoring reality seemed to permeate
our public leadership. A willful blindness at a systemic level – because after all, most highly
paid professionals depend upon the system; nobody wants to rock that officialdom boat much.
I have also been interested by some of the revisionist history that starts the GFC in 2008
with Lehman, rather than Bear Stearns in 2007, and more generally with the notion that the 2007-2009
crisis was a unique, isolated event rather than part of a multi-decade long process, that slow
motion train wreck, as if the kind of inequality that leads to systemic crashes magically appeared
out of nowhere in 2006.
Quantum Future ,
June 1, 2016 at 5:51 pm
To Washunate – I really appreciate the wise commentary, all of the time. The primary issue
is who controls the currency. A private bank like the Fed who is the ultimate lobbyist or the
the public, basically treasury. Our founders new both can and will fall prey to corruption but
out of the two choices public currency (a form of energy of all our labor) is best.
Central banking model is a form of conquest. As an empire it succeeded globally. Now such have
to own the empire and its fallacies. Including buying politicians. The rule of law must be restored
and the currency restored to public domain (despite its flaws).
washunate ,
June 2, 2016 at 12:05 pm
Thanks for the kind words. One of the things I really like about what Yves has done at NC is
create a space for those inside and outside as panda put it to share directly with each other,
without the filter of technocrats and pundits in the middle who portray an air of expertise, of
rigorous intellectual curiosity about and understanding of the system, yet seem to possess neither
detailed knowledge about things 'in the trenches' nor about the perception of those things by
the general public on 'the outside' of the bubbles of affluence and power in our society.
The general public has known for some time to be leary of everything from bankster pronouncements
to econ PhD jibberish to warmongering buffoons. But the Serious People of our system act like
every problem is a big surprise. Because of course they are protecting the looting – or at least
enabling it through various kinds of navel gazing triviality – rather than doing anything meaningful
about it.
I heartily agree that rule of law isn't some quaint notion, purity test, or luxury. It is the
foundational element of a society that aspires for what are broadly held values (outside DC) like
freedom, justice, mercy, and equality.
TheCatSaid ,
June 1, 2016 at 2:04 pm
1. Economy: "Not 20%-30% probability of "something bad happening". Rather, 100% probability
of "something bad" having already happened and now we're just watching the explosion in slo-mo.
"
Absolutely everyone I know who has established credibility with me in a wide range of spheres
agrees with the 100% figure. Timing: late 2016, early 2017 at the latest. With more far-reaching
impact than "usual" in a Great Depression or GFC.
Lambert
Strether ,
June 1, 2016 at 3:18 pm
> Honestly, I would be shocked – shocked! – if the FBI or the DoJ did anything to Hillary Clinton
on this email front
The FBI is an independent power source because Comey has his own files, just like J. Edgar.
Lynch is another matter.
Yves Smith
Post author ,
June 1, 2016 at 4:52 pm
Did you see by "something bad" I meant a Japan-level unraveling? I wasn't talking about recession
or a bear market. I was talking about a financial crisis, but a slower-moving one than we had.
And if you look at my posts from the time, I was very clear in chronicling the four acute phases
of the crisis: July-Aug 2007, December 2007, Bear and Lehman, as Very Big Deals. I was particularly
critical of the "Mission Accomplished" mode the officialdom went into in Feb-March 2008 and April-July
2008.
TheCatSaid ,
June 1, 2016 at 6:01 pm
I think you've underestimated how bad the next "something bad" is going to be.
Quantum Future ,
June 1, 2016 at 6:30 pm
Yves – Time hss proved you wise. Japanafication is exactly what has been unfolding. And
according to Forbes and the Fed, 48% of the population having less than a grand in savings means
the US is near third world. One can buy Pop Tarts in third world countries also.
But there are wealth holders still spending (albeit less than two years ago) based on the stock
market or real estate rentals. Both are subject to harsh correction and that will have some knock-on
effects in labor. Not as bad as some may think but some.
The real danger is geopolitics. And this bitch that thinks she is queen has no issues literally
seeing 1/3 of the global population dying to escape her crimes. Think of what a rapist does to
a rape victim many times. Strangle that woman so she doesnt indict you. Yeah, it is that bad.
But there are some form of tech that will end any world war quickly. Stuff of science fiction.
America's competitors should think twice, or such may dissapear. Literally.
But as Americans we do know the corruption stinks to high heaven and we are doing something
about it. So pray, war does not escalate. Mankind is literally at the end of our evolution and
defeating classic death. We need (some is happening and is great) more.of that focus and marketing
of it and less global police, empire crap.
Tom ,
June 1, 2016 at 9:40 am
Regarding the Clinton Hairball (or, Dead Woman Walking)
Just read the Cheryl Mills
transcripts and two things jumped out at me. First, on pages 104-106, the Judicial Watch lawyers
asked her about Platte River Networks and Datto, Inc. This
McClatchy article gives a long version, but the short version of what the big deal is this:
Clinton Executive Service Corp. (CESC) had Hillary Clinton's private email server physically
moved to Platte River Networks after she left office in 2013. Platte River is an IT services company.
They are headquartered in Colorado but also have a location in New Jersey, which is where Clinton's
server ended up. Platte River bought a backup device from another IT services company called Datto,
Inc, specifically to back up Clinton's server. CESC requested that Platte River do the backup
on site, and Platte River thought that's how they set up the Datto device. However – and this
must have been Clinton's worst nightmare x 10 - unbeknownest to CESC and Platte River, the backup
server accidentally synced with another off-site server belonging to Datto for two years before
anyone realized it. And here's the kicker: this off-site Datto server had all of Clinton's
30,000 or so work-related and 30,000 or so personal emails.
And the FBI found out about it and seized that Datto server and hit the jackpot of all time!
Now, in the Mills transcript, Judicial Watch dropped the questions to Mills about Platte River
and Datto pretty quick, which suggests to me that they already have some other juicy witnesses
to question and they merely tried a few quicky questions to Mills to see if they got lucky. But
to me this is the nuclear bomb that has already gone off – the shock wave just hasn't reached
us yet. I would imagine that Hillary's personal emails may be a treasure-trove relating to Clinton
Foundation Activities and all the related shenanigans
Ortel is investigating, as mentioned several
times on Naked Capitalism.
On page 138, another item of interest in the transcript appears. Mills is asked about a July
26, 2011 email chain where Clinton jokes with a staffer named Nora Toiv that it was weird Clinton
no longer had Toiv's Gmail account and Clinton wondered, "so how did that happen. Must be the
Chinese!" Here's the
email on Wikileaks.
Keep in mind, this is just a month or so after several warnings from the DS cybersecurity about
private email accounts, including this June 28, 2011 cable, in Clinton's name, warning of specific
threats to Gmail accounts of U.S. Government employees. From page 34 of the
OIG Report :
On June 28, 2011, the Department, in a cable entitled "Securing Personal E-mail Accounts"
that was approved by the Assistant Secretary for Diplomatic Security and sent over Secretary
Clinton's name to all diplomatic and consular posts, encouraged Department users "to check
the security settings and change passwords of their home e-mail accounts because of recent
targeting of personal email accounts by online adversaries."141 The cable further elaborated
that "recently, Google asserted that online adversaries are targeting the personal
Gmail accounts of U.S. government employees. (my emphasis) Although the company believes
it has taken appropriate steps to remediate identified activity, users should exercise caution
and follow best practices in order to protect personal e-mail and prevent the compromise of
government and personal information." It then recommended best practices for Department users
and their family members to follow, including "avoid conducting official Department business
from your personal e-mail accounts."142
Granted, Clinton could have been just having a laugh in the email exchange with Toiv, but it
doesn't help her case. Especially since we know of at least 15 cyberattacks on Clinton's email
server just from publically available information, including attacks from IP address in China,
Republic of Korea and Germany (and possibly Russia, if you believe the Guccifer story).
Sorry for being so long-winded.
TLDR: Clinton is a dead woman walking. And Abedin, Sullivan and others have yet to testify!
Steve H. ,
June 1, 2016 at 10:05 am
– the backup server accidentally synced with another off-site server belonging to Datto for
two years before anyone realized it. And here's the kicker: this off-site Datto server had all
of Clinton's 30,000 or so work-related and 30,000 or so personal emails. And the FBI found out
about it and seized that Datto server and hit the jackpot of all time!
Needs more exclamation marks.
jackpot! of! all! time! -- ! -- !!!!!!!
Tom ,
June 1, 2016 at 11:43 am
I know. And as an aside, another fact that has been glossed over repeatedly is that Hillary's
personal email server apparently wasn't new when she had it installed in her basement. Oh no,
the server had already been in use as President Bill Clinton's personal server before that. God
only knows what kind of incriminating stuff is on there belonging to him. No wonder he suddenly
looks like he's aged about 30 years!
MyLessThanPrimeBeef ,
June 1, 2016 at 2:07 pm
When did the FBI seize it?
No indictment since then? Why the delay with the jackpot of all time!!!!!?
Can't be that hard to go through 30,000 emails.
Tom ,
June 1, 2016 at 2:21 pm
Probably because it is the Yellow Brick Road winding its way through years of Clinton relationships
with the richest, most powerful and influential people in the world. And we will probably never,
ever catch more than a fleeting glimpse of whatever is behind the curtain.
Harold ,
June 2, 2016 at 3:01 am
Just reading that thousands of subpoenaed e-mails went missing from Bill Clinton's server in
year 2000 – personal emails from Monica Lewinsky – that kind of thing. Supposedly.
tegnost ,
June 1, 2016 at 8:36 pm
depositions are still underway, why give away your leverage
sd ,
June 1, 2016 at 11:35 am
Searching 'Pagliano' in the trove of emails at Wikileaks only brings up one response for October
26, 2012. It's a Happy Birthday wish. Shouldn't there be more emails either to or from Pagliano
and at an earlier date than 2012, at minimum one test email to make sure the server was working
when it was first set up?
Still surprised that if her server was hacked, those emails have not be given to Wikileaks.
Tom ,
June 1, 2016 at 11:44 am
Many questions linger, don't they?
Such as, why didn't Bryan also wish her Happy Birthday for 2009, 2010, 2011 and 2013?
Amateur Socialist ,
June 1, 2016 at 8:53 pm
What I don't get is how/why he is pleading the 5th and refusing to answer questions.
http://www.cnn.com/2016/06/01/politics/bryan-pagliano-hillary-clinton-email-server/index.html
That same story says he has an immunity deal and was cooperating with the FBI. I guess it's
possible he only got limited immunity and is concerned about something else but…
Ivy ,
June 1, 2016 at 11:37 am
What is the over/under on the likelihood of an "accident"? My money would be on someone with
an axe to grind against Killery.
TheCatSaid ,
June 1, 2016 at 2:22 pm
I've heard reports that an attempt was made in late 2012. Not the incident in Israel, but on
a secret trip to Iran to meet with Ahmedinejad. What I heard (not on the internet–other channels)
is that one of her SEALS on the small plane with her had a vision of what she would do as president,
and took it into his own hands to stop it. He shot her (the cause for her much-reported-on hospital
stay–with her recovery in question in early days) and he was killed by the rest of the SEAL team.
His death was then said to have occurred in Afghanistan. There's supporting tangential info about
this event that's findable.
Whether or not this story is accurate, I believe there's more to her hospital stay than the
official story. I do not think it was a routine medical event.
Roger Smith ,
June 1, 2016 at 4:28 pm
What was the "official" reason she left SOS?
TheCatSaid ,
June 1, 2016 at 6:10 pm
The only "reason" I've found stated is that she supposedly "always planned" to step down after
Obama's first term.
fresno dan ,
June 1, 2016 at 11:41 am
Tom
June 1, 2016 at 9:40 am
Thank you very, very much for that elucidating synopsis – its hard to read EVERYTHING so getting
just a slice of the prime cut keeps me up to date on an onslaught of info!
I sure hope you do more of these!!!
Tom ,
June 1, 2016 at 11:49 am
Thank you very much. After writing that, I have even more respect for how much work Yves, Lambert
and others put into this site each and every day. Same for the contributions of the many informed
commenters. Naked Capitalism is truly an exceptional resource.
SumiDreamer ,
June 1, 2016 at 3:04 pm
Yes. Thank you.
Quantum Future ,
June 1, 2016 at 6:52 pm
Agee. Nice work Tom and to all who are restoring the Republic. Make sure you go have a drink
and some fun now and then too. A phase of this has passed for me but now another one is looming
in a different way than educating.
But for can be happy with gains for a moment.
Pavel ,
June 1, 2016 at 12:40 pm
Hear, hear! Great reporting by Tom.
I had seen references to the Datto server and the online backups but there hasn't been much
discussion of them or the FBI's getting ahold of them. If they did, it truly is a nightmare for
HRC.
There is a new poll saying 48% of the public think her server was "illegal" and another 24%
or so thought it was "unethical". She and her staff are stonewalling and doubling down on their
excuses. I guess she is just hoping to make it through the convention but it all depends on the
FBI report at this stage.
Tom ,
June 1, 2016 at 1:50 pm
If the Datto server debacle checks out - and it sure looks like it does - I have read in several
places that it pretty much is a no-brainer violation of 18 U.S. Code § 793 – Gathering, transmitting
or losing defense information, specifically Section (f):
Whoever, being entrusted with or having lawful possession or control of any document, writing,
code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model,
instrument, appliance, note, or information, relating to the national defense, (1) through
gross negligence permits the same to be removed from its proper place of custody or delivered
to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2)
having knowledge that the same has been illegally removed from its proper place of custody
or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed,
and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior
officer-
Shall be fined under this title or imprisoned not more than ten years, or both.
If you have classified info on your server and all that data is being sent to another server
for two years, without your knowledge, that's pretty much the definition of "gross negligence,"
I would imagine.
And keep in mind, before we even get to the Datto debacle, I'm already giving Clinton two giant
free hall passes:
1. That it didn't constitute gross negligence to have the server in her basement in the first
place, and
2. That it wasn't gross negligence to move the server to Platte River Networks. (From what I gather,
even if this was an approved server, the U.S. government would have questions like: Who physically
picked up the server, put it on a truck or in a car, who transported the server, who had access
to it before, during and after the move?" Also, questions like, "Who owns Platte River Networks?
What is their security set-up? Who vetted the employees at Platte River? Who had access to the
server while it was there?")
Lambert
Strether ,
June 1, 2016 at 3:30 pm
So wait. You're telling me that the half of the email Clinton retained as "personal" wasn't
all about Clinton's yoga sessions and Chelsea's wedding?
On " Platte River bought a backup device from another IT services company called Datto, Inc,
specifically to back up Clinton's server," I don't think that's quite right. First, the issue
is not a device, but backup to the cloud from a device. Second, the Platte River didn't know the
backup to the cloud was taking place . From the McClatchy story:
Unbeknownst to Clinton, IT firm had emails stored on cloud; now in FBI's hands
Datto and Platte River seemed at odds, however, over how Clinton's emails wound up on Datto's
cloud storage, which may have resulted from a misunderstanding.
Platte River spokesman Andy Boian said the firm bought a device from Datto that constantly
snaps images of a server's contents and connected it to the Clinton server at a New Jersey
data storage facility. Platte River never asked Datto to beam the images to an off-site cloud
storage node and never was billed for that service, he said. Company officials were bewildered
when they learned of the cloud storage, he said.
"We said, 'You have a cloud? You were told not to have a cloud.' We never received an invoice
for any cloud for the Clintons.'"
The source familiar with Datto's account, however, said Platte River was billed for "private
cloud" storage, which requires a cloud storage node. Because Platte River lacks one, the source
said, the data bounced to Datto's off-site cloud storage. The source said that senior Platte
River officials may not have realized it, but company technicians "were managing the off-site
storage throughout."
Datto did not know it was backing up Clintons' email server until mid August, the source
said.
As to whether the FBI might recover Clinton's personal emails from Datto's storage, the
source said: "People don't Datto's service for getting rid of data."
What a mess, but no more messy than IT generally.
I like the overall picture, though, that the bomb has already exploded, but the shock waves
have yet to reach the public. Regarding FBI director Comey, this from William Gibson: "I would
say that our Mr. Swain has recently come into possession of a very high-grade source of intelligence
and is busy converting it into power."
Tom ,
June 1, 2016 at 9:48 pm
Yes, you've clarified some points that I mangled in trying to sum up the story. Thank you.
There are many more tangents to just this Platte River/Datto story that are worth following up,
but it takes so much time to try to piece together even a seemingly small story like this. I can't
even imagine the complexity and confusion facing the FBI investigators as they try to make sense
of all the fallout from Bill and Hillary Clinton's public/private activities through the years.
sd ,
June 2, 2016 at 2:46 am
The server for the Datto cloud that was backing up the Clintons' server would have also had
its own backup.
John Wright ,
June 1, 2016 at 9:46 am
One can hope that Obama handles Clinton the same way Nixon handled his vice-president, Spiro
Agnew. Spiro Agnew was the corrupt politician of the hoi polloi, as he was known as "The only
politician you could bribe with a bag of groceries.".
The Clinton Foundation and the Clintons sure put the Agnew efforts to shame as they raised
the price of buying politicians and access by many orders of magnitude.
Nixon, busy with his own scandals may have been distracted, but his justice department let
Agnew plead "nolo contendere" (no contest) to the charges of corruption.
One can wonder if Gerald Ford's pardon of Nixon installed this dual USA justice system that
we have seen in effect since his time.
The Kennedy Library honored Ford for his courage(?) in granting the pardon (
http://www.jfklibrary.org/Events-and-Awards/Profile-in-Courage-Award/Award-Recipients/Gerald-Ford-2001.aspx
)
So one Democratically connected organization signed onto this separate justice system for
the politically connected. Possibly the concern Obama has for his unfunded $1Billion Presidential
Library will force him to burnish his legacy by NOT rescuing HRC with some dubious legal maneuver.
It is somewhat ironic that Nixon was brought down by a private electronic system (his tape recording
system) while Clinton may be brought down by her own private electronic email system.
The also share a common advisor, Henry Kissinger, and both have/had phlebitis.
She probably won't borrow Nixon's "I am not a crook." line..
timbers ,
June 1, 2016 at 9:53 am
I get the tone of alarm and concern of scandal coming from Team Obama shown in this article
– I'm just not seeing it in Hillary supporters. Maybe Obama's ego is a bit too fragile. Regardless
my experience with talking to Hillary supporters is that no amount of scandal of outright criminal
lawbreaking affects their views about Hillary. They revert to "she's been scrutinized and tested
for decades by her enemies and she's survived." They are people on the margins who will be affected.
How many are the Dem establishment? It's going to take a whopper to get them to tank Hillary IMO.
Lambert
Strether ,
June 1, 2016 at 3:32 pm
That's what I see from Clinton supporters on the Twitter. Some of them good people I've known
for years. "Nothingburger" was the favorite phrase, at least for awhile.
Yves Smith
Post author ,
June 1, 2016 at 4:57 pm
Reminds me of the defenders of Elizabeth Holmes at the WSJ, who kept insisting that all the
attacks were from journalists who were jealous of the success of a brilliant young woman and only
knew how to tear down not build.
Their ranks became thinner over time as their view was increasingly less plausible.
Quantum Future ,
June 1, 2016 at 6:59 pm
Timbers – You know, a close friend since grade school loves the Clintons. He even buyed the
Bill Clinton collector doll. He stole close to $60,000 from his employer Midas, has mistresses
and has done a of very unsavory things. And I am not a saint but these people know but do not
care. Probably 1 of 3 people are sociopaths.
Stephen Gardner ,
June 1, 2016 at 10:00 am
There is a detail that is being universally missed both in the MSM and alternative press:
it is a virtual certainty that the NSA has a copy of every email sent or received
by that server. Does anyone who has read what has been published about Snowden's revelations
doubt that? Therefore the Whitehouse knows precisely what the dirt is. Furthermore, what do you
suppose the chances are that the FSB didn't hack her jury-rigged server? This potential leak path
is also well known to the white house. Don't forget the mayhem when the FSB (who else) posted
Nuland's little chat with Pyatt over an insecure line. Let no one forget that HRC is strongly
connected to the neocon project to undermine Russia's return to strength.
Just ask yourself: What would Vladimir Putin do?
fajensen ,
June 1, 2016 at 11:21 am
Just ask yourself: What would Vladimir Putin do?
Putin would do a deal. A "small favor" done in return for something else. Any mobster can understand
that.
Trouble is that Hillary represents the US so very well. Any offer would be perceived as a sign
of weakness, therefore, righteous bullying and threats from the US will be the only possible response.
So, the leaks would start – have started perhaps.
steelhead23 ,
June 1, 2016 at 10:02 am
Might this "leak" be a signal to Clinton to get out of the race? She cannot be unaware that
Bernstein is carrying Obama's water.
Ivy ,
June 1, 2016 at 11:41 am
Obama will likely have plenty of drama before he slinks out of the White House to his $1
Billion Library . Future historians will sift through the detritus of his hollow reign and
might eventually find out how he got pwned. Maybe Bernstein could have a journalistic draft underway
about that to put in his two cents?
TheCatSaid ,
June 1, 2016 at 2:26 pm
That book's been written. Apostles of Power / Coup de Twelve by David E. Martin, who has first-hand
knowledge about some of the most important facts.
It's called fiction but only some of the names and dates/sequences were changed. Cheney's name
is left in on purpose.
TheCatSaid ,
June 1, 2016 at 2:29 pm
if you read it keep in mind the reason it was written–specifically to avert a major disaster
involving a nuclear reactor explosion in the US in 2012, to enable a major electronic financial
heist. He had to reveal enough of what he knew to stop the button from being pushed. This was
successful. Only the preliminary "earthquake" at Santa Ana nuclear reactor occurred, as the charges
had already been set, but after the book came out (initially distributed on Amazon for free, so
it could be tracked to who downloaded it) then the full plan could not be carried out.
Lambert
Strether ,
June 1, 2016 at 3:34 pm
Sorry. Not buying works of fiction with the names changed (unless we're talking serious roman
a clef a la Primary Colors .
TheCatSaid ,
June 1, 2016 at 6:18 pm
Read the book before judging it. It will be obvious why names cannot be given. And consider
my comment above about why the book was written. It was not written to be a best seller,
it was written to prevent a major catastrophe. The author has given a number of extended interviews
dealing with the events described and confirming his first-hand participation. (He was offered,
twice, to join the 12 shareholders in the purchase of the 2008 presidency, without a financial
contribution because of his unique big data algorithms. He declined and experienced some very
disagreeable effects–but he's not someone who can be bought or intimidated.)
Quantum Future ,
June 2, 2016 at 1:07 am
TheCatSaid – Interesting book recommendation. Mitigation of casualties is an important goal.
It is not set in stone mass casualties will occur because of sociopathic behavior. Some can play
a role to minimize the damage. Yves does this directly regarding lawlessness. Others play some
different roles.
Now at the end of human evolution, there is nothing more important and realistic to end classic
death. But far too few have gotten the memo yet. But that is changing. For what good is it to
gain the whole world when you get old, shit your pants, lose your memory when now that is no longer
necessary? But absolutley, the wolves must be pushed back and the Republic restored to accelerate
such a lofy but now doable goal.
MyLessThanPrimeBeef ,
June 1, 2016 at 3:06 pm
In Feb, per Bernstein, people at the White House were worried and horrified.
Now, they are terrified, again, per Bernstein.
To me, it seems to be about same.
Lambert
Strether ,
June 1, 2016 at 3:36 pm
That was my counter-suggestible thought: The White House panicked once, and the Clinton campaign
shrugged it off, successfully.
I don't think the two cases are comparable, though. The Wall Street transcripts are a Sanders
campaign thing, and to every right-thinking member of the political class that spells "not serious."
But this terror is from the heart of the establishment; "serious people."
Steven Greenberg ,
June 1, 2016 at 10:15 am
At some point the White House and the Democratic party "leadership" are going to realize that
if they have to work this hard to get Clinton the nomination, they are going to have worse troubles
winning the election with her at the head of the ticket. They are going to have to choose the
lesser of two evils – 1. Let the Republicans take this election, or 2 – Let the Sanders wing of
the Democratic Party take this election.
Vatch ,
June 1, 2016 at 11:28 am
From the point of view of the Democratic Party establishment, Trump and the Republicans are
clearly the lesser evil. Despite his apparent appeal as an outsider, Trump is very much an insider.
As a billionaire, he is one of the very small number of people who own the United States. He'll
ruffle the feathers of some of his fellow plutocrats, but the "right people" will remain in charge,
and he will continue most of the billionaire friendly policies of the Clinton, Bush, and Obama
administrations.
JustAnObserver ,
June 1, 2016 at 11:39 am
if nothing else they must have realized that Sanders and his millions of supporters have effectively
blocked off their – parachute drop Biden – escape route from the Clinton disaster. I think this
is the key to why "they're freaking out". They never really had any planB 'cos those Dems and
their trained MSM toadies who "create their own reality" never for a moment thought they'd ever
need one.
NotTimothyGeithner ,
June 1, 2016 at 12:04 pm
There was Biden speculation early on for a reason, but I think people in New Hampshire (I've
never been to Iowa) take the primary seriously and force the candidates to answer tough questions.
Hillary and Obama had a celebrity following and were protected, but any other Democrat would have
to have a point. Private prison, charter school, and war supporters would be weeded put early.
Biden might be the VP, but he has been at this for years and achieved nothing except to not be
as egregious as Evan Bayh and Tim Kaine. No one will go out to see Biden unless he had a point.
The modern Democratic elite can face their voters directly. They need a celebrity wall to protect
them. Many of these thugs hid behind Obama a day expected Hillary to do the same, but who else
is a celebrity and can hide behind Katie Perry or Oprah? They might be protected by the sycophants
in their own district, but the sycophants outside the district have their own objects of devotion.
They simply can't go to Iowa and New Hampshire and be taken seriously.
JustAnObserver ,
June 1, 2016 at 12:49 pm
I take it that
"… can face their voters directly."
should have been
"… can't face their voters directly."
^
?
ckimball ,
June 1, 2016 at 12:41 pm
Several weeks ago my daughter had a dream.
She witnessed Bernie Sanders accepting the democratic primary nomination
because Hillary Clinton was disqualified by a technicality.
Three years ago during a lengthy Vipassana meditation retreat I experienced
myself sitting on a divan in a long lanai. People were milling around a
banquet table set with fruits salads flowers. There were birds flying in and out
up above us and I became aware that I could understand them and that they were excited and had
decided to have a race. Quickly the race began and was over. The winner was a little brown bird…like
a sparrow. The other birds were incredulous. How could this happen? A green parrot kept flying
up to the little brown bird asking how did you do that? But the little brown bird kept laughing
and flying away so fast the parrot could not stay with him.
The next day, continuing the practice in my room with the curtains drawn, I heard
tapping at the window. I acknowledged the sound and continued practicing but
the tap tap pause continued. Finally I had to see. I got up pushed aside the curtain and there
was a little brown bird.
When I saw the little bird land on the podium while Bernie Sanders spoke I thought of the little
brown bird I'd experienced. And when Bernie in the moments said wistfully something to the effect…it
could have been a dove
representing peace. I thought oh no, that little bird is a metaphor for the people
who want and claim their humanity and the natural world resonates with that.
tegnost ,
June 1, 2016 at 1:44 pm
I too think bernie will pull it out, the other choices are terrible. I'm looking for aspirational
latinos to flock to bernie in california and it'll be a rout that can't be ignored. I hope that's
what happens.
MyLessThanPrimeBeef ,
June 1, 2016 at 1:56 pm
That reminds me of the dove who landed on Fidel Castro's shoulder during his Jan. 8, 1959 speech.
Tom ,
June 1, 2016 at 11:10 am
Once Clinton regrettfully announces her decision to suspend her campaign for presidency (due
to mounting health concerns and after consulting with her doctors and family) and returns to private
life, she can always count on giving a speech now and again to "replenish the old coffers," right?
Cut to the kitchen in Clinton's residence:
"What do you mean Blankfein isn't returning my calls? Someone find my BlackBerry so I can call
him myself!!"
Amateur Socialist ,
June 1, 2016 at 11:58 am
Sounds like the ending sting in a segment of Clintonsomething – "The Campaign Years"
from the excellent Le Show
by Harry Shearer.
fresno dan ,
June 1, 2016 at 11:59 am
From Yves:
"…..
As of late 2007, I was assessing the odds of a really bad outcome (which I did not see as a massive
financial blowup, but a Japan-style bumping downhill over a period of years) as 20-30%, which
I regarded as uncomfortably high. I told Lambert I thought the Clinton train wreck odds were in
that range. He thought it was more like 30% than 20%.
This post indicates the odds are even higher than that. I see two implications in the Bernstein
official messaging beyond those that Gaius describes. One is that the Obama Administration has
been blindsided by how bad the underlying fact set is, and they recognize that even worse is likely
to be exposed. Someone as image-conscious as Obama would be particularly put off by that.
But the panic is also a clear indication, and perhaps as important, another message, not just
to Clinton but to Team Dem, that the Administration can't, or won't but is making it seem like
can't, do what it takes to save Hillary's bacon.
And I suspect it really is "can't". The FBI has enough autonomy that if they find real dirt
on the Clintons, they will leak like crazy if the DoJ does not pursue the case in a serious way.
That would make the Administration complicit, and Obama does not want his final months in office
tainted by his Administration touching the Clinton tar baby any more than it has to…."
============================================
I am really thinking this is the most serious issue about whether this country operates within
the confines of equality before the law since Watergate. I think the financial crisis revealed
a level of corruption that is eye opening, but that was mere pecuniary corruption.
If Hillary goes unprosecuted, we decide to let the facade collapse and no longer put the effort
into pretending that there is any relationship whatsoever between the law, justice, and the running
of the state.
armchair ,
June 1, 2016 at 12:26 pm
In this imagined history, the Clinton's see their return to the WH thwarted by an upstart junior
senator. As things start to crash around them, in 2008, a light bulb goes off. The junior senator
is still pretty nervous about the Clinton's and Clinton has leverage to make a deal with him.
She can through establishment support behind Obama. Obama takes the deal. Then, with a Clinton
at State and a future presidency on the horizon they will be able to enrich themselves and their
foundation for millions upon millions.
The future value of a Clinton presidency will sell itself. Money will pour in from everyone
in the world who needs a regulatory break or weapons a deal. So, they cut the deal to go in on
an Obama presidency.
What they get is eight years of uninterrupted money making, because a Clinton will be president
again, and you might as well get in on the ground floor. In this imagined scenario, the Clinton's
must get the presidency, because they have essentially promised weapons buyers and regulation
skirters that they will get their return on investment coming in 2017.
RUKidding ,
June 1, 2016 at 1:50 pm
Yes, most likely, at least in part. A lot of influence peddling went on, and that's for sure.
It's something that eludes most Clinton supporters that I know personally. They see Hillary as
this shining beacon of something something and something else. They have excuses for everything,
and somehow don't see influence peddling, selling arms and the like as all that bad. IOW: IOKIYAD.
I don't agree with that, myself, but many do.
Lesser evil… is still evil.
armchair ,
June 1, 2016 at 4:35 pm
It sound like you're encountering the tribal mentality, which is a drag.
Russell ,
June 2, 2016 at 1:27 am
Sounds like the game.
JustAnObserver ,
June 1, 2016 at 1:06 pm
Note its not just the CIA who would be (or is already) furious that some of their agents may
have been compromised/arrested/executed. The FBI also has agents working abroad undercover. What
if the FBI found info in the backed up emails showed one of their own had been blown ? The vengeance
would be frightening and there's nothing Comey or anyone else could do that would stop it.
JimTan ,
June 1, 2016 at 1:11 pm
I'm not sure the media's current focus on Hillary's email server is warranted. There are
definitely indications that she violated email policies, but there don't seem to be specifics
about what these actions were trying to hide. I think her very questionable family ties to corporate
money are a more meaningful topic in determining her suitability for the U.S. presidency
:
http://nypost.com/2015/05/12/us-approved-most-bill-clinton-speech-requests-within-days/
https://www.washingtonpost.com/politics/for-hillary-clinton-and-boeing-a-beneficial-relationship/2014/04/13/21fe84ec-bc09-11e3-96ae-f2c36d2b1245_story.html
http://www.ibtimes.com/clinton-foundation-donors-got-weapons-deals-hillary-clintons-state-department-1934187
http://www.ibtimes.com/political-capital/despite-walmart-ties-support-free-trade-hillary-clinton-touts-commitment-2323480
There's been some recent focus on 2013-2015 speeches given by Bill Clinton, and donations to
the Clinton family foundation over this time period. What about speeches and payments during the
earlier time period when Hillary was Secretary of Sate (January 2009 – January 2013)?
Jess ,
June 1, 2016 at 1:32 pm
Jeez Louise. The focus on her email server is, in major part, driven by the issue of the deleted
emails and HRC trying to keep her communications secret and unobtainable through FOIA. One obvious
reason is to hide the connection between Bill's speeches and Clinton Foundation activities with
Hillary's decisions as SoS. Email and corporate money is all one big hairball.
JimTan ,
June 1, 2016 at 1:57 pm
I see. Thanks for connecting the dots.
Synoia ,
June 1, 2016 at 1:53 pm
And the great hope in the White House…and get President Obama out there to help her, he's
got a lot of credibility,
They are deluding themselves. Getting Obama out there will push Trump to success.
SomeCallMeTim ,
June 1, 2016 at 3:04 pm
Gee, the internet told me just this morning that Obama is champing a the bit to hit the 2016
campaign trail for Hillary (or maybe just against Trump?)
After reading this post and comments, I'm further disabused of the Clintons, and think more
and more that Saunders is hanging in there just waiting for the dam to break.
Lambert
Strether ,
June 1, 2016 at 3:39 pm
Or, more precisely, waiting for somebody else to break the dam for him (since
no Clinton voter will ever vote for him if he does the deed himself).
dk ,
June 1, 2016 at 4:32 pm
The Clinton Machine (in other words the political operation of the Bill and Hillary, and
potentially Chelsea) has always operated on the basis the money and connections will fix everything.
It has, after all, gotten them this far. However, as a core operational mode, it also accumulates
cynicism and tends to value loyalty over performance, leading to degradation over time.
The Clinton primary 1992 campaign broke new ground (at the time) by putting the (two-way) sharing
of fundraising lists on the table when soliciting endorsements from office holders. This was already
commonplace among Republicans, who were already being consolidated by ideologically or business
focussed fundraising organizations (long before PACs became an common acronym, but already organized
under 501(c)(4) or 501(c)(6)) and often shared these donors. But the Democrats, at the time, were
more driven by fundraising lists, which were often closely guarded assets.
But by offering to share (as in, swap) donor lists with endorsers, the Clintons, without actually
breaking any laws (although improper development and use of these lists could violate FEC regulation),
were putting financial power squarely on the table, and up front (the list share offer was frequently
mentioned on the initial approach to the potential endorser, I have first and second hand knowledge
of this).
And the swap would involve the endorser sharing their list, as well as receiving one,
which would be more than a public endorsement; it would be an endorsement to donors. Reaction
in 1992 was mixed. But with Bill political success and popularity as a president (among moneyed
Dems), the Clinton Machine became a major player in Dem politics, cultivating a "deep" door list.
And what do donors pay for? Consultants, and media and data products. The Machine accumulated
a network of loyal consultants and vendors across the country; loyal, because they were certain
of getting paid (not always a sure thing in politics), and because of the large and diverse (and
at least nominally vetted) network of Machine operatives and vendors. This network also shares
strategic methodologies and technologies; essential commodities, but ones whose shelf life (effective
expiration of value) can be hard to gauge (especially by lazy/uncommitted people who feel little
pressure to actually win anything, as long as they can put on a good show and maintain their stature
by… feeding the Machine). And of course, associated (and implicitly grateful/beholden) elected
office holders (at State and local levels, not just Federal) are collected along the way.
The reliance on this Machine is one of the reasons the Clinton campaigns have displayed such
frequent tone-deafness. Not only is there a sizeable echo chamber of like-minded advisers only
to glad to support the current (but often calcified) rationals, but the approach to voter opinion
is "they'll forget if we divert them" (and also "poor people don't vote, so their opinions are
strategically irrelevant"). The Clintons were relying on a combination of news-cycle turnover
and the chorus of their social and MSM channels (repeat-until-true, repeat-until-true, etc). Both
of these tools are at least somewhat outdated in the social media age, where articles/posts/images/memes
can circulate and resurface independently of MSM news cycles, and where multiple groups can pool
opinion and effort as soon as they notice coincidence/convergence.
One can say what one will about Team Obama, but they have always been aware that they rode
to power on a populist idea (Black President) and the social media arena that amplified its force.
All political groups tend towards tone deafness, but Obama's people have newer ears. They may
not feel very beholden to anyone operating in the social media, but they disinclined to completely
ignore the potential impacts of opinions in circulation.
BTW, the donor-list swap message has changed over the years. Now the intro message for endorsement
solicitations is more like: "We'll mention you to our donors". Which is a double-edged sword;
that mention may also be "such-and-such did not endorse, just so you know". Again, leading with
this message exerts (by implication, not by direct statement) a powerful financial consideration
on the potential (And often acquiescing) endorser. Beyond that common element, solicitations are
likely to say whatever might appeal to the particular target.
Quantum Future ,
June 1, 2016 at 9:13 pm
Dk – Very interesting point about the data. I am in that space in a nutshell. By referral,
did some work with both Jeb Bush and Dean. I was hired for market intelligence for fundraising.
I remember the Time mag about Dean the Money Machine. Social media was a big deal for donors.
Webbies dont make the best door to door activists however.
Anyways, I like Jeb Bush. Dean is an asshole of a human being. So as I was managing Bush constituent
list for a time I called his office to suggest them doing market intelligence for donors.
The attorney for Jeb called me back. He told me that if I sent over a plan to not expect to get
paid for it. I thought to myself it was no wonder the Clintons could easily win – They paid people.
Jeb did look at an idea for a political social media platform I suggested to connect voters
to politicians, a debate platform. He said to call Pete Peterson for funding. Pete wouldn't give
me a meeting, his secretary said I wasnt in the club.
So for Jeb he has learned the hard way it is the company you keep. But his other issue was
hiring his own Mexican friends his wife and continued amnesty. His campign staff like any tribe,
only wanted fo hire Mexicans. Of course, it is the immigration issue where Trump ate his lunch.
In the end he wasn't ready to be POTUS. But innovation wise and on monopoly issues he was a Teddy
Roosevelt.
Thanks for letting me share my thoughts tonight Yves. You know, I appoached you as a different
user at one time and asked to consider joining in the political social media platform I was building.
But even if it was a right idea, I came across too strong. I apologize. Wish I hadnt done that
your message would been amplified a lot more by now. You are a personal hero of mine. Keep at
it, please, the we are clearing a hump in ways but much work left to do.
Quantum Future ,
June 1, 2016 at 4:45 pm
Cackling at the demise of intelligence assets is not a joking matter. Neither is it a joke,
right or deposing dictators and joking about it. Fortunately, the rule of law is being restored.
But there is a lot of domestic and geopolitical clean up. With Russia, they are about energy sales.
Yes, they got uppity with monopoly but it has gone to far.
You never want to make Putin a Geronimo with the bomb. The Chinese were made promises never
to be kept. They know a good customer when they see one so they will get over it.
The only job of government is a security racket. An unfortunate, necessary evil. When the Clintons
are well lets call it what it IS – treason. Enough is enough.
Trump is a Democrat. He is for single payer. Not so sure why some are so freaked about his
nationalist campaign rhetoric. Either him or Bernie will make a good president but Bernie has
the experience and Trump does not. It matters.
marym ,
June 1, 2016 at 11:13 pm
Trump is not for single payer
Trump's main ideas for a replacement [of Obamacare] are to allow health insurance to be
sold across state lines and permit people to make tax-free contributions to Health Savings
Accounts (HSAs). HSAs are paired with a high deductible health insurance plan and are intended
to make people more conscious of how they spend
Quantum Future ,
June 2, 2016 at 1:27 am
Mary – Competition is part of Trumps plan for private insurers. A lot of countries have single
payer government but also private insurers. It tends to work althogh I wish it all could remain
private, free market what have you. Health is like money, it is so important you have to have
the awful taint of government one way or the other.
But when pressed Trump has responded he will not let anyone die in the streets. Not arguing
to vote for the man just suggesting reading beween the lines. He is a Democrat in drag, what I
would call a moderate in policy except immigration. He is duplicating the Eisenhower playbook,
on immigration, bond holder haircuts and telling certain bankers to play ball or ELSE. This does
work. But as I mentioned Bernie has more a lot of real experience. So dealmaking as Trump claims
indeed has a lot of human psychology involved but experience is a major plus.
It woudnt surprise me if so much of this is all political theatre. Trump is the friends of
Clinton after all. Could even be with Berniw But that said, rather even if such speculation true
better than false flags to right the country. Besides, it has been fun theatre… Besides, the momentum
on policy is turning in the right direction.
marym ,
June 2, 2016 at 7:57 am
Countries that provide universal healthcare using private insurance (the Bismarck model) do
so with highly regulated, not-for-profit insurance providing legally defined coverage. Competition
and profit-taking are at the margins for elements not included in the defined coverage, such as
cosmetic surgery or a private hospital room. Trump's published healthcare plan is the same gibberish
Republicans have always offered.
Kim Kaufman ,
June 1, 2016 at 11:01 pm
There are too many comments to read through right now but is almost 250 comments a record?
Has anyone mentioned this might be a trial balloon for Biden to step in?
Phil ,
June 1, 2016 at 11:07 pm
It's interesting to ponder the various possibilities. What I don't get is why Obama's IT security
people didn't notice that Clinton digitally engaged and communicated with the *White House* in
a way that could have compromised both parties, and beyond.
fwiw, I think we are all at least *somewhat* impacted by confirmation bais re: the competency
of persons we are mostly in agreement with, even in areas outside their domain. When it comes
to senior executives and IT security (unless they are IT experts), we see these mistakes over
and over again in political and business domains. One can look to any number of well-known political,
scientific, or cultural figures who made stupid gaffs within their sphere of influence in this
way. We always seem surprised by this, but it's really not a surprise.
Most well-known political persons (I have known a few) are so busy and so immersed in what
they are trying to accomplish that their over-trust in operational personnel – and/or belief that
they can maneuver out of or overcome almost any problem – creates scenarios like Clinton's.
Bernie is my guy; I would love to see him take on Trump, but the powers that be appear to want
something else. I can't stand Trump, but when looking for other perspectives I will put on my
long-buried blue collar roots persona; then, I hear a guy (Trump) who "talks the talk" in a way
that is almost mesmerizing. I hate to admit that, but it's true – and when I connect with old
buds from way back, they reinforce this impression.
When you get enough people (in this case, Americans) scared and worried, they are no different
than any other group of human beings; they want to be "saved"; they want to "blame"; they want
to throw out the "chief"; they want to "follow a new leader"; they are not concerned (in this
case) with whether Trump can "walk the walk"; they are susceptible to someone who is very adept
at "talking the talk" (a demagogue) in a way that allays their fear and desperation – leading
them to grab onto the nearest piece of flotsam (screw the other guy!) that will keep them from
drowning. I'm beginning to worry.
JTMcPhee ,
June 1, 2016 at 11:24 pm
Seems to me that except in a relatively few corners and local settings, and now very frankly
via our mostly collective embrace of the Neo geist, "America" has always and only been about "screwing
the other guy." And Tocqueville noted how happy we are to be boiled frogs, or to find ourselves
in deep water and only too happy to stand on the other guy's shoulders, by guile or force, to
try to gain a little buoyancy to keep our own noses above water, even knowing somewhere in our
guts that we ought to cooperate to find the valve and turn off the water, or to go after the pirates
that threw us off the ship…
greensachs ,
June 1, 2016 at 11:34 pm
I don't believe "foaming one more runway" (read: having your DOJ, FBI appear helpless)
wouldn't bother this administration. A Loyalist are those unengaged (or too engaged) whom choose
willingly to believe the disastrous economic and political experiment, that attempted to organize
human behavior around the dictates of the global marketplace, has been a splendid success…or worse,
blindly, my tribal leader is in accordance with all that is good.
Russell ,
June 2, 2016 at 1:25 am
Haiti. Look at film of the Clintons in Haiti to see how they work. & Haiti is one place
where also the elites own the deeds. Haiti Is America, only sooner.
Wilmington Coup. C.S.A. methods used again, and again.
Giving the people of the US, the reinsurers of the reinsurer the USPO Service banking they paid
for and pay for is the concrete thing that can be done to "Change the Conversation" as Mad Men's
guy Hamm? no, his character would say.
Opening there.
Brooklin Bridge ,
June 2, 2016 at 9:14 am
For what it's worth, Jonathan Turley suggests Hillary still has friends in high places
in his discussion of former Clinton IT advisor, Bryan Pagliano, who is taking the fifth amendment
in deposition on email scandal,
https://jonathanturley.org/2016/06/02/former-clinton-it-advisor-to-take-the-fifth-in-deposition-on-email-scandal/#more-99459
The silence of Pagliano and the
reported lapse of memory of other top aides is likely good news for the Clinton team in
pre-November damage control. If top aides will claim faulty memories or invoke their right
to remain silent, the only disclosures before the election would have to come from the FBI
or Congress. Yet, the FBI would turn over any proposed indictments to the Justice Department
and, if the Justice Department scuttles any indictment, there would not normally be a public
report.
I kept the link in the above paragraph active as it is interesting reading.
For those curious as to why Pagliano would take the fifth (rather than go straight for a quart
:-)) when he already has immunity, one of the comments to Turley's post explains (from Tin
at 1:42 am):
They are completely different matters. The FBI gave him immunity from possible criminal
prosecution. The deposition mentioned n this post involves a civil lawsuit, "Judicial Watch
v. U.S. Department of State." It is a civil suit brought under the Freedom of Information Act
to get more documents out of the State Dept.. Pagliano is not a party to the suit, but they
want to depose him as a non-party deponent and his lawyers sought a protective order. He plans
to take the 5th and his lawyers don't want it videotaped.
docG ,
June 2, 2016 at 10:22 am
Those e-mails don't alarm me anywhere near as much as the $200,000 plus speaking fees from
Wall St. NO speech by anyone is worth anywhere near such an amount. These were clearly bribes,
there's simply no other way of looking at it. I have no interest in seeing the transcripts of
those speeches because the money counts far more than the content, and speaks for itself. No way
would I vote for someone so clearly in the pocket of the oligarchy.
Notable quotes:
"... Actually, you can hide nothing, and anything you said, wrote, or plausibly thought can and will be held against you at a time convenient for the Security State to whip it out if they have their way. ..."
JerseyJeffersonian ,
May 27, 2016 at 11:28 am
In related developments ( in the matters of legitimacy, and most especially, control
) here are two links:
https://theintercept.com/2016/05/26/secret-text-in-senate-bill-would-give-fbi-warrantless-access-to-email-records/
My comment on this in an email to others…
Amendment IV [1791]
The right of the people to be secure in their persons, houses, papers, and effects,
against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue,
but upon probable cause, supported by Oath or affirmation, and particularly describing the place
to be searched, and the persons or things to be seized.
Obviously, this paints our (overblown) liberties with an over-wide brush, and the Wise Solons
of our Senate know just how to get around this superannuated and flawed conceptual framework.
Just ignore this amendment. You've got nothing to hide, right , so what are you worried
about? Actually, you can hide nothing, and anything you said, wrote, or plausibly thought
can and will be held against you at a time convenient for the Security State to whip it out if
they have their way.
C'mon, it's an Empire now, and it plays by its own rules, and is not to be chained to some
fossilized, starry-eyed claptrap from the Enlightenment. Sheesh.
https://www.washingtonpost.com/news/checkpoint/wp/2016/05/26/special-operations-troops-assaulted-downtown-tampa-all-to-thunderous-applause/
And my comment in that email on this matter…
Wait, military special forces from over a dozen countries are running an exercise in the supposedly
sovereign territory of the United States? What, is this the transnational elite's super-special
SWAT team taking off the wraps? And Idiot America loves it. The Founding Fathers weep, just as
they do concerning that first item.
Let those malcontents from Green Day whine about the Idiocracy…
https://www.youtube.com/watch?v=a1BS7XnEZqc
February 11, 2014 | pcmag.com
This time last year, no one knew Edward Snowden. But by the end of 2013, his name was on
every top 10 list, and the revelations
contained with the NSA documents he leaked have inspired
today's "The Day We Fight Back" protests.
For a while the information contained with the leaked documents took a backseat to the cultural
impulse to dissect Snowden as a celebrity-his Reddit posts about sex and Cosmo asking "What
the hell is Edward Snowden's girlfriend thinking right now?" Then Sunday talk shows debated whether
Snowden was a was fink, traitor, whistleblower, or spy - as the elusive former contractor made an
escape to Russia worthy of a spy-thriller chase scene.
But the Snowden documents contained serious information. Since June, we have learned about a variety
of NSA programs, including PRISM, a multilayered, multiagency program that mines the data of suspected
terrorists, as well as that of anyone even marginally associated with them. And the information that
has been released is reportedly just a
fraction of what exists.
Still, we have about eight months worth of data dumps, information that has prompted the
promise of action from the White House,
bills in the Congress, and today's "Day We Fight Back" protest, which is calling on people around
the globe to protest NSA surveillance on the Web and in person. Below, we look back at some of the
most alarming revelations from Edward Snowden thus far.
- The NSA intercepts deliveries According to documents published by German newspaper
Der Spiegel, the NSA
uses a tactic called "method interdiction,"
which intercepts packages that are en route to the recipient. Malware or backdoor-enabling hardware
is installed in workshops by agents and the item then continues on its way to the customer.
- The NSA can spy on PCs not connected to the Internet Der Spiegel also published a document from an NSA division called ANT, which
revealed technology the NSA uses to carry out operations, including a radio-frequency device
that can monitor and even change data on computers that are not online.
- Phone companies must turn over bulk phone data In April,
Verizon was ordered to hand
over telephony metadata from calls made from the United States to other countries over the course
of three months. The metadata included originating and terminating phone numbers, mobile subscriber
identity numbers, calling card numbers, and the time and duration of calls. The secretive nature
of the FISA court that made the request for data, however, meant that Verizon and other companies
could not discuss the data requests.
- The NSA hacked Yahoo and Google data centers In October, The Washington Post accused the NSA of
secretly monitoring transmissions
between the data centers of Internet giants Yahoo and Google. Both companies denied giving the NSA
permission to intercept such traffic. Google's Eric Schmidt
called the move "outrageous," if true,
while Yahoo moved to encrypt its data
after the revelation.
- The NSA collects email and IM contact lists Hundreds of thousands of
contact lists
are collected by the NSA in a single day, The Washington Post also revealed. While the
targets are outside of the United States, the scope of the collection means that info from U.S. citizens
is inevitably included.
- RSA created a backdoor into its encryption software at the NSA's request In December, Reuters reported that
the NSA paid RSA $10 million to create a "back door" in its encryption products, which gave the
NSA access to data protected by RSA products like Bsafe. RSA
denied the report, but the revelation
prompted speakers to bow out of this
month's RSA Conference.
- The NSA eavesdrops on the phone calls of world leaders. The U.S. government's friends and family calling plan reportedly extends to the content of calls,
including tapping into German Chancellor Angela Merkel's phone calls from the
roof of the U.S. embassy in Berlin. The news prompted German officials to consider
creating their own Internet.
- The NSA knows how many pigs you've killed in Angry Birds. The Flappy Bird flap may be bigger, but last month,
The New York Times reported that the NSA
and British intelligence teamed up
to collect and store user data generated by "dozens of smartphone apps," including popular games
like Angry Birds. Rovio denied it,
but anti-surveillance activists still
defaced the developer's website.
- The NSA engages in industrial espionage. The U.S. government has framed the NSA's activities as necessary to keeping citizens safe, but Snowden
said on German television, "If there's information at Siemens that's beneficial to U.S. national
interests-even if it doesn't have anything to do with national security-then they'll
take that information nevertheless."
- Tech companies cooperated with the NSA and then were asked not to talk about it. Microsoft, Google, Yahoo, Facebook, PalTalk, YouTube, Skype, AOL, and Apple were all
named in the PRISM documents and
struggled with how to talk to the public about it because of gag orders.
wguerrero
Big brother is watching us all.
The revelation that an Israeli firm cracked the iPhone raises questions about state-corporate
espionage.
The Federal Bureau of Investigation (FBI) court battle with Apple over the security system in
place on iPhones appears to be over. But some experts in the communications security community are
expressing concern because of the
Bureau's unwillingness to reveal what exactly occurred to end the standoff.
According to government sources speaking both on and off the record, the FBI succeeded in breaking
through the Apple security measures
with the assistance of an unidentified third party. The technique used was apparently not a one-off
and is transferable as the Bureau
has now indicated that
it will be accessing data on a second phone involved in a murder investigation in Arkansas and is
even considering allowing local police forces to share the technology. That means that the FBI
and whatever other security and police agencies both in the U.S. and abroad it provides the information
to will have the same capability, potentially compromising the security of all iPhones worldwide.
The breakthrough in the case leads inevitably to questions about the identity of the company or
individual that assisted the Bureau. It means that someone outside government circles would also
have the ability to unlock the phones, information that could eventually wind up in the hands of
criminals or those seeking to disrupt or sabotage existing telecommunications systems.
No security system is unbreakable if a sophisticated hacker is willing to put enough time, money
and resources into the effort. If the hacker is a government with virtually unlimited resources the
task is somewhat simpler as vast computer power will permit millions of attempts to compromise a
phone's operating system.
In this case, the problem consisted of defeating an "Erase Data" feature linked to a passcode
that had been placed on the target phone by Syed Farook, one of the shooters in December's San Bernardino
terrorist attack. Apple had
designed the system so that 10 failures to enter the correct passcode would lock the phone and
erase all the data on it. This frustrated FBI efforts to come up with the passcode by what is referred
to as a "brute force" attack where every possible combination of numbers and letters is entered until
the right code is revealed. Apple's security software also was able to detect multiple attempts after
entry of an incorrect passcode and slow down the process, meaning that in theory it would take five
and a half years for a computer to try all possible combinations of a six-character alphanumeric
passcode using numbers and lowercase letters even if it could disable the "Erase Data" feature.
Speculation is that the FBI and its third party associate were able to break the security by
circumventing the measure that monitors the number of unsuccessful passcode entries, possibly to
include generating new copies of the phone's NAND storage chip to negate the 10-try limit. The computer
generated passcodes could then be entered again and again until the correct code was discovered.
And, of course, once the method of corrupting the Erase Data security feature is determined it can
be used on any iPhone by anyone with the necessary computer capability, precisely the danger that
Apple had warned about when it refused to cooperate with the FBI in the first place.
Most of the U.S. mainstream media has been reluctant to speculate on who the third party that
aided the FBI might be but the Israeli press has not been so reticent. They
have
identified a company called Cellebrite, a digital forensics company located in Israel. It is
reported that the company's executive vice president for mobile forensics Leeor Ben-Peretz was recently
in Washington consulting with clients. Ben-Peretz is Cellebrite's marketing chief, fully capable
of demonstrating the company's forensics capabilities. Cellebrite reportedly has worked with the
FBI before, having had a
contract arrangement entered into in 2013 to provide decryption services.
Cellebrite was purchased by Japanese cellular telephone giant Suncorporation in 2007 but it is
still headquartered and managed from Petah Tikva, Israel with a North American office in Parsippany,
New Jersey and branches in Germany, Singapore and Brazil. It works closely with the Israeli police
and intelligence services and is reported to have ties to both Mossad and Shin Bet. Many of its employees
are former Israeli government employees who had worked in cybersecurity and telecommunications.
If Cellebrite is indeed the "third party" responsible for the breakthrough on the Apple problem,
it must lead to speculation that the key to circumventing iPhone security is already out there in
the small world of top level telecommunications forensic experts. It might reasonably be assumed
that the Israeli government has access to the necessary technology, as well as Cellebrite's Japanese
owners. From there, the possibilities inevitably multiply.
Most countries obtain much of their high grade intelligence from communications intercepts. Countries
like Israel, China, and France conduct much of their high-tech spying through exploitation of their
corporate presence in the United States. Israel, in particular, is heavily embedded in the telecommunications
industry, which permits direct access to confidential exchanges of information.
Israel has in fact a somewhat
shady reputation in the United
States when it comes to telecommunications spying. Two companies in particular-Amdocs and Comverse
Infosys-have at times dominated their market niches in America. Amdocs,
which has contracts with many of the largest telephone companies in the U.S. that together handle
90 percent of all calls made, logs all calls that go out and come in on the system. It does not retain
the conversations themselves, but the records provide patterns, referred to as "traffic analysis,"
that can provide intelligence leads. In 1999, the National Security Agency warned that records of
calls made in the United States were winding up in Israel.
Comverse Infosys, which
dissolved in 2013
after charges of conspiracy, fraud, money laundering and making false filings, provided wiretapping
equipment to law enforcement throughout the United States. Because equipment used to tap phones for
law enforcement is integrated into the networks that phone companies operate, it cannot be detected.
Phone calls were intercepted, recorded, stored, and transmitted to investigators by Comverse, which
claimed that it had to be "hands on" with its equipment to maintain the system. Many experts believe
that it is relatively easy to create an internal cross switch that permits the recording to be sent
to a second party, unknown to the authorized law-enforcement recipient. Comverse
was also believed to be involved with NSA on a program of illegal spying directed against American
citizens.
Comverse equipment was never inspected by FBI or NSA experts to determine whether the information
it collected could be leaked, reportedly because senior government managers blocked such inquiries.
According to a Fox News investigative
report, which was later deleted from Fox's website under pressure from various pro-Israel groups,
DEA and FBI sources said post-9/11 that even to suggest that Israel might have been spying using
Comverse was "considered career suicide."
Some might argue that collecting intelligence is a function of government and that espionage,
even between friends, will always take place. When it comes to smartphones, technical advances in
phone security will provide a silver bullet for a time but the hackers, and governments, will inevitably
catch up. One might assume that the recent revelations about the FBI's capabilities vis-à-vis the
iPhone indicate that the horse is already out of the stable. If Israel was party to the breaking
of the security and has the technology it will use it. If the FBI has it, it will share it with other
government agencies and even with foreign intelligence and security services.
Absent from the discussion regarding Apple are the
more than 80 percent of smartphones used worldwide that employ the Google developed Android operating
system that has its own distinct security features designed to block government intrusion. The FBI
is clearly driven by the assumption that all smartphones should be accessible to law enforcement.
The next big telecommunications security court case might well be directed against Google.
Philip Giraldi, a former CIA officer, is executive director of the Council for the National
Interest.
PoasterToaster
Thu, 03/31/2016 - 23:43 |
7389203
You can't just clear a cookie. Google builds a permanent
profile on you and stores it at their end. They use a variety
of means to do this, such as taking your MAC address and every
other bit transmitted on the internet and linking it to a
database they have built that records your popular searches and
clicks.
This is how people get filter bubbled and steered; dirty
internet searches. A clean search would see actual societal
interests and trends instead of the contrived ones pushed by the
State narrative. It's also part of the meta- and direct data
that goes into secret profiles in the "intelligence community".
They think they can use this trendy (yet largely mythical)
Big Data to create a precrime division. It's also nice to have
dirt on the whole country in case anyone gets out of line and
challenges the aristocracy.
wee-weed up
Yep, war has always been the best automatic "go to"
solution to deflect attention away from elite politician's
gross malfeasance.
Notable quotes:
"... And he reminds us that governments also have unprecedented potential to surveil their populations at a moment's notice, without anyone ever realizing what's happening. ..."
"There's a very real difference between allegiance to country–allegiance to people–than allegiance
to state, which is what nationalism today is really more about," says Edward Snowden. On February
20, the whistleblowing cybersecurity expert addressed a wide range of questions during an in-depth
interview with Reason's Nick Gillespie at Liberty Forum, a gathering of the Free State Project (FSP)
in Manchester, New Hampshire.
FSP seeks to move 20,000 people over the next five years to New Hampshire, where they will secure
"liberty in our lifetime" by affecting the political, economic, and cultural climate of the state.
Over 1,900 members have already migrated to the state and their impact is already being felt. Among
their achievements to date:
getting 15 of their brethren in the state House, challenging anti-ridehail laws, fighting in court
for outre religious liberty, winning legal battles over taping cops, being mocked by Colbert for
heroically paying off people's parking meters, hosting cool anything goes festivals for libertarians,
nullifying pot juries, and inducing occasional pants-wetting absurd paranoia in local statists.
Snowden's cautionary tale about the the dangers of state surveillance wasn't lost on his audience
of libertarians and anarchists who reside in the "Live Free or Die" state. He believes that technology
has given rise to unprecedented freedom for individuals around the world-but he says so from an undisclosed
location in authoritarian Russia.
And he reminds us that governments also have unprecedented potential to surveil their populations
at a moment's notice, without anyone ever realizing what's happening.
"They know more about us than they ever have in the history of the United States," Snowden
warns. "They're excusing themselves from accountability to us at the same time they're trying to
exert greater power over us."
In the midst of a fiercely contested presidential race, Snowden remains steadfast in his distrust
of partisan politics and declined to endorse any particular candidate or party, or even to label
his beliefs. "I do see sort of a clear distinction between people who have a larger faith in liberties
and rights than they do in states and institutions," he grants. "And this would be sort of the authoritarian/libertarian
axis in the traditional sense. And I do think it's clear that if you believe in the progressive liberal
tradition, which is that people should have greater capability to act freely, to make their own choices,
to enjoy a better and freer life over the progression of sort of human life, you're going to be pushing
away from that authoritarian axis at all times."
Snowden drews laughs when asked if he was eligible to vote via absentee ballot. "This is still
a topic of...active research," he deadpans.
But he stresses that the U.S. government can win back trust and confidence through rigorous accountability
to citizens and by living up to the ideals on which the country was founded. "We don't want Russia
or China or North Korea or Iran or France or Germany or Brazil or any other country in the world
to hold us up as an example for why we should be narrowing the boundaries of liberty around the world
instead of expanding them," says Snowden.
Runs about 50 minutes.
TABLE OF CONTENTS
0:00 - Edward Snowden, welcome to New Hampshire. Meet the Free State Project.
0:53 - Apple vs. the Federal Bureau of Investigation. Why should strong encryption be legal?
5:02 - Is privacy dead? Should we just get over it?
10:48 - What would a legal and effective government surveillance program look like?
14:53 - Could we have stopped the slide into mass surveillance? Shouldn't we have seen it coming?
19:04 - How can government earn back the trust and confidence of the American people?
21:40 - What's wrong with our political parties?
24:27 - What are Snowden's political beliefs? Is he a libertarian?
26:27 - How did Snowden educate himself? Is he helped or hurt by his lack of formal education?
28:48 - Why did Snowden see bulk surveillance differently than his NSA co-workers?
33:03 - Was the NSA involved in gathering evidence against Ross Ulbricht?
35:39 - Will the government eventually give up fighting internet commerce? Or will they just
change tactics?
37:32 - How can Snowden advocate freedom from a place like Russia?
41:00 - How should we teach children about the Internet?
43:43 - Under what conditions would Snowden return to the United States?
Go here for full transcript, downloadable versions, and more links and videos:
http://reason.com/reasontv/2016/02/25...
Produced by Todd Krainin and Nick Gillespie. Cameras by Meredith Bragg and Krainin.
Visit http://reason.com/reasontv/2016/02/22...
for full text, links, and downloadable versions. And subscribe to Reason TV to be notified when new
videos are released.
jabbermocky
As an analytical thinker, communicator and recovering professional journalist, I can thoroughly
appreciate Ed Snowden's take on the benefits of using pseudonyms when releasing potentially incendiary
ideas to the greater population. Fairly sure we both know that no critical thinking goes unpunished
in America these days. Mission 1: Stay safe!
Michael O'Rourke
Being a former Army Ranger I find it difficult to understand how Americans support the
Right to bear Arms but not the Right of Free speech and Privacy of communication. all three
amendments have equal rights. While I don't agree with how Snowden leaked the 1984
Surveillance Corporations, I'm glad he did. Sua sponte, Uncle Mike
Robert Van Tuinen2
I am. the government intentionally hid this information and discredited and fire previous
whistleblowers. What he did was right and necessary.
Q Queuenstein
"We want a government that is...small...and legitimate". SPEAK FOR YOURSELF! GOVERNMENT IS
THE OPPOSITE OF LEGITIMATE. Government is a monopoly on violent coercive force, no matter how
small. "Representing the people" is impossible without perpetrating evil on a large
percentage. Demand 100% voluntary interaction now. No government=no rulers. We are not a
government of law when The Constitution is up for "interpretation". The government is the
biggest breach of contract and coersive force ever perpetrated on people. It's historical
existance does not argue for its continued existance. Think: zero coersion. Pessimistic? Me
too, but look at the social change enabled by digital communication. Look at the Free State
Project, Look at cryptography; We may at least find a piece of freedom in this world of
coersion and distrust. Things are bad but we are bound to hit bottom. Please applause.j/k.
robinbuster
amazing! This person's value system, sense of morality, loyalty to humanity and liberty is
admirable. The people are starving for politicians with that kind of ethos. I wish Ron Paul
run for president. I kinda like Bernie Sanders most out of the options offered in this
election.
Vlad Ratzen2
snowden said "im an engineer not a politican". when you listen to Ed Snowden, you must
recognize that he is in fact a great philosopher.
when i listen to his answers when he was asked about the apple case. the things he said are
exactly right without a single flaw in his descriptions. he described every single aspect and
he showed us by doing that, what the apple case is really all about.
he points out: it is important to make sure that a goverment does not allow backdors in
encryption, but we have also to accept the reality that we are simply unable to protect us
against the NSA surveillance apparatus. again snowden talks about NSAs (in my opinion) the
very dangerous ability to store all communication data in advance. by the way: Russ Tice said
more then once "they store everything indefinitely".
what Snowden said about the apple case destroys the sophisticated narrative the media has
created on purpose to suggest that surveillance can be avoided somehow. there is a nice
article on reason.com talking in detail about the Apple case, and how it was planned well in
advance.
if i had a single chance to ask mr snowden one question i would ask him "Mr Snowden, do you
believe what the goverment has told us about 9/11"? i am sure there was enough time for mr
snowden to listen to a guy named David Chandler, or to take a look at the movie "HYPOTHESIS"
for example.
it might be interesting to watch his reaction.
Fork Unsa1
If EVERY gubermant agency had ONE person with BALLS like Snowden and told the truth about
tyranny the American people (not to be confused with it's slimeball government) would be on
the good path to taking our Republic back. Those who perform unconstitutional tasks, or
enforce unconstitutional laws against their fellow Americans are TRAITORS and the modern day
equivalent to Hitlers SS.
dman john2
Edward Snowden is a gifted outlier, born with genius brain. How I wish to be born with such
mind.
Video... on 12.30 some assessment of Hilary email scandals. he think that she should face
criminal procecution for mishanding emails while being Secretery State...
UPDATE 9/05/2015: In a rare exclusive interview from Russia, Edward Snowden states he would come
back to the United States if he was guaranteed a fair trial. A fair trial is unlikely says ex-whistle-blower,
Daniel Ellsberg. He would not be allowed to confront his accusers. He would not be allowed to testify
in front of a jury. It would be like a closed military tribunal, and he would be locked up with no
detailed press coverage.
tags: update, edward snowden, hillary clinton, whistle blower, NSA, barack obama
Jason
,
March 7, 2016 at 5:44 pm
Using a decent VPN for everything is rapidly becoming a must. It probably won't protect
you from the NSA, but it will do the job of protecting you from your own ISP.
That you have to protect yourself from your ISP is becoming just one more part of the
sad reality that is the modern United States.
Reply
↓
NeqNeq
,
March 7, 2016 at 6:09 pm
+1 to the VPNs.
I would say Tor is about as good except that Google, Akami, and Cloudflare sites (cough
NC cough) regularly block Tor exit nodes. Still, you get a little more hardening using Tor
browser than other browsers (using defaults).
bob
,
March 7, 2016 at 6:24 pm
"Verizon Wireless" Even if it were possible to use a VPN with a phone, it would still be
affected. It's a MITM (man in the middle) attack.
The story talks about verizon wireless, not what would be called an ISP by most people-
home internet. Fios, time warner, Comcast…etc
Tor? Hahahahahahaha
Jump right into that military intel briar patch, for security®.
NeqNeq
,
March 7, 2016 at 6:53 pm
Umm… I am not sure if you confusing VPN with something else, but yes. Its trivially easy
to use VPN with almost any smartphone.
As for Tor: i agree that State sponsor surveillance is still a risk, but as noted above,
the topic was ISPs (and i mentioned websites). When you use a phone, your carrier acts as
the ISP.
Reply
↓
NeqNeq
,
March 7, 2016 at 7:02 pm
Oh and for those who might care…
The header with your unique identifier can be scrubbed out when your using a VPN. Verizon
only sees that you "went" to the VPN address…all sites you visit see you as coming from the
VPN address. Neither the two shall meet without further snooping (which is not covered by the
injection Verizon does…that we know of).
Pat
,
March 7, 2016 at 3:59 pm
Damn, I knew I should have gone through the process to remove the drm from my e books. I might
have to look into doing that immediately. But first I should check how my couple of nook newstand
subscriptions will be handled.
Whew, I have time. That is in the UK. Still a good warning shot over the bow…
Benedict@Large
,
March 7, 2016 at 4:07 pm
"… But U.S. critics say that could allow foreign companies to use the agreement to invalidate
U.S. safety rules and regulations."
One thing no one much mentions is that the TPP allows
foreign
corporations the
ability to sue to invalidate regulations, but does not all local corporations the same. In
this, TPP privileges foreign over local production, and ensures a race to the bottom on product
place of origin.
hunkerdown
,
March 7, 2016 at 7:40 pm
"A Party may exclude from patentability inventions, the prevention within their
territory of the commercial exploitation of which is necessary to protect ordre public
or morality, including to protect human, animal or plant life or health or to avoid
serious prejudice to nature or the environment, provided that such exclusion is not
made merely because the exploitation is prohibited by its law."
I thought I saw the word morality some place else in the TPP, but apparently, the IP chapter
was the only place. Bad research on my part! In any case, beware the ratchet clauses and the
enemies within, lest your health system become just "Canadian™" enough for the world market.
Notable quotes:
"... The American public has been living under collective Stockholm syndrome. The have secretly been deceived and betrayed while our freedoms, rights and national security has been compromised. The surveillance state was never for our protection. ..."
"... Various rogue agencies have intentionally and illegally subverted our constitution, rights and freedoms while secretly targeting Americans committing various crimes, including murder. ..."
"... When Clapper says "they might" then they are already doing so. ..."
"... Tea party never was. It always was promoted by the media and big business. Financed by the same. Look at the coverage: Occupy was ridiculed by big Media into no existence. Not the same at all. ..."
"... USSR has won! Now we treat our people the same way they did. Soon we can blackmail everyone into compliance. And we can easily plant evidence should we not find any - if they're in they can do anything they want. ..."
"... She is an opportunist, not a feminist. ..."
"... Ban Ki Moon and the Pope saying capitalism is destroying the life AND economy of the entire fricken globe, may be an opportunity for a popular movement, and this Bernie thing has the potential to be part of a wake up moment. ..."
"... I said I wouldn't ever do that again after O'bummer, but as Woodie Guthrie said, Hope is what makes us human and is the driver of evolution. Or something like that. ..."
"... You lost me on "equality is women having all the same opportunities as men". Actually many of us want entirely different "opportunities" and these women who play the patriarch, like Thatcher and Rice, and Shillary, do not represent the diverse and rich culture of "feminism" that is enmeshed in people's real lives. ..."
"... I'm an aussie and I can tell you America Bernie Sanders is what you need to keep you guys from becoming a laughing stock. Hillary, trump is on the same brush as the elitist of your country. Bernie may or not be able to do what he wants to as he will get stonewalled but if everyone is united and keeps fighting with him they will have no choice to implement some of them. ..."
Fgt 4URIGHTS, 2016-02-09 22:59:16
The American public has been living under collective Stockholm syndrome. The have secretly
been deceived and betrayed while our freedoms, rights and national security has been compromised.
The surveillance state was never for our protection.
https://www.youtube.com/watch?v=Kg1-vao5Ta8
Various rogue agencies have intentionally and illegally subverted our constitution, rights
and freedoms while secretly targeting Americans committing various crimes, including murder.
YeeofLittleFaith ->
Individualist
, 2016-02-09 22:37:44
I'll say this, if this inevitable surveillance can prevent actual criminals from committing
actual crimes, it might be useful.
And I'll say this: if that is the intention of these devices - and if your bog-standard criminal
is ever caught using them - I'll eat your smart fridge.
neiman1 ->
JinTexas
, 2016-02-09 22:29:54
When Clapper says "they might" then they are already doing so.
Hillary Assad ,
2016-02-09 22:26:15
Surveillance video of San Bernardino released on 01/05/16 Enjoy!!
https://www.youtube.com/watch?v=tHH7gvHXLzQ
mirandawest ->
Dan B
, 2016-02-09 22:20:40
Tea party never was. It always was promoted by the media and big business. Financed by the same.
Look at the coverage: Occupy was ridiculed by big Media into no existence. Not the same at all.
mirandawest ->
John
Leehane , 2016-02-09 22:15:38
USSR has won! Now we treat our people the same way they did. Soon we can blackmail everyone into
compliance. And we can easily plant evidence should we not find any - if they're in they can do
anything they want.
bcarey ->
harrywarren
, 2016-02-09 20:53:30
She is an opportunist, not a feminist.
Absolutely correct.
(And a panderer.)
Lisa Wood ->
kirili,
2016-02-10 07:17:32
Hear ya, I plan to hold him to the fire. I'm a realist, and married to an uber realist, so not
gonna argue with ya here, but, as this article actually says really well, is that the holistic
embrace of all inequity opens the landscape to the big conversations we do Need to have right
now.
I know i know, the UN is at one hand a weak tool and on the other a NWO franchise, but
Ban Ki Moon and the Pope saying capitalism is destroying the life AND economy of the entire fricken
globe, may be an opportunity for a popular movement, and this Bernie thing has the potential to
be part of a wake up moment.
I have let my Hope thing vibrate a bit, and I said I wouldn't ever
do that again after O'bummer, but as Woodie Guthrie said, Hope is what makes us human and is the
driver of evolution. Or something like that.
Lisa Wood
->
MajorMalaise
, 2016-02-10 07:08:42
You lost me on "equality is women having all the same opportunities as men". Actually many of
us want entirely different "opportunities" and these women who play the patriarch, like Thatcher
and Rice, and Shillary, do not represent the diverse and rich culture of "feminism" that is enmeshed
in people's real lives.
keepinitreal2000,
2016-02-10 06:12:18
I'm an aussie and I can tell you America Bernie Sanders is what you need to keep you guys from
becoming a laughing stock. Hillary, trump is on the same brush as the elitist of your country.
Bernie may or not be able to do what he wants to as he will get stonewalled but if everyone is
united and keeps fighting with him they will have no choice to implement some of them.
As an Aussie
it is important that his message is heard and implemented as America can then show the world there
is good in the world and that we all can live in a fair, just and equal world. Something America
has stopped showing for a very longtime. This hopefully will filter down to other countries as
America rightly or wrongly leads the world and many countries do follow suit.
Notable quotes:
"... Oh, but it is serious. The material is/was classified. It just wasn't marked as such. Which means someone removed the classified material from a separate secure network and sent it to Hilary. We know from her other emails that, on more than one occasion, she requested that that be done. ..."
"... fellow diplomats and other specialists said on Thursday that if any emails were blatantly of a sensitive nature, she could have been expected to flag it. "She might have had some responsibility to blow the whistle," said former Ambassador Thomas Pickering, "The recipient may have an induced kind of responsibility," Pickering added, "if they see something that appears to be a serious breach of security." ..."
"... Finally whether they were marked or not the fact that an electronic copy resided on a server in an insecure location was basically like her making a copy and bringing it home and plunking it in a file cabinet... ..."
"... In Section 7 of her NDA, Clinton agreed to return any classified information she gained access to, and further agreed that failure to do so could be punished under Sections 793 and 1924 of the US Criminal Code. ..."
"... The agreement considers information classified whether it is "marked or unmarked." ..."
"... According to a State Department regulation in effect during Clinton's tenure (12 FAM 531), "classified material should not be stored at a facility outside the chancery, consulate, etc., merely for convenience." ..."
"... Additionally, a regulation established in 2012 (12 FAM 533.2) requires that "each employee, irrespective of rank must certify" that classified information "is not in their household or personal effects." ..."
"... As of December 2, 2009, the Foreign Affairs Manual has explicitly stated that "classified processing and/or classified conversation on a PDA is prohibited." ..."
"... Look, Hillary is sloppy about her affairs of state. She voted with Cheney for the Iraq disaster and jumped in supporting it. It is the greatest foreign affair disaster since Viet Nam and probably the greatest, period! She was a big proponent of getting rid of Khadaffi in Libya and now we have radical Islamic anarchy ravaging the failed state. She was all for the Arab Spring until the Muslim Brotherhood was voted into power in Egypt....which was replaced by yet another military dictatorship we support. And she had to have her own private e-mail server and it got used for questionable handling of state secrets. This is just Hillary being Hillary........ ..."
"... Its no secret that this hysterically ambitious Clinton woman is a warmonger and a hooker for Wall Street . No need to read her e-mails, just check her record. ..."
"... What was exemplary about an unnecessary war, a dumbass victory speech three or so months into it, the President's absence of support for his CIA agent outed by his staff, the President's German Chancellor shoulder massage, the use of RNC servers and subsequently "lost" gazillion emails, doing nothing in response to Twin Towers news, ditto for Katrina news, the withheld information from the Tillman family, and sanctioned torture? ..."
"... Another point that has perhaps not been covered sufficiently is the constant use of the phrase "unsecured email server" - which is intentionally vague and misleading and was almost certainly a phrase coined by someone who knows nothing about email servers or IT security and has been parroted mindlessly by people who know even less and journalists who should know better. ..."
"... Yet the term "unsecured" has many different meanings and implications - in the context of an email server it could mean that mail accounts are accessible without authentication, but in terms of network security it could mean that the server somehow existed outside a firewall or Virtual Private Network or some other form of physical or logical security. ..."
"... It is also extremely improbable that an email server would be the only device sharing that network segment - of necessity there would at least be a file server and some means of communicating with the outside world, most likely a router or a switch, which would by default have a built-in hardware firewall (way more secure than a software firewall). ..."
"... Anything generated related to a SAP is, by it's mere existence, classified at the most extreme level, and everyone who works on a SAP knows this intimately and you sign your life away to acknowledge this. ..."
"... yeah appointed by Obama...John Kerry. His state department. John is credited on both sides of the aisle of actually coming in and making the necessary changes to clean up the administrative mess either created or not addressed by his predecessor. ..."
"... Its not hard to understand, she was supposed to only use her official email account maintained on secure Federal government servers when conducting official business during her tenure as Secretary of State. This was for three reasons, the first being security the second being transparency and the third for accountability. ..."
"... You need to share that one with Petraeus, whos career was ruined and had to pay 100k in fines, for letting some info slip to his mistress.. ..."
"... If every corrupt liar was sent to prison there'd be no one left in Washington, or Westminster and we'd have to have elections with ordinary people standing, instead of the usual suspects from the political class. Which, on reflection, sounds quite good -- ..."
"... It's a reckless arrogance combined with the belief that no-one can touch her. If she does become the nominee Hillary will be an easy target for Trump. It'll be like "shooting fish in a barrel". ..."
"... It is obvious that the Secretary of State and the President should be communicating on a secure network controlled by the federal government. It is obvious that virtually none of these communications were done in a secure manner. Consider whether someone who contends this is irrelevant has enough sense to come in out of the rain. ..."
The Obama administration
confirmed for the first time on Friday that Hillary Clinton's unsecured home server contained some
of the US government's most closely guarded secrets, censoring 22 emails with material demanding
one of the highest levels of classification. The revelation comes just three days before the Iowa
presidential nominating caucuses in which Clinton is a candidate.
jrhaddock -> MtnClimber 29 Jan 2016 23:04
Oh, but it is serious. The material is/was classified. It just wasn't marked as such. Which
means someone removed the classified material from a separate secure network and sent it to Hilary.
We know from her other emails that, on more than one occasion, she requested that that be done.
And she's not just some low level clerk who doesn't understand what classified material is
or how it is handled. She had been the wife of the president so is certainly well aware of the
security surrounding classified material. And then she was Sec of State and obviously knew what
kind of information was classified. So to claim that the material wasn't marked, and therefore
she didn't know it was classified, is simply not credulous.
Berkeley2013 29 Jan 2016 22:46
And Clinton had a considerable number of unvetted people maintain and administer her communication
system. The potential for wrong doing in general and blackmail from many angles is great.
There's also the cost of this whole investigation. Why should US taxpayers have to pick up
the bill?
And the waste of good personnel time---a total waste...
Skip Breitmeyer -> simpledino 29 Jan 2016 22:29
In one sense you're absolutely right- read carefully this article (and the announcement leading
to it) raises at least as many questions as it answers, period. On the other hand, those ambiguities
are certain not to be resolved 'over-the-weekend' (nor before the first votes are cast in Iowa)
and thus the timing of the thing could not be more misfortunate for Ms. Clinton, nor more perfect
for maximum effect than if the timing had been deliberately planned. In fact I'm surprised there
aren't a raft of comments on this point. "Confirmed by the Obama administration..."? Who in the
administration? What wing of the administration? Some jack-off in the justice dept. who got 50,000
g's for the scoop? The fact is, I'm actually with Bernie over Hilary any day, but I admit to a
certain respect for her remarkable expertise and debate performances that have really shown the
GOP boys to be a bunch of second-benchers... And there's something a little dirty and dodgy that's
gone on here...
Adamnoggi dusablon 29 Jan 2016 22:23
SAP does not relate to To the level of classification. A special access program could be at
the confidential level or higher dependent upon content. Special access means just that, access
is granted on a case by case basis, regardless of classification level .
Gigi Trala La 29 Jan 2016 22:17
She is treated with remarkable indulgence. Anywhere with a sense of accountability she will
be facing prosecution, and yet here she is running for even higher office. In the middle of demonstrating
her unfitness.
eldudeabides 29 Jan 2016 22:15
Independent experts say it is highly unlikely that Clinton will be charged with wrongdoing,
based on the limited details that have surfaced up to now and the lack of indications that
she intended to break any laws.
since when has ignorance been a defence?
nataliesutler UzzDontSay 29 Jan 2016 22:05
Yes Petraeus did get this kind of scrutiny even though what he did was much less serious that
what Clinton did. this isn't about a rule change. And pretending it is isn't going to fool anyone.
Sam3456 kattw 29 Jan 2016 21:18
Thats a misunderstanding on your part First lets look at Hillary's statement in March:
"I did not email any classified material to anyone on my email. There is no classified
material. So I'm certainly well aware of the classification requirements and did not send classified
material."
She later adjusted her language to note that she never sent anything "marked" classified. So
already some Clinton-esque word parsing
And then what people said who used to do her job:
fellow diplomats and other specialists said on Thursday that if any emails were blatantly
of a sensitive nature, she could have been expected to flag it.
"She might have had some responsibility to blow the whistle," said former Ambassador Thomas Pickering,
"The recipient may have an induced kind of responsibility," Pickering added, "if they see something
that appears to be a serious breach of security."
It is a view shared by J. William Leonard, who between 2002 and 2008 was director of the Information
Security Oversight Office, which oversees the government classification system. He pointed out
that all government officials given a security clearance are required to sign a nondisclosure
agreement, which states they are responsible if secrets leak – whether the information was "marked
or not."
Finally whether they were marked or not the fact that an electronic copy resided on a server
in an insecure location was basically like her making a copy and bringing it home and plunking
it in a file cabinet...
beanierose -> dusablon 29 Jan 2016 21:08
Yeah - I just don't understand what Hillary is actually accused of doing / or not doing in
Benghazi. Was it that they didn't provide support to Stevens - (I think that was debunked) - was
it that they claimed on the Sunday talk shows that the video was responsible for the attack (who
cares). Now - I can think of an outrage - President Bush attacking Iraq on the specious claim
that they had WMD - that was a lie/incorrec/incompetence and it cost ~7000 US and 200K to 700K
Iraqi lives. Now - there's a scandal.
Stephen_Sean -> elexpatrioto 29 Jan 2016 21:07
The Secretary of State is
an "original classifier" of information. The individual holding that office is responsible
to recognize whether information is classified and to what level regardless if it is marked or
not. She should have known. She has no true shelter of ignorance here.
Stephen_Sean 29 Jan 2016 21:00
The Guardian is whistling through the graveyard. The FBI is very close to a decision to recommend
an indictment to the DOJ. At that point is up to POTUS whether he thinks Hillary is worth tainting
his entire Presidency to protect by blocking a DOJ indictment. His responsibility as an outgoing
President is to do what is best for his party and to provide his best attempt to get a Democrat
elected. I smell Biden warming up in the bullpen as an emergency.
The last thing the DNC wants is a delay if their is going to be an indictment. For an indictment
to come after she is nominated would be an unrecoverable blow for the Democrats. If their is to
be an indictment its best for it to come now while they can still get Biden in and maintain their
chances.
Sam3456 29 Jan 2016 20:57
In Section 7 of her NDA, Clinton agreed to return any classified information she gained
access to, and further agreed that failure to do so could be punished under Sections 793 and 1924
of the US Criminal Code.
According To § 793 Of Title 18 Of The US Code, anyone who willfully retains, transmits or causes
to be transmitted, national security information, can face up to ten years in prison.
According To § 1924 Of Title 18 Of The US Code, anyone who removes classified information "
with the intent to retain such documents or materials at an unauthorized location," can face up
to a year in prison.
The agreement considers information classified whether it is "marked or unmarked."
According to a State Department regulation in effect during Clinton's tenure (12 FAM 531), "classified
material should not be stored at a facility outside the chancery, consulate, etc., merely for
convenience."
Additionally, a regulation established in 2012 (12 FAM 533.2) requires that "each employee,
irrespective of rank must certify" that classified information "is not in their household or personal
effects."
As of December 2, 2009, the Foreign Affairs Manual has explicitly stated that "classified
processing and/or classified conversation on a PDA is prohibited."
kus art 29 Jan 2016 20:54
I'm assuming that the censored emails reveal activities that the US government is into are
Way more corrupt, insidious and venal as the the emails already exposed, which says a lot already...
Profhambone -> Bruce Hill 29 Jan 2016 20:53
Look, Hillary is sloppy about her affairs of state. She voted with Cheney for the Iraq
disaster and jumped in supporting it. It is the greatest foreign affair disaster since Viet Nam
and probably the greatest, period! She was a big proponent of getting rid of Khadaffi in Libya
and now we have radical Islamic anarchy ravaging the failed state. She was all for the Arab Spring
until the Muslim Brotherhood was voted into power in Egypt....which was replaced by yet another
military dictatorship we support. And she had to have her own private e-mail server and it got
used for questionable handling of state secrets. This is just Hillary being Hillary........
PsygonnUSA 29 Jan 2016 20:44
Its no secret that this hysterically ambitious Clinton woman is a warmonger and a hooker
for Wall Street . No need to read her e-mails, just check her record.
USfan 29 Jan 2016 20:41
Sorry to be ranting but what does it say about a country - in theory, a democracy - that is
implicated in so much questionable business around the world that we have to classify mountains
of communication as off-limits to the people, who are theoretically sovereign in this country?
We've all gotten quite used to this. In reality, it should freak us out much more than it does.
I'm not naive about what national security requires, but my sense is the government habitually
and routinely classifies all sorts of things the people of this country have every right to know.
Assuming this is still a democracy, which is perhaps a big assumption.
Raleighchopper Bruce Hill 29 Jan 2016 20:40
far Left sites like the Guardian:
LMAOROFL
Scott Trust Ltd board
https://en.wikipedia.org/wiki/Scott_Trust_Limited
- Neil Berkitt – a former banker (Lloyds, St George Bank) who then helped vulture capitalist
Richard Branson with Virgin Media.
- David Pemsel – Former head of marketing at ITV.
- Nick Backhouse – On the board of the bank of Queensland, formerly with Barings Bank.
- Ronan Dunne – On the Telefónica Europe plc board, Chairman of Tesco Mobile. He has also
worked at Banque Nationale de Paris plc.
- Judy Gibbons – Judy is currently a non-executive director of retail property kings Hammerson,
previously with O2, Microsoft, Accel Partners (venture capital), Apple and Hewlett Packard.
- Jennifer Duvalier – Previously in management consultancy and banking.
- Brent Hoberman – Old Etonian with fingers in various venture capital pies including car
rental firm EasyCar.
- Nigel Morris – chairman of network digital marketing giants Aegis Media.
- John Paton – CEO of Digital First Media – a very large media conglomerate which was sued
successfully in the U.S. for rigging advertising rates.
- Katherine Viner – Startlingly not a banker, in marketing or venture capital. She is I gather
(gulp) a journalist.
- Darren Singer – formerly with BSkyB, the BBC and Price Waterhouse Coopers
FirthyB 29 Jan 2016 20:36
Hillary is in that class, along with Goldman Sachs, JP Morgan, Bush, Cheney etc.. who believe
the rule of law only pertains to the little guys.
MooseMcNaulty -> dusablon 29 Jan 2016 20:28
The spying was illegal on a Constitutional basis. The Fourth Amendment protects our privacy
and prevents unlawful search and seizure. The government getting free access to the contents of
our emails seems the same as opening our mail, which is illegal without a court order.
The drone program is illegal based on the Geneva accords. We are carrying out targeted killings
within sovereign nations, usually without their knowledge or consent, based on secret evidence
that they pose a vaguely defined 'imminent threat'. It isn't in line with any international law,
though we set that precedent long ago.
makaio USfan 29 Jan 2016 20:08
What was exemplary about an unnecessary war, a dumbass victory speech three or so months
into it, the President's absence of support for his CIA agent outed by his staff, the President's
German Chancellor shoulder massage, the use of RNC servers and subsequently "lost" gazillion emails,
doing nothing in response to Twin Towers news, ditto for Katrina news, the withheld information
from the Tillman family, and sanctioned torture?
Those were just starter questions. I'm sure I missed things.
Raleighchopper -> Popeia 29 Jan 2016 20:05
http://www.reuters.com/article/us-usa-politics-clinton-idUSN2540811420080326
Rowan Walters 29 Jan 2016 19:51
Another point that has perhaps not been covered sufficiently is the constant use of the
phrase "unsecured email server" - which is intentionally vague and misleading and was almost certainly
a phrase coined by someone who knows nothing about email servers or IT security and has been parroted
mindlessly by people who know even less and journalists who should know better.
As an IT professional the repeated use of a phrase like that is a red flag - it's like when
people who don't know what they're talking about latch on to a phrase which sounds technical because
it contains jargon or technical concepts and they use it to make it sound like they know what
they're talking about but it doesn't actually mean anything unless the context is clear and unambiguous.
The phrase is obviously being repeated to convey the impression of supreme negligence - that
sensitive state secrets were left defenceless and (gasp!) potentially accessible by anyone.
Yet the term "unsecured" has many different meanings and implications - in the context
of an email server it could mean that mail accounts are accessible without authentication, but
in terms of network security it could mean that the server somehow existed outside a firewall
or Virtual Private Network or some other form of physical or logical security.
Does this term "unsecured" mean the data on the server was not password-protected, does it
mean it was unencrypted, does it mean that it was totally unprotected (which is extremely unlikely
even if it was installed by an ignorant Luddite given that any modern broadband modem is also
a hardware firewall), and as for the "server" was it a physical box or a virtual server?
It is also extremely improbable that an email server would be the only device sharing that
network segment - of necessity there would at least be a file server and some means of communicating
with the outside world, most likely a router or a switch, which would by default have a built-in
hardware firewall (way more secure than a software firewall).
And regarding the "unsecured" part, how was the network accessed?
There are a huge number of possibilities as to the actual meaning and on its own there is not
enough information to deduce which - if any - is correct.
I suspect that someone who knows little to nothing about technology has invented this concept
based on ignorance a desire to imply malfeasance because on its own it really is a nonsense term.
seanet1310 -> Wallabyfan 29 Jan 2016 19:37
Nope. Like it or not Manning deliberately took classified information, smuggled it out and
gave it to foreign nationals.
Clinton it would appear mishandled classified material, at best she failed to realise the sensitive
nature and at worst actively took material from controlled and classified networks onto an unsecured
private network.
dusablon 29 Jan 2016 19:28
Classified material in the US is classified at three levels: confidential, secret, and top
secret. Those labels are not applied in a cavalier fashion. The release of TS information is considered
a grave threat to the security of the United States.
Above these classification levels is what is as known as Special Access Program information,
the release of which has extremely grave ramifications for the US. Access to SAP material is extremely
limited and only granted after an extensive personal background investigation and only on a 'need
to know' basis. You don't simply get a SAP program clearance because your employer thinks it would
be nice to have, etc. In fact, you can have a Top Secret clearance and never get a special access
program clearance to go with it.
For those of you playing at home, the Top Secret SAP material Hillary had on her server - the
most critical material the US can have - was not simply 'upgraded' to classified in a routine
bureaucratic exercise because it was previously unclassified.
Anything generated related to a SAP is, by it's mere existence, classified at the most
extreme level, and everyone who works on a SAP knows this intimately and you sign your life away
to acknowledge this.
What the Feds did in Hillary's case in making the material on her home-based server Top Secret
SAP was to bring those materials into what is known as 'accountability .'
That is, the material was always SAP material but it was just discovered outside a SAP lock-down
area or secure system and now it must become 'accountable' at the high classification level to
ensure it's protected from further disclosure.
Hillary and her minions have no excuse whatsoever for this intentional mishandling of this
critical material and are in severe legal jeopardy no matter what disinformation her campaign
puts out. Someone will or should go to prison. Period.
(Sorry for the length of the post)
Sam3456 -> Mark Forrester 29 Jan 2016 19:22
yeah appointed by Obama...John Kerry. His state department. John is credited on both sides
of the aisle of actually coming in and making the necessary changes to clean up the administrative
mess either created or not addressed by his predecessor.
Within weeks of taking the position JK implemented the OIG task forces recommendations to streamline
the process and make State run more in line with other government organizations. I think John
saw the "Sorry it snowed can't have you this info for a month" for what it was and acted out of
decency and fairness to the American people. I still think he looks like a hound and is a political
opportunist but you can't blame him for shenanigans here
chiefwiley -> DoktahZ 29 Jan 2016 19:18
The messages were "de-papered" by the staff, stripping them from their forms and headings and
then scanning and including the content in accumulations to be sent and stored in an unclassified
system. Taking the markings off of a classified document does not render it unclassified. Adding
the markings back onto the documents does not "declare" them classified. Their classified nature
was constant.
If you only have an unsecured system, it should never be used for official traffic, let alone
classified or special access traffic.
dusablon -> MtnClimber 29 Jan 2016 19:05
Give it up.
She used a private server deliberately to avoid FOIA requests, she deleted thousands of emails
after they were requested, and the emails that remained contained Top Secret Special Access Program
information, and it does not matter one iota whether or not that material was marked or whether
or not it has been recently classified appropriately.
chiefwiley -> Exceptionalism 29 Jan 2016 19:04
18USC Section793(f)
$250,000 and ten years.
dusablon -> MtnClimber 29 Jan 2016 19:00
False.
Anything related to a special access program is classified whether marked as such or not.
dalisnewcar 29 Jan 2016 18:58
You would figure that after all the lies of O'bomber that democrats might wake up some. Apparently,
they are too stupid to realize they have been duped even after the entire Middle Class has been
decimated and the wealth of the 1% has grown 3 fold under the man who has now bombed 7 countries.
And you folks think Clinton, who personally destroyed Libya, is going to be honest with you and
not do the same things he's done? Wake up folks. Your banging your head against the same old wall.
fanUS -> MtnClimber 29 Jan 2016 18:46
She is evil, because she helped Islamic State to rise.
Paul Christenson -> Barry_Seal 29 Jan 2016 18:45
20 - Barbara Wise - Commerce Department staffer. Worked closely with Ron Brown and John Huang.
Cause of death unknown. Died November 29, 1996. Her bruised, nude body was found locked in her
office at the Department of Commerce.
21 - Charles Meissner - Assistant Secretary of Commerce who gave John Huang special security
clearance, died shortly thereafter in a small plane crash.
22 - Dr. Stanley Heard - Chairman of the National Chiropractic Health Care Advisory Committee
died with his attorney Steve Dickson in a small plane crash. Dr. Heard, in addition to serving
on Clinton 's advisory council personally treated Clinton 's mother, stepfather and Brother.
23 - Barry Seal - Drug running TWA pilot out of Mean Arkansas , death was no accident.
24 - John ny Lawhorn, Jr. - Mechanic, found a check made out to Bill Clinton in the trunk of
a car left at his repair shop. He was found dead after his car had hit a utility pole.
25 - Stanley Huggins - Investigated Madison Guaranty. His death was a purported suicide and
his report was never released.
26 - Hershel Friday - Attorney and Clinton fundraiser died March 1, 1994, when his plane exploded.
27 - Kevin Ives & Don Henry - Known as "The boys on the track" case. Reports say the two boys
may have stumbled upon the Mena Arkansas airport drug operation. The initial report of death said
their deaths were due to falling asleep on railroad tracks and being run over. Later autopsy reports
stated that the 2 boys had been slain before being placed on the tracks. Many linked to the case
died before their testimony could come before a Grand Jury.
THE FOLLOWING PERSONS HAD INFORMATION ON THE IVES/HENRY CASE:
28 - Keith Coney - Died when his motorcycle slammed into the back of a truck, 7/88.
29 - Keith McMaskle - Died, stabbed 113 times, Nov 1988
30 - Gregory Collins - Died from a gunshot wound January 1989.
31 - Jeff Rhodes - He was shot, mutilated and found burned in a trash dump in April 1989. (Coroner
ruled death due to suicide)
32 - James Milan - Found decapitated. However, the Coroner ruled his death was due to natural
causes"?
33 - Jordan Kettleson - Was found shot to death in the front seat of his pickup truck in June
1990.
34 - Richard Winters - A suspect in the Ives/Henry deaths. He was killed in a set-up robbery
July 1989.
THE FOLLOWING CLINTON PERSONAL BODYGUARDS ALL DIED OF MYSTERIOUS CAUSES OR SUICIDE
36 - Major William S. Barkley, Jr.
37 - Captain Scott J . Reynolds
38 - Sgt. Brian Hanley
39 - Sgt. Tim Sabel
40 - Major General William Robertson
41 - Col. William Densberger
42 - Col. Robert Kelly
43 - Spec. Gary Rhodes
44 - Steve Willis
45 - Robert Williams
46 - Conway LeBleu
47 - Todd McKeehan
And this list does not include the four dead Americans in Benghazi that Hillary abandoned!
Paul Christenson Barry_Seal 29 Jan 2016 18:42
THE MANY CLINTON BODY BAGS . . .
Someone recently reminded me of this list. I had forgotten how long it is. Therefore, this
is a quick refresher course, lest we forget what has happened to many "friends" and associates
of Bill and Hillary Clinton.
1- James McDougal - Convicted Whitewater partner of the Clintons who died of an apparent heart
attack, while in solitary confinement. He was a key witness in Ken Starr's investigation.
2 - Mary Mahoney - A former White House intern was murdered July 1997 at a Starbucks Coffee
Shop in Georgetown (Washington, D. C.). The murder happened just after she was to go public with
her story of sexual harassment by Clinton in the White House.
3 - Vince Foster - Former White House Councilor, and colleague of Hillary Clinton at Little
Rock 's Rose Law Firm. Died of a gunshot wound to the head, ruled a suicide. (He was about to
testify against Hillary related to the records she refused to turn over to congress.) Was reported
to have been having an affair with Hillary.
4 - Ron Brown - Secretary of Commerce and former DNC Chairman. Reported to have died by impact
in a plane crash. A pathologist close to the investigation reported that there was a hole in the
top of Brown's skull resembling a gunshot wound. At the time of his death Brown was being investigated,
and spoke publicly of his willingness to cut a deal with prosecutors. The rest of the people on
the plane also died. A few days later the Air Traffic controller committed suicide.
5 - C. Victor Raiser, II - Raiser, a major player in the Clinton fund raising organization
died in a private plane crash in July 1992.
6 - Paul Tulley - Democratic National Committee Political Director found dead in a hotel room
in Little Rock on September 1992. Described by Clinton as a "dear friend and trusted advisor".
7 - Ed Willey - Clinton fundraiser, found dead November 1993 deep in the woods in VA of a gunshot
wound to the head. Ruled a suicide. Ed Willey died on the same day His wife Kathleen Willey claimed
Bill Clinton groped her in the oval office in the White House. Ed Willey was involved in several
Clinton fund raising events.
8 - Jerry Parks - Head of Clinton's gubernatorial security team in Little Rock .. Gunned down
in his car at a deserted intersection outside Little Rock . Park's son said his father was building
a dossier on Clinton . He allegedly threatened to reveal this information. After he died the files
were mysteriously removed from his house.
9 - James Bunch - Died from a gunshot suicide. It was reported that he had a "Black Book" of
people which contained names of influential people who visited Prostitutes in Texas and Arkansas
10 - James Wilson - Was found dead in May 1993 from an apparent hanging suicide. He was reported
to have ties to the Clintons ' Whitewater deals.
11 - Kathy Ferguson - Ex-wife of Arkansas Trooper Danny Ferguson , was found dead in May 1994,
in her living room with a gunshot to her head. It was ruled a suicide even though there were several
packed suitcases, as if she were going somewhere. Danny Ferguson was a co-defendant along with
Bill Clinton in the Paula Jones Lawsuit, and Kathy Ferguson was a possible corroborating witness
for Paula Jones.
12 - Bill Shelton - Arkansas State Trooper and fiancée of Kathy Ferguson. Critical of the suicide
ruling of his fiancée, he was found dead in June, 1994 of a gunshot wound also ruled a suicide
at the grave site of his fiancée.
13 - Gandy Baugh - Attorney for Clinton 's friend Dan Lassater, died by jumping out a window
of a tall building January, 1994. His client, Dan Lassater, was a convicted drug distributor.
14 - Florence Martin - Accountant & sub-contractor for the CIA, was related to the Barry Seal,
Mena , Arkansas Airport drug smuggling case. He died of three gunshot Wounds.
15 - Suzanne Coleman - Reportedly had an affair with Clinton when he was Arkansas Attorney
General. Died Of a gunshot wound to the back of the head, ruled a Suicide. Was pregnant at the
time of her death.
16 - Paula Grober - Clinton 's speech interpreter for the deaf from 1978 until her death December
9, 1992. She died in a one car accident.
17 - Danny Casolaro - Investigative reporter who was Investigating the Mean Airport and Arkansas
Development Finance Authority. He slit his wrists, apparently, in the middle of his investigation.
18 - Paul Wilcher - Attorney investigating corruption at Mean Airport with Casolaro and the
1980 "October Surprise" was found dead on a toilet June 22, 1993, in his Washington DC apartment.
Had delivered a report to Janet Reno 3 weeks before his death. (May have died of poison)
19 - Jon Parnell Walker - Whitewater investigator for Resolution Trust Corp. Jumped to his
death from his Arlington , Virginia apartment balcony August 15,1993. He was investigating the
Morgan Guaranty scandal.
Thijs Buelens -> honey1969 29 Jan 2016 18:41
Did the actors from Orange is the New Black already endorsed Hillary? Just wondering.
Sam3456 -> Sam3456 29 Jan 2016 18:35
Remember as soon as Snowden walked out the door with his USB drive full of secrets his was
in violation. Wether he knew the severity and classification or not.
Think of Hillary's email server as her home USB drive.
RedPillCeryx 29 Jan 2016 18:33
Government civil and military employees working with material at the Top Secret level are required
to undergo incredibly protracted and intrusive vetting procedures (including polygraph testing)
in order to obtain and keep current their security clearances to access such matter. Was Hillary
Clinton required to obtain a Top Secret clearance in the same way, or was she just waved through
because of Who She Is?
Sam3456 29 Jan 2016 18:32
Just to be clear, Colin Powell used a private email ACCOUNT which was hosted in the cloud and
used it only for personal use. He was audited (never deleted anything) and it was found to contain
no government records.
Hillary used a server, which means in electronic form the documents existed outside the State
Department unsecured. Its as if she took a Top Secret file home with her. That is a VERY BIG mistake
and as the Sec of State she signed a document saying she understood the rules and agreed to play
by them. She did not and removing state secrets from their secure location is a very serious matter.
Wether you put the actual file in your briefcase or have them sitting in electronic version on
your server.
Second, she signed a document saying she would return any and ALL documents and copies of documents
pertaining to the State Department with 30 (or 60 I can't remember) of leaving. The documents
on her server, again electronic copies of the top secret files, where not returned for 2 years.
Thats a huge violation.
Finally, there is a clause in classification that deals with the information that is top secret
by nature. Meaning regardless of wether its MARKED classified or not the very nature of the material
would be apparent to a senior official that it was classified and appropriate action would have
to be taken. She she either knew and ignored or did not know...and both of those scenarios don't
give me a lot of confidence.
Finally the information that was classified at the highest levels means exposure of that material
would put human operatives lives at risk. Something she accused Snowden of doing when she called
him a traitor. By putting that information outside the State Department firewall she basically
put peoples lives at risk so she could have the convenience of using one mobile device.
Wallabyfan -> MtnClimber 29 Jan 2016 18:10
Sorry you can delude yourself all you like but Powell and Cheney used private emails while
at work on secure servers for personal communications not highly classified communications and
did so before the 2009 ban on this practice came into place . Clinton has used a private unsecured
server at her home while Sec of State and even worse provided access to people in her team who
had no security clearance. She has also deleted more than 30,000 emails from the server in full
knowledge of the FBI probe. You do realise that she is going to end up in jail don't you?
MtnClimber -> boscovee 29 Jan 2016 18:07
Are you as interested in all of the emails that Cheney destroyed? He was asked to provide them
and never allowed ANY to be seen.
Typical GOP
Dozens die at embassies under Bush. Zero investigations. Zero hearings.
4 die at an embassy under Clinton. Dozens of hearings.
OurNigel -> Robert Greene 29 Jan 2016 17:53
Its not hard to understand, she was supposed to only use her official email account maintained
on secure Federal government servers when conducting official business during her tenure as Secretary
of State. This was for three reasons, the first being security the second being transparency and
the third for accountability.
Serious breach of protocol I'm afraid.
Talgen -> Exceptionalism 29 Jan 2016 17:50
Department responses for classification infractions could include counseling, warnings
or other action, officials said. They wouldn't say if Clinton or senior aides who've since
left government could face penalties. The officials weren't authorized to speak on the matter
and demanded anonymity."
You need to share that one with Petraeus, whos career was ruined and had to pay 100k in
fines, for letting some info slip to his mistress..
Wallabyfan 29 Jan 2016 17:50
No one here seems to be able to accept how serious this is. You cant downplay it. This is the
most serious scandal we have seen in American politics for decades.
Any other US official handling even 1 classified piece of material on his or her own unsecured
home server would have been arrested and jailed by now for about 50 years perhaps longer. The
fact that we are talking about 20 + (at least) indicates at the very least Clinton's hubris, incompetence
and very poor judgement as well as being a very serious breach of US law. Her campaign is doomed.
This is only the beginning of the scandal and I predict we will be rocked when we learn the
truth. Clinton will be indicted and probably jailed along with Huma Abedin who the FBI are also
investigating.
HiramsMaxim -> Exceptionalism 29 Jan 2016 17:50
http://freebeacon.com/wp-content/uploads/2015/11/HRC-SCI-NDA1.pdf
OurNigel 29 Jan 2016 17:42
This is supposed to be the lady who (in her own words) has a huge experience of government
yet she willingly broke not just State Department protocols and procedures, by using a privately
maintained none secure server for her email service she also broke Federal laws and regulations
governing recordkeeping requirements.
At the very least this was a massive breach of security and a total disregard for established
rules whilst she was in office. Its not as if she was just some local government officer in a
backwater town she was Secretary of State for the United States government.
If the NSA is to be believed you should presume her emails could have been read by any foreign
state.
This is actually a huge story.
TassieNigel 29 Jan 2016 17:41
This god awful Clinton family had to be stopped somehow I suppose. Now if I'd done it, I'd
be behind bars long ago, so when will Hillary be charged is my question ?
Hillary made much of slinging off about the "traitor" Julian Assange, so let's see how Mrs
Clinton looks like behind bars. A woman simply incapable of telling the truth --
Celebrations for Bernie Sanders of course.
HiramsMaxim 29 Jan 2016 17:41
They also wouldn't disclose whether any of the documents reflected information that was
classified at the time of transmission,
Has nothing to do with anything. Maybe the author should read the actual NDA signed by Mrs.
Clinton.
http://freebeacon.com/wp-content/uploads/2015/11/HRC-SCI-NDA1.pdf
beneboy303 -> dusablon 29 Jan 2016 17:18
If every corrupt liar was sent to prison there'd be no one left in Washington, or Westminster
and we'd have to have elections with ordinary people standing, instead of the usual suspects from
the political class. Which, on reflection, sounds quite good !
In_for_the_kill 29 Jan 2016 17:15
Come on Guardian, this should be your lead story, the executive branch of the United States
just confirmed that a candidate for the Presidency pretty much broke the law, knowingly. If that
ain't headline material, then I don't know what is.
dusablon -> SenseCir 29 Jan 2016 17:09
Irrelevant?
Knowingly committing a felony by a candidate for POTUS is anything but irrelevant.
And forget her oh-so-clever excuses about not sending or receiving anything marked top secret
or any other level of classification including SAP. If you work programs like those you know that
anything generated related to that program is automatically classified, whether or not it's marked
as such. And such material is only shared on a need to know basis.
She's putting out a smokescreen to fool the majority of voters who have never or will never
have special access. She is a criminal and needs to be arrested. Period.
Commentator6 29 Jan 2016 17:00
It's a reckless arrogance combined with the belief that no-one can touch her. If she does
become the nominee Hillary will be an easy target for Trump. It'll be like "shooting fish in a
barrel".
DismayedPerplexed -> OnlyOneView 29 Jan 2016 16:40
Are you forgetting W and his administration's 5 million deleted emails?
http://www.salon.com/2015/03/12/the_george_w_bush_email_scandal_the_media_has_conveniently_forgotten_partner/
Bob Sheerin 29 Jan 2016 16:40
Consider that email is an indispensable tool in doing one's job. Consider that in order to
effectively do her job, candidate Clinton -- as the Secretary of State -- had to be sending and
receiving Top Secret documents. Consider that all of her email was routed through a personal server.
Consider whether she released all of the relevant emails. Well, she claimed she did but the evidence
contradicts such a claim. Consider that this latest news release has -- like so many others --
been released late on a Friday.
It is obvious that the Secretary of State and the President should be communicating on
a secure network controlled by the federal government. It is obvious that virtually none of these
communications were done in a secure manner. Consider whether someone who contends this is irrelevant
has enough sense to come in out of the rain.
Actually you should use separate PC for you banking transaction and taxes. this can be older PC
or a cheap laptop bought specifically for this purpose, or at least a VM. But it should be a separate
operating system from OS that you use to browse internet. Doing such
things on Pc you use for regular internet browsing is playing with fire.
Notable quotes:
"... mmmm missed the best security resolution of all: go to 2-Factor Authentication (2FA) for all email financial services accounts: gmail, schwab, paypal, etc, etc - makes 30 character passwords much less important ..."
"... if a financial service provider does not have 2FA, then drop them for incompetence ..."
"... one of the best advise i received is; when doing banking on your PC make sure that is the only page open ..."
"... The main issue with a full Linux system is you need a technical support person to back you up if you're not doing it yourself. Linux had the most CVE vulnerabilities after OS X ..."
"... We really don't need more kooks thinking their messages to Aunt Tillie need strong encryption. ..."
Next up is ditching old, unused or poorly maintained software. Using software is a commitment.
If you don't update it, you are wearing a "hack me" sign on your forehead. So if there are programs
or apps that you don't use, delete them.
This year, I decided to ditch my instant messaging client Adium. I was using it to enable encrypted
chats. But like many cash-strapped open source projects, it is rarely
updated and has been linked to many
security
vulnerabilities.
m krosse,
4 days ago
mmmm missed the best security resolution of all: go to 2-Factor
Authentication (2FA) for all email & financial services accounts:
gmail, schwab, paypal, etc, etc - makes 30 character passwords much
less importantif a financial service provider does not have 2FA,
then drop them for incompetence
Fred Garven
one of the best advise i received is; when doing banking on your PC make sure that is the only page
open (actually you should have a separate Pc for such transactions, or at least a VM -- NNB) the only item running on your PC at the time no other software or open web page should be running,
because those other open software can possible view your account info.
gilbert satchell ,
4 days ago
The greatest thing I did to upgrade my security was to dump anything
and everything related to apple. Moved on over to open source Linux
Mint and yes, I still use Tor.
JV ->
gilbert
satchell,
4 days ago
The main issue with a full Linux system is you need a technical
support person to back you up if you're not doing it yourself.
Linux had the most CVE vulnerabilities after OS X:
http://www.cvedetails.com/top-...
Jonathan
So for Mr & Ms Average Internet user you are going to suggest they switch to Tor and the
dark web? Before they worry about password security? Perhaps for a journalist anonymity is
paramount but most folks are only going to expose themselves to even more malware down that
path. Better to suggest that users switch to a browser that autoupdates itself and install the
HTTPS Everywhere plugin. We really don't need more kooks thinking their messages to Aunt
Tillie need strong encryption.
Gordon Bartlett
Sorry, but it's not clear what you mean by "updating your software." Try giving specific
examples of, say, what a person running Windows on their PC or Android on their mobile phone
would do on their own to upgrade, assuming, as you do, that the patches we periodically
receive from MSFT, etc. are inadequate.
JSF
I am a retired IT professional from a federal government agency. Most of our users who
needed secure communication were rather techno phobic. Try Explaining public/private keys. I
have tried some programs like signal, PGP etc. They all require the recipient to use the same
software. Signal said "invite your contacts" I am pretty sure any one getting this invite
would consider it spam, pfishing or a virus.
The sender might not know where the recipient is located. If the Corp locks their users
machines it requires IT intervention to install anything which could be days or longer not
really conducive to time sensitive information. We need to develop better technical solutions
for people who are not tech savvy
Notable quotes:
"... The Filter Bubble ..."
"... Facebook and Your Marriage ..."
"... In a presentation titled Poke Me: How Social Networks Can Both Help and Harm Our Kids at the 119th Annual Convention of the American Psychological Association, Rosen presented his findings based on a number of computer-based surveys distributed to 1,000 urban adolescents and his 15-minute observations of 300 teens in the act of studying. ..."
"... Some of the negative side effects of Facebook use for teens that Rosen cited include: ..."
"... Development of narcissism in teens who often use Facebook; ..."
"... Presence of other psychological disorders, including antisocial behaviors, mania and aggressive tendencies, in teens who have a strong Facebook presence; ..."
"... Increased absence from school and likelihood of developing stomach aches, sleeping problems, anxiety and depression, in teens who overdose in technology on a daily basis, including Facebook and video games; ..."
"... Lower grades for middle school, high school and college students who checked Facebook at least once during a 15-minute study period; ..."
"... Lower reading retention rates for students who most frequently had Facebook open on their computers during the 15-minute study period. ..."
We ARE what we THINK - not what we look at, or what we look like, or what we think we look like.
In fact, the visual cortex can be highly deceptive when it comes to the functioning of the brain.
Optical illusions exploit this brain trick.
Most practically, overloading of the visual cortex reduces higher brain function to nearly zero.
It's a very subtle process, not understood by many TV watchers. TV makes you stupid by overloading
your visual cortex, at a certain Hz frequency, which affects your reptilian brain. This is
why you get the munchies when you watch TV, or laugh without reason. Facebook is a lot more
effective at this because the associations are stronger (i.e. your friends) and it's interactive
- making the users feel as if they are controlling their reality.
The fact is that users are not controlling Facebook - Facebook is controlling you. They
have set the stage which is limited, and allow users few useful tools to manage this barrage on your
mind. The only way to really stop this invasive virus from spreading: turn it off!
Reasons to delete your Facebook:
- Stop sharing personal details with the US government and a host of other interested groups
- Enjoy more time in your life, which can be used to pursue a hobby, write a book, or learn
a foreign language
- Fill your brain with something wholesome! Plant a tree!
- Lose weight
- Increase your IQ
- Increase the speed of your computer
- Increase the speed of your internet
- Discover the thousands of other more interesting sites on the internet - such as Wikipedia!
Learn about Quantum Physics! Did you know that major universities now publish their complete
course videos online? Users can literally get a full college education by attending Stanford
(but without the degree of course) compeltely for free, online. A good start - the Khan
Academy www.khanacademy.org
No one can argue that Facebook has provided families with means of keeping in touch at long distances.
Many grandparents wouldn't otherwise see photos of their growing grandchildren. But there are
hundreds of other social networks, private networks, and other methods, of doing the same thing -
without all the 'crap' that comes with Facebook. Remember the days when we would email photos
to each other? We'd spend time even cropping photos and choosing the best one. Now, users
on Facebook will even snap away photos of their daily dinner, or inform the world that they forgot
to wash their socks. Facebook users who engage in the practice of 'wall scanning' have little
room in their brains for anything else.
Children are also a consideration with Facebook. Web Filters actually block facebook the
same way they block other illicit sites. Parents can probably relate to this article more than
the average user. Average users have accepted spam crap as part of life. It's in our
mailboxes, it's on billboards on our highways, it's everywhere. But really - it's not!
Facebook has been banned in corporate networks, government offices, schools, universities, and
other institutions. Workers at times would literally spend all day posting and reading Facebook.
It's as useless as TV - but much more addicting. From
Psychology Today:
Below we review some research suggesting 7 ways that Facebook may be hurting you.
- It can make you feel like your life isn't as cool as everyone else's.
Social psychologist Leon Festinger observed that people are naturally inclined to engage in
social comparison. To answer a question like "Am I doing better or worse than average?" you
need to check out other people like you. Facebook is a quick, effortless way to engage in social
comparison, but with even one glance through your News Feed you might see pictures of your
friends enjoying a mouth-watering dinner at Chez Panisse, or perhaps winning the Professor
of the Year award at Yale University. Indeed, a study by Chou and Edge (2012) found that chronic
Facebook users tend to think that other people lead happier lives than their own, leading them
to feel that life is less fair.
- It can lead you to envy your friends' successes. Did cousin Annabelle
announce a nice new promotion last month, a new car last week, and send a photo from her cruise
vacation to Aruba this morning? Not only can Facebook make you feel like you aren't sharing
in your friends'
happiness, but it can also make you feel envious of their happy lives. Buxmann and Krasnova
(2013) have found that seeing others' highlights on your News Feed can make you envious of
friends' travels, successes, and appearances. Additional findings suggest that the negative
psychological impact of passively following others on Facebook is driven by the feelings of
envy that stem from passively skimming your News Feed.
- It can lead to a sense of false consensus. Sit next to a friend while
you each search for the same thing on Google. Eli Pariser, author of The Filter Bubble
(2012), can promise you won't see the same search results. Not only have your Internet
searches grown more personalized, so have
social networking
sites. Facebook's sorting function places posts higher in your News Feed if they're from like-minded
friends-which may distort your view of the world (Constine, 2012). This can lead you to believe
that your favorite political candidate is a shoe-in for the upcoming election, even though
many of your friends are saying otherwise…you just won't hear them.
- It can keep you in touch with people you'd really rather forget.
Want to know what your ex is up to? You can…and that might not be a good thing.Facebook stalking
has made it harder to let go of past relationships. Does she seem as miserable as I am? Is
that ambiguous post directed at me? Has she started
datingthat guy
from trivia night? These questions might better remain unanswered; indeed, Marshall (2012)
found that Facebook users who reported visiting their former partner's page experienced disrupted
post-breakup emotional recovery and higher levels of distress. Even if you still run into your
ex in daily life, the effects of online surveillance were significantly worse than those of
offline contact.
- It can make you jealous of your current partner. Facebook stalking
doesn't only apply to your ex. Who is this Stacy LaRue, and why is she constantly "liking"
my husband's Facebook posts? Krafsky and Krafsky, authors of Facebook and YourMarriage
(2010), address many common concerns in relationships that stem from Facebook use. "Checking
up on" your partner's page can often lead to
jealousy and
even unwarranted suspicion, particularly if your husband's exes frequently come into the picture.
Krafsky and Krafsky recommend talking with your partner about behaviors that you both consider
safe and trustworthy on Facebook, and setting boundaries where you don't feel comfortable.
- It can reveal information you might not want to share with potential employers.
Do you really want a potential employer to know about how drunk you got at last week's
kegger…or the interesting wild night that followed with the girl in the blue bikini?
Peluchette and Karl (2010) found that 40% of users mention
alcoholuse on
their Facebook page, and 20% mention sexual activities. We often think these posts are safe
from prying eyes, but that might not be the case. While 89% of jobseekers use social networking
sites, 37% of potential employers do, as well-and are actively looking into their potential
hires (Smith, 2013). If you're on the job market, make sure to check your privacy settings
and restrict any risqué content to "Friends Only", if you don't wish to delete it entirely.
- It can become addictive. Think society's most common addictive substances
are coffee, cigarettes, and alcohol? Think again. The DSM-V (Diagnostic and Statistical Manual)
includes a new diagnosis that has stirred controversy: a series of items gauging Internet
Addiction. Since
then, Facebook addiction has gathered attention from both popular media and empirical journals,
leading to the creation of a Facebook addiction scale (Paddock, 2012; see below for items).
To explore the seriousness of this addiction, Hofmann and colleagues (2012) randomly texted
participants over the course of a week to ask what they most desired at that particular moment.
They found that among their participants, social media use was craved even more than tobacco
and alcohol.
Poke Me: How Social Networks Can Both Help and Harm Our Kids
The highlights of a Facebook study via
endgadget
article:
In a presentation titled "Poke Me: How Social Networks Can Both Help and Harm Our Kids"
at the 119th Annual Convention of the American Psychological Association, Rosen presented his
findings based on a number of computer-based surveys distributed to 1,000 urban adolescents and
his 15-minute observations of 300 teens in the act of studying.
Some of the negative side effects of Facebook use for teens that Rosen cited include:
- Development of narcissism in teens who often use Facebook;
- Presence of other psychological disorders, including antisocial behaviors, mania and
aggressive tendencies, in teens who have a strong Facebook presence;
- Increased absence from school and likelihood of developing stomach aches, sleeping
problems, anxiety and depression, in teens who "overdose" in technology on a daily basis, including
Facebook and video games;
- Lower grades for middle school, high school and college students who checked Facebook
at least once during a 15-minute study period;
- Lower reading retention rates for students who most frequently had Facebook open on
their computers during the 15-minute study period.
Facebook will cause lower grades for students, but it's OK for adults? hmm...
Facebook (FB) Investment Advice
It's just a matter of time when this will result in a major scandal, FB stock will crash, and
class action investigations will pile
up. Lawyers will have to hire companies
that automate workflow just to deal with the huge amount of securities class action settlements for
this case. The Facebook (FB) IPO disaster was a telling sign about this issue. Sell
it, block it, delete it, disgard it. Facebook is a bunch of trash. There's no technology
behind it. There are a huge amount of struggling companies that have developed really ground
breaking technology that will change the life of humans on this planet earth. Facebook (FB)
is not one of those companies. Facebook (FB) is a disaster waiting to happen. It's a
liability. And it's unsolveable.
Delete your Facebook account, sell your Facebook stock if you have it - it's guaranteed that by
doing so, you can grow your portfolio, increase your IQ and overall well being. Save your business,
save your family, save your life - and delete this virus!
Notable quotes:
"... New spy programs launched by the administration will seek to collect and analyze data from social media networks and develop covert operations that allow the government to use the networks for its own counter-radicalization schemes, the US officials said. ..."
"... The events of the past decade-and-a-half have made clear that the entire corporate and political establishment favors an agenda of police-state spying on the American population. ..."
"... The NSA has been privatized. All American institutions are now dedicated to our destruction. ..."
During the tech summit, the White House delegation circulated proposals calling for tech firms to
develop tools to "measure radicalization" levels among different populations ... the White House
announced new programs against "violent extremism" in the United States, including the establishment
of a new Countering Violent Extremism task force
... [which] ... will seek to "integrate and harmonize" the operations of "dozens of federal and
local agencies," ... [which] ... will "coordinate all of the government's domestic counter-radicalization
efforts,"
... The State Department will also create a new Global Engagement Center to coordinate US government
social media work internationally, a White House statement said.
New spy programs launched by the administration will seek to collect and analyze data from
social media networks and develop covert operations that allow the government to use the networks
for its own counter-radicalization schemes, the US officials said.
Media reports this week highlighted one recent contribution, ludicrously titled "ISIS in America:
From Retweets to Raqqa," published in December 2015 by George Washington University's "Program on
Extremism."
The events of the past decade-and-a-half have made clear that the entire corporate and political
establishment favors an agenda of police-state spying on the American population.
jfl
| Jan 9, 2016 7:25:14 AM |
66
He'll get it, too. Google, Facebook, the whole parasitic silicon valley culture is on board
since the passage of the omnibus budget act in the last dark days of December 2015, bearing
DIVISION N-CYBERSECURITY ACT OF 2015
within.
The NSA has been privatized. All American
institutions are now dedicated to our destruction.
I have an email account at
posteo.de
. How
much longer can it be before a similar effort is mounted outside the USA to take over the search
function and social media on the internet? If it's 'free' - you're the product.
This should write the end to American technical dominance of the internet. I hope it will.
American based TNCs, operating under American 'law', now working hand-in-glove with the American
government simply cannot be trusted.
And they wrote the law that granted them immunity for betraying their 'customers and supported
it. They're on board for our betrayal and destruction. Always have been.
This is the review of the book of David Talbot's The Devil's Chessboard. Allen Dulles, the CIA, and the Rise
of America's Secret Government by one of Moon of Alabama readers.
Looks like the course on making The USA imperial power (which was related later in Washington consensus and Wolfowitz doctrine)
was taken directly after WWII. Cold War was just a smoke screen under which the USA tried to establish hegemony over the world. Both
documents could well be written by Alan Dulles himself.
Any president who dare to deviate from this is ostracized , impeached or killed. So the political role of intelligence agencies
since their establishment by Truman was to serve as the brain center if USA imperial beuracracy (as well as the tools for projecting
it abroad)
The CIA is a hybrid of an intelligence service that gathers and analyzes foreign intelligence and a clandestine service that
conducts covert operations. Both functions are essential to creating pretexts for wars and for expanding the US influence abroad for
multinationals, and that is what they have done for 70 years (Dulles came from Wall Street). Among other things it
deliberately creates small wars just to demonstrate the US military might. Neoconservative theorist and intelligence operative
Michael Ledeen suggested that every 10 years or so, the United States "pick up some small crappy little country and throw it
against the wall, just to show we mean business."
Another book deserves to mentioned here too here too. Prouty book
The Secret Team: The CIA and its Allies in Control
of the United States and the World (which was suppressed in 1973 when irt was published and did not see shelves before
republishing in 2011) is described like the the U.S.'s aggressive and illegal war policy conducted by CIA has finally provoked
a real military threat to the U.S., albeit one that has emerged only in response to U.S. war plans
U.S. Air Force Colonel Fletcher Prouty was the chief of special operations for the Joint Chiefs of Staff from 1955 to 1964,
managing the global military support system for the CIA in Vietnam and around the world. described how the CIA infiltrated the U.S.
military, the State Department, the National Security Council and other government institutions, covertly placing its officers in
critical positions to ensure that its plans are approved and that it has access to whatever forces, weapons, equipment, ammunition
and other resources it needs to carry them out.
Highly recommended!
Notable quotes:
"... We find Dulles attempting to convince his superiors of the need and advantages of dealing with "moderate Nazis" like Reinhard
Gehlen, so today there are personalities in our government following a policy of working with "moderate Islamists" and "moderate ultra-nationalists"
to achieve our goals. ..."
"... Perhaps someone looking for more focus on Dulles the man might be disappointed by this, but for someone like myself interested
in the history and insights of era Dulles lived in. The era covered is approximately the 1930s through the 1969. ..."
"... the ruling elite of the US was deeply split. ..."
"... A large portion of the US elite was sympathetic to the Nazis. Indeed, the pro-Nazi segment of the US elite had built up ties
with Germany during the inter-war period. The bonds were economic, political and even ideological - indeed, these links were so important
that likely Germany would not have been able to rearm itself without the help of these "patriotic" Americans (Talbot makes clear that
in some cases this kinship was evident even during the war itself!). ..."
"... And no one represents the fascist sympathizing segment of the US elite like Allen Dulles. ..."
"... Talbot covers this topic well and makes a very good case for Dulles involvement - including revealing (from his day calendar)
the fact that "fired" and "retired" from the CIA Allen Dulles, spent the weekend - from the time Kennedy was shot and killed Friday
through the hours that Oswald was gunned down - at a CIA command facility in Virginia. ..."
guest77 | Jan 9, 2016 3:28:12 AM |
55
I just finished listening to the audio book of David Talbot's The Devil's Chessboard. Allen Dulles, the CIA, and the Rise
of America's Secret Government . It was very good I think.
I'll spare you a full review, but the Dulles era has some very important and interesting similarities with our own (in fact,
the ties are most certainly those first formed during the Dulles brothers tenure at State and CIA). Talbot doesn't delve deeply
into these more recent aspects, but he does acknowledge them. And the similarities are quite clear. We find Dulles attempting
to convince his superiors of the need and advantages of dealing with "moderate Nazis" like Reinhard Gehlen, so today there are
personalities in our government following a policy of working with "moderate Islamists" and "moderate ultra-nationalists" to achieve
our goals.
Initially I had heard that it was a Allen Dulles biography, and though there is a lot of detail about his personal life, his
marriage, and even his kids, I would say it strays from what one might consider a "standard" biography and is more about Dulles
and his times. For instance, there are a couple of chapters devoted just to the Kennedy Assassination, another on Oswald, and
one on the "Generals' putsch" in France in '61. Perhaps someone looking for more focus on Dulles the man might be disappointed
by this, but for someone like myself interested in the history and insights of era Dulles lived in. The era covered is approximately
the 1930s through the 1969.
Talbot uses Dulles life as the base to build up the important (and to my mind misunderstood and misconstrued) stories in recent
US history. That story is, of course, the following: despite the impression most Americans have of our country fighting the ultimate
"good war" against universally despised enemies - that fact is that the ruling elite of the US was deeply split.
A large portion of the US elite was sympathetic to the Nazis. Indeed, the pro-Nazi segment of the US elite had built up
ties with Germany during the inter-war period. The bonds were economic, political and even ideological - indeed, these links were
so important that likely Germany would not have been able to rearm itself without the help of these "patriotic" Americans (Talbot
makes clear that in some cases this kinship was evident even during the war itself!).
And no one represents the fascist sympathizing segment of the US elite like Allen Dulles. And Talbot tracks this key
figure's fascist ties as he rises in the US power structure from his early years as an OSS man wheeling and dealing with Nazi
generals in Bern, Switzerland and on through Dulles' creation and/or support of fascist governments in Latin America, the Middle
East, and Africa during the Cold War. Talbot covers the events surrounding Dulles life excellently. Especially moving was his
chapter on Guatemala - the tragedy of the Arbenz family as a mirror of the tragedy of Guatemala is covered through the eyes of
the grandson of Arbez.
Talbot covers the horror stories of the results of America working closely with dictators like Trujillo, the Shah, Mobutu Sese
Seko, and Batista (he misses Indonesia though, an operation that caused the death of 1,000,000 Indonesians). But of course, as
an American, the most important question to Talbot is that of Dulles role in the Kennedy assassination. Talbot covers this
topic well and makes a very good case for Dulles involvement - including revealing (from his day calendar) the fact that "fired"
and "retired" from the CIA Allen Dulles, spent the weekend - from the time Kennedy was shot and killed Friday through the hours
that Oswald was gunned down - at a CIA command facility in Virginia.
guest77 | Jan 9, 2016 4:08:48
AM |
59
https://blogs.princeton.edu/mudd/2008/01/allen-dulles-papers-released-by-cia-to-princeton-are-now-online/
Allen Dulles papers released by CIA to Princeton are now online
Posted on January 23, 2008 by Dan Linke
The Central Intelligence Agency has released to Princeton University some 7,800 documents covering the career of Allen W.
Dulles, the agency's longest-serving director, which now can be viewed online at
http://arks.princeton.edu/ark:/88435/st74cq497
Dulles (1893-1969), a Princeton alumnus who headed the CIA from 1953 to 1961, was renowned for his role in shaping U.S.
intelligence operations during the Cold War. Last March, the CIA released to Princeton a collection of letters, memoranda,
reports and other papers - some still redacted - that the agency had removed from Dulles' papers after his death and before
their transfer to the University in 1974.
Softpanorama Recommended
Society
Groupthink :
Two Party System
as Polyarchy :
Corruption of Regulators :
Bureaucracies :
Understanding Micromanagers
and Control Freaks : Toxic Managers :
Harvard Mafia :
Diplomatic Communication
: Surviving a Bad Performance
Review : Insufficient Retirement Funds as
Immanent Problem of Neoliberal Regime : PseudoScience :
Who Rules America :
Neoliberalism
: The Iron
Law of Oligarchy :
Libertarian Philosophy
Quotes
War and Peace
: Skeptical
Finance : John
Kenneth Galbraith :Talleyrand :
Oscar Wilde :
Otto Von Bismarck :
Keynes :
George Carlin :
Skeptics :
Propaganda : SE
quotes : Language Design and Programming Quotes :
Random IT-related quotes :
Somerset Maugham :
Marcus Aurelius :
Kurt Vonnegut :
Eric Hoffer :
Winston Churchill :
Napoleon Bonaparte :
Ambrose Bierce :
Bernard Shaw :
Mark Twain Quotes
Bulletin:
Vol 25, No.12 (December, 2013) Rational Fools vs. Efficient Crooks The efficient
markets hypothesis :
Political Skeptic Bulletin, 2013 :
Unemployment Bulletin, 2010 :
Vol 23, No.10
(October, 2011) An observation about corporate security departments :
Slightly Skeptical Euromaydan Chronicles, June 2014 :
Greenspan legacy bulletin, 2008 :
Vol 25, No.10 (October, 2013) Cryptolocker Trojan
(Win32/Crilock.A) :
Vol 25, No.08 (August, 2013) Cloud providers
as intelligence collection hubs :
Financial Humor Bulletin, 2010 :
Inequality Bulletin, 2009 :
Financial Humor Bulletin, 2008 :
Copyleft Problems
Bulletin, 2004 :
Financial Humor Bulletin, 2011 :
Energy Bulletin, 2010 :
Malware Protection Bulletin, 2010 : Vol 26,
No.1 (January, 2013) Object-Oriented Cult :
Political Skeptic Bulletin, 2011 :
Vol 23, No.11 (November, 2011) Softpanorama classification
of sysadmin horror stories : Vol 25, No.05
(May, 2013) Corporate bullshit as a communication method :
Vol 25, No.06 (June, 2013) A Note on the Relationship of Brooks Law and Conway Law
History:
Fifty glorious years (1950-2000):
the triumph of the US computer engineering :
Donald Knuth : TAoCP
and its Influence of Computer Science : Richard Stallman
: Linus Torvalds :
Larry Wall :
John K. Ousterhout :
CTSS : Multix OS Unix
History : Unix shell history :
VI editor :
History of pipes concept :
Solaris : MS DOS
: Programming Languages History :
PL/1 : Simula 67 :
C :
History of GCC development :
Scripting Languages :
Perl history :
OS History : Mail :
DNS : SSH
: CPU Instruction Sets :
SPARC systems 1987-2006 :
Norton Commander :
Norton Utilities :
Norton Ghost :
Frontpage history :
Malware Defense History :
GNU Screen :
OSS early history
Classic books:
The Peter
Principle : Parkinson
Law : 1984 :
The Mythical Man-Month :
How to Solve It by George Polya :
The Art of Computer Programming :
The Elements of Programming Style :
The Unix Hater’s Handbook :
The Jargon file :
The True Believer :
Programming Pearls :
The Good Soldier Svejk :
The Power Elite
Most popular humor pages:
Manifest of the Softpanorama IT Slacker Society :
Ten Commandments
of the IT Slackers Society : Computer Humor Collection
: BSD Logo Story :
The Cuckoo's Egg :
IT Slang : C++ Humor
: ARE YOU A BBS ADDICT? :
The Perl Purity Test :
Object oriented programmers of all nations
: Financial Humor :
Financial Humor Bulletin,
2008 : Financial
Humor Bulletin, 2010 : The Most Comprehensive Collection of Editor-related
Humor : Programming Language Humor :
Goldman Sachs related humor :
Greenspan humor : C Humor :
Scripting Humor :
Real Programmers Humor :
Web Humor : GPL-related Humor
: OFM Humor :
Politically Incorrect Humor :
IDS Humor :
"Linux Sucks" Humor : Russian
Musical Humor : Best Russian Programmer
Humor : Microsoft plans to buy Catholic Church
: Richard Stallman Related Humor :
Admin Humor : Perl-related
Humor : Linus Torvalds Related
humor : PseudoScience Related Humor :
Networking Humor :
Shell Humor :
Financial Humor Bulletin,
2011 : Financial
Humor Bulletin, 2012 :
Financial Humor Bulletin,
2013 : Java Humor : Software
Engineering Humor : Sun Solaris Related Humor :
Education Humor : IBM
Humor : Assembler-related Humor :
VIM Humor : Computer
Viruses Humor : Bright tomorrow is rescheduled
to a day after tomorrow : Classic Computer
Humor
The Last but not Least Technology is dominated by
two types of people: those who understand what they do not manage and those who manage what they do not understand ~Archibald Putt.
Ph.D
Copyright © 1996-2021 by Softpanorama Society. www.softpanorama.org
was initially created as a service to the (now defunct) UN Sustainable Development Networking Programme (SDNP)
without any remuneration. This document is an industrial compilation designed and created exclusively
for educational use and is distributed under the Softpanorama Content License.
Original materials copyright belong
to respective owners. Quotes are made for educational purposes only
in compliance with the fair use doctrine.
FAIR USE NOTICE This site contains
copyrighted material the use of which has not always been specifically
authorized by the copyright owner. We are making such material available
to advance understanding of computer science, IT technology, economic, scientific, and social
issues. We believe this constitutes a 'fair use' of any such
copyrighted material as provided by section 107 of the US Copyright Law according to which
such material can be distributed without profit exclusively for research and educational purposes.
This is a Spartan WHYFF (We Help You For Free)
site written by people for whom English is not a native language. Grammar and spelling errors should
be expected. The site contain some broken links as it develops like a living tree...
Disclaimer:
The statements, views and opinions presented on this web page are those of the author (or
referenced source) and are
not endorsed by, nor do they necessarily reflect, the opinions of the Softpanorama society. We do not warrant the correctness
of the information provided or its fitness for any purpose. The site uses AdSense so you need to be aware of Google privacy policy. You you do not want to be
tracked by Google please disable Javascript for this site. This site is perfectly usable without
Javascript.
Last modified: March, 01, 2020






 © AP Photo/ Christopher Lane
Edward Snowden Not Dead: 'He's Fine' Says Glenn Greenwald After Mysterious
Tweet
On Friday night, famed NSA whistleblower Edward Snowden tweeted out a 64 character
code before quickly deleting the message along with a mysterious warning earlier this
week that "It's Time" which had called on colleagues of the former contractor
to contact him leaving the internet to speculate that the characters could be an
encryption key for a major document leak, it may be a "dead man's switch" set to go
in effect if the whistleblower were killed or captured, or potentially both.
© AP Photo/ Christopher Lane
Edward Snowden Not Dead: 'He's Fine' Says Glenn Greenwald After Mysterious
Tweet
On Friday night, famed NSA whistleblower Edward Snowden tweeted out a 64 character
code before quickly deleting the message along with a mysterious warning earlier this
week that "It's Time" which had called on colleagues of the former contractor
to contact him leaving the internet to speculate that the characters could be an
encryption key for a major document leak, it may be a "dead man's switch" set to go
in effect if the whistleblower were killed or captured, or potentially both.

 © REUTERS/ Svein Ove Ekornesvaag/NTB Scanpix
'It's Time': Whistleblower Edward Snowden Tweets Mysterious Warning
© REUTERS/ Svein Ove Ekornesvaag/NTB Scanpix
'It's Time': Whistleblower Edward Snowden Tweets Mysterious Warning